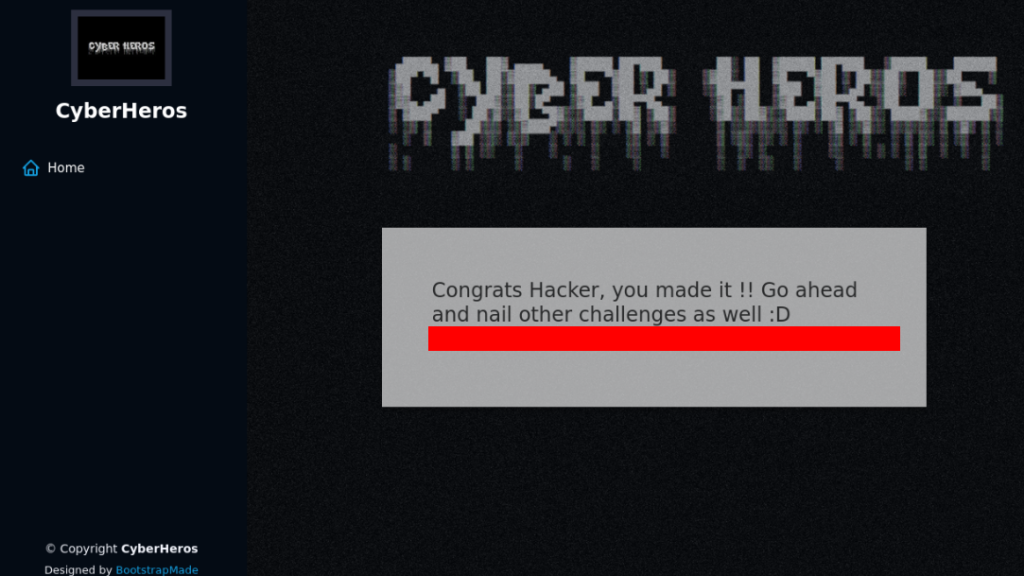
Creds >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox (aka TheSysRat)
Recon >>>
Nmap >>
┌──(root㉿kali)-[/home/kali]
└─# nmap -A -p- -T4 10.10.23.37
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-05 14:58 EST
Nmap scan report for 10.10.23.37
Host is up (0.052s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 26:29:50:3a:db:03:0b:e5:04:45:f3:61:24:91:8e:46 (RSA)
| 256 41:8c:1b:9b:5f:fe:fc:cd:7f:4e:0a:61:4a:26:c1:5a (ECDSA)
|_ 256 14:63:ae:ea:a4:95:9a:13:10:22:e3:a6:73:f6:bc:93 (ED25519)
80/tcp open http Apache httpd 2.4.48 ((Ubuntu))
|_http-server-header: Apache/2.4.48 (Ubuntu)
|_http-title: CyberHeros : IndexNothing special.
Web Site >>

Looks normal nothing special.
Dirsearch >>
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/Downloads/reports/http_10.10.23.37/_23-12-05_15-10-10.txt
Target: http://10.10.23.37/
[15:10:10] Starting:
[15:10:25] 200 - 475B - /assets/
[15:10:25] 301 - 311B - /assets -> http://10.10.23.37/assets/
[15:10:28] 200 - 725B - /changelog.txt
[15:10:39] 200 - 2KB - /login.htmlSo we can download login.html and look on source code >>
And interesting is a login script inside login.html >
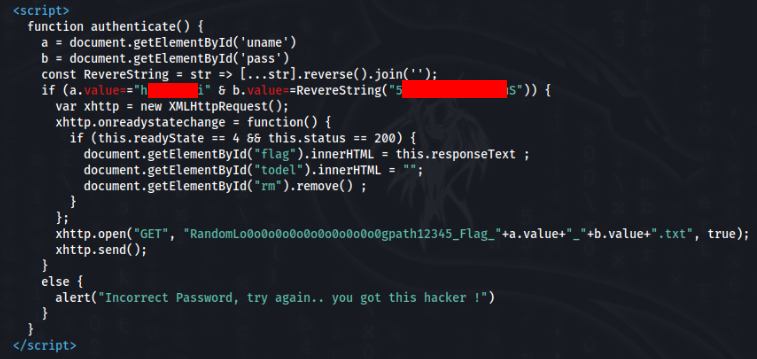
Super easy, script include login and string which we reverse, we will get a password. So let’s try it…. And it work :-).