CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
Description >>
After participating in one too many incident response activities, PicoSecure has decided to conduct a threat simulation and detection engineering engagement to bolster its malware detection capabilities. You have been assigned to work with an external penetration tester in an iterative purple-team scenario. The tester will be attempting to execute malware samples on a simulated internal user workstation. At the same time, you will need to configure PicoSecure’s security tools to detect and prevent the malware from executing.
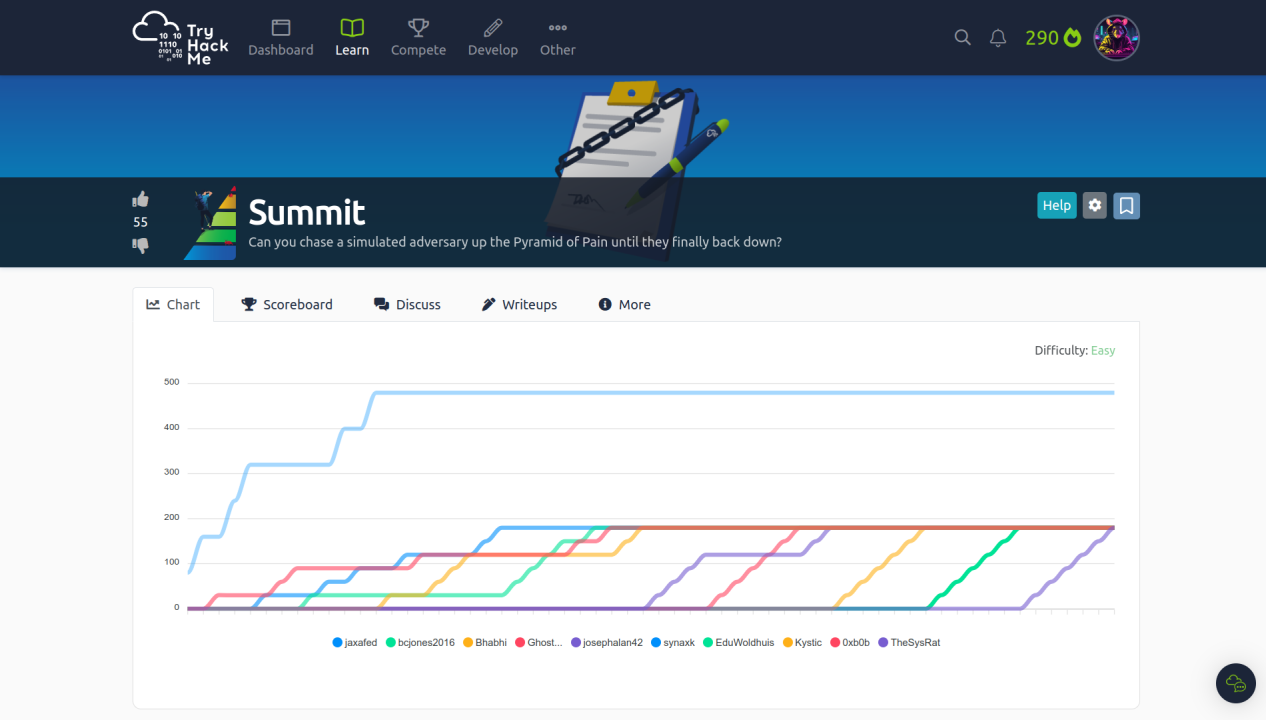
Following the Pyramid of Pain’s ascending priority of indicators, your objective is to increase the simulated adversaries’ cost of operations and chase them away for good. Each level of the pyramid allows you to detect and prevent various indicators of attack.
