Today I will look on some reverse engineering techniques. This challenges are really good playground! Let’s try!
Creds >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox (aka TheSysRat)
What I used:
- FlareVM – for testing Windows 32-bit apps
- Strings – it is also basic technique for hard-coded strings inside app
- Ghidra – one of the best de-compiler tool and open source !
Level 0 – WarmUP 🙂
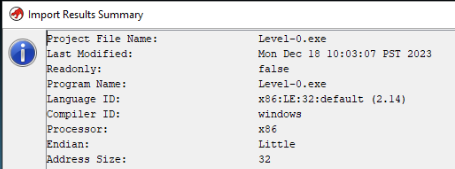
After import to Ghidra we can see basic information >
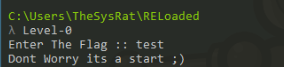
We can try run the program in terminal >
So we can try to analyse with strings, I used a strings inside Ghidra >
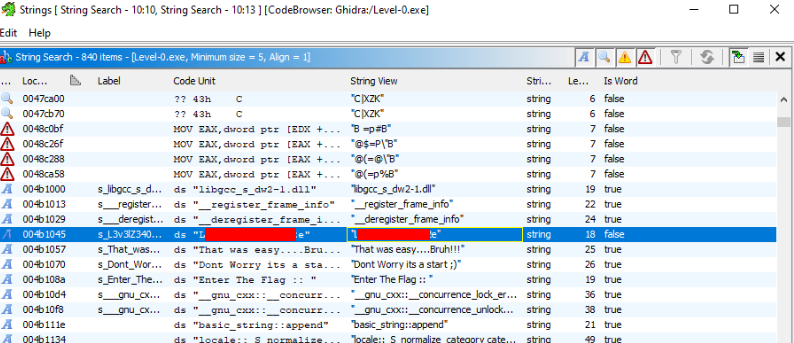
And yes we can find a flag, we can also tested in program, if it is work >
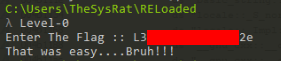
So this was easy, let’s continue >
Level 1
In this task we are looking for a code or pin, so we can start in try to look on app output and test it >
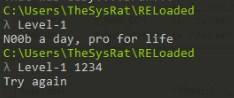
After that we have two options brute forcing or we can de-compiled app in Ghidra and try to find a variable or function for check our input >
I checked in Ghidra, first step is looking for a interesting strings, and there is something spicy >
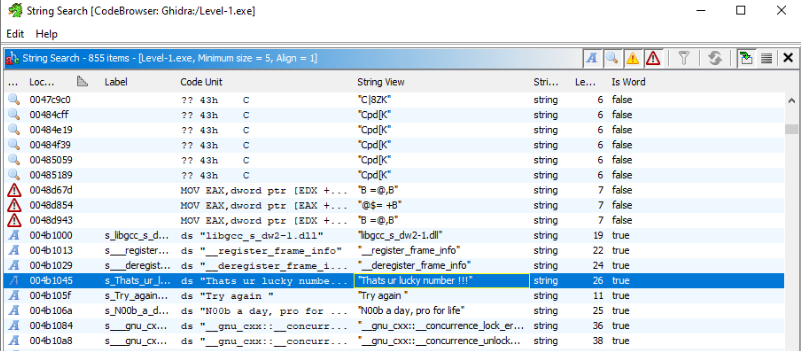
And we can find a de-compiled function like >
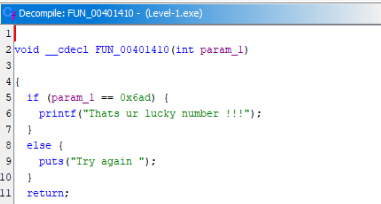
Interesting variable is there 0x6ad which we can convert to decimal >
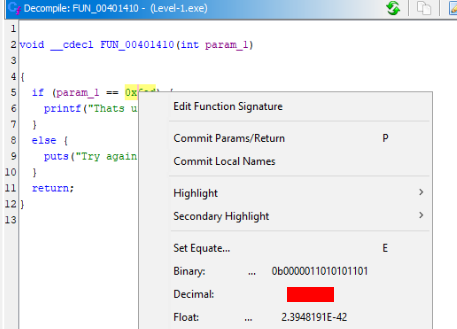
And we can find our lucky number, let’s try to test in our app >
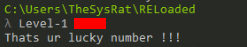
And works!
