Today I get a sample of phishing email, targeting on czech users e-mail address hosting on atlas.cz .
Email looks really simple >>
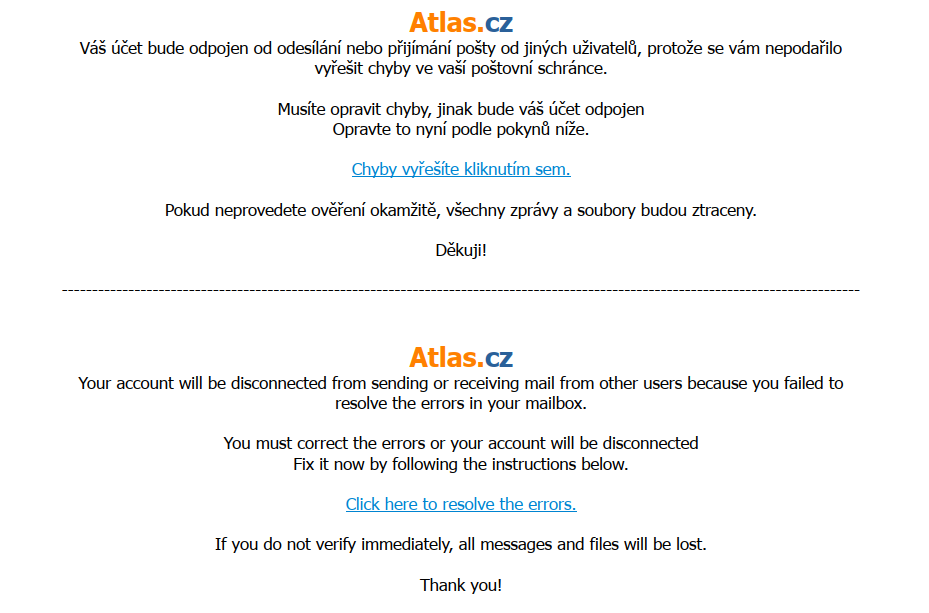
First alert is email address came from >
-------- Přeposlaná zpráva --------
Předmět: DŮLEŽITÉ_INFORMACE
Datum: Thu, 29 Feb 2024 11:50:22 +0100
Od: Atlas.cz e-mail <dusan***ras@atlas.cz>That is one of abuse email user, I contacted him do change password.
Second alert is link to direct >>
We can found in the body of e-mail this >
<a href="https://rb.gy/kd8v1d" moz-do-not-send="true">Chyby
vyřešíte kliknutím sem.</a></font></strong></div>Quick search in virustotal.com >>
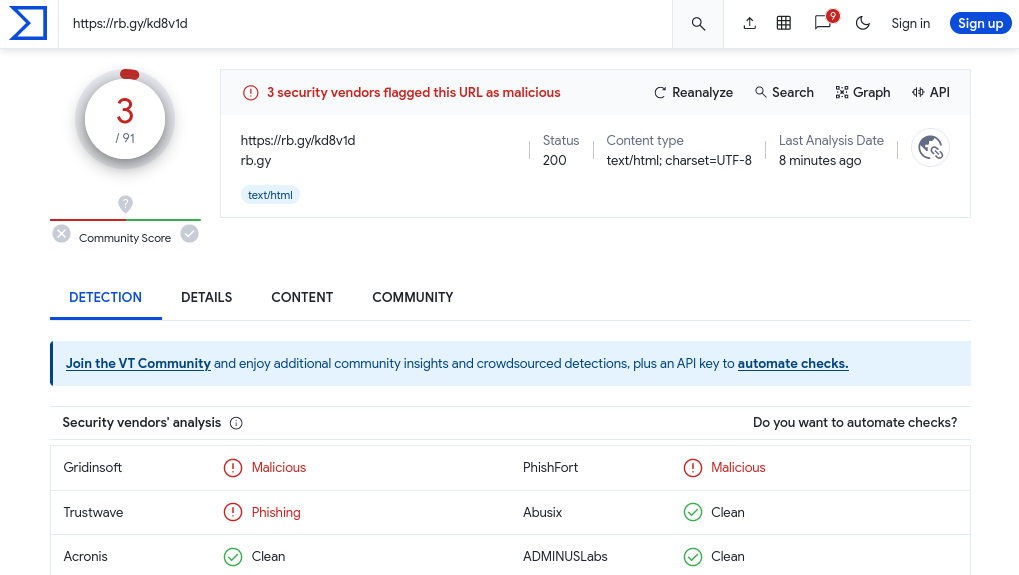