So let’s start >>
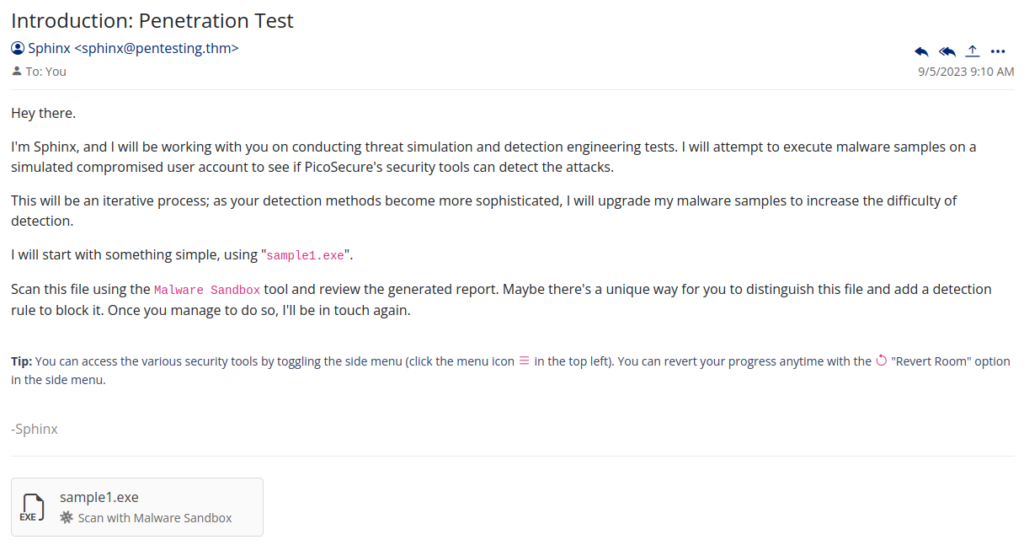
Sample1.exe >>>
We can open mail box and let’s look on message >
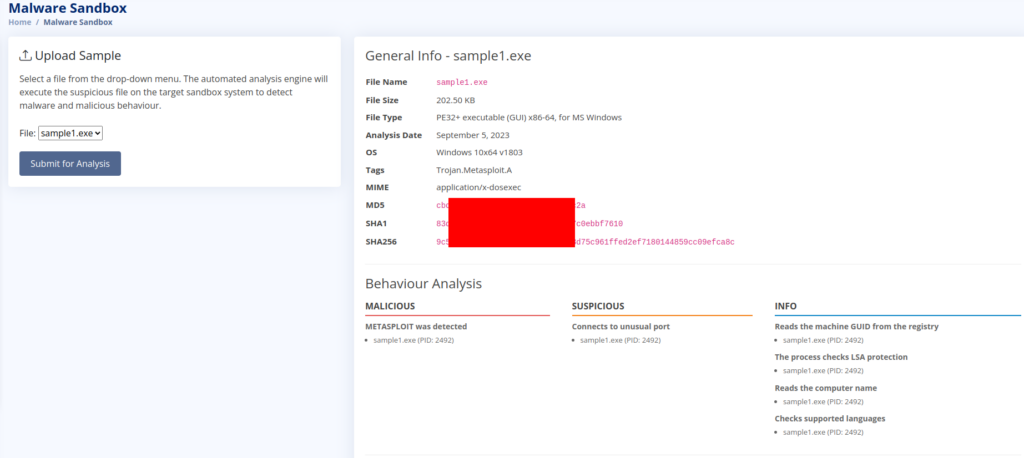
Now we can scan malware sample in Malware Sandbox >
We can solve it and create rule into Manage Hashes >>
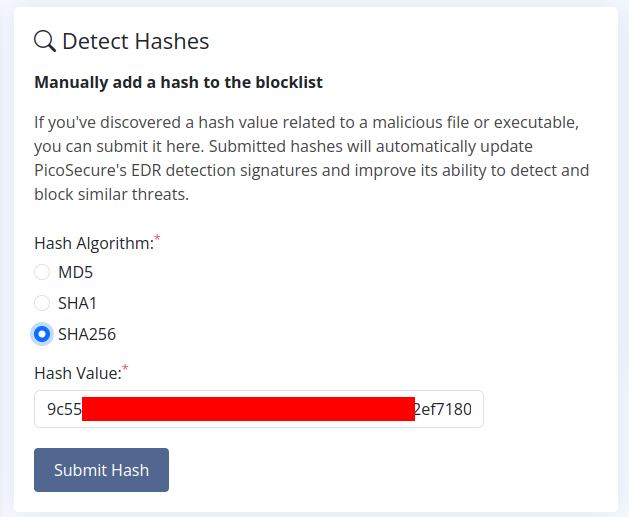
