After last warm up we will continue and will look on some HARDER reverse engineering problems. This challenges are really good playground! Let’s try!
Last episode > Level 0, 1, 2 >>
Creds >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox (aka TheSysRat)
What I used:
- FlareVM – for testing Windows 32-bit apps
- Strings – it is also basic technique for hard-coded strings inside app
- Ghidra – one of the best de-compiler tool and open source !
- ImmunityDebbuger – great tool for 32-bit app debugging
Level 3
What we do first time, we can try to run this app >
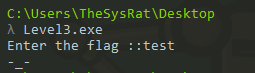
OK, possible first hit is output after input bad flag. So let’s look on strings in app. I used strings in Ghidra >
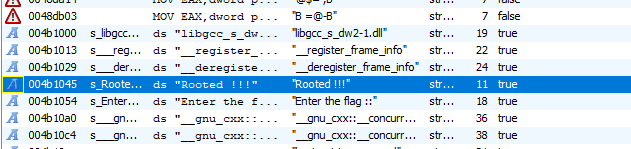
And there are two interesting “Enter flag ::” and “Rooted !!!”. So let’s inpect >

We can diassembilly Function FUN_001014af and there is a source code >
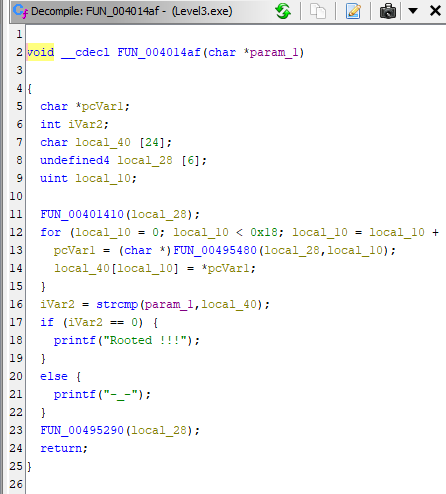
We are looking for a MASTER pasword, is locate in local_40 parametr. We have to look in memory before changeing parameter using XOR in the loop.
So we should set break point in ImmunittyDebugger to this memory addr >
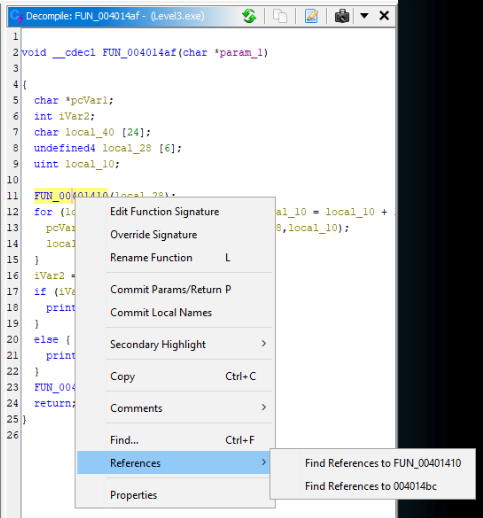
We have to find a references to FUN_00401410 >
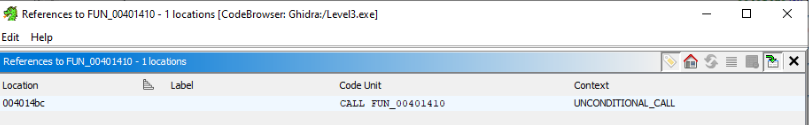
So we can try it in ImmunittyDebugger >
Set thwe Break Point to our reference 004014bc (Press F2) >
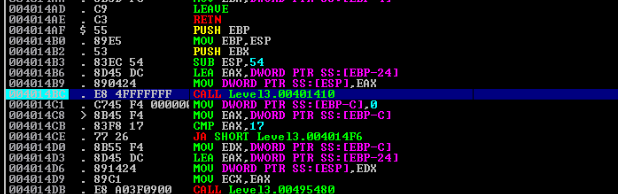
After that we can run the app ( Press F9 ) >
Now we will insert any input to the app >
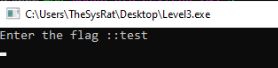
App is pausing in on our Break Point >
And we can go some steps into ( Press F7 ) after some steps (about 14x) we will see a flag in Registers (MMX) section like this >
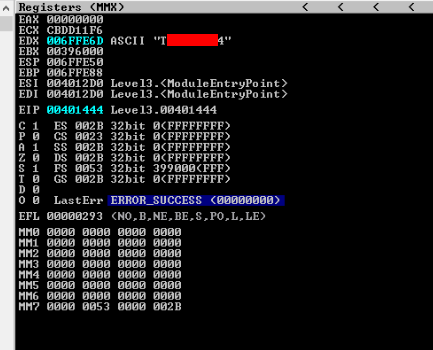
That was little hadr, but DONE !
Level 4
We can start as last time running the app >
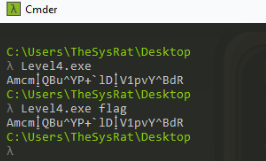
So output is looking not so good, no hint are there.