Not much scans alert, but we can found this uncovered address >>
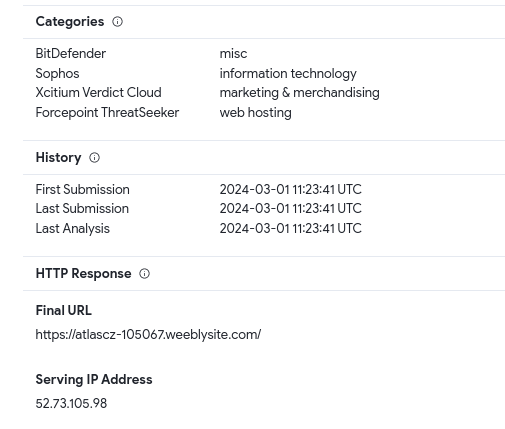
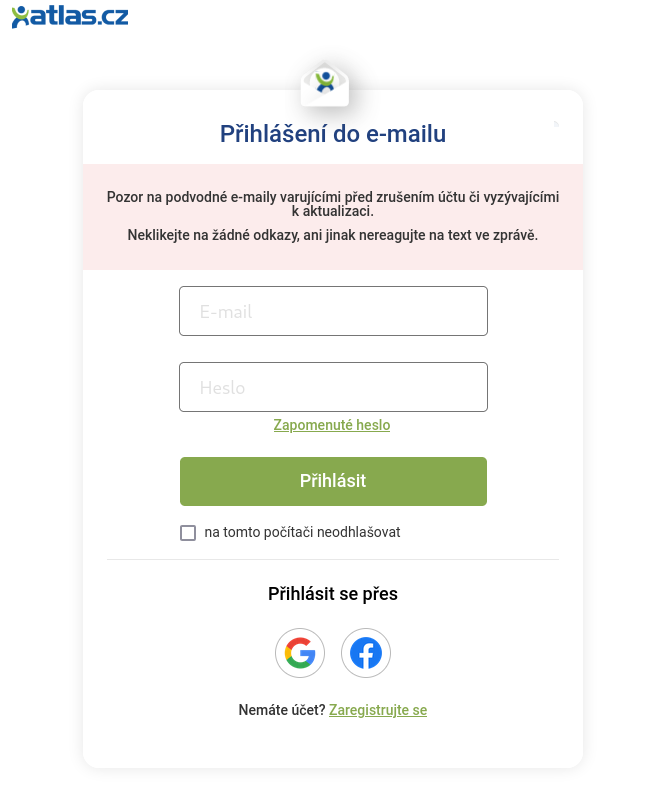
So let’s look on it. After run link in browser we can see quite similar page as original login page >
Fake login >>

Original login >
Let’s Burp it >>>
What we can do is look on request and try to find what is collect user data >
Our request >
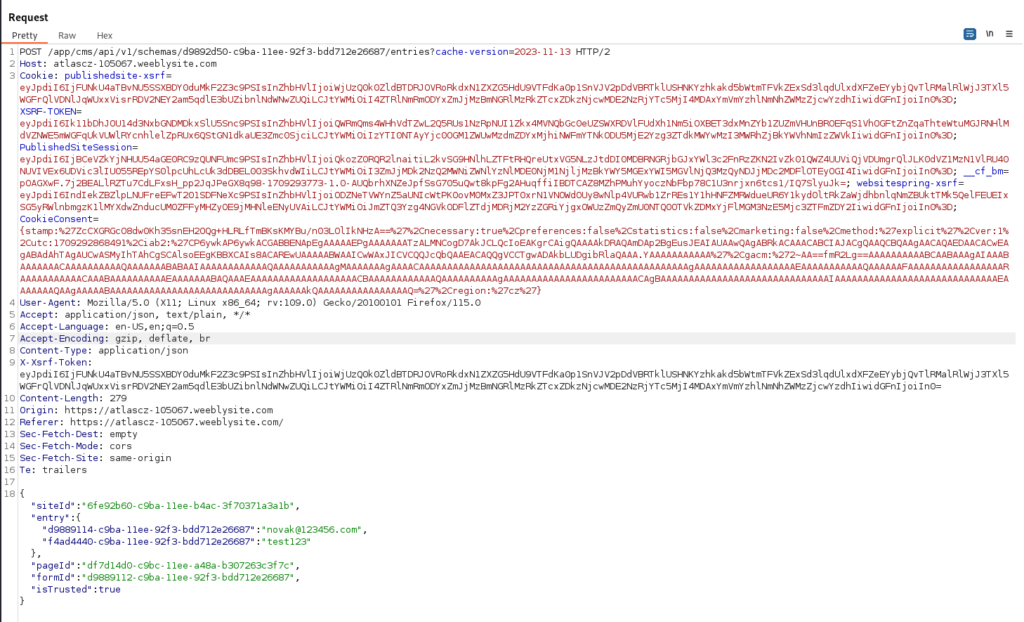
There we can find some JSON data to send over API request to store our personal data. Website is using Weebly CMS, and there is hidden a script in e-commerce module to allow attacker collect our data (Requests before sending).