And yes, it was right way >
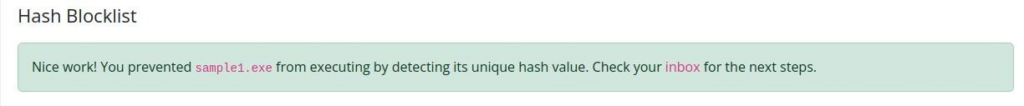
Sample2.exe >>>
Inside mail box we can found new instruction >
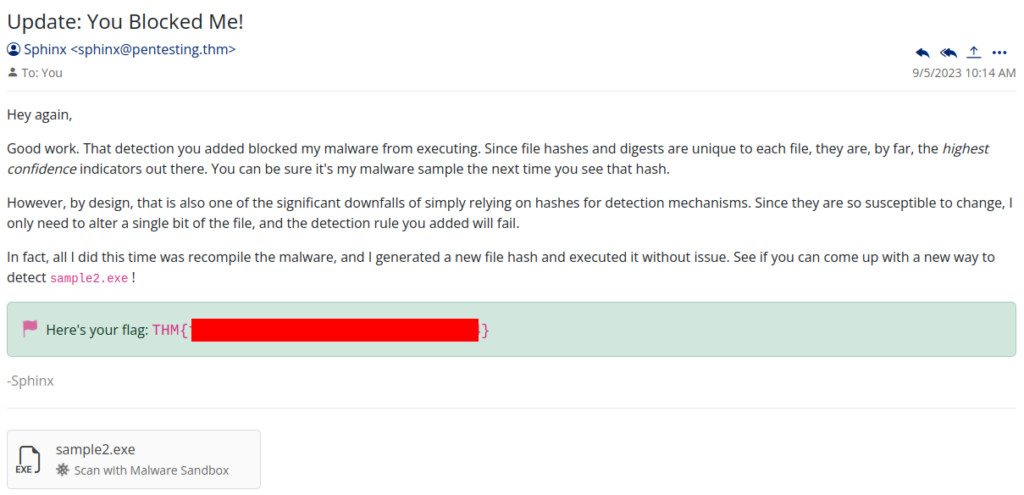
So we can again analyse malware in Sandbox and we can found some interesting thing in Network Activity >>