Level 2
We can start with run the app and look for any hint >
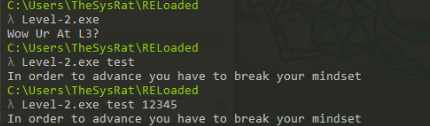
In level 2 we are looking for instruction and we have to manipulated with that. So we can start import to Ghidra and try to some string used before.
And there is another one look better >>
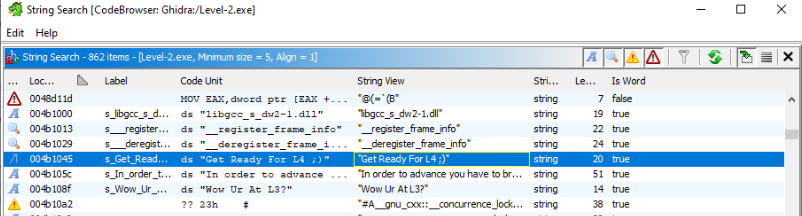
And we can found this two interesting parts :
De-compiled code >>
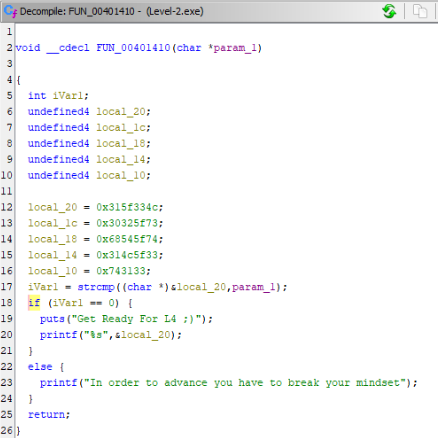
And instructions >>
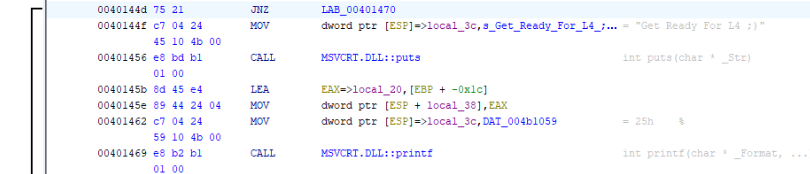
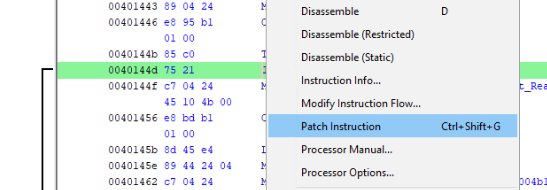
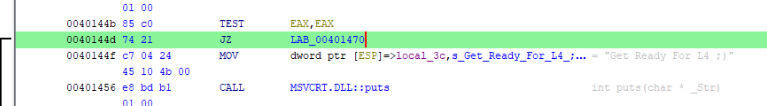
So what we can do, it is manipulated with this instruction >

Which mean change this condition >
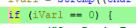
So if we change flag JNZ { Jump short if not zero (ZF=0) } to JZ { Jump short if zero (ZF = 1) } ! If we do that, all flag without original flag should be accepted! So do this >
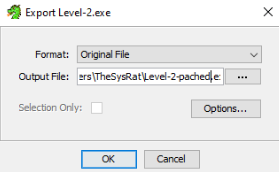
And export program as “Original File” with another name >
And we can try >