Next we can see another strange, schema id is same as a first entry in JSON data collection.
weeblysite.com >>
There is not too much interesting to find >
┌──(kali㉿kali)-[~]
└─$ whois weeblysite.com
Domain Name: WEEBLYSITE.COM
Registry Domain ID: 1767369527_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.safenames.net
Registrar URL: http://www.safenames.net
Updated Date: 2023-12-19T08:45:56Z
Creation Date: 2012-12-19T04:07:22Z
Registry Expiry Date: 2024-12-19T04:07:22Z
Registrar: SafeNames Ltd.
Registrar IANA ID: 447
Registrar Abuse Contact Email: abuse@safenames.net
Registrar Abuse Contact Phone: +44.1908200022
Domain Status: clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Domain Status: clientUpdateProhibited https://icann.org/epp#clientUpdateProhibited
Name Server: DNS1.P08.NSONE.NET
Name Server: DNS2.P08.NSONE.NET
Name Server: DNS3.P08.NSONE.NET
Name Server: DNS4.P08.NSONE.NET
DNSSEC: unsignedHole traffic is guarded by Cloudflare, if we will enumerate server services >
PORT STATE SERVICE VERSION
80/tcp open http Cloudflare http proxy
|_http-server-header: cloudflare
|_http-title: Attention Required! | Cloudflare
443/tcp open ssl/http Cloudflare http proxy
|_http-server-header: cloudflare
| ssl-cert: Subject: commonName=weeblysite.com/organizationName=Cloudflare, Inc./stateOrProvinceName=California/countryName=US
| Subject Alternative Name: DNS:weeblysite.com, DNS:*.weeblysite.com
| Issuer: commonName=Cloudflare Inc ECC CA-3/organizationName=Cloudflare, Inc./countryName=US
| Public Key type: ec
| Public Key bits: 256
| Signature Algorithm: ecdsa-with-SHA256
| Not valid before: 2023-09-29T00:00:00
| Not valid after: 2024-09-27T23:59:59
| MD5: 5203:81c5:1dff:9e92:2832:07f8:355f:592a
|_SHA-1: b146:c751:e8c2:741a:ae4e:ad99:bf5e:026e:f083:81ef
|_http-title: 400 The plain HTTP request was sent to HTTPS port
8080/tcp open http Cloudflare http proxy
|_http-title: Attention Required! | Cloudflare
|_http-server-header: cloudflare
8443/tcp open ssl/http Cloudflare http proxy
|_http-server-header: cloudflare
| http-methods:
|_ Supported Methods: OPTIONS
| ssl-cert: Subject: commonName=weeblysite.com/organizationName=Cloudflare, Inc./stateOrProvinceName=California/countryName=US
| Subject Alternative Name: DNS:weeblysite.com, DNS:*.weeblysite.com
| Issuer: commonName=Cloudflare Inc ECC CA-3/organizationName=Cloudflare, Inc./countryName=US
| Public Key type: ec
| Public Key bits: 256
| Signature Algorithm: ecdsa-with-SHA256
| Not valid before: 2023-09-29T00:00:00
| Not valid after: 2024-09-27T23:59:59
| MD5: 5203:81c5:1dff:9e92:2832:07f8:355f:592a
|_SHA-1: b146:c751:e8c2:741a:ae4e:ad99:bf5e:026e:f083:81ef
|_http-title: Attention Required! | Cloudflare
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Uptime guess: 0.000 days (since Fri Mar 1 06:36:26 2024)
Network Distance: 8 hops
TCP Sequence Prediction: Difficulty=264 (Good luck!)
IP ID Sequence Generation: All zerosSo nothing interesting there.
Conclusion >>
- Don’t click on shorted links !
- Look for email , if is official or not !
- Be careful before you get somewhere you login data !