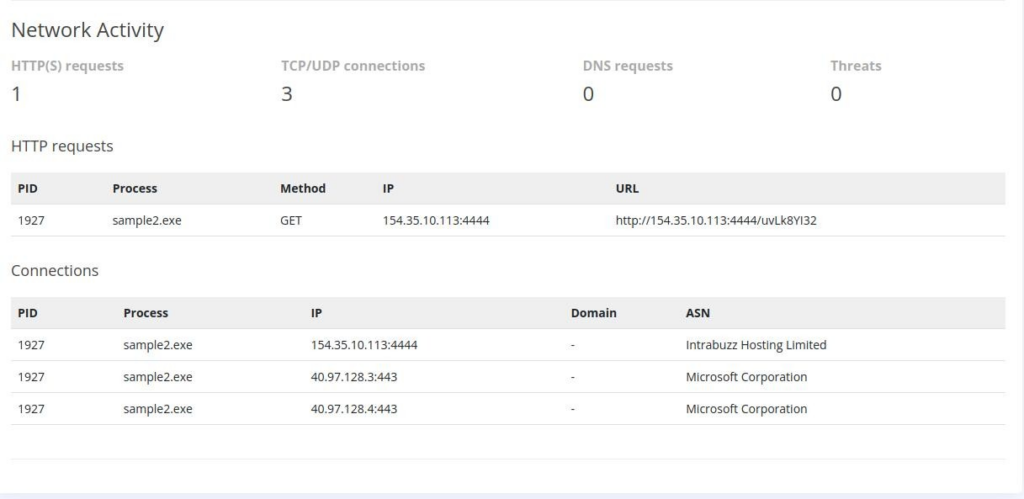
So we can add new Rule into Firewall Manager >>
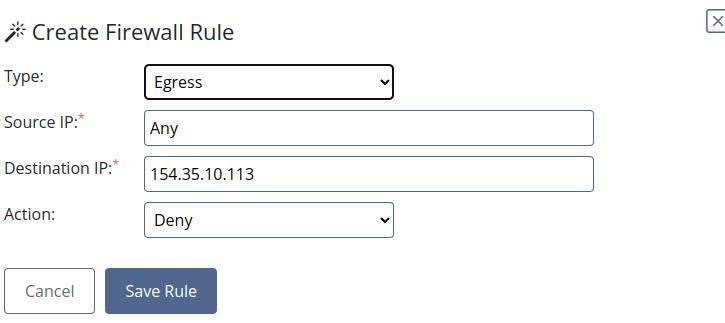
And success >>
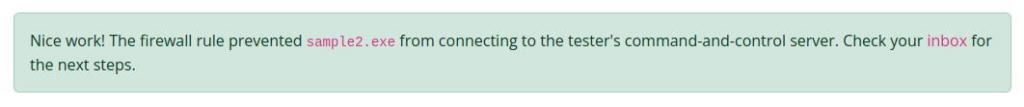
Sample3.exe >>>
Inside mail box we can found new instruction >
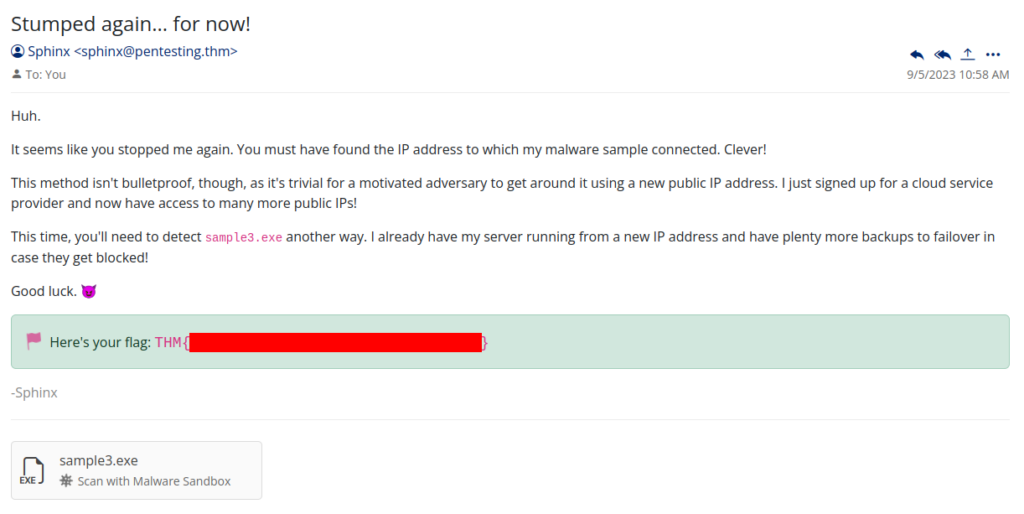