So Let’s start Ghidra and look on it what we could find.
There no too much, but one interesting thing is there in functions >
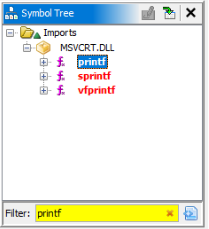
Therte is a printf function, maybe is a hint.. We can find a reference to our function >
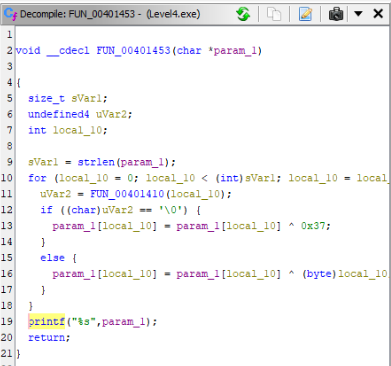
Now we can see param_1 variable, we can find a reference to FUN_00401453 >
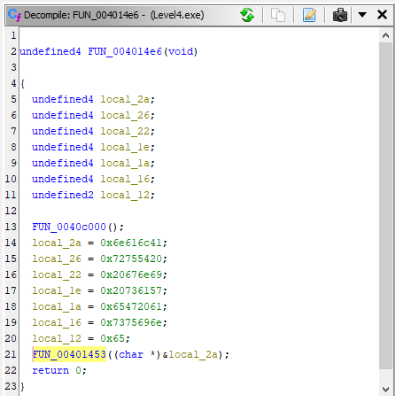
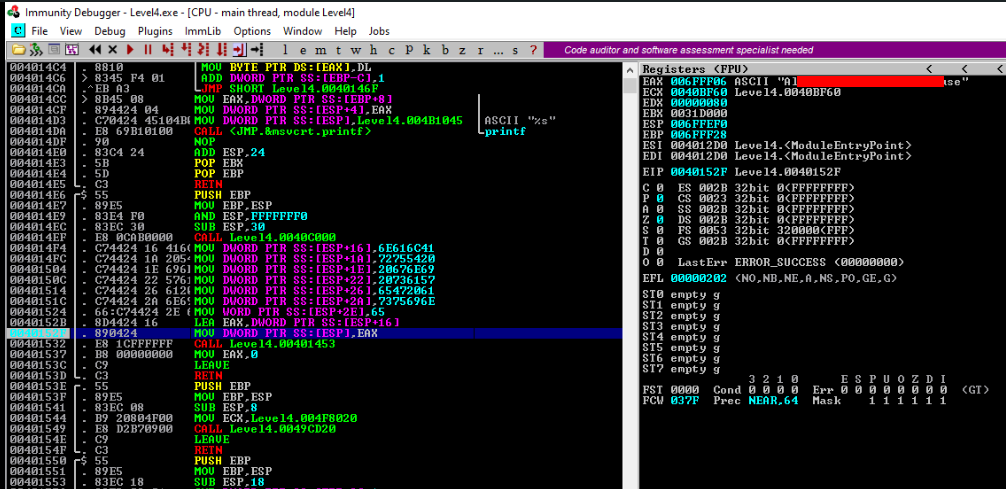
And there would be our BreakPoint, step before Call FUN_00401453, there is probably moving our flag to local_40 variable >
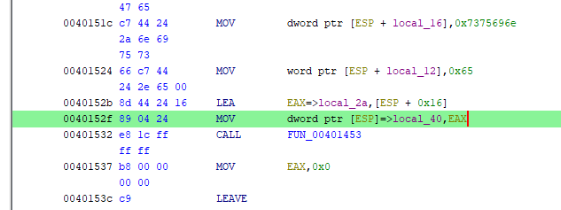
So let’s try in ImmunittyDebugger >
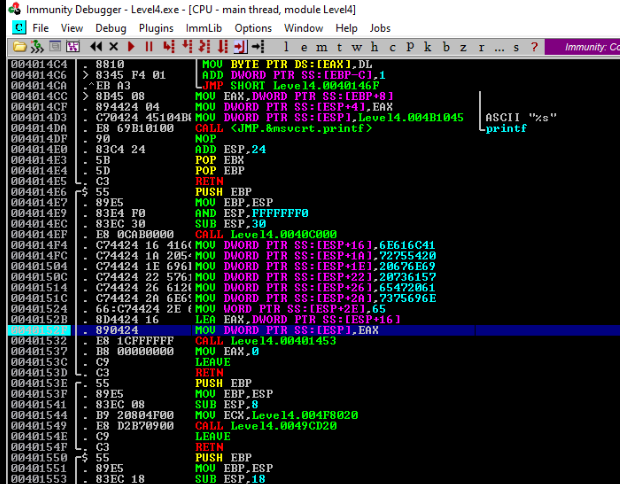
Set Break Point to addr 0040152F ( Press F2 ) >
Run app ( Press F9 ) >
And if everthing is OK, we can see the flag >