So again we start be analyse malware, now we can found a domain for add another rule into DNS filter >>
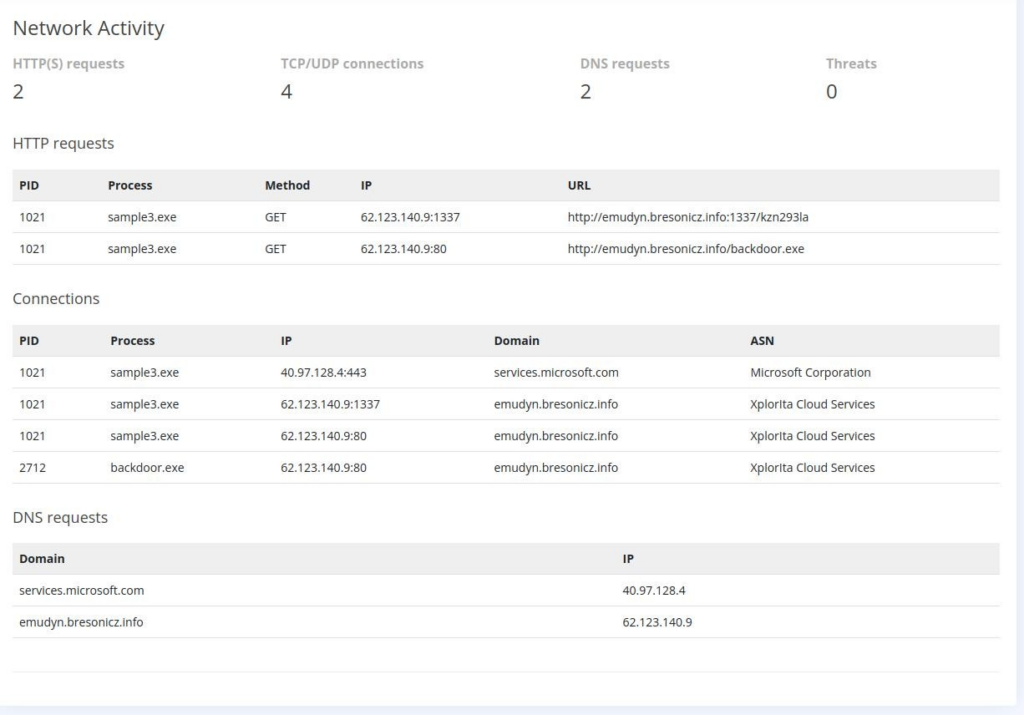
We create new rule >>
And success >>

Sample4.exe >>>
Inside mail box we can found new instruction >
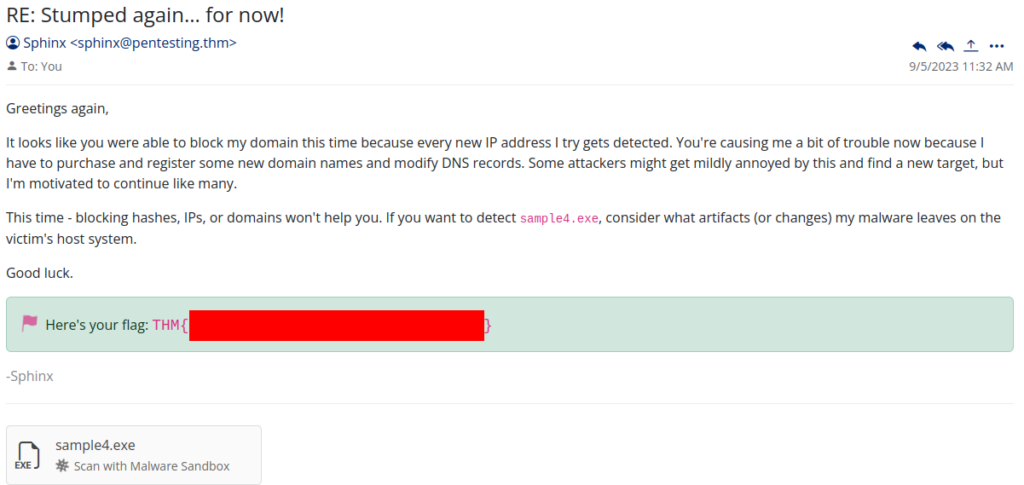
So again we start be analyse malware, now we can found is a registry keys and on of this do something evil DisableRealtimeMonitoring >>
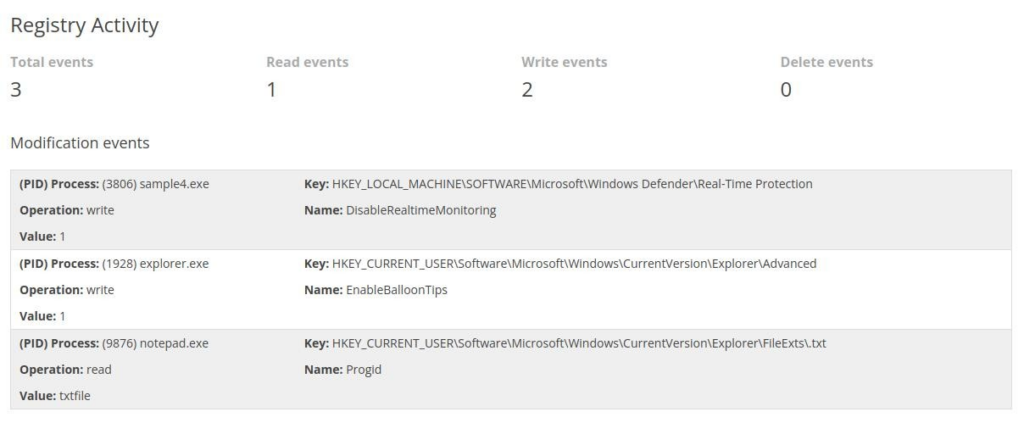
So we can do a Sigma rule to stop this activity >>
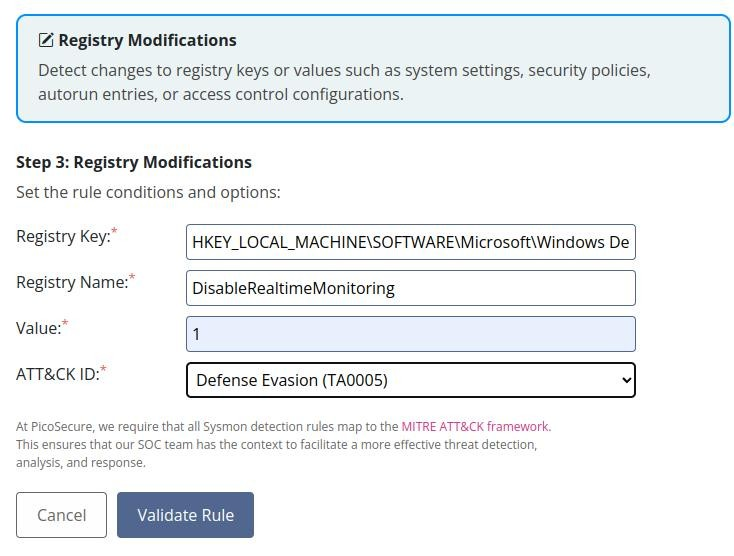
And success!
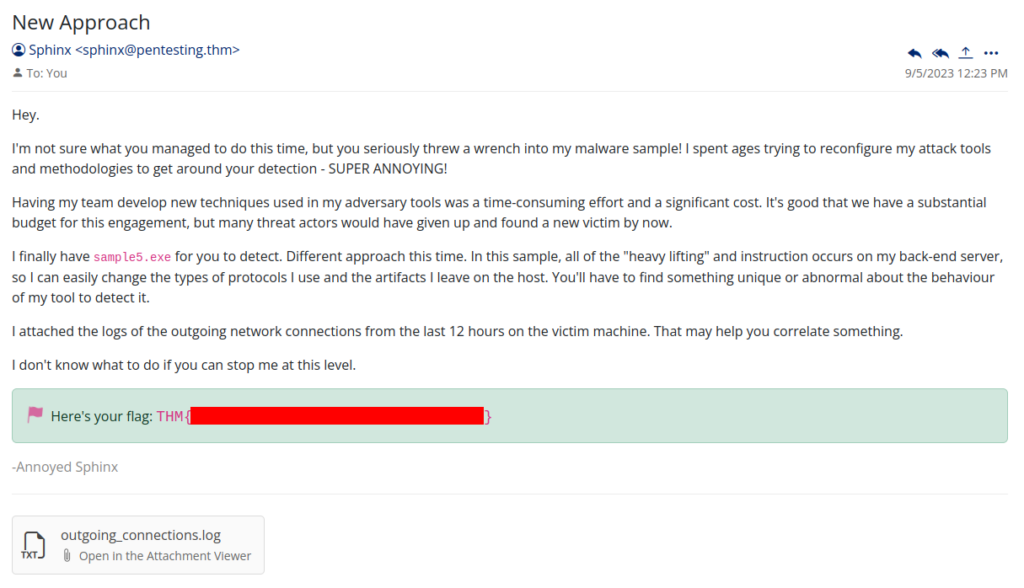
Sample5.exe >>>
Inside mail box we can found new instruction >
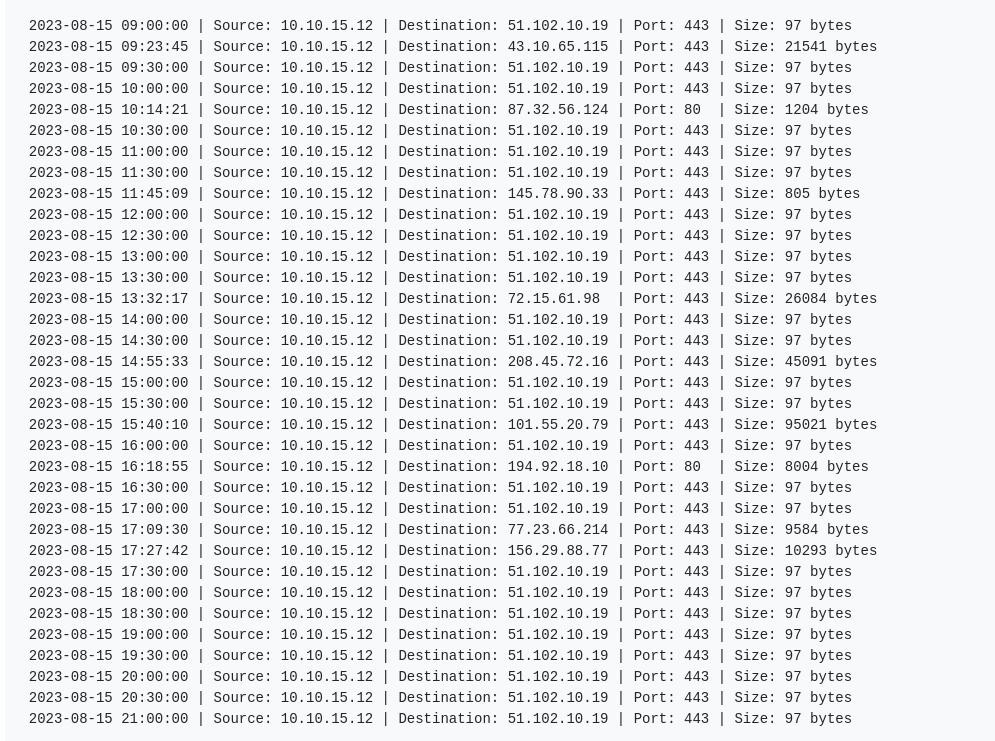
So let’s look on outgoing_connections log >>
How to fix it? We can create another Sigma Rule >>
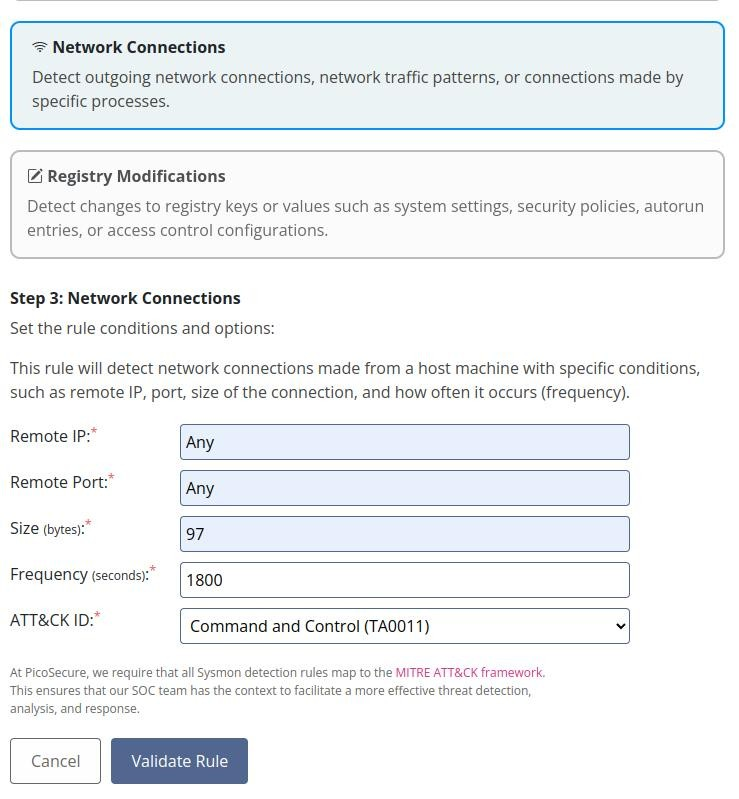
And again success!! So let’s to last one >>
Sample6.exe >>>
In mail box we have the last one instruction >>

So we can inspect commands log >>
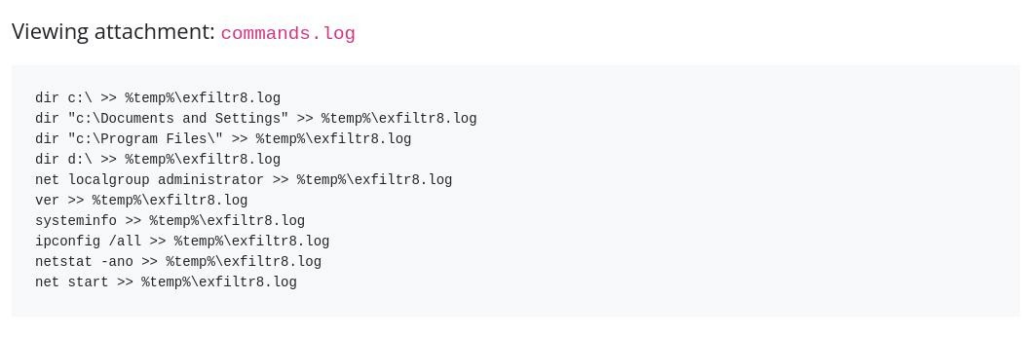
And we can see some commands, so we can create another one Sigma Rule
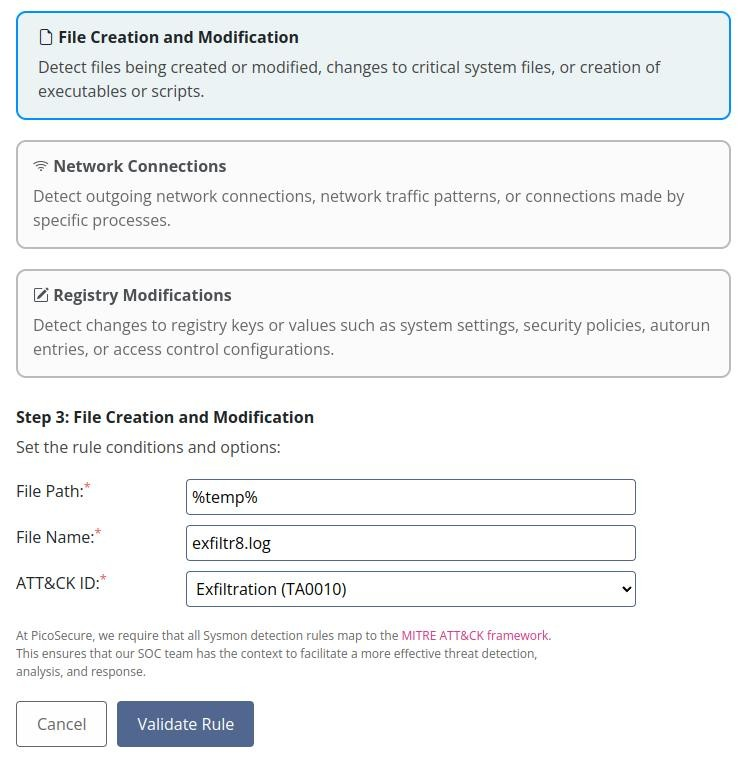
And again success!!